
via: USA Networks Mr. Robot airs on Wednesdays at 9/10 central on USA
This week’s episode answered A LOT of questions — we met the infamous White Rose and found out why the Dark Army backed out of the planned takedown of Steel Mountain a few episodes ago, we found out why Cisco blackmailed Ollie into infecting AllSafe with malware and we (kind of) found out who Mr. Robot and Darlene really are! Although many of my questions were answered in this episode, I also found myself asking “what?” and “why?” throughout it. What is a honeypot? What is reverse engineering and why is Tyrell talking to Mr. Robot? Why is Tyrell happy about Fsociety hacking E Corp?
I turned to my colleague Ivan Jedek, malware analyst at Avast, to get some answers to my questions.
At 11 minutes into the show, Gideon has a meeting with Tyrell to tell him that AllSafe is determined to find the hackers that hacked into E Corp. He explains to Tyrell that AllSafe has air gapped E Crop’s private network, implemented a honey pot and reconfigured all firewalls. Tyrell cuts Gideon off to question the honeypot and Gideon explains that a specific server was involved in the last FSociety hack, CS30. He explains that if there is a chance hackers are in the network, honeypot will ensure they cannot cause damage. They will log in to the decoy server they set up thinking they are in they’re in E Corp’s main network — he is personally keeping tabs of all the traffic.
Stefanie: What is a honeypot and what is it used for?
Ivan: A honeypot is a trap to catch cyberattackers. It comes from the idea that you can lure a bear by attracting it with a honey pot. As Gideon explained in this scene, a honeypot is a decoy. In this case, Gideon set up a honeypot to look like an E Corp server appearing to be connected to the company’s network. In reality, it is isolated and, like Gideon explains to Tyrell, is being monitored for unauthorized access.
At 14:26, we see the AllSafe employees frantically trying to get to the bottom of the malware attack that hit them and Elliot tells Ollie he is trying to reverse engineer the malware.
Stefanie: What is reverse engineering? Is it something that you guys in Avast’s Virus Lab do often?
Ivan: Reverse engineering is when you take something apart to see how it was built or put together. In this case, Elliot is disassembling the malware to see what it does and where it came from. We do reverse engineer malware in the Virus Lab, but we don’t wear lab coats when we do this! If we receive a virus sample that our system didn’t automatically detect, for example, then we like to reverse engineer the sample to find out how it works — then, we can create a detection for it to send to our users. Sometimes we reverse engineer malware because we find interesting or to observe how a certain malware family is progressing
During Elliot’s meeting with White Roe, Elliot learns that by targeting Terry Colby, he opened a vulnerability and raised Gideon’s suspicion. Elliot puts the pieces of the puzzle together and realizes that the Dark Army targeted AllSafe with malware to monitor Gideon, which lead to the Dark Army’s discovery of the honeypot, which is why they pulled out of the deal to take down Steel Mountain. When Elliot leaves the meeting, he is on a mission to take down the honeypot so that FSociety can access the Steel Mountain network to take down E Corp. Elliot goes back to the AllSafe office and in the meantime, Darlene has sent 100 MMS to get Gideon’s phone, which forces him to charge his phone and leave it unattended while a video made by FSociety plays in the AllSafe conference room. While everyone is watching the video, Elliot gets the security token and logs into Gideon’s account to submit a request to take down the honeypot.
Stefanie: Why send all those MMS? What is a security token?
Ivan: Elliot had Darlene send Gideon’s 100 large MMS files to overload his phone and drain his battery. This caused Gideon to charge his phone and allowed Elliot to take it while the video distracted the company. A security token is a temporary password that is sent to a device. The token helps prove one’s identity, as it is sent to a separate device. In this case, Gideon set up two-factor authentication on his AllSafe account so that an additional, temporary password would be sent to his phone whenever anyone attempted to log into his account.
Stefanie: Interesting! Do you also happen to know the reason why Tyrell and Mr. Robot met?
Ivan: That I do not know! I guess we will have to wait till next week to find out.
What did you think of this week’s episode? Let us know in the comments below!
![]()
















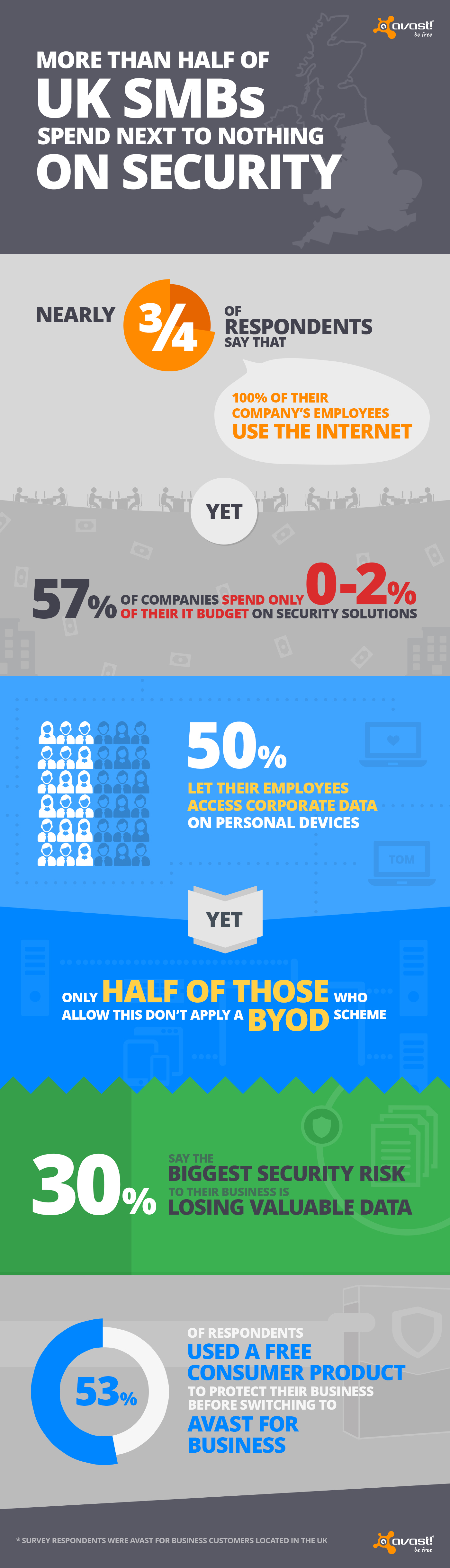 In February, Avast launched the world’s first free, easy to use, cloud-managed security offering, Avast for Business, protecting SMBs from viruses and cyberattacks. We conducted a survey amongst our Avast for Business users in the UK to gain further insight into how local SMBs handle their security.
In February, Avast launched the world’s first free, easy to use, cloud-managed security offering, Avast for Business, protecting SMBs from viruses and cyberattacks. We conducted a survey amongst our Avast for Business users in the UK to gain further insight into how local SMBs handle their security.