How secure do you feel after handing a stranger your wallet? Or giving your smartphone to someone?
The post Get some privacy on iOS with the new Avira Vault appeared first on Avira Blog.
How secure do you feel after handing a stranger your wallet? Or giving your smartphone to someone?
The post Get some privacy on iOS with the new Avira Vault appeared first on Avira Blog.
Experts believe that the success tied to a recent spate of DDoS for hire groups may be because many are copycat collectives operating with a shorter lifespan.
The Let’s Encrypt initiative reached yet another milestone this week when it entered public beta, a step that it claims will help make it easier for website owners to embrace HTTPS encryption.
Black Friday and Cyber Monday are huge shopping occasions, not only in the US but across the world. Last year it was reported that the US spending over Thanksgiving reached an all time high with $89 billion being spent online.
Email campaigns offering deals and discounts are commonplace these days and every week retailers try to tempt me with discounts in an attempt to generate online sales. This dynamic method of communicating means that offers can be targeted based on my purchase history and the preferences I may have shared with the retailer.
On my shopping list this year are things I’ve been holding back purchasing in anticipation of discounts and offers that will surely land in my inbox, or that I might able to find online. One of them is a new laptop for my son.
But there’s also a dark side to some email that arrives in inboxes. Cybercriminals know that we get excited by deals and offers, or need to maintain our online payment methods, and they use this knowledge in an attempt to scam us. Most of us think of this as spam and just delete it, but sometimes it is difficult to identify the real emails from the fake ones.
Recently, I asked our research team which organizations in the US are being impersonated the most in emails. Specifically the ones used in “phishing” emails that attempt to gain access to your accounts, or trick you into providing your credentials so they can steal your hard earned cash.
The list below is compiled by AVG’s Web Threats Team from anonymous data from more than 200 million users and our own spam honeypot system.
If you live outside the US then your list will look fairly similar with local banks from your country taking the place of the US banks in this list.
Checking my inbox from last week I count six emails that look like they are from Paypal, inspecting the emails closely I find that two of them are fraudulent phishing emails, both trying to get my login and password.
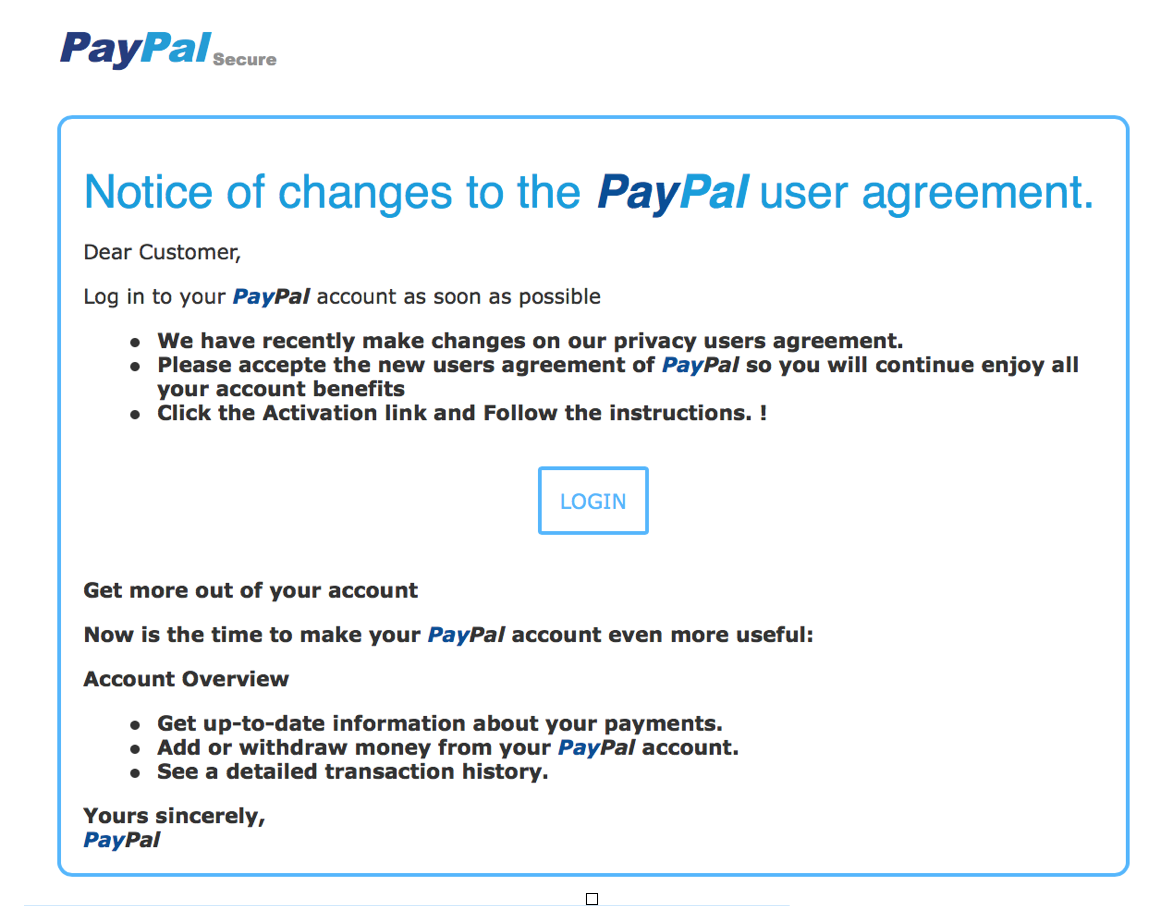
The email looks and feels as though it came from Paypal, but there are some clues that point to its true nature.
If at any point you think the email is spam and fraudulent then do not open or click on any links, just delete the email. Opening the email will download the content which the cybercriminals mark so that they know the email was opened and that your email account is active, they will send you more!
If you did click the link and you have up to date anti-virus software, such as AVG AntiVirus FREE, or AVG AntiVirus FREE for Android, then you should see a detection screen like the one below or your browser may also show a warning screen.


What do you do if you think the email was real and have not clicked or opened it, that’s an easy one. Open your browser and go to paypal.com and login. I am sure if there is important account information they need they will ask for it when you login.
It’s important to have updated Anti-Virus software, as these types of attacks use websites that change and disappear in minutes to try and hide from detection. Having up to date security software gives you the best possible chance of being protected.
All this should not put you off finding that great deal or bargain online, but I hope these tips help you check what you click on or open and visually check it looks real. I know I will be looking for that deal this week and will be delighted if I find it online so I don’t need to join the crowds in store.
![]()
![]()
Thousands of embedded devices share cryptographic keys and certificates, exposing millions of connections to man-in-the-middle attacks.
Many parents will have noticed the invasion of talking, AI-enabled toys hitting the shelves this holiday season. Once inanimate, mute objects on which we had to project personalities, movement and more, the latest high-tech toys are increasingly learning to think for themselves – with sometimes worrying consequences.
One of the most talked about recent examples of such a toy is Barbie. The beloved companion of many, Barbie recently became more interactive than ever with the launch of a Wi-Fi connected version that listens, replies and learns over time. As anyone who has heard Barbie’s suggestion to hold a “pizza party!” will well know, the power of speech isn’t new to the doll – the latest release however is branching out considerably further, combining Wi-Fi and ‘machine learning’ to be able to have entire conversations with playmates.
Much like Siri or Cortana, Hello Barbie is mic’d up and connected to a server in the Cloud which analyzes what is said to the doll and then selects an appropriate response. Learning as she goes along, Barbie mimics a real life friend by remembering details that she can drop into future replies.
While this might be every kid’s dream, it’s likely to be a real cause for concern for the more privacy and security conscious parents among us.
Much of the technology we use on a daily basis is now equipped to ‘listen’ to us in a similar manner in order to facilitate easier, more human interaction. As already mentioned, the most obvious example of this are personal assistants like Siri and Cortana which sit on our mobile devices and activate at our command. An easy enough use case to understand. What can be alarming however, is when technology not traditionally designed to listen to us is enabled to. Smart TVs, for example, have been in the press recently due to their ability to listen to conversations, capture the data and relay it to third parties. Even connected baby monitors have been called out due to their susceptibility to hacking.
As with any connected device, the debated risk is that Hello Barbie could offer an easier in for hackers attempting to intercept your Wi-Fi network. While ToyTalk which manages the toy’s cloud connection emphasizes the security measures it has taken, it also admits that ‘no device is 100% secure.’ On top of their security concerns, parents might also wonder what is happening to the data being captured as their child chats away to Barbie. Is it being stored anywhere? Yes. Is anyone listening to it? Yes. Will that child end up being bombarded with advertising for other talking toys? Hopefully not – according to ToyTalk, it does share recordings with third-party vendors, but only to improve their products. In any case, it sounds like any secret told to Barbie in confidence won’t stay that way for long!
Whether you like it or not, talking toys could be here to stay. This year, Elemental Path launched CogniToys – talking and listening dinosaurs enabled by IBM’s Watson, the famous artificially intelligent computer able to ‘understand’ human language. Another example is Ubooly, a cuddly bear described as the ‘Learning Toy that Listens’, becoming interactive once connected to a smartphone or tablet. Though only two examples, it’s just a matter of time before more of these toys hit the shelves.
So how do you feel about toys that listen? Will you be letting Barbie say hello to your child? With Christmas just around the corner, it’s worth considering the security implications of the latest high-tech toys available this season, and how connected you want your child to be.
![]()
![]()
The “Most used words” app became a Facebook hit within days of its launch. At the moment of writing this article, it has been used by nearly 18 million users globally. There are many controversies about user privacy in relation to data that is collected by the app.

“Most Used Words“ is an unexpected privacy nightmare. Source http://en.vonvon.me/
Earlier this week, the British company Comparitech published a blog post about the privacy nightmare caused by this innocent-looking Facebook app. “Most used words” is presented as a simple, playful quiz in which Facebook scans through and analyzes users‘ posts in order to generate a collection of words they use most frequently on Facebook. Sounds like fun, right? Before you try it yourself, take a closer look at this data-hungry wolf in sheep’s clothing – after some analysis of the app, it has turned out to be a privacy thief. When using the app, users give away following details:
First, the app asks for a couple basic pieces of information:
1. Name
2. Everything you’ve ever posted on your timeline
But then, it asks users to agree to give away the following personal details:
3. Profile picture, age, sex, birthday,and other public info
4. Entire friend list
5. All of the photos and photos you’re tagged in
6. Education history
7. Hometown and current city
8. Everything you’ve ever liked
9. IP address
10. Information about the device you’re using, including browser and language
Let’s face it — our concept of the privacy has unarguably changed in the age of the Internet and social media. In the digital world, we leave our fingerprints on a daily basis while browsing, shopping, playing, and chatting on multiple devices. Regardless of our online activities, there should be limits as to how companies collect, store and process our personal data. In this case, the owner of the app, South Korean company vovon.me, can be accused of a serious breach of user privacy.
What do you give away when installing “Most used words”?
According to Vonvon’s official terms and conditions, you agree to your personal information being used in the following ways:
1. Used after the termination of your membership to the website and/or use of Vonvon’s services, for any reason whatsoever. (This basically means that you already gave away your data if you used the app.)
2. Stored on any of Vonvon’s servers at any location, including the countries that have little to no legal regulations regarding data privacy.
3. Sold to the third parties, which you agreed to according to this statement: […] We do not share your Personal Information with third parties unless We have received your permission to do so, or given you notice thereof (such as by telling you about it in this Privacy Policy) […]
4. Used in any manner by the third parties, as Vonvon doesn’t take any responsibility for it: […] this Privacy Policy does not apply to the practices of entities Vonvon does not own or control, or to individuals whom Vonvon does not employ or manage, including any third parties to whom Vonvon may disclose Personal Information[…]
How to protect yourself?
We have good and bad news for you. The bad one is that if you have already installed any of Vonvon’s apps, it’s unfortunately no longer possible to protect your privacy. (See point 1 in the paragraph above.)
If you haven’t used it yet, let this be a lesson to you. The same lack of privacy concerns can also be seen in other permission-hungry apps – this is why a weather forecast app would like to have access to your pictures and a cooking app requests your IP address.
We also advise you to review the current list of apps that you have already installed on Facebook, determine if you use them on a regular basis and pinpoint what kind of data the apps are requesting from you. You can do this by doing the following:
1. Select Settings in the top right of Facebook
2. Click Apps in the left menu
3. Hover over an app or game and click to edit its settings
You can find out more about Facebook apps‘ privacy and security in the About Apps section of the Help Center.
If you are an Avast user, log in into your Avast account and go to Social Media Security > Apps — we will guide you how to analyze each of your apps‘ security.
You might be surprised how many apps you have installed throughout the years, so don’t forget to make an audit of your apps on a regular basis.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
The holiday shopping season is upon us and shoppers are flocking to the Web to find online deals and coupons. Shopping extensions for your web browser can help you find the best prices, but how do you know you are finding a great deal from a SAFE and trusted retailer?
There are several shopping tools that can help you find the lowest price from around the web, but I’ll start with the one that finds low prices and guarantees the safety and integrity of the online shop – Avast’s very own SafePrice.
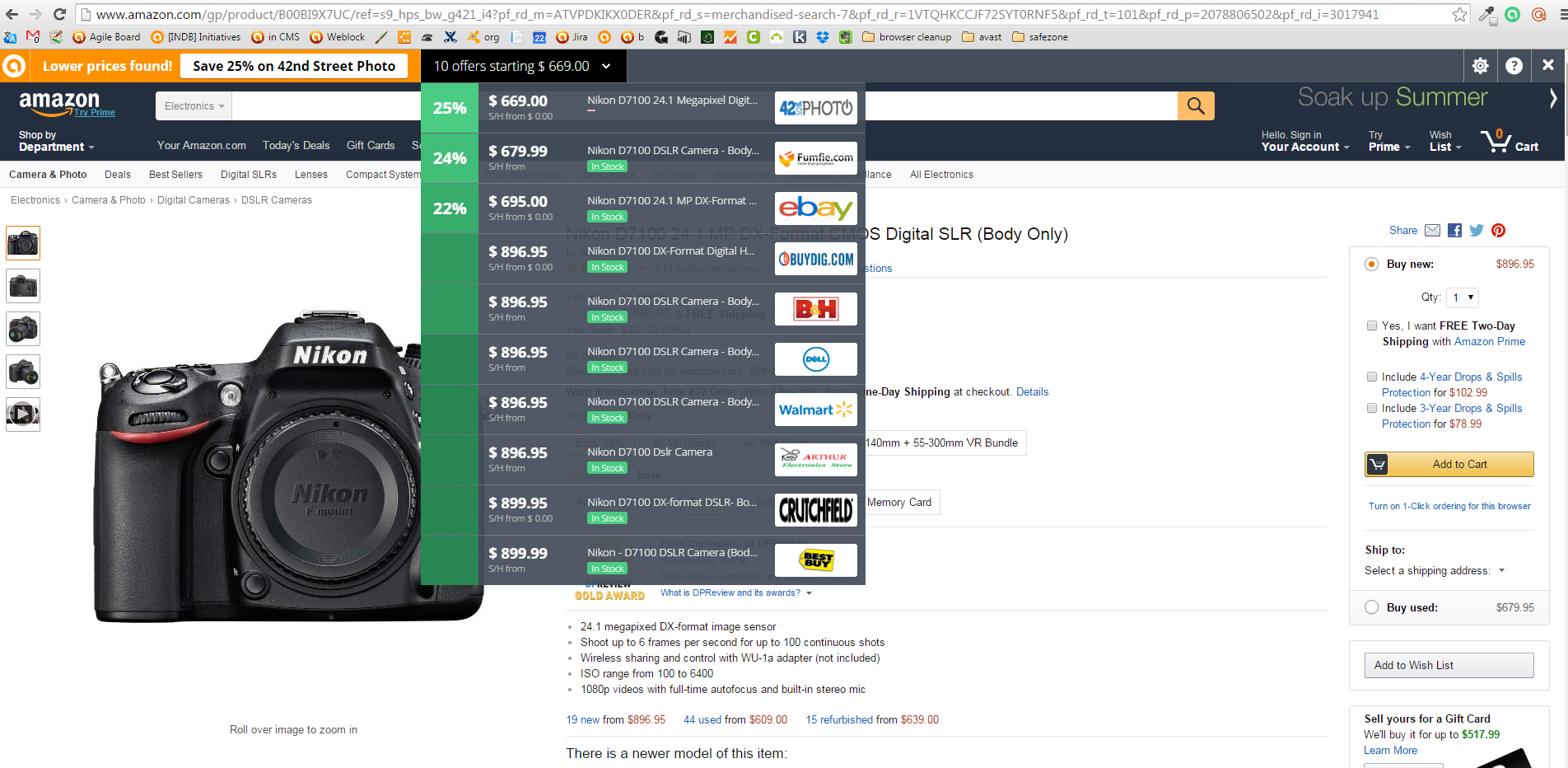
Instead of visiting price comparison sites first, all you do is go to your favorite online store and pick out what you want to buy. SafePrice checks the price against thousands of verified stores, then displays the best deals and coupons at the very top of your browser. The bar is invisible when you’re not shopping.
Avast users already have SafePrice installed. If you are not an Avast user, but wnat to use it to find trusted stores, then add the extension to Chrome from the Chrome Web Store.
 Here’s what SafePrice does:
Here’s what SafePrice does:
SafePrice will never compromise your privacy. The specific products you are searching for and the URLs of the shopping sites you visit are communicated to our server. All personally identifiable information is stripped from this data in real time, so that the data that comes into our servers is completely anonymous.
InvisibleHand
InvisibleHand discreetly notifies you if the product you’re shopping for is available more cheaply from another retailer or travel site. It also shows you deals on hotels, rental-cars, and flights. Available for Chrome and Firefox.
Honey
Click on the Honey ‘Find Savings’ button during checkout and Honey will automatically apply coupon codes to your shopping cart. Available for Chrome and Firefox.
The Camelizer
For power-shoppers, this extension lets you track product price history information for items on Amazon, Best Buy, and Newegg. If you don’t need to buy the item now, you can sign up for price drop alerts via email or Twitter. Available for Chrome and Firefox.
RetailMeNot Coupons
For those who want to shop from their Android device (last year 53% of us did!), you can install RetailMeNot and search for the top deals and coupons from over 50,000 retailers.
Read our tips for safe shopping online.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
The Internet Identity Workshop (IIW) recently held their 21st Meeting and AVG was one of the sponsors. Once again hosted at the Computer History Museum in Mountain View, California, this academic conference is focused on finding, probing and exploring the issues related to identity management.
The organizers, Phil Windley (@windley) and Kaliya Hamlin (@IdentityWoman) have managed to keep the IIW event rich with content, and suitably engaging to attract a loyal following of technical people.
The core themes of the conference were around trust, identity, privacy and technology – areas that we at AVG are very passionate about!
While a lot of users are quite proficient with the “sticky note system” for managing their internet identity, passwords and usernames – this conference by contrast is aimed at highly technical and advanced solutions that one day might provide a better and more secure alternative.
Technological advancement is happening quickly in the world of identity, and even a relatively new technology such as OAuth 2.0 is old news at IIW, with this year’s conversation all about the Blockchain – a technology utilized by the well-known cryptocurrency, Bitcoin.
Whereas previous identity recommendations have centered around technologies that look like an unbreakable-black-box, the Blockchain discussion is driven by a general consensus for complete transparency underpinned by cryptography that provides security and integrity.
The notion of using a Blockchain, which is a type of ‘distributed ledger’ offers the possibility of providing a secure history of every transaction – a chain of trust, which also acts as a permanent record of your identity that cannot be removed or tampered with.
This model of establishing trust is quite intuitive and human. We trust people who are trusted by others, and so forth. For example, it’s the way Google search rankings work (pages that link to other pages), and the way that SSL certificates are signed so you can trust your banking website.
“No, I am your father!”, from Darth Vader in Star Wars, just wouldn’t have carried the same element of surprise to Luke if they had access to Blockchain technology!
![]()
![]()
Imagine your smartphone, tablet, and TV talking about you behind your back.
The post Avira now identifies SilverPush ad-tracking as malware appeared first on Avira Blog.