Hundreds of millions of email usernames and passwords are ‘up for grabs’ in Russia’s criminal underworld, thanks to a major data breach.
The post 272 million email accounts compromised in major data breach appeared first on We Live Security.
![]()
Hundreds of millions of email usernames and passwords are ‘up for grabs’ in Russia’s criminal underworld, thanks to a major data breach.
The post 272 million email accounts compromised in major data breach appeared first on We Live Security.
![]()
A 10-year old boy has found a security flaw in Instagram and, for his efforts, been rewarded $10,000 by Facebook.
The post 10-year-old Finnish boy uncovers Instagram comments vulnerability appeared first on We Live Security.
![]()
Ransomware – it’s the online threat everyone’s talking about. Crypt0L0cker was one of the first on the scene in 2013; and since then, the costs of attacks continue to grow.
As an individual or business owner, you may be wondering just what ransomware is, what kind of risk it poses to you, and how attacks like these can occur.
Here’s the breakdown.
What is ransomware?
Ransomware is a type of malware with the ability to silently encrypt your files, before demanding payment for their return – often with a time limit.
And not only does ransomware target your most valuable files, like photos, documents and spreadsheets, it can also lock down system files to render your web browser, applications, and entire operating system unusable.
Our VirusLab has analyzed many variants of ransomware, including the well-known Crypt0L0cker, Locky, and TeslaCrypt.
But the threat isn’t limited to PCs. Both Android™ mobile devices and Macs can be infected as well.
How does ransomware get on my PC?
Most commonly, ransomware is spread via malicious email links and attachments – often concealed by changing the file extension and compressing the malicious code into a zip file. Opening the file infects your system.
Ransomware can also be bundled into other applications, such as games, video players, etc. So any application from an unknown or untrusted publisher is a potential risk upon installation.
Once on your system, ransomware works in the background, connecting to a remote server to encrypt single files, whole directories of files, or complete drives.
How do I know if my PC is infected?
You’ll see a message pop up demanding payment, which can range from a few hundred to tens of thousands of dollars. Payment must usually be made in some form of anonymous currency, like Bitcoin.
But even if you pay the ransom, there are no guarantees your files will be unlocked.
So naturally, this kind of malware has incredibly serious consequences, particularly for businesses holding sensitive customer information or internal data that’s not securely backed up.
Does AVG protect against ransomware?
It sure does. Both our PRO and FREE versions of PC antivirus provide protection against ransomware. This goes for AVG Business Editions, too.
Our protection is multi-layered. Not only do we check against known malware variants and behavioral patterns in our virus database, we also further test previously unseen files in a secure virtual environment before they are executed on your PC. This is done using artificial intelligence, sophisticated behavioral analysis and various other methods.
And we automatically update it all, so you stay protected.
![]()
![]()
Google is adding further security to the world wide web by introducing HTTPS for every blogspot domain name.
The post Google introduces HTTPS for blogspot domain names appeared first on We Live Security.
![]()
 PandaLabs, Panda Security’s laboratory, outlined in this report the main cyber-security developments over the first months in 2016, showing statistics of malware and cyber-attacks in the first quarter of 2016. The amount of malware created continues to break records, with more than 20 million new samples identified, an average of 227,000 per day.
PandaLabs, Panda Security’s laboratory, outlined in this report the main cyber-security developments over the first months in 2016, showing statistics of malware and cyber-attacks in the first quarter of 2016. The amount of malware created continues to break records, with more than 20 million new samples identified, an average of 227,000 per day.
Cyber-criminals continue attacking without giving sensitive infrastructures the chance to take a break, as seen in the attack suffered by 21st Century Holdings, a clinic specialized in cancer treatments with headquarters in Florida. The clinic had to alert their 2.2 million patients and workers that their personal data might have been compromised.
The Rosen Hotels & Resort chain has been the victim of an attack that occurred between September 2014 and February 2016. The company alerted their clients who may have used a credit or debit card in their establishments over this time period that their data could have been stolen by the attackers.
Even the world’s most powerful governments haven’t been spared, such as the United States, where the Department of Defense has presented a rewards program called “Hack the Pentagon” in which rewards are offered to hackers who find security holes in the Pentagon’s web pages, applications and networks.
Smartphones are another easy target for cyber-criminals. SNAP is the name of a vulnerability that affects the LG G3 phones. The problem is due to an error in the implementation of LG notifications called Smart Notice, which allows JavaScript to be executed.
The growing sector, the Internet of Things, is also affected by this year’s criminal activity. In this area, we can see how something as innocent as a doorbell can be attacked. Manufacturers are becoming more aware of their product’s safety, in fact, General Motors just launched a new rewards program for hackers who are able to find vulnerabilities in their vehicles.
The PandaLabs study shows that Trojans continue to be in the lead of all malware samples. Out all malware samples created in 2016, Trojans are number one with 66.81% of the total (an increase compared to last year), followed by viruses (15.98%), worms (11.01%), PUPs (4.22%) and aware/Spyware (1.98%):
When we analyze the infections caused by malware worldwide, we find Trojans in the lead again. This is normal if we take into account the rise in ransomware infections, including the rise of Trojans, which is also one of the most popular attacks cyber-criminals use because it allows them to obtain money easily and securely. There are more and more companies whose networks are falling victim to these cyber-criminals and who are paying millions of euros to rescue their stolen information:
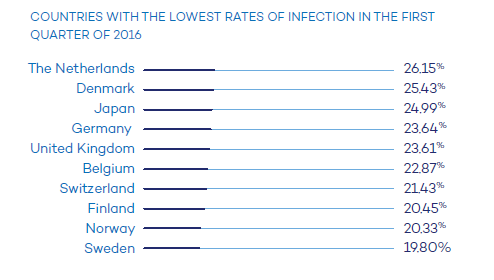
In this study we can find a table showing the countries with the highest and lowest infection rates in Q1 of 2016: Asia and Latin America (China leads the ranking with 51.35% of infections) are the most affected countries; while the Scandinavian countries have the lowest infection rates with (Sweden at the lowest at 19.80%).

 If you want to know more about the specific attacks, be up to date with the latest research carried out by the FBI, and the latest news of the cyberwar, you can download the entire document here. We hope this is of interest to you!
If you want to know more about the specific attacks, be up to date with the latest research carried out by the FBI, and the latest news of the cyberwar, you can download the entire document here. We hope this is of interest to you!
The post PandaLabs identifies 227,000 malware samples per day in the first quarter of 2016 appeared first on Panda Security Mediacenter.
From Locky to SamSam, JIGSAW to CryptoLocker, today’s ransomware variants can take down businesses with dramatic consequences.
Ransomware will prevent file access, web browsers, applications, and entire operating systems – holding the lifeblood of a business operation ‘hostage’ until a ransom is paid.
At AVG, we use a multi-layered security approach with multiple layers of inspection and testing to identify and eliminate a wide variety of malware, including ransomware. When accessing a file, our multi-layered security approach uses several different inspection and detection techniques, as detailed below, to determine whether the file is malicious.
This is reflected in our security technology engine powering our AVG Antivirus Business Edition and Internet Security Business Edition software solutions.
Simply described, the process includes these layers:
We also regularly submit our security software to independent test labs. Results from these independent tests serve as more proof points to the effectiveness of our technology and multi-layer approach. Our latest round of testing by AV-Test.org earned a six out of six rating – the highest rating for protection. In a recent Real-World Protection Test by AV Comparatives, AVG scored a 99.8% detection rating.
It is difficult to predict and guard against everything hackers may throw our way, but in the face of constantly evolving threats, a multi-layered security approach is a smart strategy.
To find out more about our AVG Business Edition solutions, please visit our business security page.
![]()
![]()
Third party risks to organizations has been described as a “serious threat”, a new study by the Ponemon Institute and Shared Assessments as revealed.
The post Third party risks ‘ a serious risk’ appeared first on We Live Security.
![]()
This past month, there was a giant development in science. Once again, technology has caught up to what we thought was only imaginable. For the first time in history, a quadriplegic recovered mobility in one of his hands thanks to neuroprosthetics, which in this case, is the superhero combination of an implanted brain-chip and a sleeve made of electric bands.
Ian Burkhart, a 24-year-old American man, is paralyzed due to a spinal cord injury that was caused from a diving accident a few years ago. What at first seemed like a hopeless predicament for him, has become a positive example for science and humanity.
Burkhart continues to live a life of passion and purpose—coaching high schoolers, inspiring others through public speaking, and working towards his undergrad degree—while living by the quote “Success, it’s what you do with what you got”.
Swiping a credit-card or playing a bit of Guitar Hero are two simple things Burkhart thought he would never be able to do again. He has been able to train his brain to exercise commands, which are later carried out using the implanted chip and electrode sleeve. According to scientists, in a few years, many disabled and paralyzed people could be dressing and feeding themselves, completely independently.

But, as always, with each new advancement comes challenges and opportunities for those who are looking to take advantage. Which is why it is critical that we protect the sensitive data that has yet to be compromised: the information that is stored in our brains.
Expert Alfonso Muñoz, from Criptored, explained how EEG headbands are vulnerable to the same attacks as your smartphone or your computer, stating that “any type of attack can happen because, really, you are not copying waves, you are copying bits”. The security-risks associated with the possibility of registering brain waves are alarming. Muñoz warns about the future of “mental surveillance” and “brain hacking”.
Imagine that someone, somewhere could read your mind… spy on your thoughts. This fear has already been proven in rigorous academic studies. When it comes to this on-going marathon between humans and technology, even with the good, that we stay wary of possible intruders. Like Muñoz said, “attacks have limitations“. However, “the truth is, the thought that it can be done, in a relatively simple way, is scary“.
Information from your brain can be removed without you knowing it
The post Science is one step closer to reading your mind appeared first on Panda Security Mediacenter.
Ransomware is being increasingly relied upon in cyberattacks, according to Verizon’s latest Data Breach Investigations Report.
The post Cybercriminals ‘increasingly relying upon ransomware’ appeared first on We Live Security.
![]()
Smartphones have become vital to our existence, accompanying us in our day-to-day lives, both at work and at home. Since May 1st is International Workers’ Day, we are celebrating by reviewing some of the top applications we believe are most useful for our professional success.
These app icons saturate our phone screens, but with good reason. Today, there is an app for everything. Apps offer a wide range of possibilities and solutions, helping us organize our tasks and merge our professional and personal lives.
Even though we do our best to make our Smartphones as secure as possible, sometimes there are vulnerabilities, like large amounts of malware waiting to take over your phone. As seen above, there are a variety of applications waiting to be downloaded and used to help you on your journey up the career ladder. However, we must keep in mind that there are some risks that come with installing anything downloaded off the internet.
Black Hats frequently use apps as keys to “get into” our phones. If you use them as work tools or to share sensitive and private data, you should think about downloading an antivirus.
We have some tips when downloading these applications. First of all, “avoid the black market” and download your apps in authorized stores that are reliable. Secondly, choose apps with official developers (these will always be more secure). Thirdly, pay attention to the number of downloads (if there are more than 1,000, we can consider it a popular app and reduce the possibilities of giving problems.) Lastly, review the feedback from other downloaders to make sure it is a good one.
Current Smartphone attacks have put device security and personal information in danger, which is especially hazardous when your devices are connected with your work-life. Prevention is the best possible thing you can do to guarantee your security.
Here at Panda Security, we hope you continue in the fight against cyber-threats and keep on protecting your work-life. Have a great weekend and a wonderful International Workers’ Day!
The post Tips to help protect your professional Apps appeared first on Panda Security Mediacenter.