Phishing continues to blight the Internet and is a thorn in the side of companies around the globe. Not only is it one of the most serious problems facing any company with even a minimal activity on the Web, it is also an ever-increasing threat.
 So much so, that a recent study has revealed that in the last year alone there have been more than a million attacks of this nature. This means that on average, a phishing attack is launched every thirty seconds with the aim of defrauding companies and home-users alike. In the case of businesses, the damage inflicted by this onslaught is nothing short of dramatic: the total cost to companies around the world is in excess of 9,000 million dollars, more than 8,000 million euros at today’s exchange rate.
So much so, that a recent study has revealed that in the last year alone there have been more than a million attacks of this nature. This means that on average, a phishing attack is launched every thirty seconds with the aim of defrauding companies and home-users alike. In the case of businesses, the damage inflicted by this onslaught is nothing short of dramatic: the total cost to companies around the world is in excess of 9,000 million dollars, more than 8,000 million euros at today’s exchange rate.
The total cost to companies around the world is in excess of 9,000 million dollars.
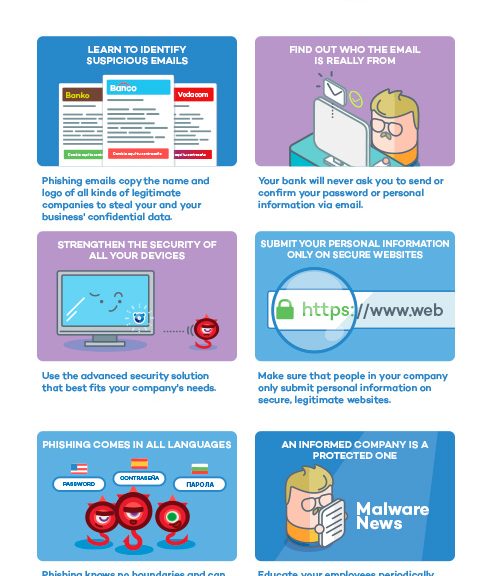
Given this situation, in addition to having proper protection, it is more important than ever that companies follow a series of recommendations to prevent falling victim to an attack that could have grave financial consequences. Checking the source of each email you receive and not accessing bank websites from links included in emails are two of the basic precautions you can take to avoid falling into the traps set by cyber-criminals.
What makes these and other similar measures so essential is the dramatic increase in phishing attacks that has taken place over the last year. In the second quarter of 2016 alone, more than half a million unique attacks were identified, that’s a 115 percent increase on the previous quarter. Moreover, the increase with respect to the same period in 2015 is even more alarming: 308 percent.
In the second quarter of the year “Phishing” attacks have been incresing in a 115 %
To counter this situation, it is essential for companies to ensure that their employees are aware that they must only enter confidential data on trusted websites which, as with all secure pages, have an address starting with HTTPS. Phishing attacks are on the rise and they are also evolving. Now, for example, not only are they aimed at identity theft on social networks or taking money from current accounts, they are also being used to steal from e-Wallets.
The post A phishing attack is launched every thirty seconds: 6 tips to protect yourself appeared first on Panda Security Mediacenter.