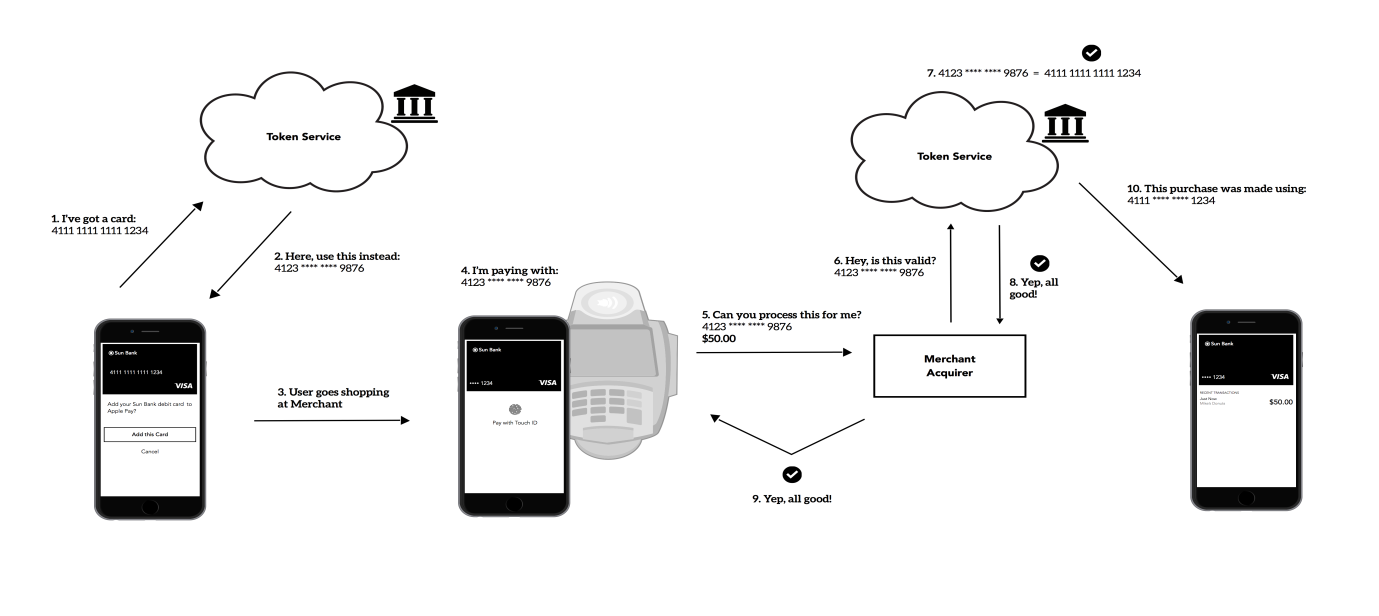
A blog released this week by Cybersecurity firm Zimperium details how Android phones can be infected when receiving an MMS (multimedia messaging service), giving hackers complete control of your phone. The report estimates that the security vulnerability is present in 950 million devices.
All the hacker needs for the attack is your phone number, and they can send you the message. In some cases the clever attackers have the message delete itself after delivery. The phone needs to be running Android 2.2 or later for it to be effected, that’s the majority of phones.
MMS Messages sent to Android phones that use the default messenger app use a piece of software called Stagefright that processes the messages. It is this component that potentially vulnerable to attack.
The real danger in the attack is that it requires no user intervention or action and can be installed completely without the victim’s knowledge.
Zimperium are a responsible company and not only alerted Google to the issue but also provided them with the necessary code to resolve the issue, and Google being responsible as well patched the software quickly, within 48hrs.
The big question is how do you get the fix and what is required? Generally this is dependent on your handset provider building the fix into their Android software and then pushing the fix to you. Typically, new software updates are not pushed to devices older then 18 months, this is of course due to the way we, as consumers, churn our mobile phones and always want a new one.
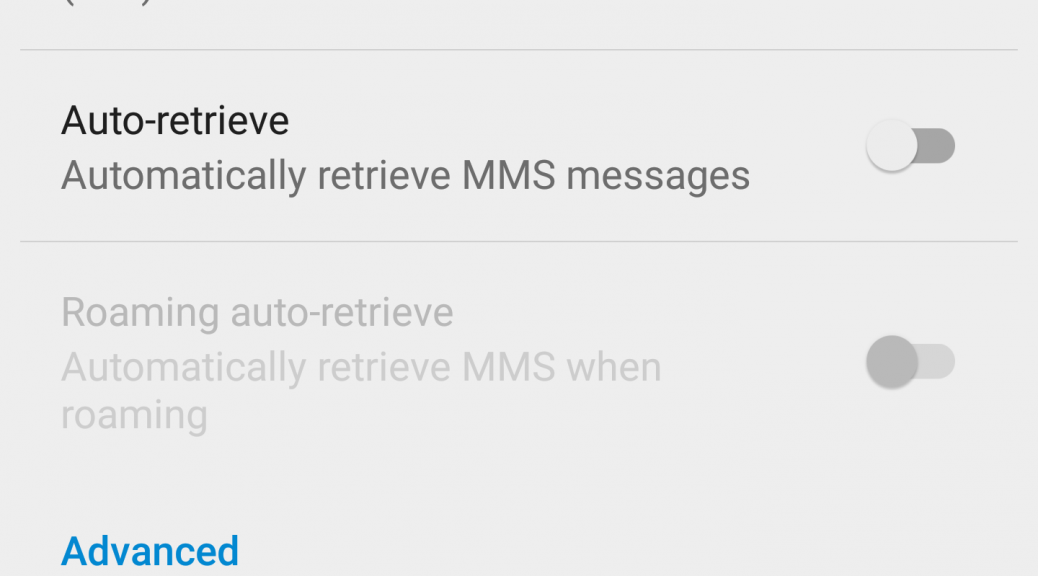
Disabling Auto-Retrieve
Alternatively, you can reduce the risk by switching off the ‘auto-retreive’ option in the Android MMS service, this would then mean that any MMS destined for your phone would need to be accepted by you. I have just taken these preventive steps on my Nexus 6 as follow:
- Open the messenger app
- From the menu (top right corner) take the option for ‘Settings’
- Then select ‘Advanced’
- You can then change the ‘auto-retrieve’ option to off
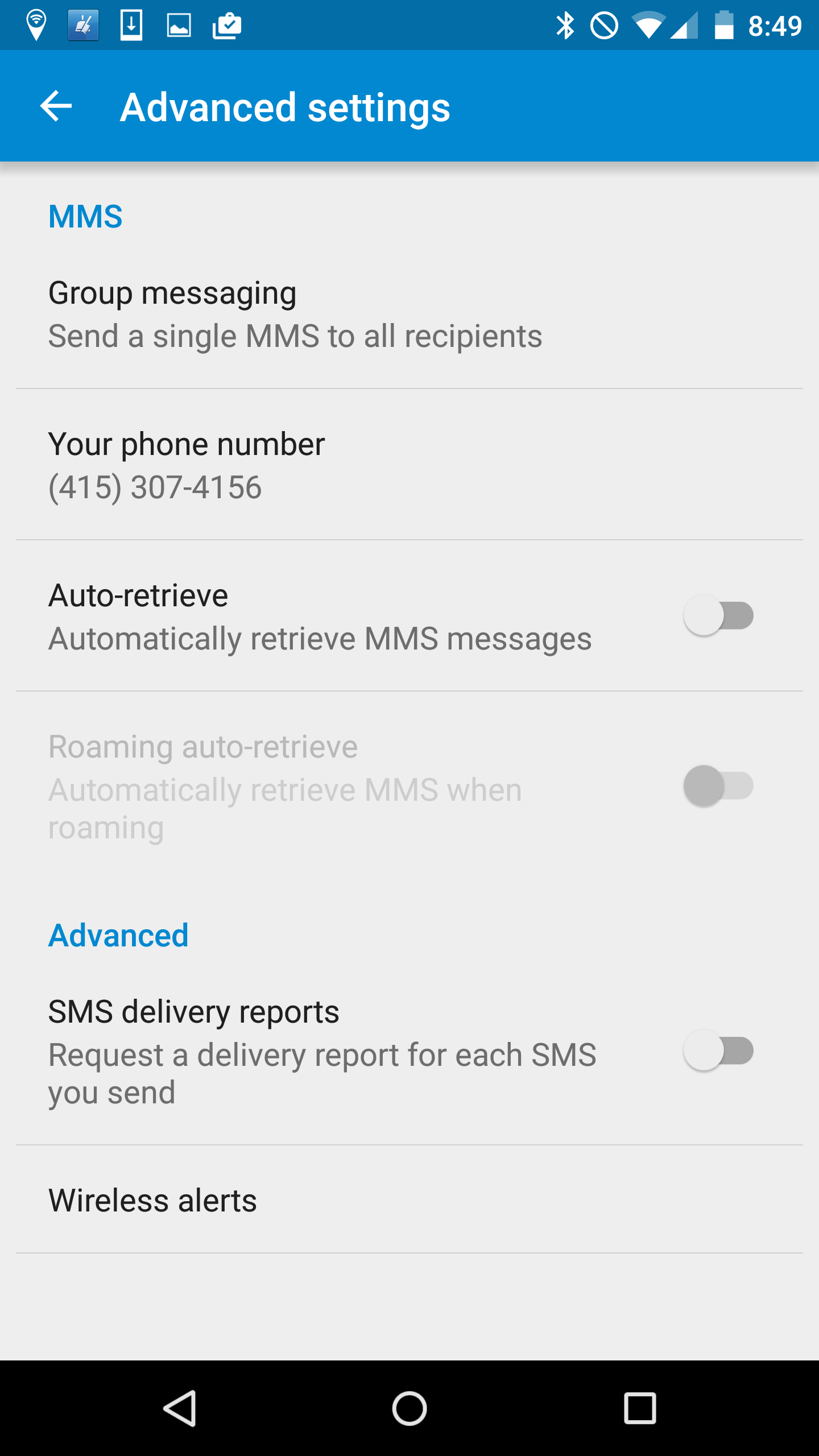
If you are running Google Hangouts as the default way to receive MMS messages then switching back to the standard messenger and switching the auto-retrieve option off will help mitigate the risk.
There are other vendors who also use the Stagefright code, some of whom have responded quickly and already released and delivered the fix to their users, they include Mozilla, Silent Circles Blackphone and CyanogenMod.
The research paper detailing the exact details of the vulnerability is due to be delivered at the Black Hat conference in Las Vegas next week. Every year around this time hacker’s use the conference to publish major issues found in our everyday devices. Just last week Charlie Miller published a report on taking control of a Chrysler Jeep.
I wonder what devices are next on the list and isn’t it worrying that they wait for Black Hat to publish the details rather than raise the concern when they actually find it.
Follow me on Twitter @TonyatAVG
![]()
![]()