Many of us have found ourselves in situations in which we need Wi-Fi connection and are unable to find it easily. Since we’ve become used to being connected to safe and steady Wi-Fi networks at home or in the office, it can become frustrating and inconvenient when we’re unable to establish a quick connection and gain secure online access.
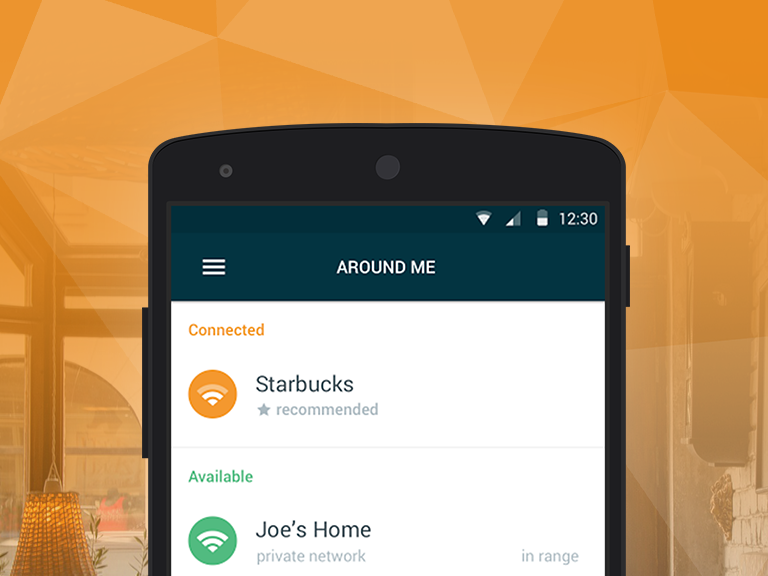
For those seeking a fast, reliable and secure Wi-Fi connection, we’re happy to introduce you to Avast Wi-Fi Finder. Our new app gives you the opportunity to have a fast connection regardless of your location while continuously providing you with privacy and security. Whether you’re at the gym, a hotel, cafe, bus station or library, Avast Wi-Fi Finder has got you covered.
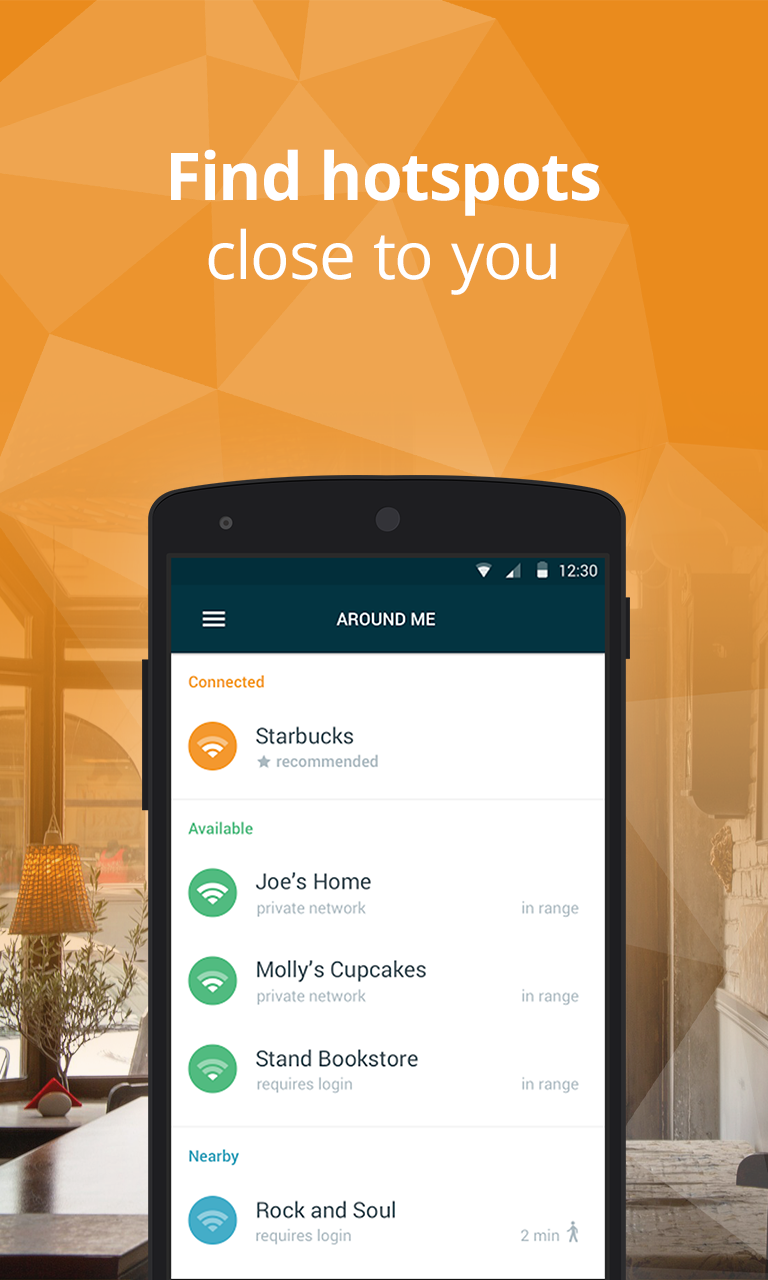
With Avast Wi-Fi Finder, you’re not limited by your data plan – instead, the app allows you to save on funds that would otherwise be spent on establishing a mobile Internet connection. No longer will you be stuck having to purchase a refreshment at the nearest cafe or register for a service in order to connect to fast, reliable Wi-Fi networks – the passwords of our recorded Wi-Fi networks are stored and provided to you.
Getting to know the app
Using Avast Wi-Fi Finder, the following features are at your fingertips:
- Connect to the fastest, most secure hotspots around. Avast Wi-Fi Finder helps you automatically connect to Wi-Fi networks nearest to your location, helping you save on monthly bills and roaming fees.
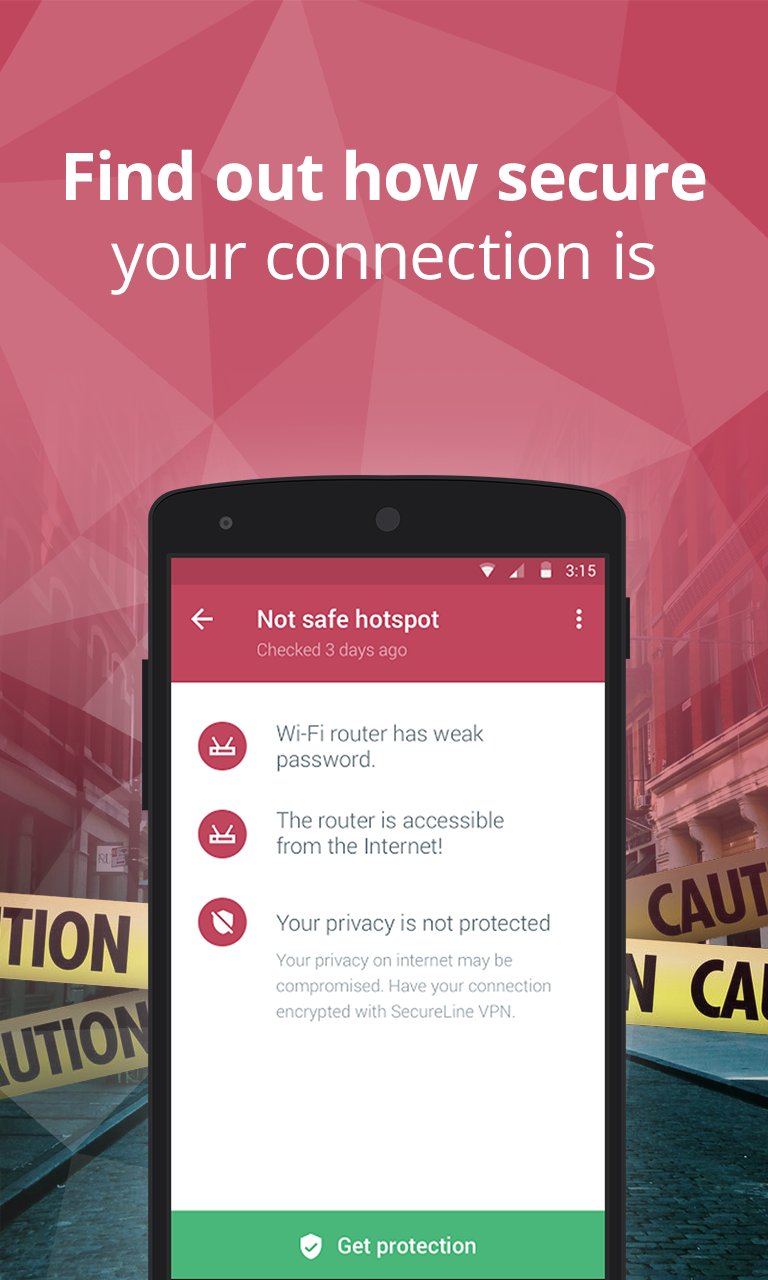
- Get speed and privacy. There’s no need to compromise on your security. Avast Wi-Fi Finder checks the security ratings of each network and keeps you protected while you browse, chat, or email away.
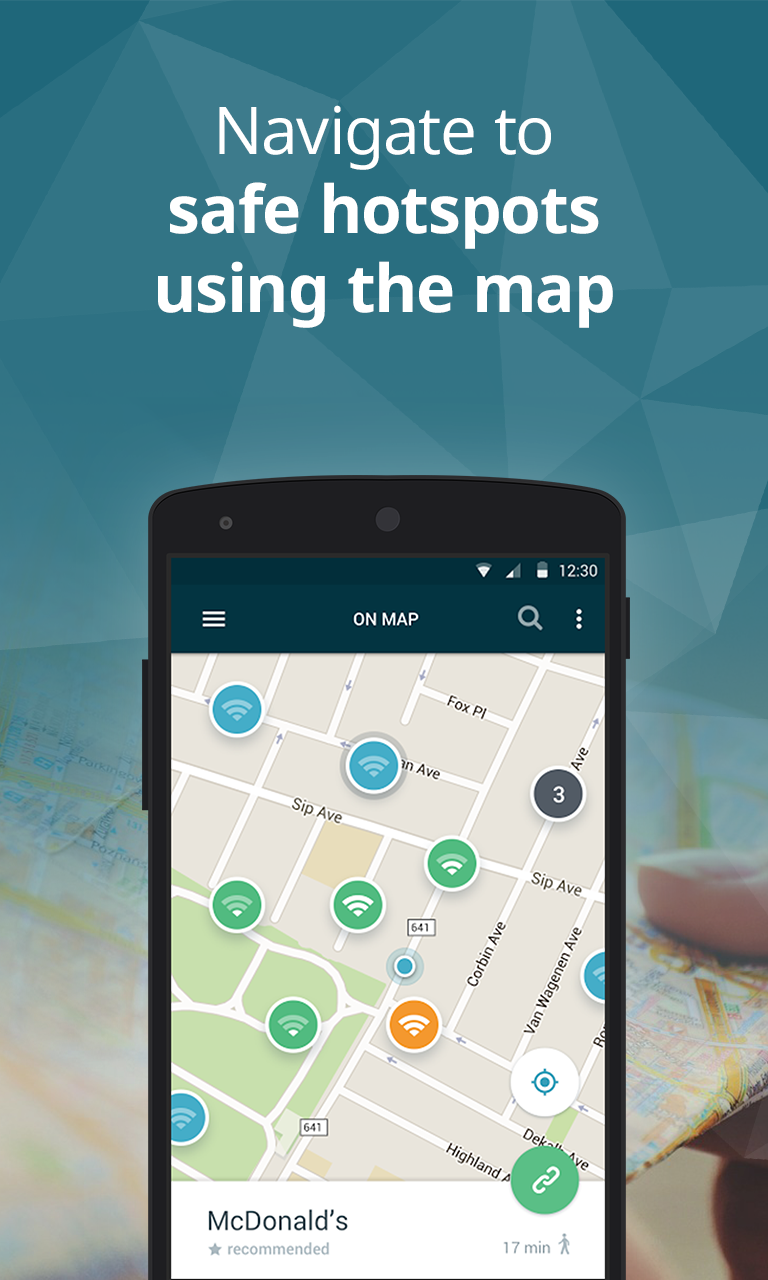
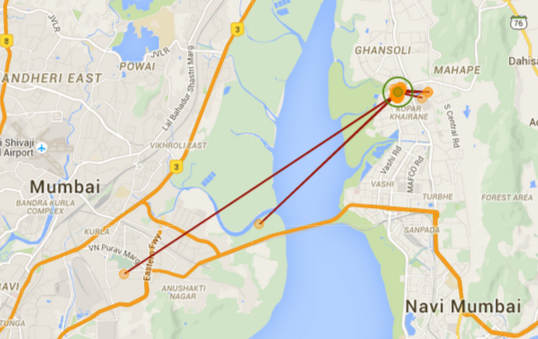
- Follow your map and you’re set to go. The app’s user-friendly map allows you to navigate to a widespread collection of fast, reliable hotspots recommended and crowdsourced by people just like you from all around the world.
In just a few simple steps, you can become one of the beta testers who help us make Avast Wi-Fi Finder (and other Avast mobile apps) the best that they can be. Read through our guide to get started in the Avast Android beta program.
Since the beta version of Avast Wi-Fi Finder has only recently been launched, we’d like to ask our users to be patient, as certain locations may not yet be filled with available Wi-Fi networks. As our community of beta testers continues to grow, the size and quality of our network database will do the same. To speed up this process, we encourage our beta testers to add available Wi-Fi networks to locations as they find them. Get started by becoming a tester for Avast Wi-Fi Finder on Google Play!
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()