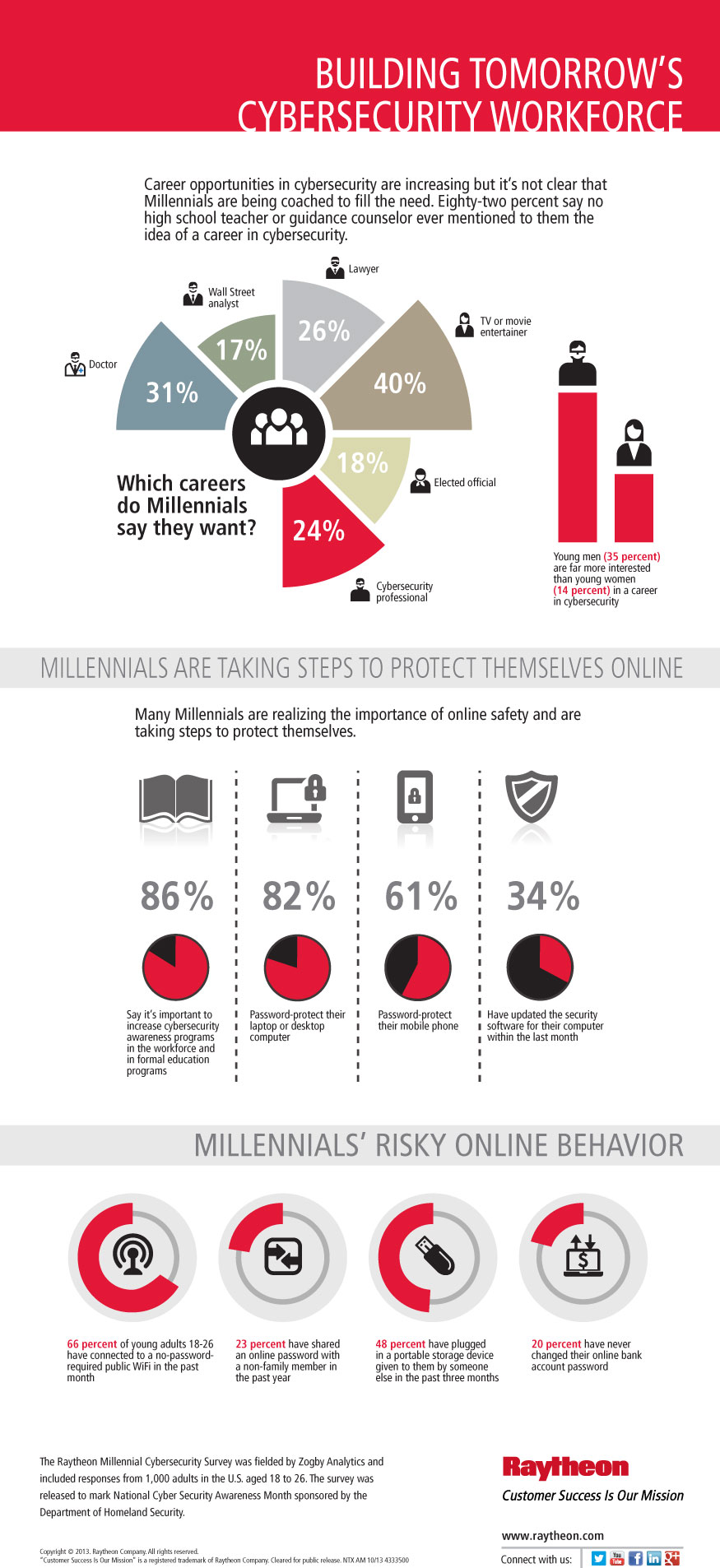
A developer created a game that became an Internet sensation in just a few hours. Overwhelmed by the success of his work, he decided to sell it.
This is similar to what happened with Flappy Bird. Vietnamese game developer Dong Nguyen, decided to sell the famous app as soon as it became successful.
Yet in this case the game is not about birds and tubes, rather viruses and IT security. The game is called ‘Hacker Experience‘ and its creator, a computer science student at the University of Winnipeg, has been saturated by the response to this simulator.

“I’m tired. So I’m selling my game that just went viral “. With these words, Renato Massaro, who is just 21 years old, has terminated his relation with ‘Hacker Experience’, the game he was working on for two-and-a-half years.
The game is a hacking simulator, where players can play the role of a cyber-criminal trying to become rich and powerful working for an evil corporation. In this game, you can hack virtual servers, develop new software, mine bitcoins, work on missions, hack banks, etc.
But it’s only a game; everything that happens is just a simulation, so players are not really handling viruses that could damage their computers or destroying the hardware on other people’s systems. It’s all a work of fiction, a simulator that you can play online and which became an incredible success within just a few hours.
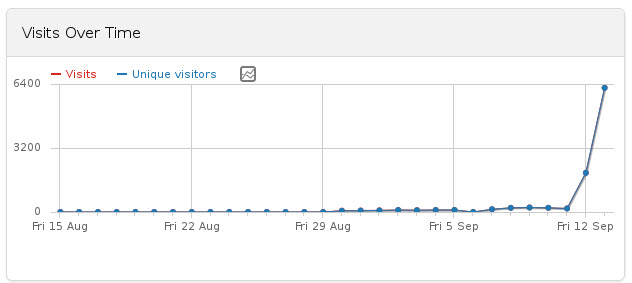
“It went viral in a matter of minutes,” says Massaro, who goes on to explain how he launched ‘Hacker Experience‘ at 4pm on September 13 and, “…by the end of the day, it had 2000 registered users and 1000 online.”
This instant success was largely down to two news aggregators: Hacker News and Reddit who made the name of this game spread like wildfire and the number of users rocket in no time at all.
What this Brazilian student had been working on for so long, suddenly became a sensation. “Now, about 30 hours later, there are 6000 registered users and 1500+ online,” said Massaro, as he realized that the situation was simply too much for him.
In just a few hours the situation had become unbearable for the young student having received thousands of emails and messages. Overwhelmed by the situation, the creator of the simulator decided to put ‘Hacker Experience’ up for sale.
What was the asking price? There wasn’t one. Massaro waited for offers via email. He was selling the game, the code and the NeoArt Labs brand, under which he had launched the game, but as he had never before sold software, he had no idea what price to put on his game.
He did however tell potential buyers that this was the result of more than two and a half years work and that ‘Hacker Experience’ was already a lucrative source of income.

According to his calculations, revenue from Google AdSense and Premium account users (‘Hacker Experience’ is based around the ‘freemium’ model, where players pay for certain features that give them an advantage or make the game quicker) would offer a minimum return of $1000 (about 800 euros) a month. However, Massaro also claims that with a few adjustments and offering more advantages to Premium users, ‘Hacker Experience’ could soon be offering returns of up to $5000 (almost 4000 euros) per month.
Nevertheless, any potential buyer should also be aware the game’s users have already found flaws and have been sending them via email to the creator as well as publishing them on the Hacker Experience wikipedia page and forum.
The game is still operating, though probably it is now under new ownership. In exchange, the creator will have received a decent sum (according to his own calculations, Massaro suggests that a price of some 60,000 dollars for the game would be easily recovered within the space of one year) and above all he can now enjoy the peaceful life that was so rudely interrupted by ‘Hacker Experience‘, the virus game that went viral.
The post Hacker Experience. The game about IT security caused a sensation on the Internet appeared first on MediaCenter Panda Security.