In this video, Tony Anscombe explains how to install AVG Protection and AVG Zen![]()
![]()
Tag Archives: protection
Is your data secure in the cloud?
It’s a very broad topic so I chose to focus my answers on three particular things.
When you put your data in the cloud, someone else holds it?
There’s a security gap between the private and public cloud. You might have invested heavily in your own private cloud or on premise systems, but data on the public cloud are not secured by you. Who controls this data? Who is responsible for it and who is accountable should something go wrong? This needs to be addressed as a priority. Consider that CTOs and CIOs must as part of SOX compliance procedures sign off on their company data being secured and under control. Yet if that data is held in the cloud and you cannot audit the security measures there, then the reality is that it is being managed by someone else – the cloud service provider.
So what we need to focus on is understanding how we can help businesses get back control of securing their data.
Cloud and mobile has changed the assumptions businesses had that they can control all the devices being used within their organizations to access their data.
With cloud services, businesses have limited authority to define what security is being used by their provider to protect their data. Company executives might not like this situation, but they will still have had to confirm that their data is secure and compliant with regulations. This is a no-win scenario for businesses.
That fact that critical data is stored on cloud services means that the business is now effectively in someone else’s hands. There is the additional challenge of how the IT department can control a situation where an employee has their own device and wants to use it to connect to this cloud-based data using tools like Salesforce, for example.
If the malware is running on that device, the IT manager is not in control of identifying and fixing that. They are in the position of having to guarantee to the business that company data is secured when in fact that might not be the case.
Hackers realized this pretty quickly. They started to target individuals within organizations when they were off the network and interacting with the cloud via a device in order to retrieve data they needed.
I expect that this risk will soon become untenable. And in the near future, that we will start to see companies pushing back on signing documents that their data stored in the cloud is secure because in reality, that data is no longer part of their business, no longer within their control.
In small to medium sized businesses, there is less likelihood they will even have any sort of systems in place to manage this and so they ultimately have less control and less confidence that their private, business data is safe in the cloud.
The Internet of Things means businesses need long-term perspective for their cloud strategy.
This brings me to this last point. If we fast forward two or even five years, and look at the impact of the Internet of Things, it’s clear we need to start thinking already about how to connect and manage these new devices and sensors for business. More importantly, we need to harness the data that is coming out of them. We’ll want them to be under control and we will all start to use services.
We also have privacy to consider. This is one of the rising stars in security. It’s a big challenge and even law enforcement agencies are becoming more active in this area.
As the panel drew to a close, I emphasized that things will start to change. Cloud service providers should start to work with their client teams on premise to give back to that business a degree of control. This will be the first step towards giving CIOs and CTOs that confidence to sign compliance documents because they will be able to verify that company data is indeed secure.
![]()
![]()
Tuning in to Cybercrime
The BBC has begun airing a six-part series, presented by British technologist, writer and “futurist†Ben Hammersley.
Called “Cybercrimes with Ben Hammersley,†the series was produced in partnership with The Open University. It looks at the range of cybercrime – from the scam emails that fill up our inboxes to drugs and guns that can be bought anonymously on what is called the shadowy business of “darknet,†and even governments spying on their own citizens.
Hammersley emphasizes that 2013 was a very bad year for cybercrime in businesses. He notes: “In February, $45 million was stolen from ATMs around the world after cyber criminals hacked credit cards and gave them unlimited withdrawal limits. Then, in November, 40 million credit card numbers were removed from the point-of-sale terminals of US retailer Target.â€
We’ve chronicled other recent major breeches here. The fact is, major data breaches are occurring at a regular pace now, and are having an impact on our most standard, or reliable, institutions.
The global annual cost of cybercrime has been estimated at several hundred billion dollars. PwC’s 2014 Global Economic Crime Survey found that 7% of US organizations lost $1 million or more due to cybercrime incidents in 2013; furthermore, 19% of US entities reported financial losses of $50,000 to $1 million.
As Hammersly points out, ” Cybercrime affects each and every one of us. Every aspect of our lives is vulnerable to the criminal abuse of our networked world…â€
It’s good to see the issue of cybercrime getting more in-depth attention in mainstream venues such as the BBC… I’m hoping there will be a large audience tuning in for what promises to be a very interesting and educational series. The more educated people are, the better equipped we all will be to protect ourselves online.
Of course, cybercrime is a major issue to us at AVG: Our mission is to secure devices, data and people – and we are always working to give people and businesses the tools and information they need to better protect themselves online. We haven’t talked about it a lot, but AVG Innovations Lab monitors current trends and develops software and apps to meet the needs of today’s consumer – as well as looks to future vulnerabilities to meet those needs too. In fact, we will be showcasing some of the work of our labs –including solutions to growing threats in mobile and the Internet of Things– during a press-only event we are calling “AVG Experiential Lab,†in San Francisco on Sept. 18.
![]()
![]()
Protection for your family, plain and simple
Sadly, the hassle of managing the family technology is only going to get greater. The number of connected devices in our homes is growing rapidly. In 2013, the average home already had more than five connected devices. Homes like mine, with more than 20 devices, are driving this average up with every passing day.
As we start to realize that our families are spending so much time online, it is our responsibility as parents to ensure that they are doing so safely. Then the long to-do list of Internet safety comes into focus.
Our tablet has run out of space? Has my son set his privacy setting correctly on social media accounts? Is the security software on my own phone updated? What can I do to speed up my wife’s laptop?
As our list of devices continues to grow, so too does the to-do list of the family tech wiz.
There must be a simpler way to manage my family’s devices without having to actually track down each device every time I want to do something.
That’s why for 2015, AVG is launching AVG Protection: the one-stop solution to help me keep my family protected across all our devices—no matter how many—wherever we are.
AVG Protection brings together our best security products for all platforms: AVG Internet Security for Windows desktop, laptops and tablets; AVG AntiVirus for Android smartphones and tablets; and AVG AntiVirus for Mac under a single subscription. Add to this AVG PrivacyFix and AVG Cleaner for Mac and Android, which are free, to complete my protection, performance and privacy needs — the solution is a compelling one.
But most importantly, AVG Protection has AVG Zen to tie them all together. AVG Zen allows me to manage all of our devices from one screen, fix issues, scan machines, and enable protection remotely from my PC or my Android device when mobile. And the alerting system lets me know when something needs my attention so I can rest assured my family is safe online. The days of checking up on each of my direct family or my extended family devices one by one are over.
It couldn’t be easier to start protecting your family using AVG Protection, click here to get started.
![]()
![]()
How many devices do you have in your home?
It’s probably more than you think. There are the obvious ones such as laptops, tablets and smartphones. But did you think of your smart TV, games console or even your refrigerator? Our homes are very quickly becoming digital environments with dozens of connected devices making up what is known as The Internet of Things.
You may have already heard of devices such as Nest that offer smart solutions to everyday functions like heating your home, but while it may sound futuristic, it is very much part of reality. As an industry, the Internet of Things was already worth well over $30 billion in 2013 and is set to surpass $70 billion by 2018.
The transition to a digitally connected world has well and truly begun. Whether you track your daily activity using a fitness wearable, have your home alarm system linked to your phone or simply stream movies to your television, that’s all part of living in an increasingly connected world.
In an ideal world, this connectivity would be seamless and integrated. In reality though, each of these connected devices are being developed in isolation across dozens of different verticals. The end result is a fractured market that can make it confusing and difficult for you to keep track of all your devices.
There must be an easier way. A simple product that can help you control your personal Internet of Things without the hassle of managing each one individually.
And that’s the idea behind AVG Zen™. We want to make managing your digital world as simple as possible. We want to avoid the culture of countless notifications, constantly prompting you and pulling you back to manage your devices. The idea behind AVG Zen is to offer peace of mind.
The vision is that someday, AVG Zen will help you track all of the devices on your personal Internet of Things. Today, AVG Zen is already a powerful tool that can take much of the hassle out of managing your many devices (and those of your family).
As a central dashboard, AVG Zen allows you to monitor and manage the security and performance of your devices by adding them to your AVG Zen network. It’s an incredibly easy and powerful way to ensure that your PCs, Mac and Android devices are locked down and running smoothly.
That’s AVG Zen – and we are working to ensure it will continue to bring peace of mind to  your connected world as that world continues to grow.
![]()
![]()
AVG Technologies Launches 2015 Products
AMSTERDAM and SAN FRANCISCO – November 4, 2014 – AVG® Technologies N.V. (NYSE: AVG), the online security company™ for 182 million active users, today announced the availability of its 2015 portfolio of protection, performance and privacy products. This includes the new all-in-one AVG Protection and AVG Performance suites for PCs, Android devices and Apple devices, and AVG Ultimate, which includes both protection and performance suites in a single package. These come with the latest version of AVG Zen®, the app for Windows PCs and Android smartphones and tablets that makes it simple for consumers to look after their own and their family’s devices.
What’s new in AVG Zen
AVG Zen can be downloaded from the Google Play store or when installing AVG Protection, AVG Performance, or AVG Ultimate. It shows at a glance the full status of the Protection or Performance settings customers have on the PCs, Android devices, and Mac computers they have added to the AVG Zen network.
AVG Zen’s refreshed look and feel for the 2015 products means users can easily:
- Add an unlimited number of their family’s devices.
- Run a scan remotely from their mobile device to their PC (and vice versa), other mobile device or Mac computer.
- Run Automatic Maintenance on Windows PCs and laptops remotely or check up on Android devices and Mac computers.
- Easily access individual products, such as AVG AntiVirus or AVG PC TuneUp®, directly from AVG Zen.
Yuval Ben-Itzhak, Chief Technology Officer, AVG Technologies said, “AVG Zen is designed to make it easy to manage the necessary maintenance and updating that keeps people’s favorite online devices working at their best simple. In the last few months, we have added some key features to AVG Zen, including being able to scan and fix issues on a device remotely, and offering all-in-one packages for full device protection and performance improvement. The Internet of Things is exploding with smart home revenues expected to reach a global market value of $71 billion by 2018. We see great potential for AVG Zen to become a household fixture that simplifies and makes this online experience more meaningful.â€
AVG Protection: includes AVG AntiVirus or AVG Internet Security, AVG AntiVirus for Mac®, AVG PrivacyFix™ and more, all-in-one package
AVG Protection delivers the latest versions and full range of AVG’s Protection products for desktop and mobile in a single suite, without the customer having to purchase the individual products. With AVG Zen, all PCs and mobile devices running AVG Protection products can be monitored for security issues. The new Remote Actions feature also helps users fix security problems, such as remotely enabling security features that have been disabled on one from another device, such as a PC or Android smartphone.
AVG Protection includes:
- AVG Internet Security: now delivers even earlier detection methods with our new outbreak detection and priority updates.
- AVG AntiVirus for Android: customers get the same great experience on their Android tablets as on their mobile devices. This includes locate, lock and remote wipe a smartphone using the Anti-Theft feature if it has been stolen. It also features app lock and backup, privacy settings for social media, call and message blocker and wipe device for improved online privacy.
Customers purchasing the AVG Protection subscription will receive the PRO products including AVG Internet Security. They can also add the devices of family members to their AVG Zen Network to share all the PRO benefits at no extra cost. The PRO subscription for unlimited PCs and mobile devices is $59.99 for one year, with the individual products also available. AVG Protection is also available as a 30-day trial from www.avg.com/protection.
AVG Performance: includes new AVG PC TuneUp®, AVG Cleaner, AVG Cleaner for Mac, AVG Cleaner™ for iOS® and more, all-in-one package
AVG Performance brings together all of AVG’s hero performance products in one single place, AVG Zen, for ease of use. It includes software and mobile apps to keep PCs or laptops running Windows, smartphones and tablets running Android, Mac computers and now even iPhones and iPads in top shape, an all-in-one performance suite that covers all popular platforms on the market. AVG Zen makes it simple to check the status of all the devices in the home and clean PCs remotely from a smartphone or a secondary PC.
AVG Performance includes:
- AVG PC TuneUp: AVG’s award-winning version includes 39 tools to speed up, fix up, clean up, and enhance battery life of all Windows® PCs and laptops with features like Automatic Maintenance, Program Deactivator and Economy Mode. The all-new AVG Cleaner for iOS feature safely removes leftover files from iPhone and iPads once plugged into any Windows PC and laptop. It also removes redundant files, such as corrupt downloads, temporary files, or invisible crash reports, helping free up space for their personal data or to install the new iOS updates. The Disk Cleaner feature has also been significantly enhanced support has been added to clean up leftover files from popular gaming platforms Steam and Origin, Skype, nVidia/Intel/AMD drivers as well as iTunes and Quicktime.
- AVG Cleaner for Android: with the new ‘large file scanner’, users can scan their Android phones for storage hogs, such as old downloads or videos in addition to enhancing battery life with ‘Battery Profiles’ and thorough cache cleaning. AVG Cleaner for Mac scans disks and looks for leftover files from Mac OS X and programs as well as duplicates that users may have forgotten about.
AVG Performance is available as a 30-day trial from www.avg.com/performance. The PRO subscription for unlimited PCs and mobile devices is $39.99 for one year, with the individual products also available.
AVG Ultimate is available as a 30-day trial from www.avg.com/ultimate. The PRO subscription for unlimited PCs and mobile devices comes in at $89.99 for one year. The individual products are also available.
AVG Zen with AVG Protection, AVG Performance and AVG Ultimate are available to customers in Canada, Germany, Ireland, Spain, UK, US.
###
About AVG Technologies (NYSE: AVG)
AVG is the online security company providing leading software and services to secure devices, data and people. AVG has over 182 million active users, as of June 30, 2014, using AVG’s products and services including Internet security, performance optimization, and personal privacy and identity protection. By choosing AVG’s products, users become part of a trusted global community that engages directly with AVG to provide feedback and offer mutual support to other customers.
All third party trademarks are the property of their respective owners. AVG does not claim any affiliation, sponsorship or endorsement by such third parties of AVG products.
Â

Yuval Ben-Itzhak, CTO, AVG Technologies
Â
Contacts:
US
Katie Han
Waggener Edstrom for AVG
+ 1 (212) 551 4807
UK
Samantha Woodman
Waggener Edstrom for AVG
+ 44 (0)20 7632 3840
Â
Keep in touch with AVG
![]()
![]()
AVG 2015 Protection Update
Reviewers Guide:
Images:
![]()
![]()
Don’t fall for these scams this Halloween!
Facebook Reset Scam
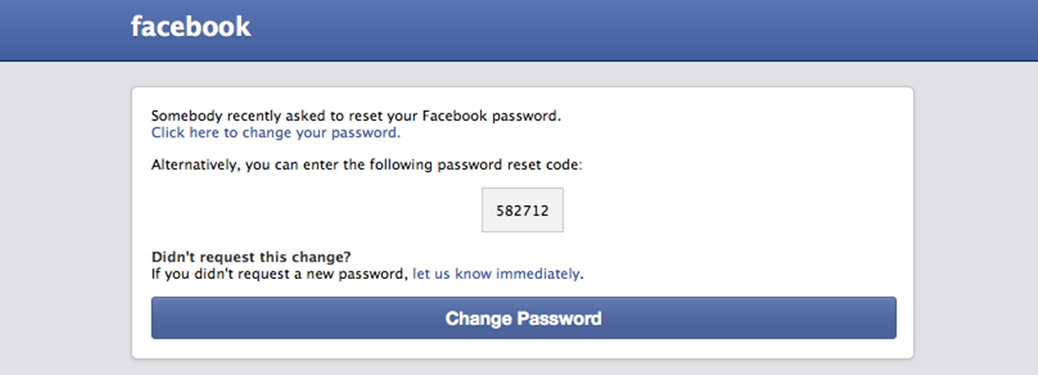
The Facebook reset requests arrived via email and text message: “Somebody asked to reset your Facebook password.†At first it was annoying; then it was worrisome – a possible scam/phishing target.
Facebook says that these alerts are sometimes triggered due to a person mistakenly entering the same name and then, when their password doesn’t work, the customer asks for a reset. That might be possible in certain cases, but just based on the constant messaging, this was clearly beyond a normal user mistake, and an imitator scam.
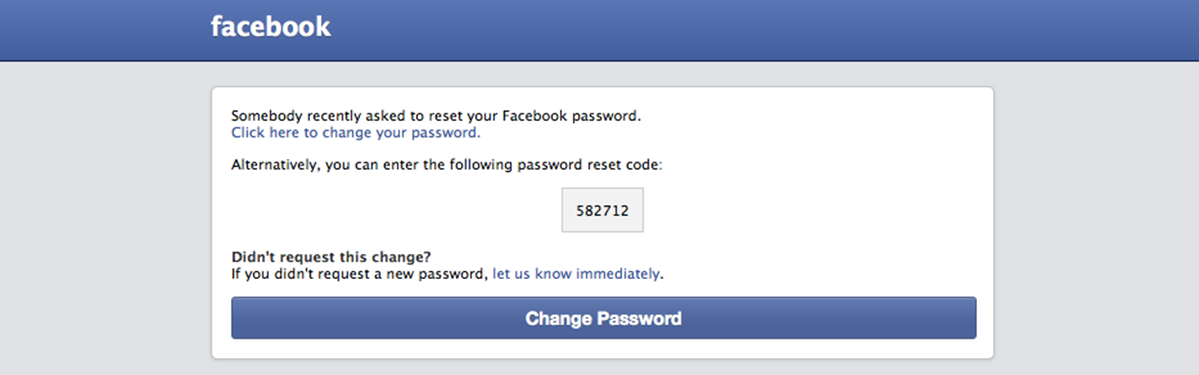
Let’s set aside the fact that although I have unlimited mobile data, many people don’t, and would end up paying for these unwanted texts. What’s more problematic is thinking about the many users who unsuspectingly fall for the request, click away and sign away their passwords.
Facebook says it will never ask you for your password, so if this happens to you, resist the urge to click. Any time you receive an urgent call to action in an email, be wary.  Don’t click on links contained in emails as a general rule. Instead, go to Facebook manually and look at the notifications. Needless to say, keep your anti-virus software up-to-date and use a password manager to keep your passwords safe and secure.
Facebook itself advocates the following steps:
- Use an up-to-date browser
- Use unique logins and passwords for each of the websites you use.
- Check to see that you’re logging in from a legitimate Facebook page with the facebook.com domain.
- Be cautious of any message, post or link you find on Facebook that looks suspicious or requires an additional login.
IRS and Other Scary Calls
You might imagine getting a voice message from the IRS wouldn’t be good news. And it’s not! This is a current scam making the rounds: Someone claiming to be an officer of the Internal Revenue Office leaves a message for you or your legal representative to call their hotline regarding an extremely time sensitive issue – before they take legal action. I was immediately suspicious: Would the IRS really leave me a phone message if there were an issue? The answer is “No.â€
What’s really scary is that the IRS reported in August 2014 it had received 90,000 complaints and identified approximately 1,100 people who have fallen victim, given up credit card numbers, etc. and lost an estimated $5 million from these scams.  You can learn more about the same on IRS. gov.
Fast forward to another cell scam: persistent calls received from an unknown number in the local area code. No voicemails were left. But after the calling persisted several times a day for a few days, you become curious as to who was calling. When I rang the number I got a “This number has been disconnected†message…
Lots of research later and it’s unclear as to whether this is just some weird harassment or part of the “One-ring†cell phone scam that the FTC has issued warnings about. In the latter scenario, scammers are using auto-dialers to call cell phone numbers across the country. They let the phone ring once and hang up — hoping you’ll call back, either because you believe a legitimate call was cut off, or you will be curious about who called. If you do, chances are you’ll hear something like, “Hello. You’ve reached the operator, please hold.†While waiting, you rack up some hefty charges — a per-minute charge on top of an international rate. The FTC notes: There’s no danger in getting the call: the danger is in calling back and racking up a whopping bill. If you’re tempted to call back, try checking the number first through online. Go here to learn more.
As for persistent calls, you can block them. You can block calls on both Android and iOS phones. On an iPhone look on your list of recent calls, just click the “i” in the circle to the right of the number. It will open an info tab, just scroll to the bottom and click block number. You should also report the number to your service provide (AT&T, Verizon, etc.) to get them blocked there.Halloween comes and goes, but scary scams will continue, and it requires a higher level of awareness from all of us! Check out AVG’s Facebook page for ongoing alerts and simple tips to help your friends be more safe online!
![]()
![]()
What kids want to know about Internet Safety
Who are you and why are you here?
Maddie: My name is Maddie Moate and I am a YouTube Presenter, I make lots of videos mostly about science and technology. I know quite a lot about social media, and how to stay safe using technology. That’s why I’ve been invited here today.
Luke: I’m Luke Franks and I’m a presenter, I present shows on live kids TV but also do the online X-Factor. I spend a lot of time online, on social media in particular so I’ve come along today to talk to people about how they can do that in a safe way.
Have you ever been cyberbullied? Do you think there are ways to stop cyberbullying?
L: I don’t think I’ve ever been cyberbullied, but I’ve had people send me some nasty messages. They don’t make you feel good when you read them. I think the best thing you can do is talk to an adult, either your parents or someone at school who you trust. It’s not okay and it shouldn’t happen!
M: Totally. Just because it is happening online doesn’t mean that it’s okay. It’s just as bad as bullying in real life. I’ve had a couple of instances where people say not very nice things to me on YouTube. It can be very difficult but it’s important to remember that you don’t have to handle it by yourself. Look for some support.

What are the pros and cons of social media?
L: Good question. One of the best things about social media is that it’s a very easy way to share things with your friends and build a place online where you can all hang out.
M: Yeah, it’s a great way of sharing photos and memories with friends and family who might live far away. But these days it’s very common to be part of bigger communities that share wider interests or passions for activities, brands or music.
L: Exactly. One of the great things about YouTube is that it can also be a great learning tool. Let’s say you wanted to learn the guitar. You can go onto YouTube and find hundreds of free lessons that will teach you exactly what you want to learn.
And the cons?
L: There are definitely some cons. You don’t always necessarily know who is online or who you are talking to. So you have to be aware and be careful about what you are putting online.
M: There are also lots of people who see what you do online but aren’t speaking up. It’s easy to think that you are just talking to certain people but actually your messages can be seen by many more than you think.
How do you keep safe on the Internet?
M: Check your privacy settings. You want to make sure that what you are posting can only be seen by the people you want to read it. Remember that anything you put online can be discovered, so try and make sure that you are showing a good representation of yourself.
L: Yeah, settings can be quite complicated sometimes but it’s worth checking them from time to time to make sure you’re not sharing with too many people.
Can someone be addicted to technology?
M: Yes! Definitely.
L: I think you can. I spend so much time on my phone and I love tweeting and finding out about stuff online. But there’s a real world too and it’s important to learn skills for the real world and not just online. You can’t stay on your phone forever!
M: It can be very easy for people to get addicted to creating an online personality or life that doesn’t actually exist. It can seem more exciting online where you might be more cool or popular but actually the most important thing is to look after the real you in the real world.
![]()
![]()
Good News from the Government
With all the data breaches making headline news, and more importantly, affecting millions of Americans, the Obama administration announced a strong government plan to add security for debit cards that are used for federal benefits such as Social Security.
Specifically, in an executive order signed at the Consumer Financial Protection Bureau, President Obama ordered that government agencies that process payments employ enhanced security features.
Those measures include launching a chip and PIN initiative that the government has named “BuySecure†initiative. Chip and PIN means that secure information is embedded in a chip in a credit card and users must enter a PIN number in order to use the card, much like they currently do with a debit card. The President moved without Congress on this one, which if anything highlights the importance and the need for haste in this matter.
Chip and PIN reduces the chance of fraud, as I pointed out in an earlier post (see here).
The point is that smart cards are revamped credit cards with microchips that store your data on the card. Chips are better than magnetic strips because the strips use the same technology as a cassette tape (remember those?) and thus are easy to copy. But chips generate a unique code each time they are used. So, while criminals can still steal your card and still commit fraud and sell data, they can’t copy your card and create more fraudulent ones under your name. It’s a big step in the secure data direction.
The major catch with the chip cards, until now, is that most retailers don’t have the technology for them just yet. The main companies that have had breaches have announced plans to install the new technology (this includes Home Depot, Target, etc., and it is also interesting to note that Walmart was ahead of the curve on this one).
But no doubt with the government behind this movement, it’s going to push this technology and added security into the mainstream, essentially making it the new way of doing business via credit.
Thus far there has been some foot-dragging on chips, not just because retailers will have to upscale to the new technology, but also as banks and retailers have argued over who is in fact responsible for security. This should definitely speed up, and resolve, the process.
“There is a need to act and [to] move our economy toward stronger, more secure technologies that better secure transactions and safeguard sensitive data,†the White House said in a statement.
President Obama, speaking about the motivation behind the order, said, “Identity theft is now America’s fastest growing crime. These crimes don’t just cost companies and consumers billions of dollars every year; they also threaten the economic security of middle-class Americans who worked really hard for a lifetime to build some sort of security.â€
AVG is glad that the government recognizes identity theft, cyber security, and data breaches as increasingly crucial problems. These are definitely issues that is not only a drag on the economy and businesses, but also affect peoples’ lives, and livelihood. I applaud the President’s bold move on chip and PIN.
![]()
![]()