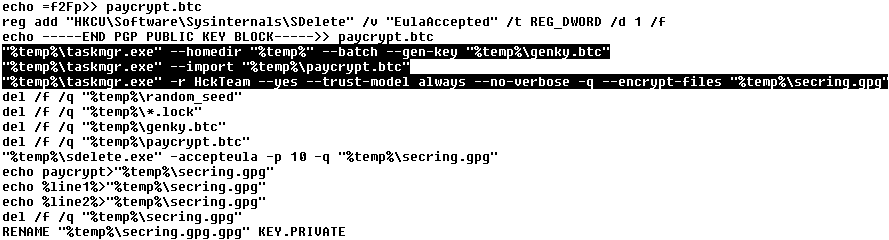
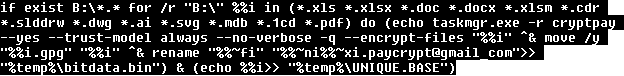- The second quarter of 2014 has seen the creation of 15 million new strains of malware
- Trojans are still the most common type of malware, though they are losing ground thanks to the rise of PUPs (Potentially Unwanted Programs)
- Smartphones, both Android and iOS, are still under attack
- The global infection rate during this period was 36.87%, a significant increase on previous quarters, thanks in part to the increase in PUPs
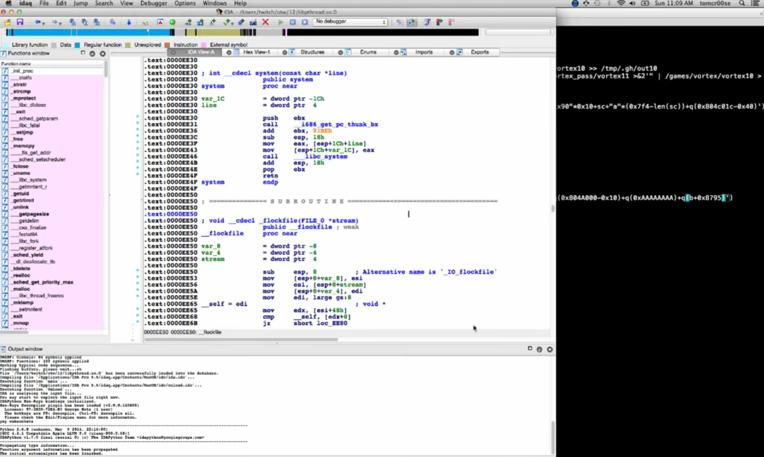
Panda Security, The Cloud Security Company, has announced the latest findings of the PandaLabs quarterly report for Q2 2014. The main conclusions of the study include the fact that malware is still being created at the record levels reached in the previous quarter: 15 million new samples were generated, at an average rate of 160,000 every day.
While Trojans are still the most common type of malware, accounting for 58.20% of new malware, this figure is significantly lower than the previous quarter (71.85%). This is not so much due to a drop in number of new Trojans, but more to a substantial increase in PUPs (Potentially Unwanted Programs) during this period.
Attacks on mobile devices have continued to gather momentum over this quarter, though this time they have also targeted the Apple iOS in addition to Android. In the case of the latter, the most notable cases have involved fake antivirus apps and ransomware.
There have also been many notable cases of hacking targeting major companies across different sectors, such as eBay, Spotify or Domino’s Pizza,as well as more attacks by the Syrian Electronic Army (SEA). A security flaw -dubbed Heartbleed– in the OpenSSL library used for encrypting communications made the headlines around the world in April.At the same time, Microsoft ceased to offer support for Windows XP, with serious security implications for users of this OS.
PUPs on the rise
While Trojans are still the most prevalent type of malware (58.20% of new threats), they are losing ground thanks to the rise of PUPs (Potentially Unwanted Programs). In fact, in recent months there has been a notable increase in software bundlers, which install PUPs -without the user’s consent- along with the programs that the user really wants to install.
Trojans are followed a long way behind in the ranking by worms (19.68%), adware/spyware (0.39%) and viruses (0.38%).
Trojans the cause of most infections
Trojans, once again, have accounted for more infections (62.8%) than any other type of malware, although this figure is lower than the previous quarter (79.90%). PUPs are in second place with 24.77% of infections, underlining how these techniques are now being used massively. A long way behind came adware/spyware (7.09%), viruses (2.68%) and worms (2.66%).
Infections by country
The global infection rate during the second quarter of 2014 was 36.87%, a significant rise on recent periods, thanks largely to the proliferation of PUPs. Country by country, China once again had the most infections, with a rate of 51.05%,followed by Peru (44.34%) and Turkey (44.12%).
It’s clear from this ranking that the regions with the highest levels of infections are Asia and Latin America. Spain also has an infection rate above the global average with 37.67%.
On the other hand, Europe is the area with the lowest infection rate, with nine countries ranked among the least infected countries. Sweden (22.13%), Norway (22.26%) and Germany (22.88%) had the lowest rates while Japan, with an infection rate of 24.21%, was the only non-European country in the top ten of this ranking.
The full report is available here.
The post Malware still generated at a rate of 160,000 new samples a day in Q2 2014 appeared first on MediaCenter Panda Security.