More than a dozen apps removed from Google Play store after it was determined they were overly aggressive adware.
Tag Archives: Mobile Security
The best ways to speed up your android device

Six top tips for speeding up a sluggish Android device
It’s soul-destroying and one of the hardest things you’ll ever have to deal with. No, not Sunday lunch with your mother-in-law. We’re talking about Android devices operating at frustratingly slow speeds. It wasn’t like that when you bought it of course. So what’s going on? Why is speed such a big issue half a year down the line? “Is my service provider at fault?” we hear you ask.
It probably isn’t. 88% of all US connections are 3G or 4G, so there should be enough juice available for everyone. Sorry to disappoint you but in all likelihood, your problem is closer to home. Like, with the device itself and the way you are using it. But the good news is that help is available. It’s a fact of life; Android devices will stop performing at top condition after any prolonged period of use. Nobody said you have got to settle for that.
You’ll find below six useful tips to speed up your sluggish Android device.
- Back things up. All those photos & videos from that last holiday are so last year anyway… export, weed out, or cull them – whatever you want to call it: it’s time to backup your device. That should be the first step you take. Doing it will free up some space on your phone, and this eventually creates a better working device.
- Reboot. When was last time you switched it off? You can’t remember, can you? Well, maybe it’s time to switch it off and restart the device. Your mom will be proud of you!
- Clear up that cached data. Cached data will build up in your applications over time. This affects the performance of your device – you’ll find it hard shifting the blame on this one… To delete individual caches simply open up the settings on your phone and go to Storage and press the Cached Data button. It will delete all this useless data choking your beloved cell phone.
- Be realistic about your device’s capabilities. Did you overburden your phone with resource-hungry apps gnawing away relentlessly? They’re degrading your phone’s performance, so weed out or cull those apps – whatever you want to call it: it’s time to make some space. Do you really need everything you’ve installed anyway?
- Make sure your OS is fully up to date. You should always keep your OS up to date. Yes it’s time-consuming, yes it’s annoying, but just like visiting your mother-in-law it’s got to be done. There are good reasons why Google releases improvements to the Android operating system: those updates deliver stability, higher performance and plenty of benefits. It’s not worth missing out, and they are for free.
- Disable unnecessary animations. No matter how great they look, animations and special effects are known to slow things down. Boost performance by taking a closer look at your launcher’s settings.
Panda Mobile Security
If after following all these tips your Android device is still not working at an optimal speed, keep in mind that Panda Mobile Security maximizes the performance and battery life of your smartphone by analyzing in real time the activity of the apps installed on it.
These are just a few tips
There are plenty of other things to consider too. For example, why not use a high-speed memory card to your device? Not only you will increase your storage space (up to 2TB depending on your phone’s capabilities), but your device will start working faster. Also, if you’re are a gamer, check out one of the RAM memory optimizers.
Obviously, we’re all for cleaning things up… but make sure you don’t disable your Panda Security anti-virus software by mistake.
Stay safe!
The post The best ways to speed up your android device appeared first on Panda Security Mediacenter.
Cellphone Usage Increases by 20% since 2015

Cellphone Usage Goes Up to 5 hours a Day! Stay Safe While Out & About with Security Tips from Panda
An interesting piece of news came out recently. According to analytics firm Flurry, US consumers spend up to 5 hours each day on their mobile devices. That’s right: 300 minutes per day. Or to put it differently, a whopping 35 hours every week. It’s a lot more than television by the way. The research firm claims this level of usage is a 20 percent increase compared with the fourth quarter of 2015. If keep on the same growth in percentage, very soon we will be spending more time staring at the little screen rather than sleeping.
That’s what we call real news. But is that surprising? Well, not really.
The uptake of mobile devices has been phenomenal, experiencing eye-watering high year-on-year growth. No wonder all big industry players have launched mobile phones with ever larger screens, not to mention a broad range of tablets to suit all budgets. In the US alone, mobile connections now exceed the actual population of the country; and over half the population access social media from mobile devices – a six percent growth since last year.
So it’s fair to say mobile devices have become a hub for everyday activities, from banking to shopping. Of course, we still make phone calls with our devices… though less and less, with free texting having cannibalized our communication habits.
We’ve moved into an era where phones would be totally unrecognizable to Alexander Graham Bell, the man credited with having invented the telephone (though, perhaps more accurately, he was the first to obtain a patent for his invention, back in in 1876).
So what does it mean when it comes to security?
Are your mobile habits putting your safety at risk?
Hackers can nowadays use malicious apps or unsecured networks to access vital pieces of information sitting on your mobile device. According to software experts Panda Security, there are some simple steps you can take to stay safe:
- Phones have become increasingly loaded with sensitive data so being hacked is more of a risk. Set a secure password from the outset and combine it with biometric protection, if the device enables it.
- Android or iOS operating systems can be vulnerable to hacks. Installing regular updates and patches will help ensure your software is providing the best level of protection available.
- Clean-up and backup your phone regularly, by exporting your data for safe storage. And while you’re at it delete any old apps you’re not using anymore – don’t let them access your user data such as your location!
- Always access the Internet via secure Wi-Fi networks. Unsecured networks may allow nearby hackers to intercept your data – do not let them get you! In addition, please do not do any shopping or banking on a public Wi-Fi network, that’s a recipe for disaster.
- If you get text messages from unknown senders asking for personal information, just delete them. If you click on links in those messages, you hackers take advantage of you and install malware on your device phone. Don’t download apps by text message as this is a popular way for criminals to infect your mobile phone.
Having in mind, some people spend a total of 35 hours a week on their phones, it is safe to say, some of the digital print they leave may contain sensitive information. If you are one of those people, keep doing what you are doing as here at Panda we are making sure you are protected!
The post Cellphone Usage Increases by 20% since 2015 appeared first on Panda Security Mediacenter.
The Dark Side of Shopping Apps

Are shopping apps safe?
As we shoppers get better at identifying scams, cybercriminals are having to create new ways to try and steal our money. Effective PC security tools like Panda Safe Web can identify and block fake websites before scammers have a chance to trick us.
But increasingly we are shopping from our smartphones and tablets instead of desktop PCs. Realising this, cybercriminals have begun to develop a range of mobile-focused attacks designed to steal personal data and money.
So when you do fire up a shopping app on your mobile phone, how do you know it can be trusted?
Here are some tips.
1. Only download apps from official sources
Both the Apple App Store and Google Play Store use a very strict approval process to protect their customers. Whenever an app is submitted to one of these official stores, it is checked to ensure that it is not infected with malware, and doesn’t take personal data without your permission.
For iPhone users this is great news – every app they can download has been checked to ensure it is safe. Especially as Apple devices cannot install apps from anywhere else but the App Store.
Android users on the other hand are not limited to the Google Play store – they can download and install apps from virtually anywhere. Although this is much more flexible, not all app stores or websites apply the same security checks. Cybercriminals exploit this weakness by tricking Android users into downloading infected apps from email attachments or fake app stores. Once installed, this malware allows scammers to steal credit card details, or to encrypt your files so you cannot access them without paying a ransom.
When it comes to downloading shopping apps you must ensure they come from the official app store – otherwise you could be inviting cybercriminals onto your phone.
2. Install a mobile Security tool
You wouldn’t dream of leaving your PC unprotected against malware – so why ignore your mobile phone? Just this week mobile hacking hit the headlines again as government officials tried to highlight the risks.
It is absolutely essential that Android owners install a mobile security tool to protect themselves against fake shopping apps. Panda Mobile Security scans installed apps to detect malware and alert you to potential problems before your data can be stolen.
Using Panda Mobile Security you can also control what each app does, preventing them from accessing your data, or from triggering your camera or microphone. You can also prevent apps – good or bad – from uploading your information to the cloud, adding an additional layer of protection.
Stay alert
As well as installing security software on your mobile phone, you need to treat apps, web downloads and email attachments with caution. In the same way that you don’t open attachments from people you don’t know on your PC, you shouldn’t download unknown apps from untrusted websites.
As our phones become an important part of our shopping habits, criminals will devote more of their time and effort to attacking them. So it pays to protect yourself now before they attack you.
The post The Dark Side of Shopping Apps appeared first on Panda Security Mediacenter.
It Did What? The Dirty Secrets About Digital Assistants

Are Siri and Other Digital Assistants Actually a Security Risk?
People started fearing digital assistants before they even became a reality. Before computers were even a household commodity, Stanley Kubrick was terrifying cinemagoers with HAL, 2001: A Space Odyssey’s rogue AI assistant.
Today though, our intelligent personal assistants form an important part of our lives. As AI technology advances they will become even more prevalent.
While the dangers imagined in Sci-fi movies of the 60’s and 70’s are thankfully far from being around the corner, it’s important to look at the real security risks that digital assistants could pose.
Despite being the most popular intelligent personal assistants, Siri and Cortana are not the only iterations of this growing technology on the market. Amazon, for example, now offers it’s Echo device, while Facebook has recently released its own digital assistant called M.
So what are the dangers?
Not to sound too ominous, but IBM has banned the use of Siri for its employees. The rule was set by IBM Chief Technology Officer Jeanette Horan, who cited security concerns.
You know those large license agreements you have to agree to when you first start using a device, the ones most people don’t bother reading?
Well, Apple’s iPhone Software License Agreement, quite vaguely, shows how voice commands are used after being submitted to Siri. “When you use Siri or Dictation, the things you say will be recorded and sent to Apple in order to convert what you say into text.”
What’s more, “by using Siri or Dictation, you agree and consent to Apple’s and its subsidiaries’ and agents’ transmission, collection, maintenance, processing, and use of this information, including your voice input and User Data, to provide and improve Siri, Dictation, and other Apple products and services.”
Sounds like jargon? The convoluted styles in these agreements often help to gloss over important information that most companies know their user’s will be glancing over at best.
Siri may not literally be watching you, but the fact is that everything you say to her is sent to a big data center in Maiden, North Carolina. IBM’s Horan decided to ban Siri because it could be storing sensitive information for an unspecified amount of time.
If Apple were breached, hackers could intercept that data. And perhaps just as alarmingly, a lot of the data is sent to third party companies. Besides the fact that you’ll receive an onslaught of targeted ads, the more companies this information is sent to the less private it becomes.
This is far from being solely an Apple issue though.
Amazon Echo, A Criminal Witness?
In a case that has seen Amazon largely mirror Apple’s resolve on handing over encrypted data to the FBI, the Amazon Echo may have been a key witness to a murder.
James Andrew Bates is suspected of having killed Victor Collins in his apartment. No one else was present at the scene of the crime, except that is, Alexa, who was being used to stream music throughout the night.
Amazon, much like Apple, have abstained from giving police the data on Alexa, saying it would set an unwanted precedent. This shows though, at the very least, that police in Bentonville, Arkansas, where the crime took place, believe Alexa may be capable of storing sensitive information. So much so, they believe it could incriminate a suspect in a murder case.
Whilst this is obviously an extreme example of a data privacy issue, what implications does it have in a regular home?
The biggest all-round concern for cybersecurity experts is that these devices are constantly programmed to listen. Amazon’s Echo device is called to action by the command “Alexa”. This seems like an obvious vulnerability that could be used by hackers to listen into conversations taking place in the home.
Aside from this, the Echo cannot differentiate between different voices, so anyone who comes into your home potentially has access to every account linked to Alexa.
Other Risks
So, whilst it is yet to have happened, or to have been allowed by any of the big tech companies, lawyers or the police could potentially subpoena sensitive information. This is, of course, if law enforcement gets their way.
If they do, they’ll have the key to a huge amount of information, Apple, Amazon and Google being amongst a growing list of companies that keeps an archive of commands.
The problem, however, goes beyond the mere use of digital assistants. As the use of integrated devices and smart homes increases, more and more devices will have the ability to store potentially sensitive information. A Smart TV, for example could easily have the capability of storing recorded information. Whilst this would seemingly be primed towards targeted ads, there is again the possibility that sensitive information could be stored unbeknownst to its users.
Keep Safe
The obvious advice is easy to uphold, and is one that most people will already be practicing. Don’t say sensitive information, like passwords or credit cards details, out loud. It’s likely to become increasingly difficult to know who (or what’s) listening within your own home.
Meanwhile, whilst operating systems such as iOS do let you manage data collection by changing privacy settings, the only option the Amazon Echo gives you is to unplug the device when not in use. It’s important, therefore, to look at your privacy settings, whatever the device.
So aside from telling us tomorrow’s weather, where the best restaurants are, and the occasional bad joke, digital assistants do pose some real risks to our cybersecurity.
Whilst the technology undoubtedly makes us more seamlessly connected to our tech devices, in turn making our lives easier, it’s important to always take into account the issue of privacy; an issue that tech is increasingly making more tenuous within our own homes, for better or for worse.
The post It Did What? The Dirty Secrets About Digital Assistants appeared first on Panda Security Mediacenter.
Mobile security: The reality of malware … augmented
What awaits us in terms of mobile security trends? Throughout this article, we will discuss how risks might develop in the near future.
The post Mobile security: The reality of malware … augmented appeared first on WeLiveSecurity
![]()
Mobile World Congress 2017: Are Future Technologies Safe?

“Technology is very hard to predict.”
So said Reed Hastings, Netflix CEO, during his keynote at this year’s Mobile World Congress when asked what his forecast was for future technologies over the next five to twenty years.
This year’s Mobile World Congress (MWC) was full of tech that gets us excited about the future though. From 5G, which could be up to a thousand times faster than 4G, to new real-world VR applications, the event over the years has become so much more than just a showcase for mobile devices.
We were able to check it out, and have put together a list of some of the technologies that got us most excited, and that we feel will form a big part of our future lives.
As Hervé Lambert, Global Consumer Operations Manager at Panda Security, was quick to point out though, there is a flipside. As he put it, as these new technologies advance, cyber criminals “will become more specialized with each type of attack and will go deeper into the system.” For every new exciting piece of tech, there is of course, the question of cyber security.
How will this tech shape our future and will it be one where we can feel safe in the physical and digital world?
Robots / AI
Driving home the MWC’s futurist appeal, as well as the fact that the event is more than a simple mobile device exhibition, was the amount of robots on display this year. PaPeRo, the human companion robot was demoed by various companies. Its impressive face recognition capabilities can be utilized for public safety, even being able to track lost children in shopping malls.
At the Ubuntu stall, meanwhile, REEM and REEM-C were both on display. REEM-C, which was designed by Barcelona-based PAL Robotics, is a flexible full-size humanoid biped robot that is used for different types of research, including AI.
Being connected to the Internet of Things (IoT) obviously poses potential risks.
REEM-C, for example, weighs 80 kg. In a future where robots are more widely available, a malicious attacker could cause real damage by taking control of such a heavy piece of machinery.
AI and big data analysis is actually being used today to make people safer though. During a keynote speech at the MWC, Takashi Niino, CEO and president of the NEC Corporation, described how real-time analysis with face recognition technology is being used in Tigre, Argentina to reduce crime. The highly accurate face recognition technology can be used to identify criminals, and even to detect suspicious behavior. Since the “urban surveillance system” was implemented, vehicle theft has gone down by 80 per cent in Tigre.
“AI will soon become a reality of most people’s daily lives”
As always, there’s another side to the coin though. Whilst high-speed data analysis allows law enforcement to act more efficiently, it also does the same for cybercriminals. “Cyber crime is increasingly becoming automated and the number of incidents are escalating exponentially”, said Hervé Lambert. “AI will soon become a reality of most people’s daily lives, so it is very important that its development is overseen responsibly by engineers that are specialized in intelligent security.”
Virtual Reality (VR) / Augmented Reality (AR)
Virtual reality has been touted for a while as the next big thing in entertainment. We’ll be able to fully immerse ourselves in distant locations and invented realities. Arguably, its close relative, augmented reality (AR), is where the most life-changing innovation is going to take place though.
Several new VR/AR applications were on show at the MWC. Relúmĭno –which was on show at Samsung’s C-Lab VR projects stall– demonstrated an impressive practical application for VR. The Relúmĭno app, designed for Samsung’s Gear VR headset, acts as a smart visual aid for visually impaired people by remapping blindspots. The effect, when using the headset, can be described as seeing the world as a cartoon with edges and surfaces in your surroundings rendered as sharp black lines.
Other separate standalone projects, like Inflight VR, aim to enhance our inflight experience with VR entertainment. Flight notifications will appear at the bottom of the screen as you navigate the hand-tracking controlled system. LiveRoom, on the other hand, will allow people a more immersive retail experience with its AR capabilities, and can also be used to enhance the classroom experience.
What dangers do we face when it comes to VR/AR though?
VR and AR can be compared to social media, but on a whole other level. This means that when it comes to online privacy, the stakes will be much higher. An unfortunate example has already been seen of this in real life. Users have reported sexual harassment on VR, with inappropriate gestures by some gamers towards other players. Much like with social media, some users sadly see the anonymity afforded by their digital avatars as allowing them to act inappropriately in the digital world.
This type of problem could reverberate beyond just VR gaming though. It’s very likely that our digital avatars will become an even more important part of our lives in VR than they are now in the likes of Twitter and Facebook. If hackers can carry out ransomware attacks after retrieving information on social media, it’s possible that this type of attack will be an even bigger danger with VR in the future.
Connected and Autonomous Cars
One of the visions of the future presented at the MWC was one of people sitting back on their commute to work, in their driverless cars, as the vehicle safely takes control of everything.
Whilst this future may still be in the distance, some cars on display at the MWC are certainly taking us in that direction. Roborace showed off its “robocar” at the even, whilst Peugeot revealed its Instinct concept car, a futuristic and stylish vehicle that wouldn’t look out of place in a sci-fi movie. One of the Instinct’s capabilities is that it can change the ambience inside the vehicle, depending on the passenger’s mood. Stressed out after work? It’ll put you into a relaxed seating position and change the lighting to ‘ambient’.
As the car will connect to the IoT using Samsung’s Artik cloud platform, it will be able to seamlessly integrate your vehicle’s operating system with other devices. This could make your car remind you that a drive to the supermarket is in order, for example. Haven’t been keeping up with your fitness regime? Your car could encourage you to stop and jog the rest of your journey.
Potential risks
Of course there are potential risks when it comes to this technology. Though the technology doesn’t exist yet, there were many 5G demonstrations at the MWC. Most of these focused on reduced latency speeds, meaning that we’ll have a future where almost anything can be controlled in real-time. Could hackers take control of a vehicle that’s connected to the IoT and take it off course without the passenger realizing? It’s a scary prospect.
“Online security’s Achilles’ heel is the Internet of Things”
According to Panda Security’s Hervé Lambert, “online security’s Achilles’ heel is the Internet of Things”. It’s important for cyber security experts to keep up with tech innovations, as there’s no doubt that cyber criminals will too.
Lambert says that hackers aren’t the only worry though. It’s a possibility that in the future, “insurance companies could exploit driving data. This could include data about the way people drive and it could be used to increase insurance prices based on new criteria.” Insurers could have access to a huge amount of data, including where people drive and where they park.
Third-party data gathering could be taken to a whole new level. The IoT will massively benefit our lives, but sadly, it could also open a door to hackers and companies that are looking to financially exploit its users.
Honorable Mentions
“Smart cities, smart factories, smart cars, and anything ‘smart’ will also create a necessity for smart security.”
There was so much tech on show at this month’s Mobile World Congress that will undoubtedly shape our futures and improve our lives in many ways.
Just as autonomous cars look to be brining sci-fi predictions to real life, IIT’s grapheme electrode prosthetic is set to change people’s lives in a way that was previously only imaginable on the big screen. Think Luke Skywalker’s robot hand in The Empire Strikes Back. Graphene, a material that is invisible to the naked eye, will allow electrodes to be embedded comfortably into a robot-like prosthetic hand; a big advance in prostheses.
Drones were also a big draw at the MWC. Though they can be used for games as well as to record things from a distance, their most prominently discussed capacity at the MWC was for use in security systems. Whilst the flying machines will allow efficient surveillance, we also face the Orwellian prospect of drone surveillance as a means for law enforcement. Will they keep us safe or be used to control us? Only time will tell.
When pushed to give an answer for his forecast of the future, Reed Hastings said, “[at Netflix] we’re not sure if we’ll be entertaining you or AI.” While such advances in artificial intelligence are still a long way away, the Mobile World Congress has shown this year that technology will increasingly become a seamlessly integrated part of our very existence. Though future predictions are largely positive when it comes to new technologies, there’s a negative side that also merits attention.
As Hervé Lambert puts it, “smart cities, smart factories, smart cars, and anything ‘smart’ will also create a necessity for smart security.”
Cyber security is undeniably a big part of the puzzle when it comes to a future of safe, smart, integrated cities.
The post Mobile World Congress 2017: Are Future Technologies Safe? appeared first on Panda Security Mediacenter.
Don’t be an IRS phone scam's next victim. Start tax season safe.
Ever answered your mobile phone only to find silence? Or that a machine has called you? Or even that it’s a completely unexpected call from someone claiming to be from the Internal Revenue Service (IRS)?
![]()
International Women’s Day: 8 empowered woman in the computing world
8 empowered woman in the computing world to celebrate International Women’s Day
Often seen as a male-dominated industry, women have played an important part in driving developments in the computer industry. As we celebrate International Women’s Day, these eight women have blazed a trail in IT, setting an example to us all.
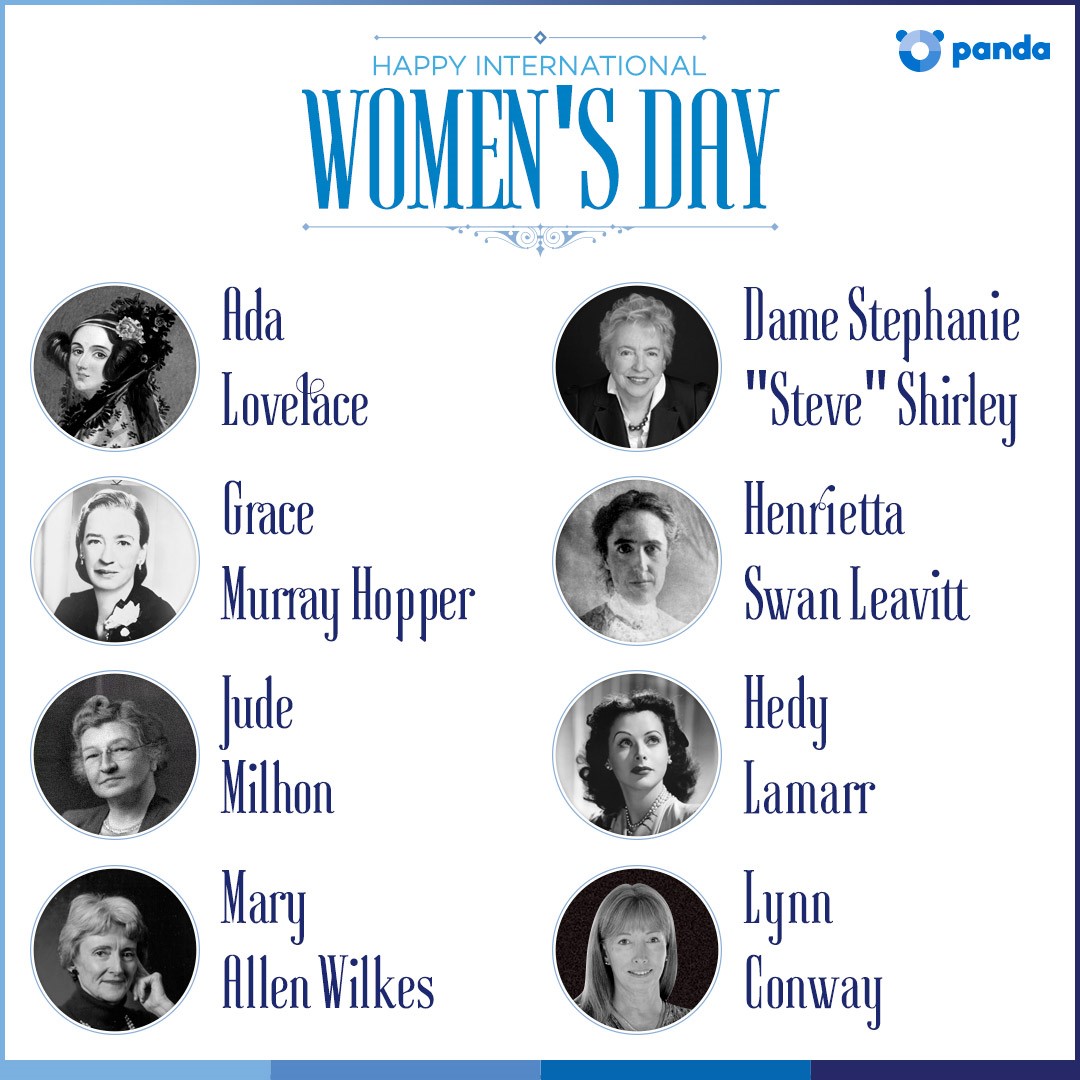 Ada Lovelace
Ada Lovelace
Despite being the daughter of the well-known bohemian hell-raiser George Byron, Ada Lovelace’s own life was incredibly successful, albeit slightly less “colourful”. Encouraged to study maths and logic by her mother, Ada’s studies soon brought her into contact with Charles Babbage, ‘the father of computers’.
As part of her work with Babbage, Ada created what is believed to be the first ever computer program – an algorithm to be run by Babbage’s legendary Analytical Engine.
Grace Murray Hopper
As well as being a Rear Admiral in the United States Navy, Grace was one of the first programmers of the Harvard Mark I computer. Her work led to the creation of the first compiler – a tool used to change computer code into a fully-functioning application.
Grace was also instrumental in creating COBOL, one of the first programming languages, and one that is still in use today.
Henrietta Swan Leavitt
During study for a graduate degree, Henrietta began working at the Harvard College Observatory. Her job – as a human computer was to help grade photographs taken through the observatory’s telescope, and to perform complex mathematical calculations.
Henrietta’s work paved the way for the techniques used by astronomers today to calculate the distance between Earth and distant galaxies.
Hedy Lamarr
Best known as a Hollywood actress, Hedy Lamarr was also an accomplished inventor in between roles. During World War II, Hedy helped to create a jam-proof radio guidance system to be used with torpedoes.
Although this signal-hopping technology was deployed by the US Navy until the 1960s (where it proved to be particularly effective), it is still in use today. The same basic principles are also used in modern WiFi and Bluetooth radio technologies – like those that make your smartphone and tablet work wirelessly.
Dame Stephanie “Steve” Shirley
After leaving school, Stephanie went to work for the Post Office Research Station where she helped build computers from scratch. She also learned to program machine code – the very low level language used by computer parts to work properly.
In 1962, Stephanie founded Freelance Programmers, a software company with the intention of helping women get into IT – just 1% of her programmers were male. The team worked on a broad range of projects, including the black box recorder for the supersonic jetliner, Concorde.
Jude Milhon
Having taught herself to program computers, Jude’s first job was in the IT department of a US food manufacturer. She also helped to create the Berkley Software Distribution (BSD) operating system which is still in use today.
Jude was also a committed social activist and hacker, going by the name of “St Jude”. Coining the term “cypherpunks”, St Jude helped to promote the idea of using cryptography to protect personal information as a route to social and political change.
Mary Allen Wilkes
Despite majoring in philosophy and theology, Mary became a computer programmer at the Massachusetts University of Technology. Initially she was programming IBM systems as part of a speech recognition project.
Later Mary was moved to a team working on LINC, widely believed to be the world’s first “personal computer”. As far back as 1964, Mary was using the LINC computer at home to refine the system’s design.
Lynn Conway
After a very successful period at university, Lynn was recruited by IBM to work on a project designing an advanced supercomputer. Known as the Advanced Computing Systems (ACS) project, the resulting computer is believed to have been an example of the first superscalar design.
Later Lynn worked for major organisations including DARPA and Xerox, and MIT as an associate professor.
Examples to us all
Although these women may serve as examples to women considering a career in IT, their experiences and achievements are actually a lesson for all young people – regardless of gender.
The post International Women’s Day: 8 empowered woman in the computing world appeared first on Panda Security Mediacenter.