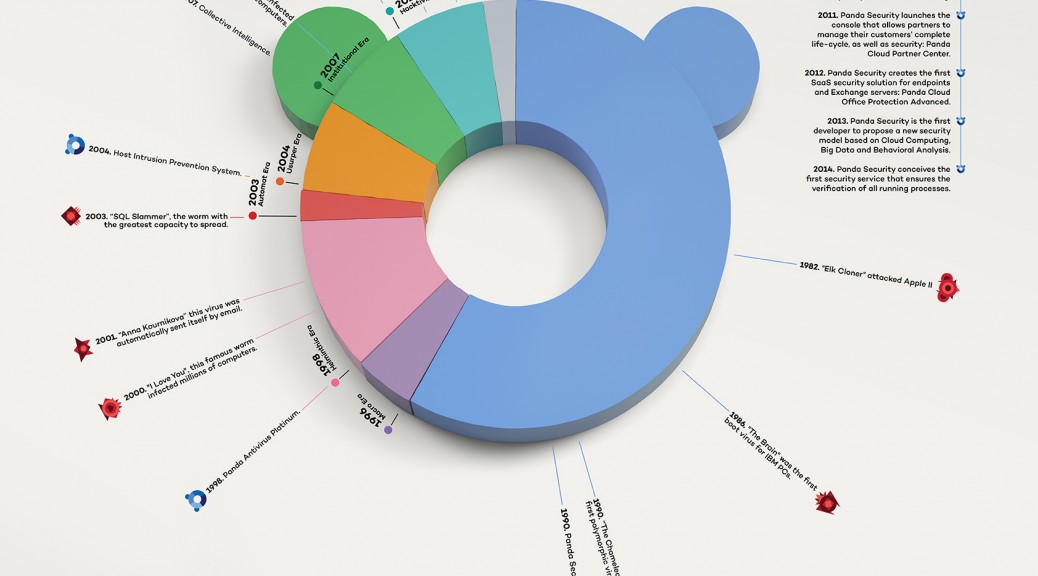
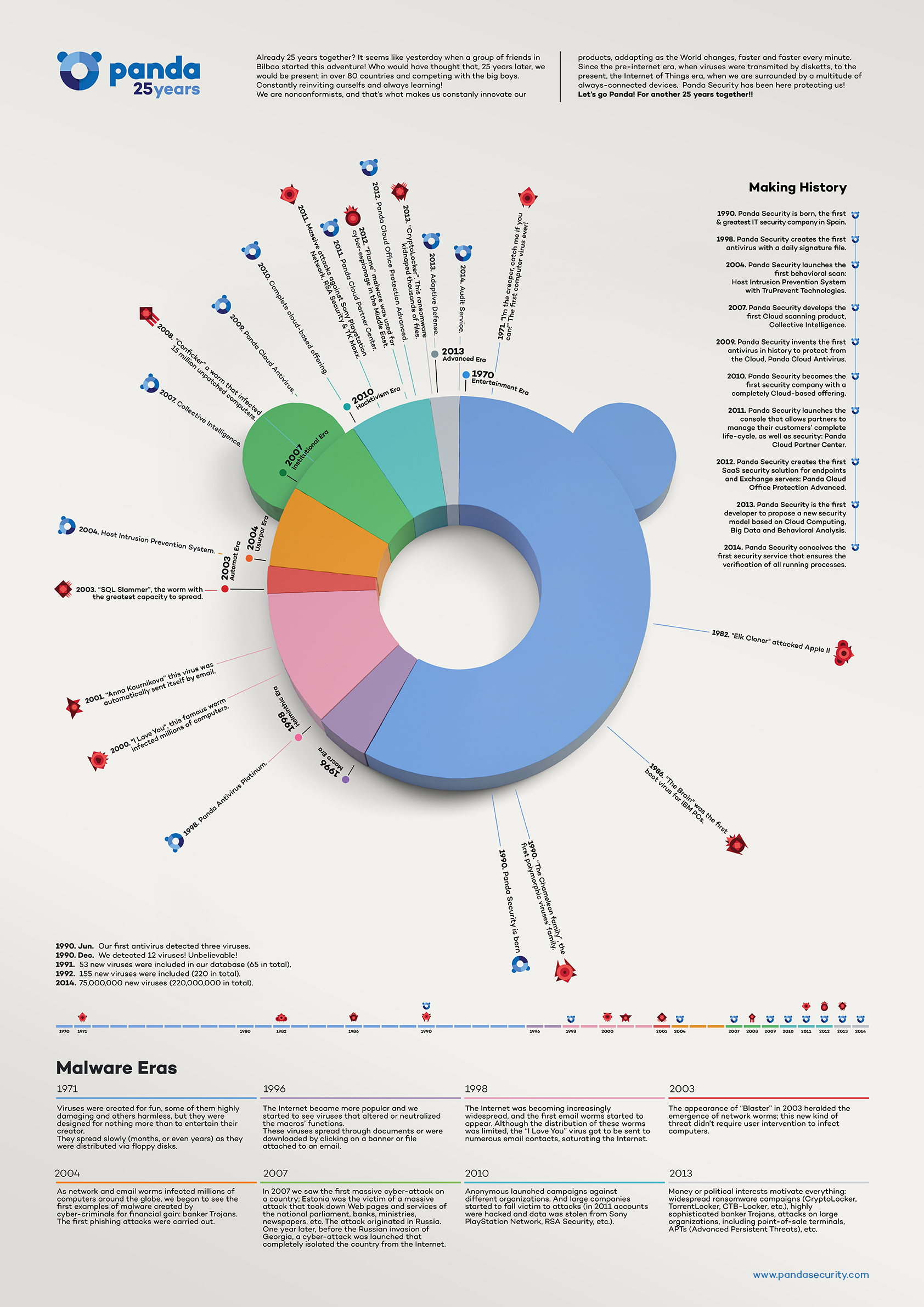
What is Cloud Computing
Cloud Computing means storing and accessing data and programs in ‘the cloud’. This concept has been the basis of an entire business model that provides services and computing resources over the Internet.
This technology leverages the cloud to free users from having to worry about processing and storage work. Everything is done from and in the cloud.
Cloud Computing technologies don’t require any type of specific infrastructure from the user and provide cross-platform access at any time from anywhere.
Cloud-based security is an absolute necessity. Therefore, if you are looking for a business antivirus that provides best-of-breed cloud-based protection, look no further. Try Endpoint Protection.
Endpoint Protection provides cloud-based cross-platform protection for all your endpoints, minimizing maintenance costs and resource usage.
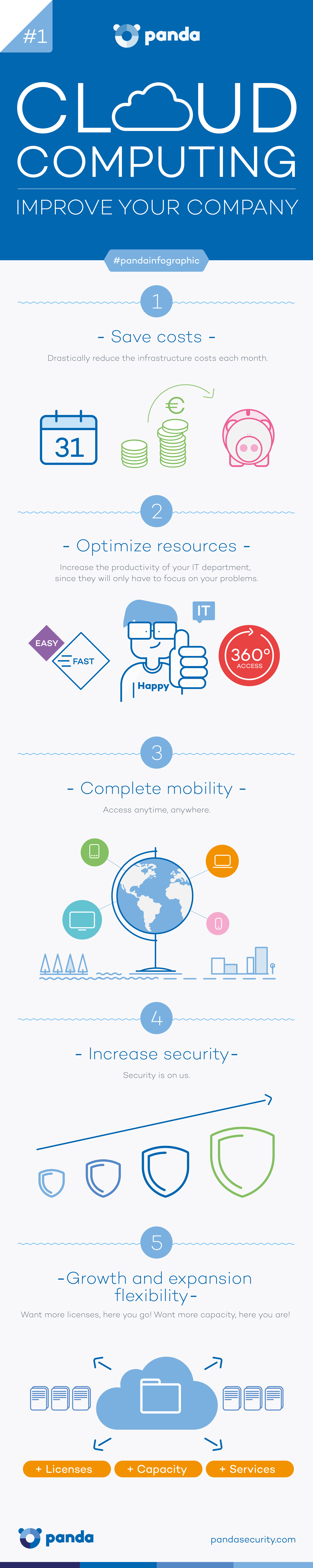
5 Reasons why Cloud Computing will boost your business
- Save costs.
a. No need to buy any specific hardware since everything is in the Cloud (is Cloud based), which will drastically reduce the infrastructure costs.
b. No need maintenance experts since the Cloud based solutions management is maintained by its creators from the cloud. - Optimize resources.
a. Increase the productivity of your IT department, since they will only have to focus on your problems, not on tools configuration, since the Cloud technology configuration and maintenance is as easy to use as your email.
b. Increase the productivity of your workers offering them 360 access.
c. Achieve more efficient and dynamic environments. - Complete mobility.
a. Access anytime, anywhere.
b. Total access to the applications and the information.
c. Access from any device connected to the Internet. - Increase security.
a. No need to make efforts in order to protect your Cloud based solutions, security is on us.
b. The security technology you had ever imagined for your business safeguards your data.
c. In case of disaster the Backup services in the cloud will save your business. You will be able to recover your data anytime. - Growth and expansion flexibility.
a. Want more licenses, here you go! Want more capacity, here you are! Want to expand your services, done! Everything you want, just by extending your Cloud services.
If you want to share this infographic, here toy have the code:
The post What is Cloud Computing and how it will boost your business – Infographic appeared first on MediaCenter Panda Security.