Is something not right with your browser, but you can’t quite figure out what?
Does your Chrome browser seem a little “off”, but you can’t figure out why? Maybe it’s eFast.
Here’s another reason to slow down when installing software, especially free software. A new Potentially Unwanted Program (PUP) disguised as the Google Chrome browser is sneaking onto users computers bundled with legitimate software, hidden deep within the ‘Custom’ or ‘Advanced’ settings that most people skip over. Once installed, eFast, as it has been called, serves up ads and tracks your online activities and sells personally identifiable information to advertisers.
“Read the installer screens to make sure what they actually install,” warns Michal Salat, researcher in the Avast Virus Lab. ” The Next->Next->Next->Done approach is exactly why we deal with PUPs daily. If there isn’t an option not to install some additional software, terminate the installer immediately. Better safe then sorry.”
Researchers at Malwarebytes says that eFast actually installs a new browser rather than hijacking your existing one. If you already have Chrome installed, it will replace it making itself the default browser. The fake browser uses the same source code for the user interface as the real thing making it difficult to tell the difference. It is so tricky that it even replaces shortcuts on your desktop that look similar to Google Chrome.
In addition to all that, eFast hijacks some file associations, so that it can open as many times as possible therefore having the opportunity to show you more ads! If you open a file like JPEG, PDF, or PNG, it will be opened with eFast, resulting in pop-ups, more ads in your searches, and other adware. You can see the list of file associations on Malwarebytes security blog.
How to find out if eFast is on your computer
Open your browser and type in chrome://chrome. The authentic Chrome browser will take you to the ‘About’ section and check if your browser software is up-to-date. It looks like this.
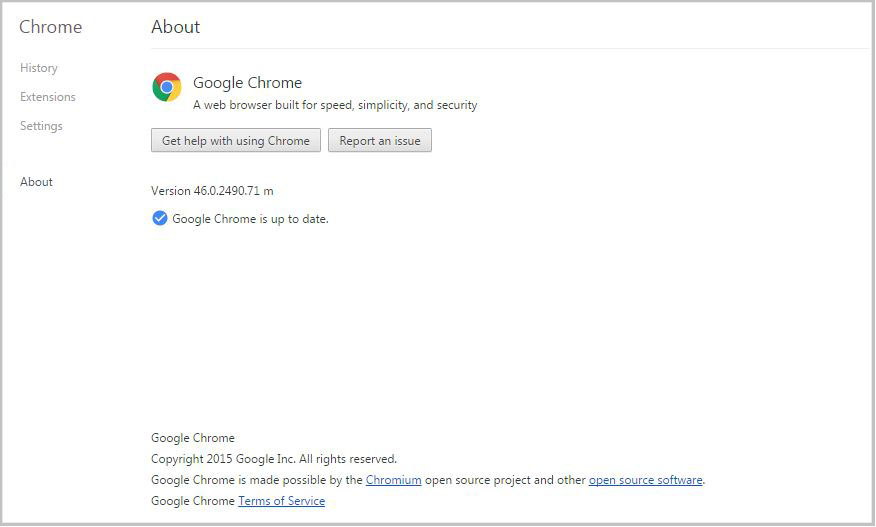
If you have a fake version of Chrome, then you will be taken to a fake About page, get an error, or the link won’t work. In that case, check out the removal instructions on PCrisk.
eFast is classified as a Potentially Unwanted Program, also known as a PUP. PUPs are annoyances like search bars, intrusive adware, etc. that Avast does not detect by default. However, the option can be enabled.
How to turn on PUP detection in Avast
- Open the Avast program and go to settings
- Open Active Protection
- Click Customize next to Web Shield
- Go to Sensitivity and put a check mark beside PUP and suspicious files
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()