Facebook has changed hugely over the years – remember ‘Pokes’? – and today’s sharing machine, with its videos, its news and its scams, is very different from the bare site Mark Zuckerberg launched.
Naturally, each new ‘feature’ has also brought new privacy worries – and security-conscious users should revisit their profile with our detailed guide to ‘maxing’ privacy on Facebook.
But some things haven’t changed – namely, the Facebook scams. It’s not that cybercriminals are unoriginal – it’s just that there are a few Facebook scams which work again and again, and all the criminals need to do is vary them slightly to keep money rolling in.
ESET Senior Research Fellow David Harley says, “While hoaxes may not seem the most dangerous aspect of online life, the migration of old hoaxes and new variations from email to social media does have some serious implications, as people Like and Share links without checking because they seem to come from likeminded and trusted friends.â€
“The more FB friends you have, the more you’ll see these reverberate. You may not worry about political propaganda, but medical hoaxes and semi-scams can be a literal threat to health. “
ESET’s Social Media Scanner offers a quick, free way to check out if that news story on Facebook is true – or a scam. It never hurts to be cautious, though – and here are five classic scammy and spammy posts you should NEVER click.
 ‘Help, I’ve been mugged abroad’
‘Help, I’ve been mugged abroad’
Your friend or family member has lost their phone – so it makes sense they’d contact you via Facebook for help. Usually the story goes that they have been mugged or are in hospital – but it’s one of THE classic online scams, and one of the common uses cybervillains put hijacked Facebook accounts to. ESET’s Harley offers detailed tips on spotting the scam – known as ‘Londoning’,  due to early versions being used on Americans. Harley quotes a typical text: “I hope you get this on time, I made a trip to Manila(Philippines) and had my bag stolen from me with my passport and personal effects therein. The embassy has just issued me a temporary passport but I have to pay for a ticket and settle my hotel bills with the Manager.â€
“I have made contact with my bank but it would take me 3-5 working days to access funds in my account, the bad news is my flight will be leaving very soon but i am having problems settling the hotel bills and the hotel manager won’t let me leave until i settle the bills, I need your help/LOAN financially and I promise to make the refund once i get back home, you are my last resort and hope, Please let me know if i can count on you and i need you to keep checking your email because it’s the only way i can reach you.â€
Naturally, people worry – but it’s not your friend. Someone has hijacked their account. Harley offers five steps to take in a post here – starting with “Be suspicious†and “Verify.â€
 ‘See who has been looking at your Facebook profile’
‘See who has been looking at your Facebook profile’
Facebook will NEVER introduce a feature that allows people to see who has looked at their profile – with the number of people who surreptitiously look up old (or potential new) flames it would probably cause World War III.
Beware – it’s a classic scam post, along with variations on real new Facebook features, or fake ones such as turning your profile pink (another bizarrely long-lived scam).
Links offering early access to features such as Facebook’s A Look Back video, or upgrades to Timeline can also be scams, as reported here. The key warning sign is that you are directed outside Facebook – look at the URL.
If Facebook was ‘upgrading’ you, it would do so within Facebook. As soon as you see an external site URL, close the window – and do not install any app. In many cases, scam videos will install a ‘rogue’ Facebook app to spread rapidly via the network – but as reported by We Live Security here, such scams can, in the worst case scenario, lead to tainted sites which infect users with PC malware.
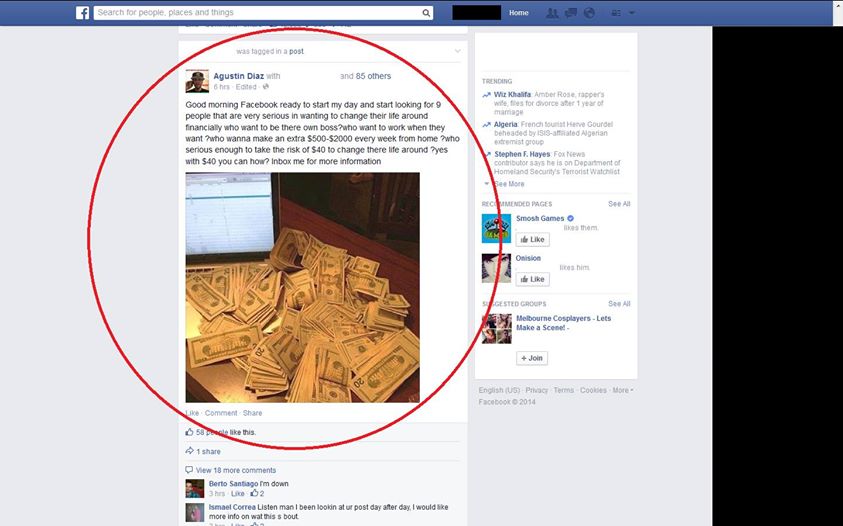
If I get a million Likes….
What’s the harm in “Liking†a page if it’ll get his girlfriend to marry him? Not a huge amount – but you’re still helping scammers earn money. Campaigns such as privacy drives, or “Click This if You Hate Cancer†are also usually just as fake (ESET Senior Research Fellow David Harley offers tips and thoughts on these “chain letters†of Facebook)  – as are pictures where you’re urged to click and see what happens. Likes, of course, are the “currency†of Facebook – so criminals collect them by any means, air or foul. Daylan Pearce, a search-engine expert at Next Digital in Melbourne says pages with 100,000 likes can be sold for $200, according to adverts unearthed by Pearce.
‘Within 3 days a post like this one has 70,000 likes, and someone somewhere is about to make a nice little profit by selling the page to a business wanting some quick wins. The buyer then changes the page details.Instant fanpage with a big following, lots of likes.â€
Your “Likes†also remain visible forever – and could serve adverts to your friends. Any pages you have “Liked†are also now searchable in Facebook’s new Graph Search. Visit your Activity Log and make sure you haven’t “Liked†any companies, products or sites you wouldn’t want the world to know about.
The warning from Facebook
“WARNING : Your account is reported to have violated the policies that are considered annoying or insulting Facebook users.system will disable your account within 24 hours if you do not do the reconfirmation.†The fake warning, is of course, a tool as fundamental to scammers as lockpicks are to burglars – witness this report just this week. Some of the bad English in that particular post should alert you to the fact that this is not a communication from Facebook – but it’s good enough to fool you if you’re not fully alert.
It’s a scam and a particularly vicious one at that.
Identified by Facecrooks.com – a great site to stay up to speed with the latest scams – the ‘warning’ scam is easier to fall for because Facebook does block certain posts or behavior – but the warning sign here is that a genuine reprimand would NEVER ask for your password. Why would Facebook need it at that point? Facecrooks writes, “if a user submits their Facebook login credentials, then the scammer will have complete control over their account. They can access their personal information to try and steal their identity, they can send bogus messages to their friends stating that they are in trouble and please send money, they can send links to other scams to all of the victim’s Facebook friends….the opportunities for misuse and exploitation are endless! Similar scareware posts involve Facebook purging drug-related posts – again, a scam.
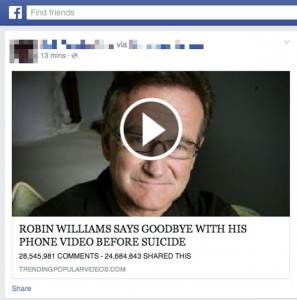 The morbid celebrity-death story
The morbid celebrity-death story
News stories DO spread through Facebook – but so do fakes, or hybrids where a real story is changed to offer one morbid detail. Last week, a video purported to offer a video of Robin Williams making his last phone call, should ring alarm bells – few news sources would play such a video so soon after someone’s death. The scam, which you may see shared by your Facebook friends oblivious to the fact that they are helping fraudsters earn money, claims to be a ghoulish video of Robin Williams making his last phone call before committing suicide earlier this week. Of course, you might be fooled into believing it is genuine. After all, you have just seen one of your Facebook friends share it on their wall.
Multiple scams – including some using fake Facebook profiles – targeted grieving victims of the recent Flight Mh17 tragedy. Alistair MacGibbon of the University of Canberra said that the criminals would hope to make money for referring victims to unscrupulous sites – and that the practice was increasingly common. “Crooks are super-fast these days at picking up on anything that’s remotely topical, and working out how to monetize it from a criminal point of view,†he said. “It’s a really distasteful trend.â€.
The too-good-to-be-true ticket offer
Cybercriminals follow the news avidly – hoping to fool users into clicking on malicious links in fake news stories – but the low-hanging fruit is upcoming events. Whether it’s the World Cup or a big concert, people  DO want tickets – and worst of all, some companies offer them through Facebook competitions, which makes the scam more convincing. A recent tickets scam encouraged fans to forward the link to friends to win Rolling Stones tickets. “You’d be making a big mistake if you clicked on the link, as you will be taken to a third-party website which strongly encourages you to share the link via social media, and then coerce others into clicking on it,†writes We Live Security’s Cluley. It is often safer to Google the subject of a link or type a website’s main URL into a browser instead of clicking the link – here, fans would have found that, on the official Stones website, there was no mention of the offer at all.
The post Facebook scams – the ‘classics’ and how to avoid them appeared first on We Live Security.










 ‘See who has been looking at your Facebook profile’
‘See who has been looking at your Facebook profile’