The entire world population generates and saves enormous amounts of essential information every day. We do so not only to remember and look back on the past, but also, our companies and institutions need this information to run efficiently and transparently.
The entire world population generates and saves enormous amounts of essential information every day. We do so not only to remember and look back on the past, but also, our companies and institutions need this information to run efficiently and transparently.
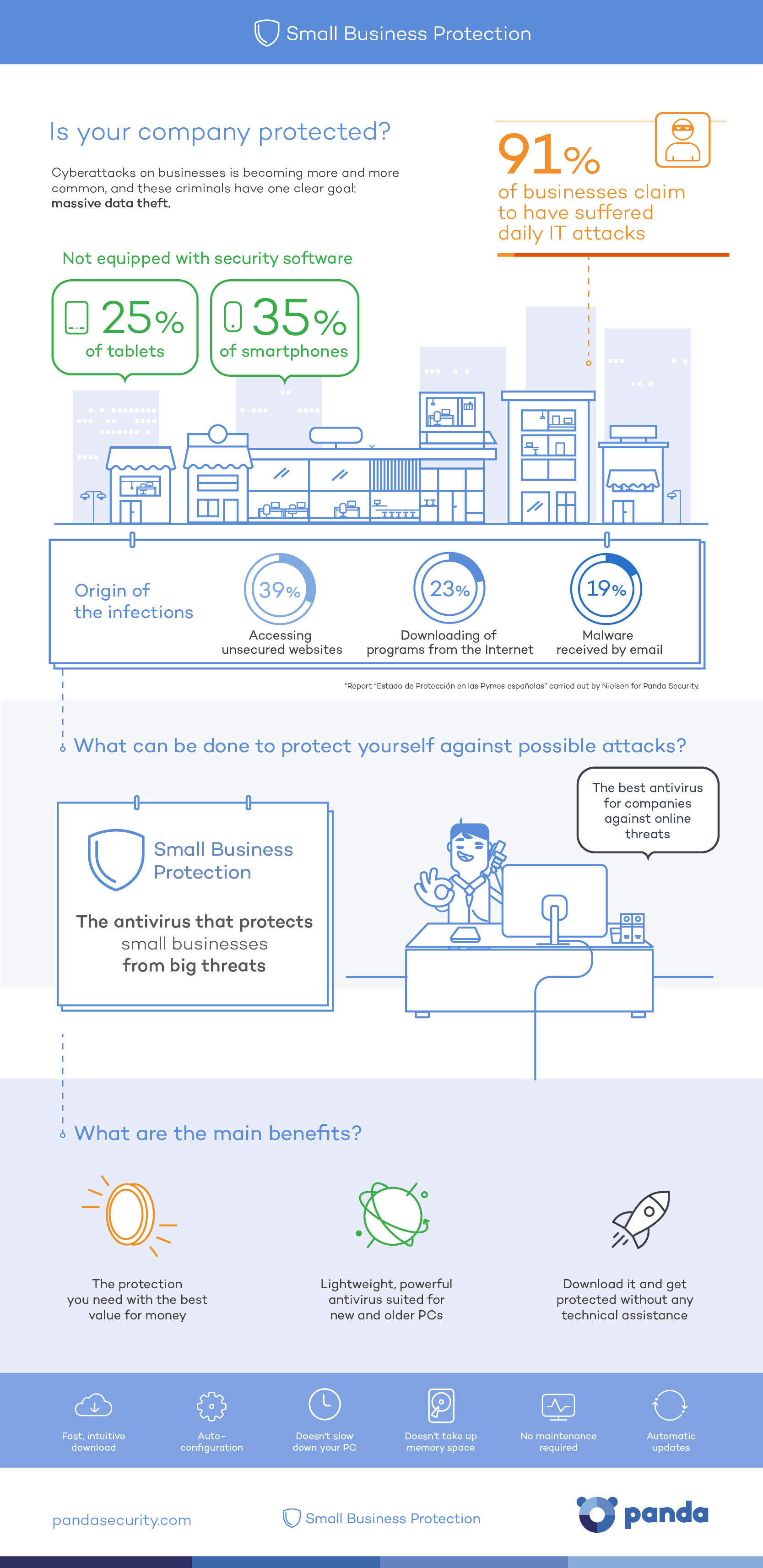
That is why today, on International Archives Day, we wish to stress the importance of safe and responsible preservation for all kinds of files and, in particular, those which contain personal information belonging to people and companies. Do not forget: although an application, a program or an operating system can be re-installed, corporate or personal information is unique and should be a top priority.
Here are some tips to keep them from falling into the clutches of cybercriminals:
Backup Files
Now more than ever, ransomware is the greatest threat for companies and individuals, which is why backups are the most fundamental tool (and the last resort). They keep us from losing valuable information in the event of a cyber-attack. It is highly recommended to keep at least two backups: one stored in the cloud and a physical one (in an external hard disk, a pen drive, etc.)
Encryption
Before uploading files to the cloud, save them in a storage device or send them by e-mail. It is recommended that you encrypt the most sensitive information, at least, so that they will not be accessible if they fall into the wrong hands. An attacker who gains hold of your files will not be able to read their contents if this person lacks the encryption key, something that only you will have the power to.
Continuous Updating
Always keep your operating system, browser and applications updated to the latest version that is available. This allows you to protect the malware that usually takes advantage of the latest vulnerabilities. Operating your computer with an older version of software makes your most confidential information at risk for theft.
Do Not Use Unknown Computers or Networks
If you go on a trip and you plan on using a computer that is not yours, or connecting your mobile device to public Wi-Fi (such as at a coffee shop or at an airport…), make sure you avoid as much as possible accessing private and sensitive files. If you connect to an open Wi-Fi and you are forced to send personal or confidential information, make sure that it is encrypted and use a virtual network (VPN). Learn how to do so, here.
Install a Good Anti-virus
At Panda, we know how important your photos, videos and other files are for you. That is why we offer file encryption, backup and information protection with our anti-virus superstar: Panda Protection Service. With Panda, nobody can hijack your data! Enjoy the rest of your day.
The post Learn how to protect your information on International Archives Day appeared first on Panda Security Mediacenter.