The latest ESET discovery of the first known Android lock-screen-type ransomware that spreads in the wild and sets the phone’s PIN lock is examined.
The post Aggressive Android ransomware spreading in the USA appeared first on We Live Security.
![]()
The latest ESET discovery of the first known Android lock-screen-type ransomware that spreads in the wild and sets the phone’s PIN lock is examined.
The post Aggressive Android ransomware spreading in the USA appeared first on We Live Security.
![]()
Another Android threat similar to the well-known Koler A from last year is causing panic among Android users. The family is detected by Avira as Android/Locker.A and has tens of thousands of variants, with new ones created every day.
The post Phones Under Attack By New Mobile Ransomware appeared first on Avira Blog.

Chinese jailbroken iPhone users targeted
In what has been called the biggest iPhone hack ever, 250,000 Apple accounts were hijacked. That’s the bad news.
The good news is that most Apple device users are safe. Why? Because the malware dubbed KeyRaider by researchers at Palo Alto Networks, only infects “jailbroken” iOS devices. (there’s that bad news again)
When you jailbreak a device like an iPhone or iPad, it unlocks the device so you can do more with it like customize the look and ringtones, install apps the Apple normally would not allow, and even switch carriers!
The KeyRaider malware entered the jailbroken iPhones and iPads via Cydia, a compatible but unauthorized app store, which allows people to download apps that didn’t meet Apple’s content guidelines onto their devices. The malware intercepts iTunes traffic on the device to steal data like Apple passwords, usernames, and device GUID (“Globally Unique Identifier” which is your ID number similar to your car’s VIN). Users reported that hackers used their stolen Apple accounts to download applications from the official App Store and make in-app purchases without paying. At least one incident of ransomware was reported.
Chinese iPhone users with jailbroken phones where the primary attack target, but researchers also found incidents in 17 other countries including the United States, France, and Russia.
The best way to protect yourself from KeyRaider and similar malware is to keep your iPhone or iPad the way it was intended, that means never jailbreaking your device.
The researchers who discovered this malware offer a service on their website to query whether your Apple account was stolen.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
CoreBot is new information-stealing malware in the wild with a modular design that could turn the credential-stealing malware into something much worse.
A rash of compromised WordPress websites is behind this week’s surge in Neutrino Exploit Kit traffic
A SANS ISC report indicates a prominent cybercrime group has begun using the Neutrino Exploit Kit, but that hardly spells the end of the road for the notorious Angler EK.
This week’s episode of Mr. Robot continued from where it left off last week, focusing on the show’s characters rather than hacking methods. We see Elliot struggle with himself as he figures out that Mr. Robot is his dad (who died years ago), who he has been imagining in his mind. Meanwhile, Tyrell’s world is crumbling. His wife gave birth to a baby boy, but tells him she does not want to be with him unless he “fixes things”. He then gets fired from E Corp and remains as the prime suspect in Sharon’s murder investigation. It doesn’t look like Tyrell did a very good job of fixing things, if you ask me…
Despite the lack of hacking, I did have a few questions about the final scene of the episode. I spoke with my colleague, senior malware analyst Jaromir Horejsi, who helped me better understand FSociety’s plan.

In the last scene of the episode, Tyrell pays Elliot a visit. Tyrell tells Elliot about how he murdered Sharon and how surprisingly good that felt. Elliot then decides to tell Tyrell about his plan to take down E Corp. Elliot explains to him that by encrypting all of E Corp’s files, all of their financial records will be impossible to access as the encryption key will self-delete after the process completes.
Stefanie: Clearly, E Corp is in some pretty big trouble if this plan succeeds, but could something like this happen to the average user? How disastrous would it be if, for example, if my personal computer’s data were to be encrypted?
Jaromir: Ransomware is a common and nasty form of malware that encrypts data and demands a ransom, as the name suggests. We have seen many cases of ransomware on PCs and mobile devices. Encrypted data is impossible to decrypt unless you have the encryption key, which is pretty disastrous if you ask me.
Stefanie: What is an encryption key and what should I do if my data is encrypted by ransomware?
Jaromir: An encryption key is information that is needed for the functional output of a cryptographic algorithm or cipher. You can think of encryption as a vault or door that is locked and the encryption key is the key or combination to open the vault or door, and in the case of encryption, to decrypt data. If your device is infected with ransomware you can a) delete the ransomware by using an antivirus rescue disc, b) reboot into safe mode and remove it manually or c) reboot using another operating system stored on an external disc. Once this is done, you can restore your data, using your backed up files. This is why it is important to always back up your data! More importantly, you should have antivirus software installed on all of your devices — PC and mobile — to prevent ransomware from infecting your device in the first place!
We highly discourage paying ransom, as this proves to cybercriminals that their methods are effective and encourages them to continue spreading ransomware.
Stefanie: What happens to the encryption key in ransomware? Does it also self-delete?
Jaromir: If cybercriminals do their job correctly, so to speak, the encryption key should be deleted by the ransomware, similar to what Elliot programed his encryption program to do. Ransomware typically generates a key and uses it to encrypt files. The ransomware then encrypts the encryption key with the attacker’s public key and sends the encrypted key to the attacker. Once this is done,and the files on the infected device are encrypted, the ransomware securely deletes the encryption key from the infected device, meaning that the attacker is the only one who has the encryption key that can decrypt the encrypted files on the infected device.
Thank you, Jaromir, for taking the time to speak with me. ![]()
What did you guys think of the episode? Let us know in the comments below!
![]()
 It is frustrating when your antivirus protection stops you from visiting a website that you know and trust, but these days even the most popular websites can fall prey to attacks.
It is frustrating when your antivirus protection stops you from visiting a website that you know and trust, but these days even the most popular websites can fall prey to attacks.
This week security researchers discovered booby-trapped advertisements on popular websites including eBay, The Drudge Report, weather.com, and AOL. The ads, some of which can be initiated by a drive-by attack without the user’s knowledge or even any action, infected computers with adware or locked them down with ransomware.
Computer users running older browsers or unpatched software are more likely to get infected with malware just by visiting a website. Avast blocks these infected ads, but to be safe, please use the most updated version. To update your Avast, right-click the Avast Antivirus icon in the systems tray at the bottom-right corner of your desktop. From the menu, select Update.
“This kind of malvertising is a fairly easy way for cybercriminals to deliver adware or another malicious payload. Many websites sell advertising space to ad networks then deliver the targeted ads to your screen,” said Avast Virus Lab researcher Honza Zika. “All Avast users with current virus databases are fully protected against this attack, but those without protection or up-to-date security patches run the risk of being infected with ransomware.”
Malicious ads have appeared on legitimate websites for years now. In 2010, Jiri Sejtko, the director of Avast Virus Labs reported on ads poisoning and predicted that “The ad infiltration method is growing in popularity alongside with the web site infections. Now we are facing probably the biggest ad poisoning ever made.” In the years following, many legitimate sites have suffered this attack notably Reuters, Yahoo, and Youtube.
For a more technical explanation of how infected ad networks work, read the study done by Avast Virus Lab analysts, Malvertising and OpenX servers.
Since infected ads can appear on legitimate sites that you normally visit with no problem, you have to trust your antivirus protection to do it’s job. Here are some steps you can take to protect yourself’
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
Spam messages spoofing Microsoft and promising a free Windows 10 upgrade instead drop the CTB-Locker crypto-ransomware on compromised machines.
It’s a common belief (and myth) that Apple products are invincible against malware. This false line of thinking has recently again been refuted, as iPhone and iPad users have been encountering a ransomware threat that freezes their Internet browsers, rendering their devices unusable. The ploy, commonly known as iScam, urges victims to call a number and pay $80 as a ransom to fix their device. When users visit an infected page while browsing using the Safari application, a message is displayed saying that the device’s iOS has crashed “due to a third party application” in their phone. The users are then directed to contact customer support to fix the issue.
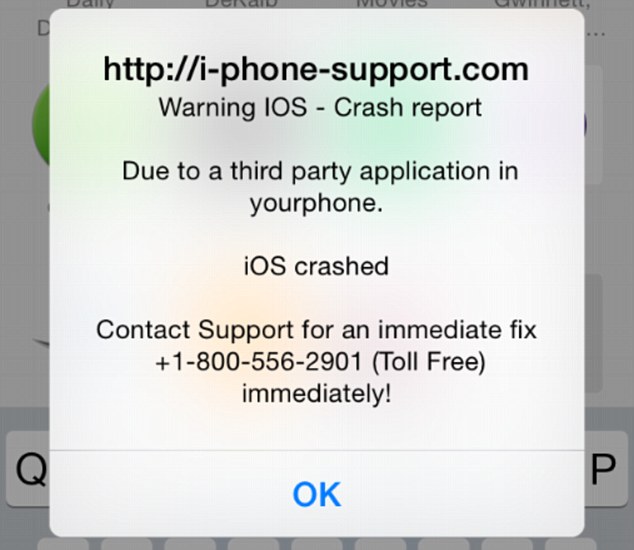
iScam displays a “crash report” to affected users. (Photo via Daily Mail)
In the midst of this vexing threat, Avast’s suite of security applications identifies URLs which contain malicious content. When discovered, these addresses are flagged for malware and then stored in our blacklist database.
While scanning for malicious URLs, we discovered that many of the servers related to iScam are located in the United States. While iScam has affected users located in both the U.S. and U.K., the origins of the threat have remained fairly nebulous up until this point. Here are a few examples of where we’ve discovered malicious servers in the U.S.:
Every cloud has a silver lining – in this case, you can celebrate the fact that you’re protected from iScam using Avast SecureLine VPN. Not only does Avast SecureLine VPN protect you while browsing on unprotected Wi-Fi networks, but it also scans websites to check for malicious content and keep you from becoming affected by them. Once Avast SecureLine VPN is installed onto your iPhone or iPad, it automatically notifies you of the risks of connecting to unsecured Wi-Fi and you have the option of connecting to the secure VPN. Once turned on, Avast SecureLine VPN creates a private ‘tunnel’ for your data to travel through, and all your activities done over the Internet – inbound and outbound through the tunnel — are encrypted. If a website is infected with iScam, Avast SecureLine VPN blocks it, so users will not encounter the scam. For your best protection, Avast SecureLine VPN is available to download in iTunes.
Check out Apple’s support forum for additional tips on how to keep your device safe while using Safari.
![]()