News emerged recently that Apple has been challenged about storage on their iOS devices.
According to news sources, Apple has come under fire for the size of their latest operating system iOS8 which can apparently occupy up to 23.1% of the devices total storage.
On top of this, the upgrade from iOS 7 to iOS 8 alone can take up more than 1.3 Gigabytes of storage space.
While the storage statistics for iOS 8 might be surprising, it’s important that iPhone and iPad users realize that often their storage can be taken up by multiple unnecessary files and not just operating system files.
Operating systems are not the only files that bloat and grow over time; in fact it’s quite common for updates to systematically increase an app’s footprint on our devices as new features and enhancements are added
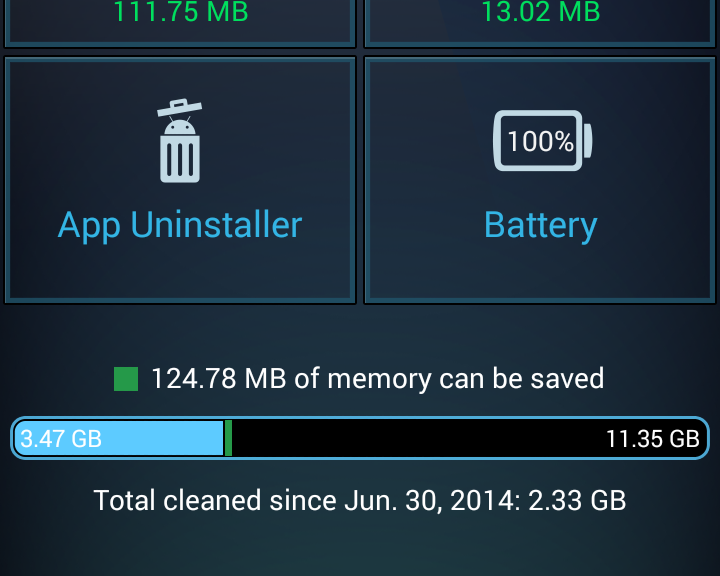
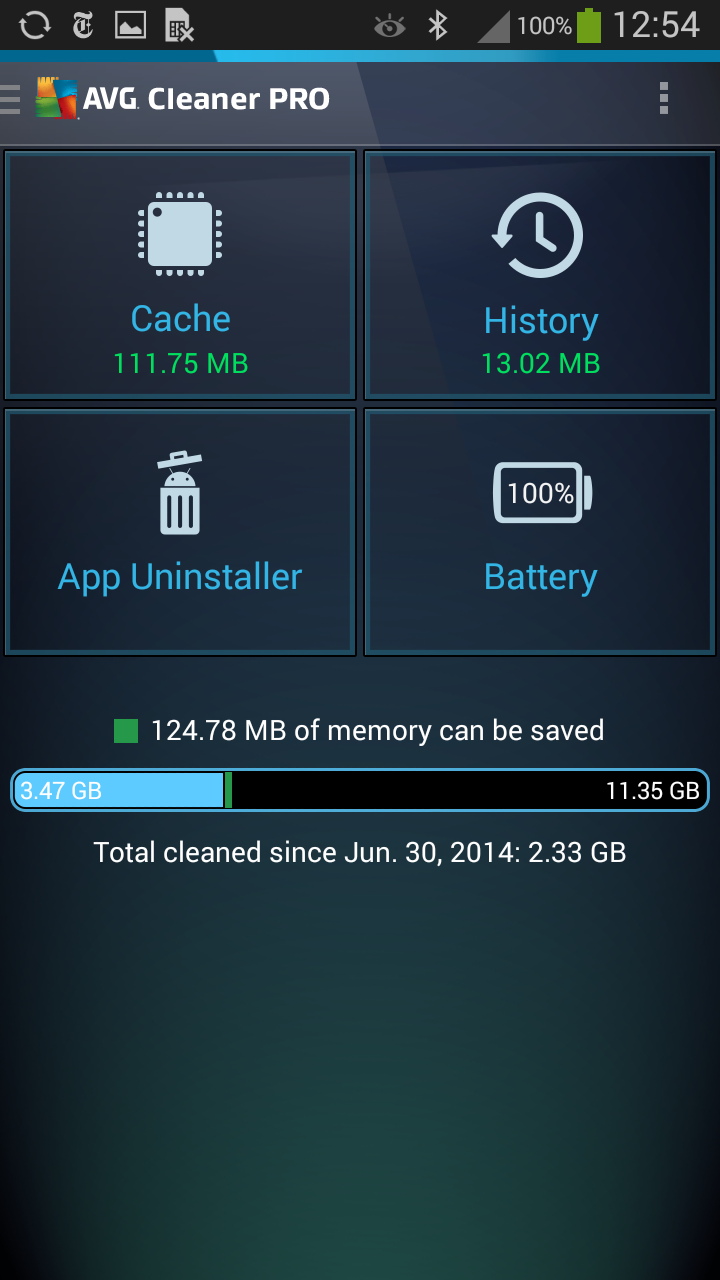
That’s why it’s very important to regularly clean out your mobile device, get rid of unwanted or unneeded files and apps and create space for the things you really want.
To help you do this, AVG has developed iOS Cleaner as part of the AVG PC TuneUp performance suite. iOS Cleaner can help you reclaim back valuable storage space on your iPhone or iPad devices by locating and removing duplicate files and unnecessary clutter and temporary files.
We’ve also prepared this easy to follow guide to help you get started.