At the end of this month, Avast will end support for our older consumer versions of Avast Antivirus. Those are: Avast Free Antivirus, Avast Pro Antivirus, Avast Internet Security, and Avast Premier.

Update to Avast 2015 for maximum protection.
A good antivirus program is a necessity to protect your Windows PC from malware attacks, to keep your computer running smoothly, and to protect your online identity and personal data. Over the past 3 years, Avast engineers have improved our database of known virus definitions, the mechanism in which zero- day and widespread malware are detected, and the frequency of streaming updates sent to our customers. Avast 2015, with its unique Home Network Security feature which scans your home network for potential risks, is our best performing security product yet.
After May 31st, 2015, Avast will no longer provide security patches or technical support for versions 8.0.1497 and lower. Security updates patch vulnerabilities that could be exploited by malware, endangering your machine and the data on it. Please update to the latest version so you can receive regular security updates and benefit from the enhanced features and higher detection rates that protect your computer from malicious attacks. This update is also recommended because the latest version is compatible with Windows 10.
If you are running an older version of Avast, you can easily move to the latest version of Avast 2015.
How to check for the latest version and do a program update
If you need to update later, here’s a quick way to do it.
- Right click on the orange Avast ball icon in the system tray.
- Select Update from the menu and then click Program.
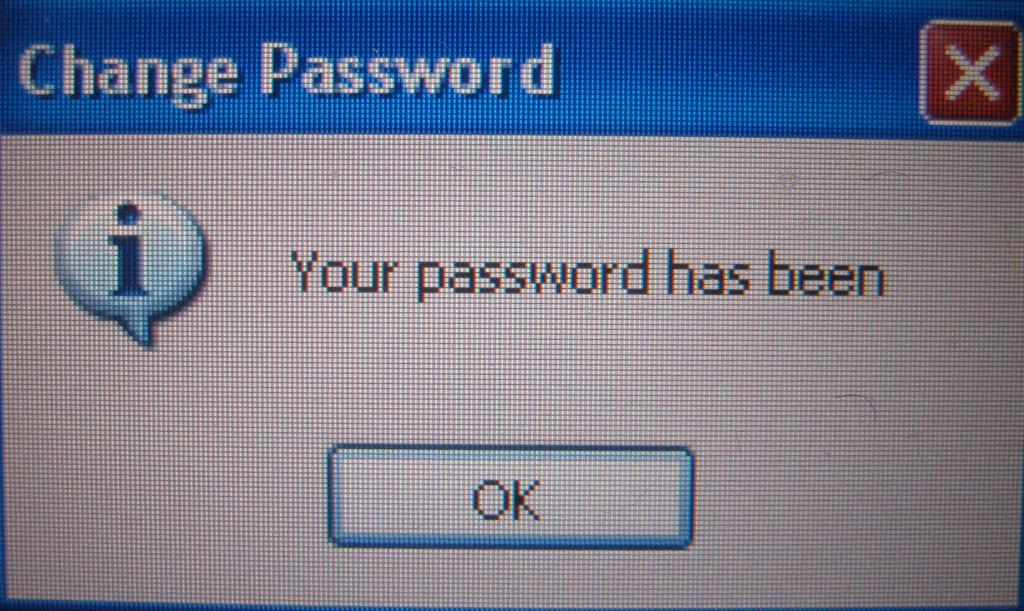
The update screen in the Avast user interface shows you the overall progress of the program update. When it’s done you will be asked to restart your computer. Click Yes to reboot immediately. Once the computer is restarted, information about the update may appear. If you are using a paid subscription, then your protection will be valid for the remaining period of your subscription.
Why to upgrade
- Better detection rates
- Easier technical support
- We fixed bugs and problems that still might exist on your current version
- Receive further program updates to ensure best protection
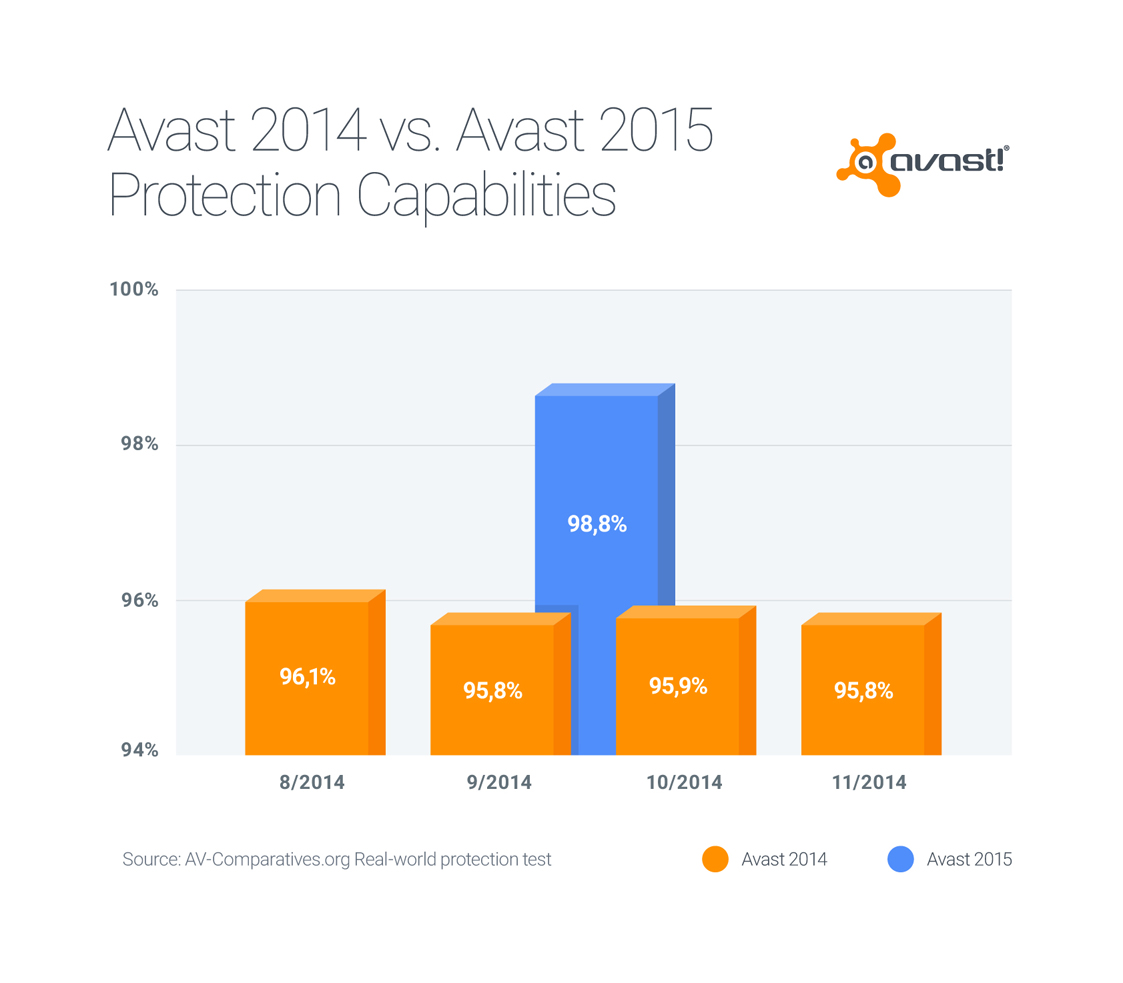
Avast 2015 has better detection rates than older versions. Update as soon as possible for maximum antivirus protection.
If you prefer an older version of Avast and require technical support, you will be asked to update first before we can assist you. There will be no patches issued and technical support will end on May 31st, 2015.











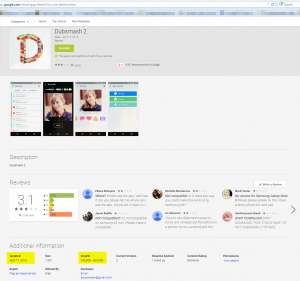 The answer is a resounding YES. The Avast Virus Lab gives us an example from a trusted download source, Google Play: A
The answer is a resounding YES. The Avast Virus Lab gives us an example from a trusted download source, Google Play: A  Once you decide that you do want to protect your Android device, you can be confident in Avast Mobile Security, Avast’s free security app available on Google Play. A survey by AV -Comparatives said that
Once you decide that you do want to protect your Android device, you can be confident in Avast Mobile Security, Avast’s free security app available on Google Play. A survey by AV -Comparatives said that  One of the challenges with using a smartphone for so many activities, is that the battery gives out before we do. Our new free app
One of the challenges with using a smartphone for so many activities, is that the battery gives out before we do. Our new free app  Avast Battery Saver has only been available for a month or so but already 200,000 customers have downloaded it from the Google Play Store. For Earth Day we
Avast Battery Saver has only been available for a month or so but already 200,000 customers have downloaded it from the Google Play Store. For Earth Day we  Small and medium-sized businesses (SMBs) run the risk of data breaches just like there Enterprise cousins. Luke Walling, the General Manager of Avast for Business, explains that the biggest threat to SMBs is not actually hackers sitting somewhere far away.
Small and medium-sized businesses (SMBs) run the risk of data breaches just like there Enterprise cousins. Luke Walling, the General Manager of Avast for Business, explains that the biggest threat to SMBs is not actually hackers sitting somewhere far away.  Speaking of Avast for Business, our new disruptive free security offering for SMBs has 75,000 new customers in just 2 months. If you have a start-up, a small business, if you work in a school or non-profit organization, then
Speaking of Avast for Business, our new disruptive free security offering for SMBs has 75,000 new customers in just 2 months. If you have a start-up, a small business, if you work in a school or non-profit organization, then  Our researchers are constantly surprised by the creativity of malware authors. Recently, they found a new way
Our researchers are constantly surprised by the creativity of malware authors. Recently, they found a new way  Most people have security protection on their computers. That’s great when there are things like the banking malware we wrote about. With all that great protection why is it that they don’t trust the warnings? The Avast Virus Lab explored
Most people have security protection on their computers. That’s great when there are things like the banking malware we wrote about. With all that great protection why is it that they don’t trust the warnings? The Avast Virus Lab explored 

