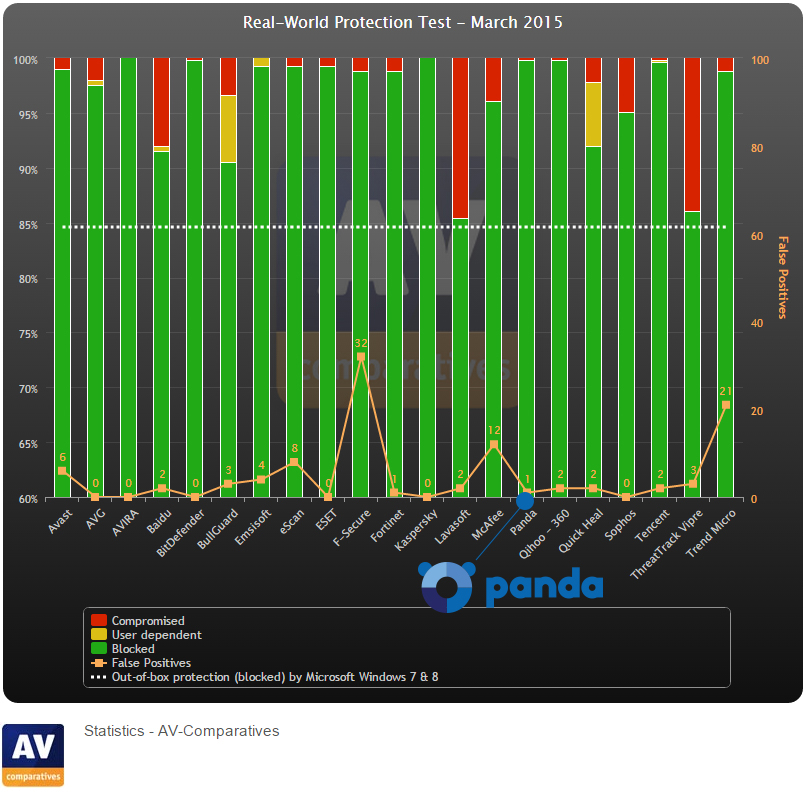
Panda Security presents its light, simple and cross-platform security solution for endpoints.
Endpoint Protection, our corporate antivirus, offers continuous and centralized protection for your Windows, Mac and Linux systems, including laptops, servers, leading virtualization systems and Android devices.
“With Panda Enpoint Protection 7.20 we continue to strengthen our cross-platform security solutions by securing one of companies’ weakest and most vulnerable points: mobile devices,” explained Eduardo Fernández, Product Marketing Manager at Panda.
And if you need an additional layer of protection, try Endpoint Protection Plus, which includes protection for Exchange servers, anti-spam, Web monitoring and filtering, and anti-theft features for mobile devices.

Cross-platform protection
As forecast by our colleagues at PandaLabs at the beginning of the year, in 2015 attacks on smartphones, and especially those running Android, are set to reach new levels. Not only will they increase, they will also become more complex, and they will all have a common target: to steal users’ personal data.
This is particularly serious in the case of company smartphones and tablets, and cyber-criminals will do anything to get hold of this information.
If 2014 saw more Android malware in circulation that ever before, all indications are that in 2015 these threats will grow exponentially, as will the number of victims.
In this context, it will be essential for users to have antivirus protection on mobile devices. “Our ultimate goal is to help customers seal off this major malware entry point,” added Fernández.
Endpoint Protection: Benefits
- Easy-to-use protection for all devices
- Remediation actions
- Real-time monitoring and reports
- Profile-based configuration
- Centralized device control
- Quick, simple installation
- Malware Freezer to “freeze” detected malware for seven days, and restore files in the event of a false positive.
Additionally, Endpoint Protection Plus includes:
- Anti-spam and Web filtering
- Anti-theft protection for mobile devices
If you are interested in trying our solutions, request a free demo of:
ENDPOINT PROTECTION
ENDPOINT PROTECTION PLUS
The post New version of Endpoint Protection, our leading antivirus for corporate environments appeared first on MediaCenter Panda Security.