Malware Writers Can’t Keep Their Hands Off Porn
In April, we reported on a porn clicker app that slipped into Google Play posing as the popular Dubsmash app. It seems that this malware has mutated and once again had a short-lived career on Google Play, this time hidden in various “gaming” apps.
For your viewing pleasure
The original form of this porn clicker ran completely hidden in the background, meaning victims did not even notice that anything was happening. This time, however, the authors made the porn a bit more visible to their victims.
The new mutation appeared on Google Play on July 14th and was included in five games, each of which was downloaded by 5,000-10,000 users. Fortunately, Google reacted quickly and has already taken down the games from the Play Store.
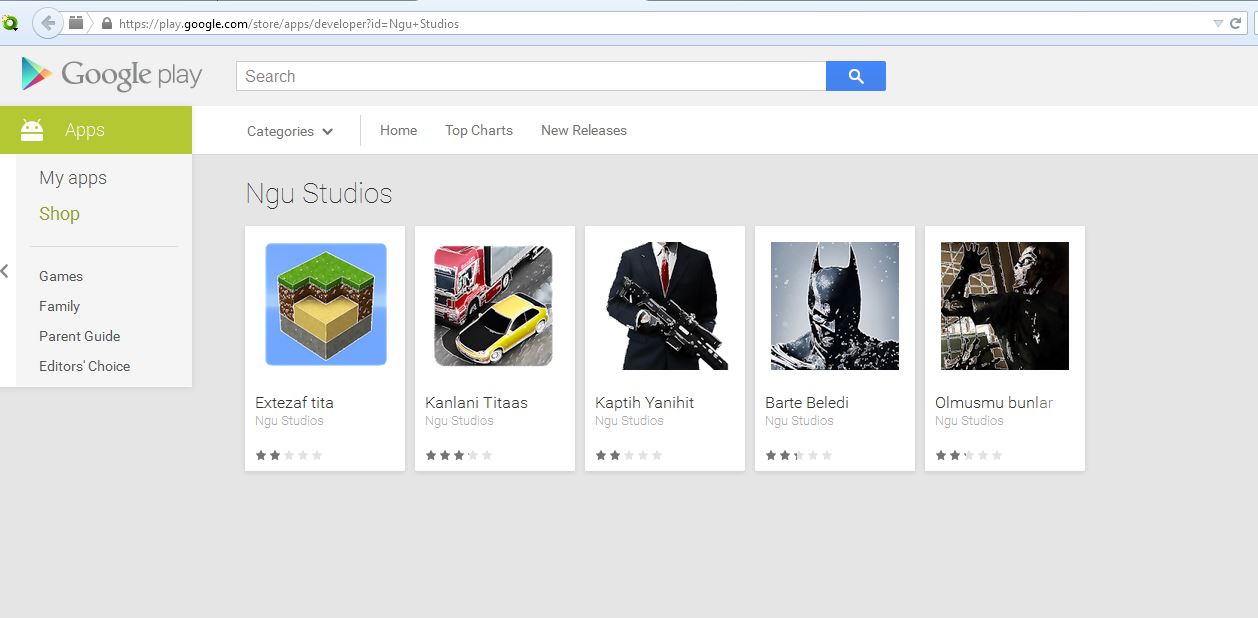
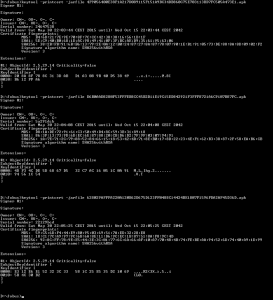
The selection of “gaming” apps affected by Clicker-AR malware on the Google Play Store.
Once the app was downloaded, it did not really seem to do anything significant when opened by the user. However, once the unsuspecting victim opened his/her browser or other apps, the app began to run in the background and redirect the user to porn sites. Users may not have necessarily understood where these porn redirects were coming from, since it was only possible to stop them from happening once the app was killed.
May I?
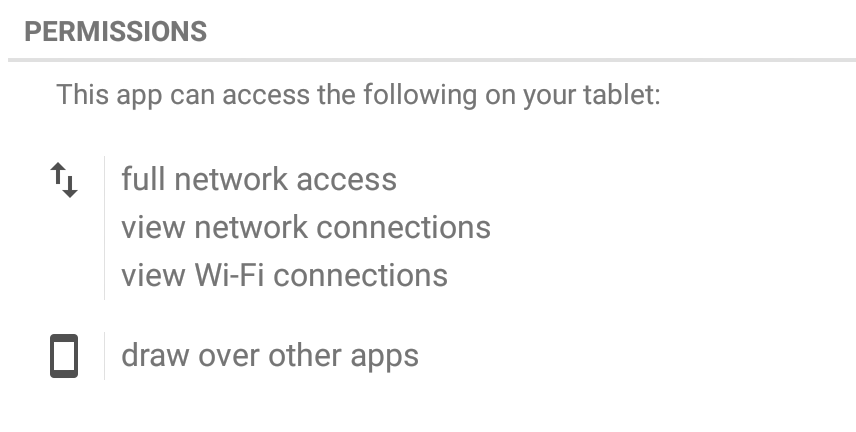
This new mutation, which Avast detects as Clicker-AR, requested one important permission that played a vital role in helping the app do its job. The app requested permission to “draw over other apps”, meaning it could interfere with the interface of any application or change what victims saw in other applications. This helped the malware put its adult content in the forefront of users’ screens.
Let’s play “Clue”
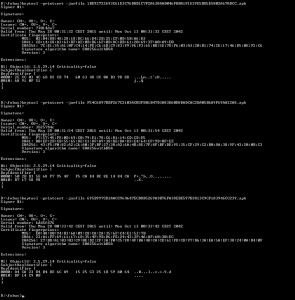
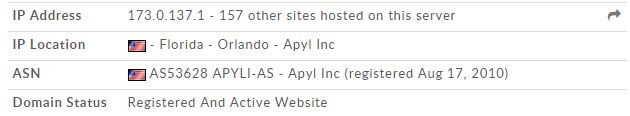
We did not immediately realize that the group behind Clicker-AR was comprised of the same folks from Turkey behind the fake Dubsmash app. Then, our colleague Nikolaos Chrysaidos dug a bit deeper and was able to connect some clues to figure out who was behind this piece of malware. He noticed that the fake Dubsmash app and the new apps shared the same decryption base64 code for the porn links. We then noticed that they shared the same function with the same name “bilgiVer”, which means “give information” in Turkish. Finally, the old and new apps used the same DNS from Turkey. Not only did they have a server in Turkey, but they also now made use of an additional server in the U.S. – it seems they made some investments using their financial gain from April!
Bye bye, porn!
As mentioned above, these malicious apps have already been removed from Google Play and Avast detects the malware as Clicker-AR. The following games are infected with Clicker-AR: Extezaf tita, Kanlani Titaas, Kapith Yanihit, Barte Beledi, and Olmusmi bunlar. If you have any of these apps installed on your device, we suggest you remove them (unless you, um, enjoy them) and make sure you have an antivirus app, like Avast Mobile Security, installed to protect yourself from mobile malware.
Follow Avast on Twitter where we keep you updated on cybersecurity news every day.
![]()