Over the last few years, as I have seen family and friends lose loved ones, I am constantly reminded of the importance of our digital legacy.
Just this past year, a friend and former colleague passed away. I, like so many, was shocked and saddened. He was healthy and vibrant until the day he died of a heart attack while out cycling.
I first learned of his death online – where family and friends announced his passing on a Facebook page. What soon followed was a vast outpouring of friends gathering to remember, mourn and celebrate him, and to console his family and each other.
That Facebook page remains to this day, months later, with occasional new posts that continue in remembrance and celebration of his life.
I don’t know if my friend left a directive about his digital assets, but I do think he would be pleased by the tributes and what has become a living online memorial.
While that approach was absolutely the right one for him as a tech industry figure, it may not be for everyone. We don’t always know what our loved ones would want if and when the time comes. Or we might not know how to secure and remove their assets per their wishes.
“Boomers will be one of the first to leave behind a vast and varied digital footprint”.
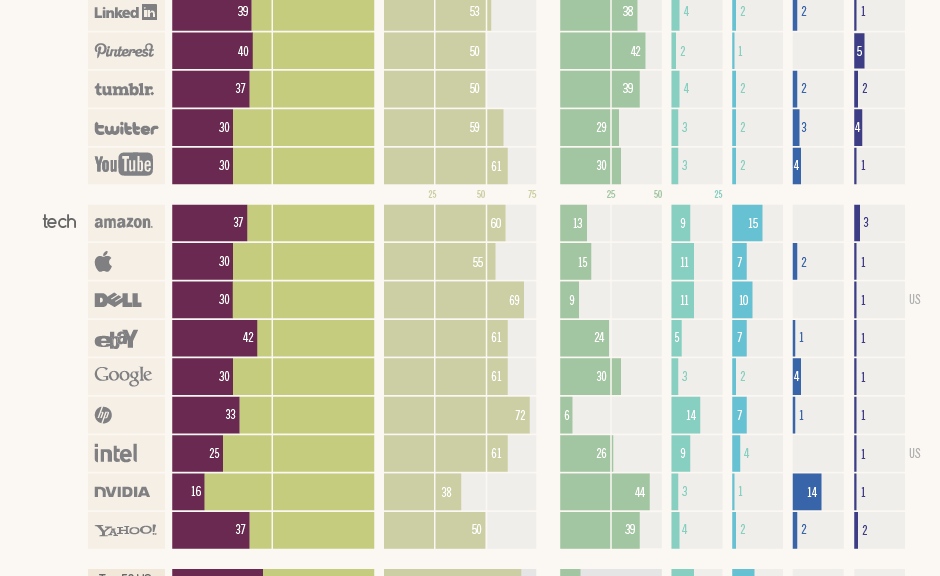
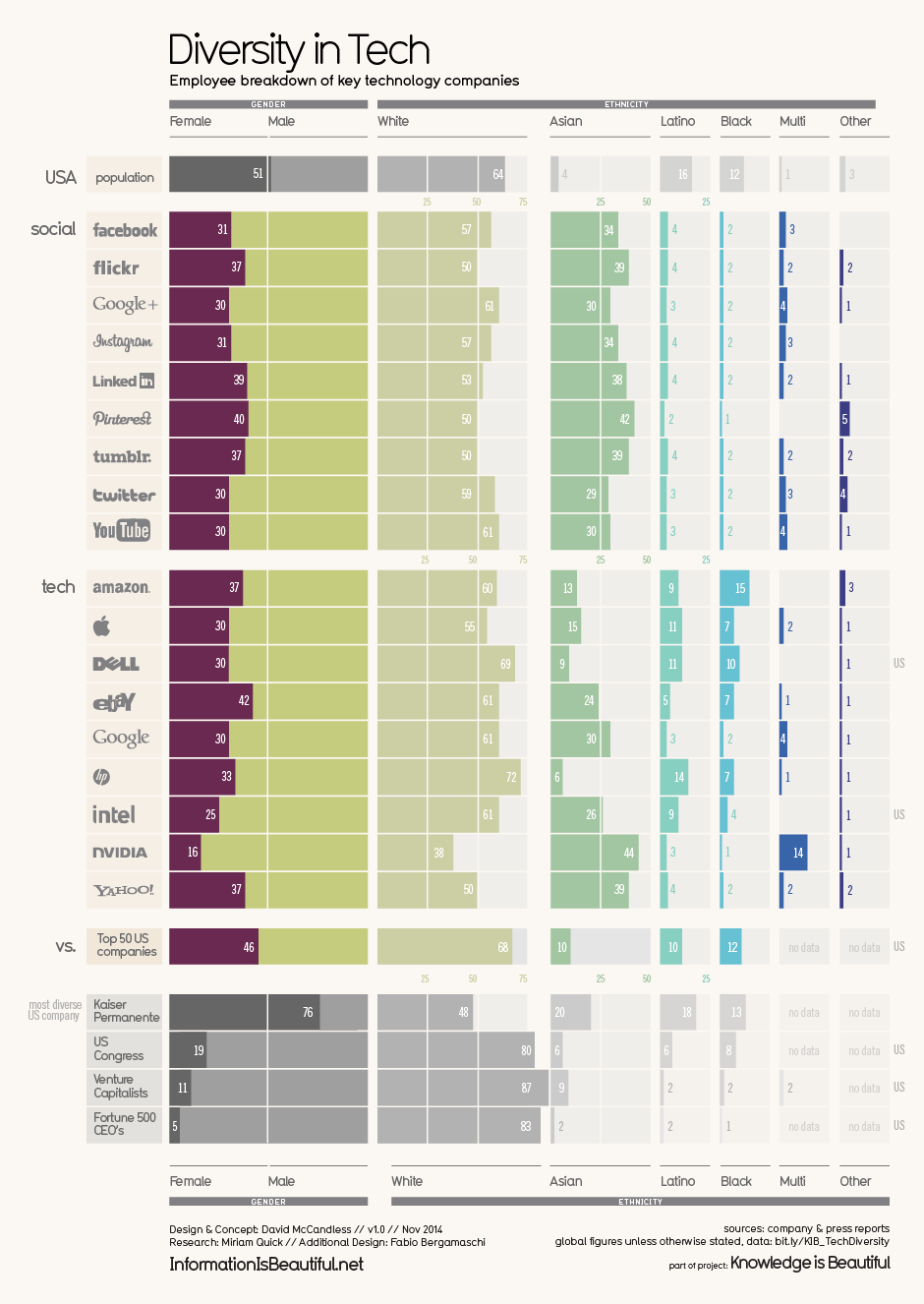
Our generation (the Boomers) will be one of the first to leave behind a vast and varied digital footprint – including social media accounts, emails, tweets, images, videos and more. But most of us have yet to consider just what it is we are leaving behind, and what we want others to do with it?
To me, it is like any form of estate planning. It’s something we know we should do, but most of us put off– unless forced to deal with it. Except that it’s not exactly the same, because to date there are few of us who have even thought about our digital legacy, let alone planned for it.
In new research we at AVG have just conducted with those 50-plus (aka Boomers and Seniors), 83% of nearly 5,000 people we polled in nine different countries, have yet to consider their digital legacy.
Among our research findings:
- Even the among the respondents who were familiar with the concept of digital legacy (12%), had never thought about it
- Only 3% could say they actually have taken steps to prepare their family ahead of time
- Yet, when the concept was explained to all, 1 in 4 admitted concerns about having a digital legacy.
This corroborates findings of other earlier independent surveys, which I wrote about in my column first exploring this topic last spring.
Clearly, further education is needed to help people make plans for their online lives – after they are no longer with us.
Even when all relevant paperwork is in place and documented, the task of managing a digital estate of a deceased relative can be a difficult and emotional task.
Here are three suggestions I have on digital legacy planning:
- Make a will and add a digital codicil, which is a simple document that amends your will, to include your digital assets.
- Make a list of your digital assets, passcodes and avatars, if you have them.
- Share information and help educate your family and friends about the need for digital estate planning.
Because AVG is committed to helping people deal with the security and privacy of data, devices and people, this is a topic where we feel we can contribute.
We have developed an eBook Dealing with Digital Death that offers a starting point for tackling the issue.
It offers considerations, recommendations, resources and guidance – from how to tackle the sensitive issues around what to do with social media profiles and blogs to creating memorials and practical information on digital estate planning and how to delete retail accounts. I hope you’ll find it useful.