
![]()

![]()
Wi-Fi networking is absolutely essential to the modern home. From smartphones to games consoles to intelligent thermostats like Nest, virtually every appliance now requires a wireless internet connection.
As a result, there is all kinds of valuable information being transmitted across your Wi-Fi network – credit card numbers, passwords and sensitive photos and files. Which makes your network a natural target for cybercriminals.
Because you can’t see wireless network signals, you cannot easily tell how far they reach. It is not unusual for your network to extend into the street outside your house – which provides an opportunity for hackers to get connected.
Using basic cracking tools, it is possible to bypass Wi-Fi network security in as little as 10 minutes. It may be that these hackers simply want to use your internet connection to get online – not as serious as stealing your sensitive personal information, but still stealing nonetheless.
The first sign that your Wi-Fi network has been compromised will probably be a general decrease in internet speeds. The more people connected to your network, the more problems you will have loading webpages or streaming videos
If you notice anything strange happening on your network, you must investigate. The first thing to check will be the Wi-Fi router itself.
Log into your router using the username and password supplied when it was installed (they are often printed on a sticker on the rear of the unit). The specifics for each router are different, but you are looking for the Wi-Fi status page which lists all the devices that have connected, or are connected, to your network.
These details may be under a section called Attached Devices, Device List or Home Network for instance.
The list should look something like the image below (we’ve blocked out some of the most sensitive details):
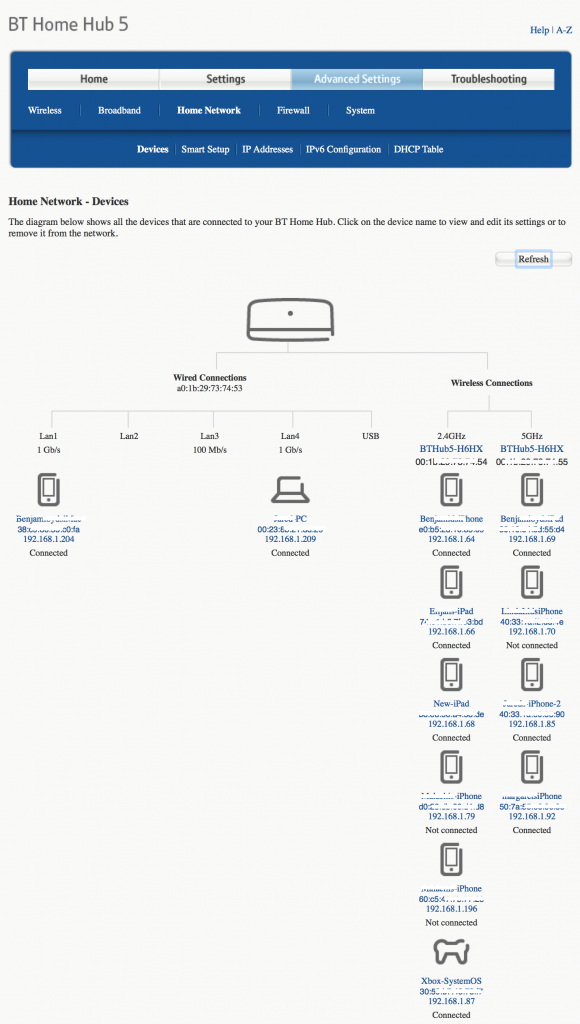
Have a look through the listing, looking for any devices that are unfamiliar. Any devices you don’t recognise indicate a hacker may have compromised your network security.
It is possible that some of the devices have “unfriendly” names that aren’t immediately recognisable, but which are completely legitimate. Make sure you check all of your Wi-Fi-attached devices before panicking!
There are a number of advanced techniques for improving your Wi-Fi network security, like locking down network access to pre-approved devices based on the unique MAC identifier. Far simpler, and almost as effective, is to simply choose a more robust security protocol.
The latest, most secure option is WPA2 as shown below:
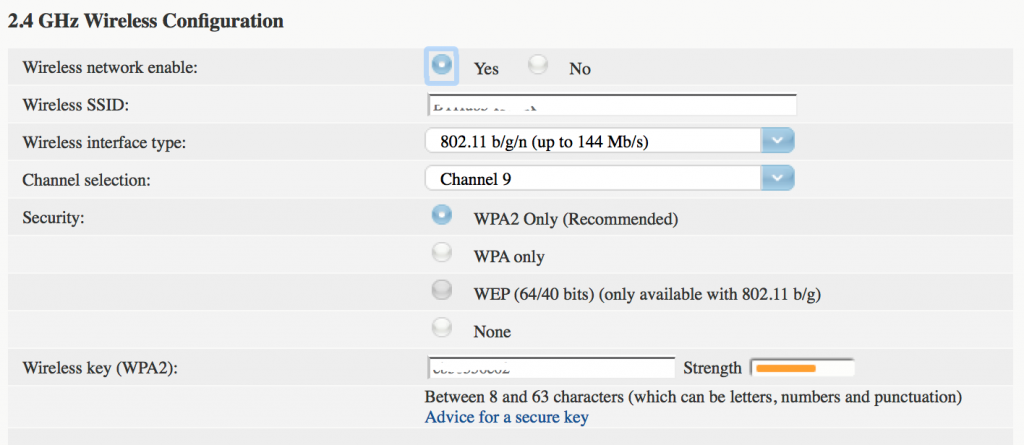
Just remember that if you do change the security protocol setting, you may have to reconnect all of your Wi-Fi devices – but that’s a small price to pay to prevent people cracking their way onto the network.
You should also add a second layer of security to deal with the eventuality that a hacker still manages to break in. A comprehensive security application installed on your PCs and Android phones will help prevent your personal data being stolen. This has the added benefit of blocking viruses and to protect younger members of your family from questionable web content.
you need to stay aware of what is happening on your network to keep the bad guys out. These tips will help you tell if something is wrong and help to formulate an effective response.
In the meantime, download a free trial of Panda Security to protect your PCs while you check your router.
The post How to tell if your Wi-Fi network has been hacked appeared first on Panda Security Mediacenter.
Phishing continues to blight the Internet and is a thorn in the side of companies around the globe. Not only is it one of the most serious problems facing any company with even a minimal activity on the Web, it is also an ever-increasing threat.
 So much so, that a recent study has revealed that in the last year alone there have been more than a million attacks of this nature. This means that on average, a phishing attack is launched every thirty seconds with the aim of defrauding companies and home-users alike. In the case of businesses, the damage inflicted by this onslaught is nothing short of dramatic: the total cost to companies around the world is in excess of 9,000 million dollars, more than 8,000 million euros at today’s exchange rate.
So much so, that a recent study has revealed that in the last year alone there have been more than a million attacks of this nature. This means that on average, a phishing attack is launched every thirty seconds with the aim of defrauding companies and home-users alike. In the case of businesses, the damage inflicted by this onslaught is nothing short of dramatic: the total cost to companies around the world is in excess of 9,000 million dollars, more than 8,000 million euros at today’s exchange rate.
The total cost to companies around the world is in excess of 9,000 million dollars.
Given this situation, in addition to having proper protection, it is more important than ever that companies follow a series of recommendations to prevent falling victim to an attack that could have grave financial consequences. Checking the source of each email you receive and not accessing bank websites from links included in emails are two of the basic precautions you can take to avoid falling into the traps set by cyber-criminals.
What makes these and other similar measures so essential is the dramatic increase in phishing attacks that has taken place over the last year. In the second quarter of 2016 alone, more than half a million unique attacks were identified, that’s a 115 percent increase on the previous quarter. Moreover, the increase with respect to the same period in 2015 is even more alarming: 308 percent.
In the second quarter of the year “Phishing” attacks have been incresing in a 115 %
To counter this situation, it is essential for companies to ensure that their employees are aware that they must only enter confidential data on trusted websites which, as with all secure pages, have an address starting with HTTPS. Phishing attacks are on the rise and they are also evolving. Now, for example, not only are they aimed at identity theft on social networks or taking money from current accounts, they are also being used to steal from e-Wallets.
The post A phishing attack is launched every thirty seconds: 6 tips to protect yourself appeared first on Panda Security Mediacenter.

Malvertising – yet another offspring of the online advertising, has been around since 2008. However, in 2016 we’ve been observing more and more creative ways of hackers trying to compromise your system by injecting malicious or malware-laden advertisements.
They are getting so creative that infected adverts are no longer a threat that comes only from questionable torrent websites.
There are reported cases of malicious codes being able to sneak up into your devices from reputable online advertising networks and webpages. A few days ago even Google acknowledged a fault in their Chrome browser – as reported by Ars Technica, over a two-month span starting in August 2016, a malicious advertising campaign downloaded the Banker.AndroidOS.Svpeng banking trojan on about 318,000 android devices. Even though the malicious installation files were not automatically executed, they have been named names such last-browser-update.apk and WhatsApp.apk – file names that could have been easily mistaken for legitimate ones.
Spotify was recently under fire too – multiple sources such as Engaged confirmed some listeners got not just free music but malicious code too. Some of the confirmed cases state files didn’t even have to be executed in order to cause damage. All three major platforms have been targeted – Linux, Mac and Windows. It is not yet confirmed if the code has been able to affect all three platforms.
It’s not yet that hard to get unnoticed. All reputable advertising networks have strict guidelines for organizations interested on working with them. However, even though advertisers pass rigorous checks, in some cases advertisers can modify the ads after they have been approved. This is particularly easy when the ads are hosted on their own servers. Therefore, seeing a malicious ad should not surprise you and you will have to be prepared.
There is a simple way to not be a victim – remain vigilant. Hackers are after your credit card information, social security number, address and personal information. Just don’t share this information with them! Phishing tactics are getting more and more advanced and you need to stay on top of your game – here’s how;
The post Spotify under fire: Are we entering a new era of malvertising? appeared first on Panda Security Mediacenter.

That hard disks, pen drives and other physical storage devices are an attractive target for cyber-criminals wanting to steal confidential information from enterprises is something that company managers are well aware of. And, in fact, they try to educate their employees about the need to use those tools properly.
However, the now-popular digital cloud, used by businesses to store increasing amounts of sensitive information, must also be taken into consideration when designing a company’s cyber-security strategy. Moving to the cloud has powerful benefits – cost savings, easy access to files from anywhere, convenience, etc.- yet it also poses some risks that must be identified and controlled.
According to a recent study published by the prestigious Ponemon Institute, the majority of businesses have not or do not know if they inspect their cloud services for malware.
The majority of businesses have not inspected their cloud services for malware.
According to the study, while 49 percent of business applications are now stored in the cloud, fewer than half of them are known, officially sanctioned or approved by the IT Department.
While respondents understand the risk of data breaches, nearly a quarter could not determine if they had been breached, and nearly a third couldn’t determine what types of data were lost in the breach(es). Neither do they know how the breach(es) occurred.
This and similar studies seem to indicate that enterprises rely too much in the security measures adopted by cloud service providers themselves and that, all too often, companies leave the protection of their most valuable secrets and assets almost exclusively in the hands of third parties such as Amazon or Slack.
To resolve this situation, CISPE, a coalition of cloud service providers operating in Europe, has published the sector’s first code of conduct aimed at ensuring data security and confidentiality. Compliant cloud infrastructure providers will be able to identify themselves with a ‘Trust Mark’ that will provide additional security assurance for customers, especially corporate ones.
Nevertheless, despite the measures taken by these Internet giants to ensure the integrity of the information stored on their servers, companies and their employees cannot ignore their own responsibility to keep corporate data and documents secure. Just as they take good care of their hard drives and pen drives, they should also take care of the cloud to prevent their data from ending up in the wrong hands.
The post Companies don’t take proper care of the data they store in the cloud appeared first on Panda Security Mediacenter.

Tuesday’s election defied virtually all expert opinion confidently put forth on traditional media channels. As many pundits have since accurately, albeit belatedly, noted, the outcome was a complete rejection of the country’s political establishment. More than that, it was a repudiation of the centralized, elite-driven information network that wrongly believed it still held a monopoly on public opinion. The result of this year’s presidential election is a stark indicator that the dominance of newspapers and cable television has passed, and that the new barometer of the public mood is social media—which Donald Trump understood better than any of the analysts and commentators who predicted his defeat.
![]()

Something as apparently inoffensive as employees keeping up with the lives of ‘celebs’ on the Internet could be far more dangerous than you think for your company’s IT systems. Whether you like it or not, some employees take advantage of dead time (and not-so-dead time) to look for all the latest gossip and news on the Web.
There may not be anything too risky about reading reputable newspapers online to see the latest news or check out your team’s results (although there have been cases of malware-laden ads in online newspapers). However, gossip columns and other celebrity stories have become a serious threat for the security of computers and mobile devices.
Cyber-criminals are well aware of the interest generated by the lives of the stars, which is why they have come up with specific strategies to bait users into downloading malicious programs on their computers when they access this content.
Cyber-criminals are well-aware of the interest generated by the lives of the stars.
The first step that the average user takes when looking for information about celebs is to ask Google. Yet some searches are more risky than others. Some famous people and related events offer more potential for attackers, as was the case recently with Brad Pitt and Angelina Jolie after their separation became public.
New film or music releases are also a popular weapon for criminals whose aim is to infect users’ computers and devices looking for passwords and other confidential information. Whenever a new story breaks, searches related to those involved increase dramatically and it becomes easier to infect users with malware hidden on malicious websites with related stories.
New film or music releases are also a popular weapon for criminals.
In order to minimize the threat, apart from having an efficient policy for controlling the way your employees use your company’s devices, the most effective measure is awareness. Firstly, your company’s workers should learn to distinguish between trusted pages and those that could potentially be used by criminals to infiltrate your systems. They should also avoid any links to illegal downloads, whether direct or via ‘torrent’ (highly in demand when a new film or song is released).
Of course, you can get an additional guarantee of protection against malware that exploits users’ fascination with celebrity news by having a security solution to protect all your devices, such as Panda Security’s corporate solutions.
The post Searching for celebrity news on Google can be dangerous for your computer appeared first on Panda Security Mediacenter.

Warning – the following article may contain spoilers
Charlton Brooker’s Black Mirror television series has become something of a phenomenon thanks to its almost prophetic predictions about society and technology. Set in the very near future, Black Mirror borrows technology stories from the media, and imagines the worst possible outcomes to create a bleak view of the world that we are creating today.
What makes Black Mirror so compelling is that the storylines are simultaneously outlandish and plausible. More impressive is the fact that some of the predictions have actually come true.
As the third season of Black Mirror airs on Netflix, it’s time to consider how close to reality the latest round of predictions really are.
Hackers take control of a Kenny’s laptop, and use the webcam to secretly film him in a compromising situation. Kenny then receives a string of ransom texts to his phone, demanding he follow the supplied instructions or risk the embarrassing video being leaked to his friends, family and the rest of the world online.
The reality is that malware already exists to hack into computers, activating the web cam remotely. And like most malware, you probably won’t even notice anything is wrong until you receive a ransom demand or similar.
To prevent being spied on, some people take the extreme step of taping over their webcam – a method favoured by Facebook CEO Mark Zuckerberg.
Just as effective (and much easier to manage) is to protect your computer with a robust antivirus application like Panda Security that can detect and block malware before it can install itself.
The Metropolitan Police investigate the brutal murder of a journalist in London. All the evidence seems to point to the woman’s husband, but of the detectives assigned to the case suspects that social media may also play a part.
As more deaths follow, it is discovered that a swarm of robot bees has been programmed to kill anyone trending online with the hashtag #DeathTo. The mob mentality of social media users is unwittingly singling out individuals for death.
The robot bees may not yet exist, but the vicious hashtags that accompany each attack in Black Mirror certainly do. Cyberbullying is widespread, and really does cause lasting damage to the victim, leading to stress, depression and, in extreme cases, suicide.
Online bots that respond to trending hashtags already exist, helping to spread viral messages, or trigger specific actions for companies that monitor social media. The artificial “intelligence” to drive a swarm of robot bees is ready, even if the technology is not.
To avoid attracting the attention of trolls online, parents should consider installing a comprehensive internet security package like Panda Gold Protection (you can download a free trial here). This will allow you to block access to sensitive sites – including social media – protecting your family against simple, unintentional mistakes becoming headline (life-threatening) news.
Black Mirror makes for uncomfortable viewing – mainly because it is so close to the reality we know. The dire outcomes of each episode are just realistic enough to create a terrifying view of the future. Fortunately you can avoid starting some of these chains of events with some effective internet security software.
For more help and advice about staying safe online, please get in touch.
The post Black Mirror – How much is already real? appeared first on Panda Security Mediacenter.

Can you imagine a system that could not be hacked? That repelled those who tried? This apparently impossible dream has been pursued by developers for decades, without much success. In theory, this is perfectly possible; in practice, however, it demands too much effort and program code would be too long.
However, the HACMS project has taken a very big step to fulfill that dream. According to information recently revealed to the public, in the summer of 2015 the U.S. Defense Advanced Research Projects Agency (DARPA) conducted an experiment consisting of subjecting an unmanned military helicopter equipped with a new kind of security mechanism to attack by a team of six hacking experts. The helicopter was impossible to hack into, despite the hackers had the advantage of having been given access to some parts of the drone’s computer system.
The security mechanism they were testing is based on an old concept that only recently is becoming a reality: formal verification, a style of software programming that ensures code integrity. With the technology that we have today, it was absolutely impossible to hack into key parts of the helicopter’s computer system, its code as trustworthy as a mathematical proof.
Writing such strong computer code has been the aspiration of every expert since the inception of computer science. For a long time it seemed hopelessly out of reach, but the technological advances made by military and academic institutions, in collaboration with large multinationals such as Microsoft and Amazon, have made the idea of creating hacker-proof code a closer reality.
The technological advances made by military and academic institutions, along with tech giants,
have pulled hacker-proof code into a closer reality.
 The ongoing efforts towards developing unhackable code are being spurred by the need to strengthen security in our increasingly interconnected world, with the Internet of Things becoming a reality in households, cities and almost every object that surrounds us.
The ongoing efforts towards developing unhackable code are being spurred by the need to strengthen security in our increasingly interconnected world, with the Internet of Things becoming a reality in households, cities and almost every object that surrounds us.
The promising results of the HACMS project have already been replicated in other areas of military technology, such as satellites and driverless trucks, and Microsoft is working on two projects based on similar techniques: one aimed at securing complex cyber-physical systems such a drones, and another one, codenamed Everest, to create a verified version of HTTPS that allows users to browse online safely.
It is difficult to think that we are witnessing the beginning of the end of hacking, but it is true that we are one step closer to making things much harder for cyber-criminals by designing programs which, with today’s technologies, are impossible to tamper with.
The post Are we closer to hacker-proof computer code? appeared first on Panda Security Mediacenter.

On November the 2nd we witnessed a new spam campaign delivering emails each with a Word document attachment targeting UK companies. Each email message had the subject “Companies House – new company complaint” and the Word document attachment was titled “Complaint.doc”. When users open the document, this is what they see:
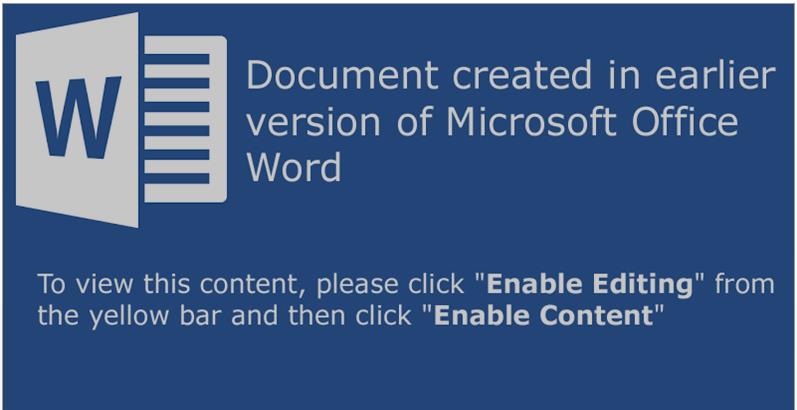
If the user follows the instructions given, the macro in the document will be executed. It will download a file called dododocdoc.exe which will be saved in %temp% as sweezy.exe and then executed. This file is a variant of the TrickBot malware family. Once executed it will install itself in the computer and will inject a dll into the system process svchost.exe. From there it will connect to the command and control server.
This has not been a massive campaign, but it has been targeted to UK companies – we’ve just seen a few hundred e-mails to our clients, and all of them were protected proactively without needing any signature or update. However taking a look at the potential victims, all of the emails were to companies, no home users were targeted, and it turns out that most of them were to businesses in the UK. There were 7 cases in Spain, and one in Belgium, Ireland and Thailand. The campaign was short, the first case happened at 10:55am and the last one at 12:11pm (GMT).
The macro uses PowerShell to execute the malware, which is a common technique that is becoming more and more popular recently, being used in ransomware attacks or even to infect Point of Sale terminals.
From Panda Security we recommend that businesses ensure all software is updated, have a reputable security solution in place and hold regular staff security awareness training.
The post TrickBot, new spam campaign against companies appeared first on Panda Security Mediacenter.