Google is rolling out a new extension for Chrome that will monitor users’ logins and warn them if they enter a Google password on a non-Google page, a move designed to help protect users against phishing attacks. The new extension, called Password Alert, works for both consumer accounts and Google Apps for Work accounts. Company […]
Tag Archives: Phishing
Humans the weak link in alleged White House hack
Earlier this week, it emerged that Russian hackers have successfully managed to infiltrate the computer systems at the White House.
Given the highly sensitive nature of information held within any government’s systems, we have to assume that the breach is significant. Although full details of the breach have not yet been made public (and maybe never will) some news sources indicate that President Obama’s schedule was among the information accessed.
It’s hard to see America taking this intrusion lightly, given the history between the countries and I expect to see them double down on security in the coming weeks.
Some are asking questions of the US government’s security policies and rightly so. Although protecting such a vast network of computer systems is a very complex operation. I was not surprised to learn that the attackers gained access to the system via a form of “spear phishing” attack targeting the end user.
Governments, just like any organization, are only as secure as their weakest link. Sadly, when it comes to security the weakest link is always a human. We as people are susceptible to social engineering and as such can unknowingly undermine even the most sophisticated of security technologies.
All hackers need to know is who to target and how – and then they can start to build out a profile of their victim and work out how to target them. It can take a long time but it’s often worth the wait, especially in an attack like this.
It will be interesting to see how this plays out in the coming months.
![]()
![]()
Don’t take the bait: Beware of web attack techniques

When it comes to cybercrime, it’s always better to be in the know. Here are a few ways that web attacks can find their way onto your device. Don’t be fooled — most cybercrooks design attacks to take place where you’d least expect it.
-
Social engineering preys on human weakness
“A lot of attacks are still using social engineering techniques; phishing emails – ways of convincing the user to give up valuable information,” said Avast CEO Vince Steckler.
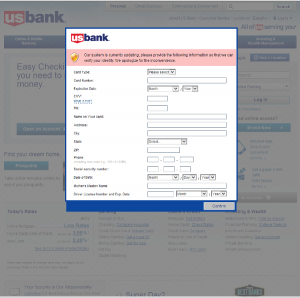
In a phishing or spearphishing attack, hackers use email messages to trick people into providing sensitive information, click on links, or download malware. The emails are seemingly sent from organizations or individuals the potential victims would normally get emails from, making them even more deceptive. Last July, Avast took a look at the Tinba Trojan, banking malware that used spearphishing to target its victims.
An example of an injected form from Tinba Trojan targeting U.S. Bank customers.
Web attacks also take place through SMS Text Phishing, also known as SMSishing. This method has become one of the most popular ways in which malicious threats are transmitted on Android devices. These text messages include links that contain malware, and upon clicking them, the malicious program is downloaded to the user’s device. These programs often operate as SMS worms capable of sending messages, removing apps and files, and stealing confidential information from the user.
-
Malicious apps attempt to fool you
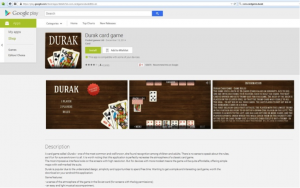
Malicious programs can disguise themselves as real programs by hiding within popular apps or games. In February, we examined malicious apps posing as games on Google Play that infected millions of users with adware. In the case of malicious apps, cybercrooks tamper with the app’s code, inserting additional features and malicious programs that infect devices. As a result, the malware can attempt to use SMSishing in order to collect additional data.
The Durak card game app was the most widespread of the malicious apps with 5 – 10 million installations according to Google Play.
-
Ransomware uses scare tactics that really work
Another name that made headlines was a group of malware dubbed ransomware, such as CryptoLocker, and its variants Cryptowall, Prison Locker, PowerLocker, and Zerolocker. The most widespread is Cryptolocker, which encrypts data on a computer and demands money from the victim in order to provide the decryption key. Avast detects and protects its users from CryptoLocker and GameoverZeus.
Make sure you back up important files on a regular basis to avoid losing them to ransomware. Ransomware made its way from desktop to Android during the year, and Avast created a Ransomware Removal app to eliminate Android ransomware and unlocks encrypted files for free.
Count on Avast apps to keep mobile malware at bay
To keep your devices protected from other ransomware, make sure to also install Avast Free Mobile Security & Antivirus from the Google Play store. It can detect and remove the malware before it is deployed.
Install Avast Ransomware Removal to find out if your Android devices are infected and to get rid of an infection. Avast Ransomware Removal will tell you if your phone has ransomware on it. If you are infected, it will eliminate the malware. Android users who are clean can use the free app to prevent an infection from happening.Once installed, you can easily launch the app to scan the device, remove the virus, and then decrypt your hijacked files.
Google Apps ‘Defect’ Leaks Private WHOIS Data Of 280,000
A Google Apps bug leaked hidden WHOIS registrant information in the clear, putting close to 300,000 domain owners at risk for identity theft, phishing scams and more.
Pharming Attack Targets Home Router DNS Settings
A pharming attack has been detected targeting home routers distributed from Brazil’s largest telco, a rare instance of a web-based attack changing DNS settings in order to redirect traffic.
Phishing, exploits and botnets – how can they affect your business?
How can phishing exploits and botnets affect a business?
The post Phishing, exploits and botnets – how can they affect your business? appeared first on We Live Security.
Microsoft phishing email targeting corporate networks with ‘neurotic malware’
Security researchers have uncovered a trojan that evades sandboxes specifically targeted at corporate users, hidden in legitimate looking phishing email that apes Microsoft’s Volume License.
The post Microsoft phishing email targeting corporate networks with ‘neurotic malware’ appeared first on We Live Security.
How to detect and avoid phishing scams
As I predicted last week, the recent data breach at US insurance firm Anthem Blue Cross Blue Shield has led to a sharp increase in the number of phishing attacks pretending to be from the company.
In this short video you will learn how to:
- Recognise phishing emails in your inbox
- Check you are on a legitimate webpage
- View security certificates to ensure sites are safe
For more details on phishing and how to stay safe, visit this blog post from my colleague Michael McKinnon.
Follow me on twitter @tonyatavg
Apple ID user? Careful! There is a new phishing attack!
Careful! We have detected a new phishing attack!
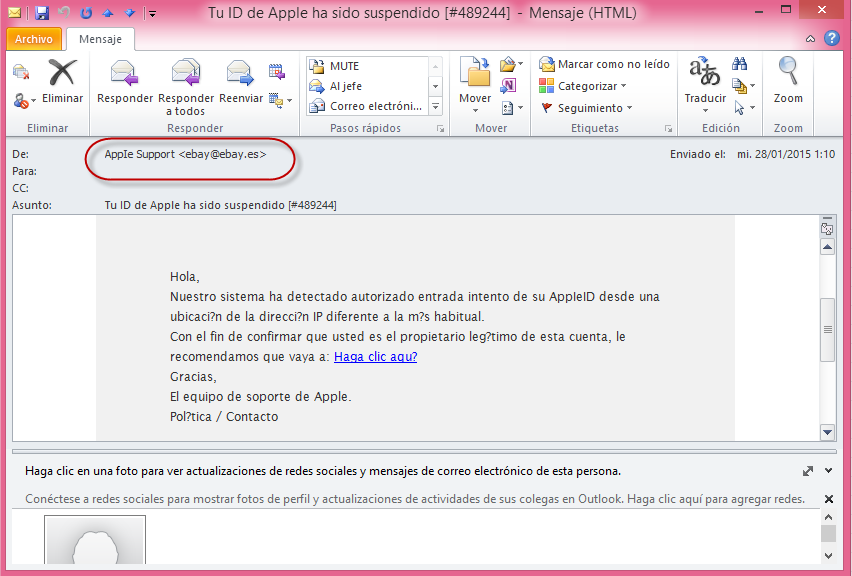
If you receive an email with the Spanish text: “Hola, nuestro sistema ha detectado autorizado entrada intento de su Apple ID…” (“Hello, our system has detected authorized access attempt of your Apple ID…,”) careful, it is phishing!
Below is an example of the email and the first thing that should catch your attention is the sender’s email address: AppIe Support <[email protected]>
Using the excuse that someone has tried to access your Apple ID account, the cyber-criminals ask you to change your details. When you click on the link, a page opens that is an almost perfect imitation of Apple’s website:
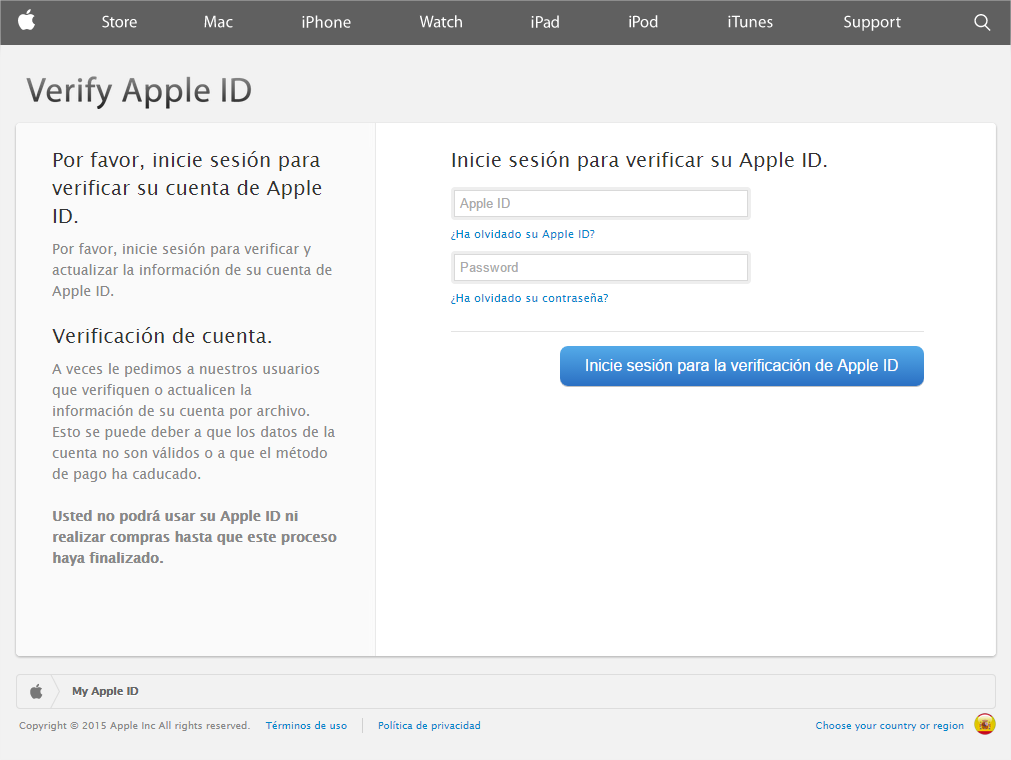
After signing in with your Apple ID login details, the next step is to update your personal details.
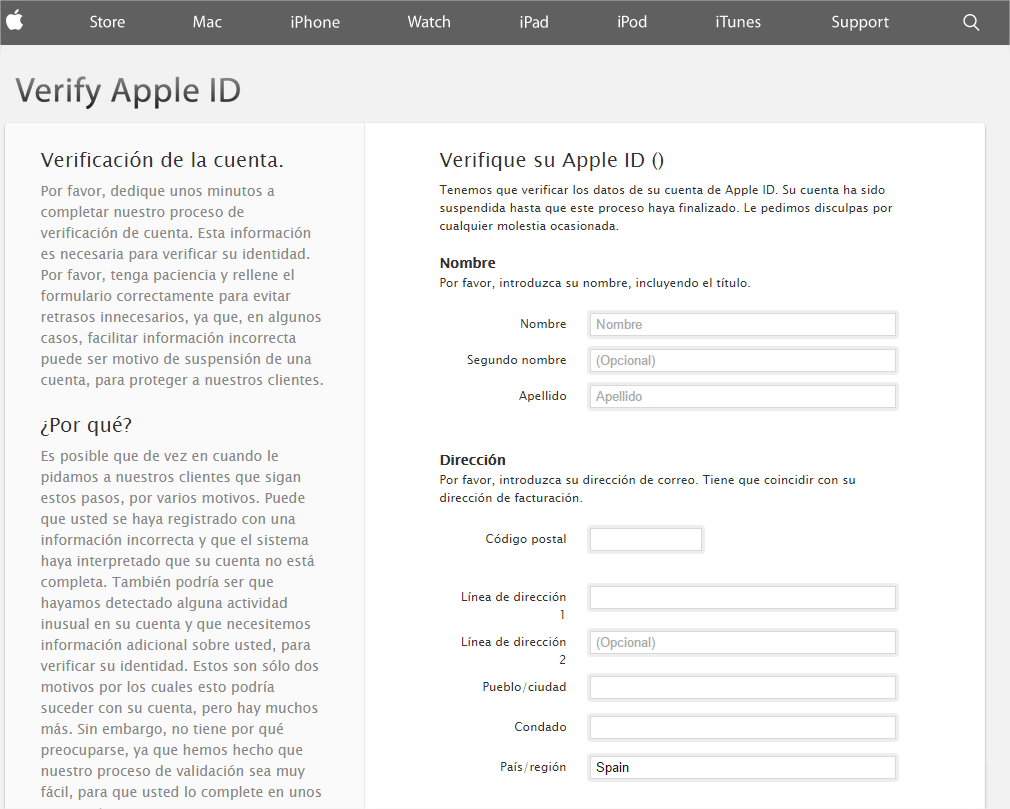
In addition to your name, address or telephone number, it requests your bank and credit card details in order to verify your identity and as the default method of payment for purchases and for iTunes or the App Store.
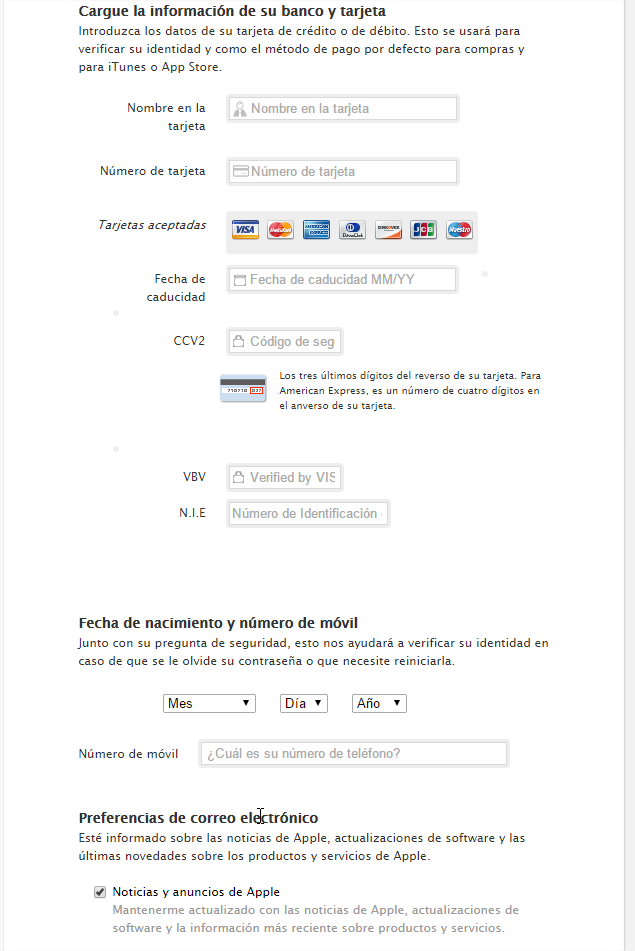
So, if you fall into the trap and enter all of this data, you will be giving the criminals access to this sensitive information.
As we always say, no company will ever ask you to send your personal details to them via email. If they do, be suspicious! In addition, in this case prevention is better than cure and it is important to have an extra layer of protection by installing one of the antivirus software from our 2015 line.
The post Apple ID user? Careful! There is a new phishing attack! appeared first on MediaCenter Panda Security.