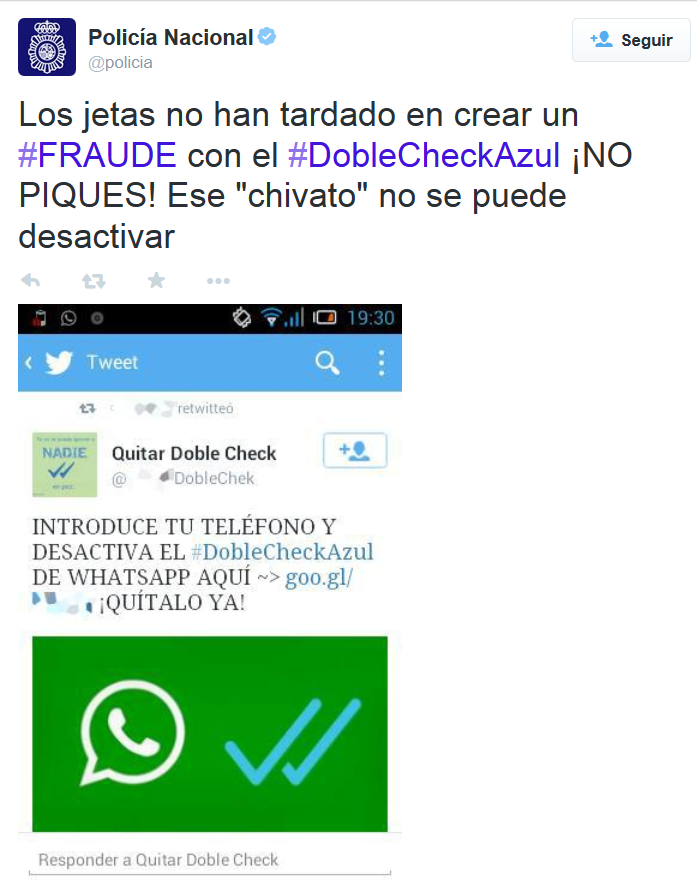
Someone is spying on your company’s emails. Probably in your office names like Yesware, Bananatag or Streak don’t ring a bell, but they know a lot of things about you, and how your corporate email is managed.
Because of these three services, anyone that sends an email to your corporate account might know when, where and with what device was the email read. So, all this information is known by the sender and also by these tracking tools.
How do these applications work? Simply insert a transparent 1×1 image into an email, and then notifies the sender where and when that email has been read.
Is like this that some companies sneak into your office’s privacy to find out if you are ignoring them, and taking, as they are already in, any information about your employees habits. Now, thanks to a Chrome extension you will be able to know who is using your email as a Trojan horse to snoop in your business.
Its name: Ugly Email. This tool alerts the user which emails in his inbox are being tracked by one of these three services.
If you want to use Ugly Email in your office computer, you just need to do is follow this link to the Chrome extension and click on “Add to Chrome”. From that moment on, Ugly Email will allow you to know which emails are being tracked.
It will mark the emails containing a tracking pixel with an eye icon next to the subject heading.
As Ugly Mail’s creator, Sonny Tulyaganov, explains, this tool detects the tracked emails but doesn’t store, save, or transmit any data from your email account; everything takes place on the user’s computer.
But for now the extension Ugly Email has its limitations: it is only available for Chrome, it only works with Gmail and it only effective detecting emails tracked by Yesware, Bananatag and Streak, the three more popular tools but not the only ones.
However Tulyaganov says that Ugly Email will be soon available for Firefox and Safari, the default browser in Apple’s operating system. He also indicated that it will continue adding more tracking services in the future.
This extension won’t prevent others to track the emails they send to your corporate account, but at least you will know who wants to know the time you read the email and from where. Stop it then, is on you.
The post Ugly Mail: How to know if your emails are being tracked appeared first on MediaCenter Panda Security.