For more tips on online security and privacy, check out the AVG Academy YouTube channel.
![]()
![]()
For more tips on online security and privacy, check out the AVG Academy YouTube channel.
![]()
![]()
This change to “chip and PIN” has already occurred in many other countries and has reduced credit card fraud – in particular “card skimming” and “cloning” whereby somebody can make a copy of your credit card and use it elsewhere.
Most credit cards now contain a “smart chip” on them that are much more secure than the “magnetic stripe”. The reason for this is that the smart chip is actually a tiny-computer that can interact directly with a payment terminal or ATM – and they’re designed never to give up their secret information. Whereas a magnetic stripe reveals all its data and is easily copied.
U.S. business owners who fail to upgrade their payment terminals to support chip & PIN by October will also become liable for any fraudulent transactions as American Express, Discover, MasterCard and VISA get set to implement the change. However, some “pay at the pump” Gas stations will be exempt until 2017.
The good news for all of us though is that insisting on a PIN at the point of sale means your card, if lost or stolen, is useless to whoever might get hold of it – except for contactless transactions which don’t require a PIN under a certain transaction amount. As always you should still protect your credit cards the same way you do with cash.
Five (5) quick PIN tricks and tips:
Until next time, stay safe out there.
![]()
![]()
For more information on improving the speed, coverage and reliability of your home wireless Internet connection, visit our in depth guides.
Boosting Home Wi-Fi Signal Strength Part One
Boosting Home Wi-Fi Signal Strength Part Two
![]()
![]()
Emoji’s such as smiley faces and others pictographs used commonly by many people nowadays have been put forward as a possible replacement to the humble password or PIN by a British start-up called Intelligent Environments.
As reported in The Guardian recently, the concept lends itself to our natural ability to remember pictures much more vividly than standard characters like letters and numbers.
Add to that research that shows 64% of millennials are using Emoji’s almost exclusively in their communication, and one wonders if this trend just might have some merit in the future.
The method proposed is that instead of entering your password or PIN, instead you would select a sequence of 4 Emoji pictures from a possible set of 44. The math behind this says that an Emoji “password” would therefore be one out of a possible 3,748,096 combinations.
However, the question of whether this would be more secure over the standard password, and in particular a 4-digit PIN is open for debate.
While technically your 4-digit PIN is only one from a combination of 10,000 choices, the implementation on your mobile device tends to be much more secure, by the fact that incorrect attempts will result in gradually increasing timeouts – making it much more difficult and impractical to crack easily.
And consider that, just as with passwords, it is possible that people will select Emoji sequences that are quite predictable. For example, selecting Emoji’s that tell a common story, like a Man, a love heart, a Woman, and a bunch of flowers; it’s quite possible people will end up selecting popular Emoji versions of the 1234 PIN equivalent.
On the positive side, think of how hard writing down your Emjoi “password” is going to be for those of us who aren’t artistically gifted.
If you are concerned about only using a 4-digit PIN on your mobile device, however, there are options you can change:
For more information keeping your mobile device safe, check out the video below 6 Tips to Secure your Android Phone video.
Until next time, stay safe out there.
![]()
![]()
In a blog post , LastPass revealed that they “discovered and blocked suspicious activity on our network” and that it found “no evidence that encrypted user vault data was taken”.
LastPass seem to be transparent in sharing information about this security breach. They have provided what appears to be good technical detail about the information potentially compromised, along with the type of cryptography used to secure their user’s “Master” passwords.
The actual compromise of the ‘server per user salts’ and the ‘authentication hashes’ would allow the attackers to brute-force a targeted user’s password, but LastPass is claiming this information has been created using what is known as a ‘key derivation function’ called PBKDF2, considered best practice.
This makes it extremely difficult for attackers to brute-force the passwords in bulk and instead limit attackers to cracking one password at a time – meaning they would have to target a particular user (or use many computers to target multiple users).
However, the weakest link here is the compromise of ‘email addresses’ and ‘password reminders’. Two likely scenarios come to mind that may arise as a result of this compromised information:
(1) Phishing attacks to LastPass users is now very likely, if the attackers choose to send email pretending to be from LastPass to trick them into divulging their Master passwords.
(2) The password reminders may give the attackers clues when attempting to brute-force a password. Some users are known to provide password reminder clues that are very easy to interpret that almost reveal the password in full immediately.
Worse, the addition of the password reminder information to a phishing email may increase the success of that type of attack.
LastPass is right to advise all their users of this compromise, and hopefully all LastPass users are able to heed the warning and change their Master password, plus activate multi factor authentication options.
The positives in this case, however, appear to be the best practice use of cryptography in their storage of master passwords (i.e. PBKDF2) and the failure to access ‘encrypted data’ (stored passwords and Master Passwords). This is potentially down to LastPass having separate systems for this sensitive data.
If the attackers had been able to compromise the ‘encrypted user data’ then LastPass would surely be advising their users to not only change their Master password, but every other password stored within their accounts – and this would be a monumental task for all concerned.
![]()
![]()
For AVG, helping to keep our 200 million users safe online isn’t just a question of reacting to threats as and when they appear. Instead, our security is built on a foundation of deliberate, pre-emptive action in order to keep their data and identity safe.
One way to be proactive is through a bug bounty program, which offers rewards to researchers that legally find and responsibly disclose vulnerabilities. By safely identifying and fixing vulnerabilities before attackers discover them, bug bounty programs help make software and websites more secure.
This extra security is one of the reasons I’m pleased to share that AVG has started a bug bounty program on Bugcrowd. Bugcrowd gives AVG the opportunity to have a well-established and respected community review its PC security products. This proactive approach to the security of our software will give our more than 200 million active users even more peace of mind and protection.
By starting a bug bounty program, AVG joins other companies like Google, Microsoft, Facebook and Apple taking that extra step to secure its users.

The AVG bug bounty at Bugcrowd is currently focused on two of our PC based security products, AVG AntiVirus FREE 2015 and AVG Internet Security 2015.
If you think you’ve got what it takes to become a bug bounty hunter, you can see all the technical details here on AVG’s bug bounty page at Bugcrowd.
![]()
![]()
A famous football coach once said, “If you’re not getting better, you’re getting worse” and ironically this statement applies to your own security as well. If you’re not keeping up-to-date with the latest security, then it’s probably getting worse because the threats just keep getting better.
This simple fact has been proven again by a researcher who demonstrates how he can hack most garage doors using nothing more than a modified electronic toy. Researcher Samy Kamkar has published his findings and a video explaining how he was able to hack a number of fixed-code garage door openers in under 10 seconds.
I’ve released OpenSesame, a new vulnerability that can open fixed code garages in under 10 seconds with a Mattel toy https://t.co/0oRayWw8JV
— Samy Kamkar (@samykamkar) June 4, 2015
Not only is this a case of how old technology can be outdated by modern devices, but in this example the cause is a child’s toy that even today has already been discontinued by its manufacturer and is considered a throwaway item by some. Recycling hackers unite.
There’s no doubt that hardware-hacking gadgets are starting to become more popular such as mobile phone jammers and issues with keyless entry systems on cars.
Luckily, for those of us fortunate enough to have a garage door, Samy has chosen not to reveal the inner-workings of his research, so that criminals can’t benefit. But, let’s face it, the cat is out of the bag on this one, and the clock is now ticking.
Samy has also recorded a video explaining how to can protect yourself from attacks like these.
Most of the tips involve learning about the technology in everyday objects such as garage doors. Once you know how the tech works, you can understand how it can be vulnerable to various attack types.
Until next time, stay safe out there.
![]()
![]()
Researchers at ZScaler have discovered a new variation of the “Porn Droid” ransomware that affects Android devices.
Once the device is infected, the malware sends the user a message, apparently from the FBI, accusing the user of watching child pornography. It then demands a $500 ransom to restore the device to normal.
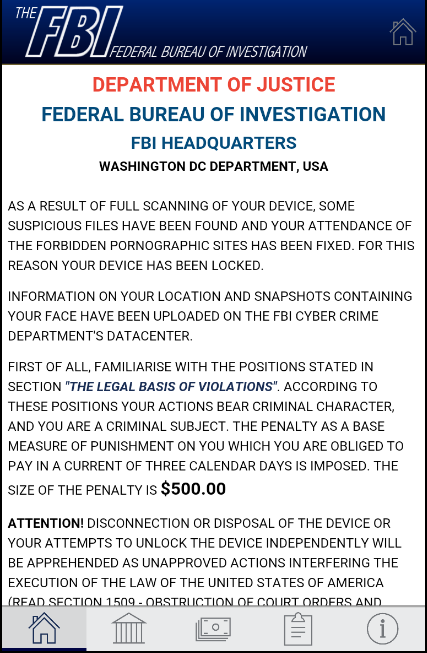
Infection:
After masquerading as a Google patch update, the malware then asks for a number of powerful permissions including “Erase all data” and “set storage encryption”.
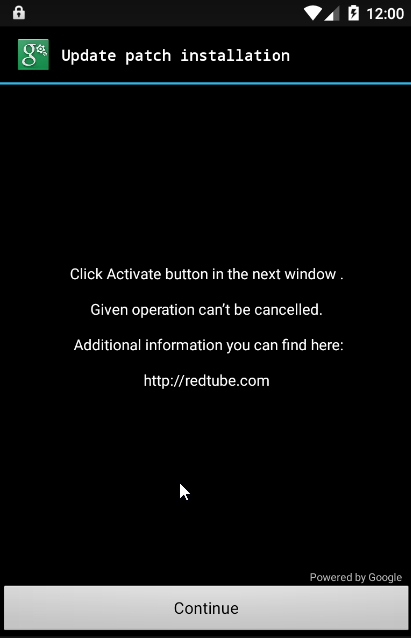
Clearly, the message is not from the FBI and the victim should not pay the ransom.

Always check permissions
Apps are the lifeblood of our Android devices and make them the powerful and useful tools we know and love. Apps help us stay in touch with family and friends, guide us, educate us and sometimes simply entertain us. But how much attention do we pay when we install an app? In the case of this ransomware, an alert user would never have granted those permissions to an app.
For a list of permissions to look out for when installing an app, check out this AVG Academy video from Michael McKinnon.
Have up-to-date security software
One of the simplest and most effective ways of keeping your device safe from malware such as “Porn Droid” is to have up-to-date antivirus protection.
By scanning links and attachments before they are loaded onto your device, security apps like AVG’s AntiVirus for Android can help keep your device free from randomware and running in top condition.
![]()
![]()
A new report from the UK fraud prevention service, Cifas shows that incidences of identity fraud rose by 27% in the first three months of 2015 with nearly 35,000 confirmed cases.
In fact, identity theft was so prevalent that it very nearly constituted half (47%) of all recorded cases of fraud.
The report also highlighted the fact that 80% of all identity fraud in the first quarter was attempted or perpetrated online and that credit card and bank account details were the most common targets for attackers to pursue.
As Detective Chief Superintendent Dave Clark, from the City of London Police explains “By following some simple procedures, such as creating strong passwords, protecting internet connected devices with up-to-date security software and not sharing too much personal information online, we can make life much more difficult for the identity fraudsters.”
Creating a strong password
Creating a strong and memorial password doesn’t need to be difficult. We’ve created an easy to follow infographic that explains exactly how it’s done in three simple steps.
AVG’s Michael McKinnon also has some great advice on simple mistakes you can easily avoid when creating a password.
Get up-to-date security software
Like Detective Chief Superintendent Dave Clark explained above, having up-to-date security software is important on all of your devices. Importantly, protecting your devices is neither expensive nor complicated. AVG has a number of free security solutions that can help protect your PC, Mac or Android device. AVG Zen also makes it incredibly easy to manage the security, performance and privacy of multiple devices all from one screen.
Don’t give up your personal information
While you should try not to “overshare” online anyway, taking the time to learn about “phishing” and how to avoid it can you detect scams and hoaxes online so that you don’t unknowingly hand over your valuable information to an attack.
AVG’s Tony Anscombe has some great advice to avoid phishing:
Perhaps Mother’s Day is your opportunity, for one day at least, to bring back the tradition of enjoying a meal surrounded by great conversation and the people you love.
Technology has definitely changed the dinner table dynamic, sometimes for good, and sometimes for bad. And depending on your age, your family values, and how you use your mobile devices, the experience is often different for many of us.
For some, dinner times used to be a place where debate over controversial urban myths often surfaced. In the days before “Mythbusters” existed, it was at the dinner table where hypotheses’ and logic were tested and rigorously explored.
And while stronger family personalities often won arguments based on false pretences – mobile devices and Internet now mean that the real facts are just a Google or Wikipedia search away. In my view, the lessons of learning to “agree to disagree”, along with the ability to resolve conflict using conversation alone, are sadly lacking in today’s world.
Busy family schedules used to be communicated across the dinner table too, but even this has been replaced by Calendar invites and Facebook events. For technologically savvy families there’s virtually no need to discuss such things during mealtime.
It’s no wonder with all the technology at our disposal, and with the humdrum of daily living taken care of by apps of every kind, that Mother’s are missing out on the attention and conversation they deserve.
So, for this Mother’s Day, switch to flight-mode during dinner time and pretend you’ve taken off to a world of wonder and beauty – one where loving connections are fostered, arguments are settled the old fashioned way, and where stories are shared and enjoyed.
Happy Mother’s Day, and stay safe out there.
![]()
![]()