Research spot SoakSoak botnets spreading the Neutrino Exploit Kit that in turn infect the unsuspecting with the CryptXXX ransomware.
Tag Archives: ransomware
Jackware: When connected cars meet ransomware
Beware jackware, malicious software that seeks to take control of a device, the primary purpose of which is not data processing or digital communications.
The post Jackware: When connected cars meet ransomware appeared first on We Live Security.
![]()
Finally: Avira launches Mac Antivirus Pro!
We are happy to finally announce Mac Antivirus Pro, the premium version of our free AV security software for Apple OS X devices.
The post Finally: Avira launches Mac Antivirus Pro! appeared first on Avira Blog.
Tales from Ransomwhere
Last week, Pandalabs received a question about a specific family of ransomware that was using PowerShell, a Microsoft tool that is included in Windows 10 and that has been abused by cybercriminals for some time. We get these questions every now and then, we find those questions amusing as we consider ourselves the best ones stopping ransomware attacks. But to be honest I must admit we do not write that much about it as we should, we don’t share all our findings with the community, which is why we have decided to do it on a regular basis from now on in this “Tales of Ransomwhere” series.
it comes via a phishing email that has a Word document attached
The specific ransomware we were asked about sounded like old news to us, and in fact, our colleagues from Carbon Black wrote about it back in March. The attack flow is easy to follow: it comes via a phishing email that has a Word document attached. Once opened, a macro in the document will run cmd.exe to execute PowerShell, first to download a script from the Internet, and then will run PowerShell again using that downloaded script as input to perform the ransomware tasks.
This Powerware, as named by Carbon Black, is yet another ransomware of the thousands we see. We were blocking it even before we were aware of this particular family (as in 99.99% of the cases, did I already mention we are the best ones in the world stopping ransomware attacks?) although I have to admit that for some security companies this particular family is a bigger challenger than the rest. Why is that? Well, a number of these “Next Generation AVs” or whatever they call themselves, rely a lot on signatures (wait, weren’t they the ones that claim they do not use signatures?!?!) and at the same time their presence is stronger at the perimeter than at the endpoint. And as you can imagine, blocking Word documents at the perimeter is not really convenient. Once they have infected some customers they can add signatures and protect the rest (like blocking IPs where the script is being downloaded from) although the lack of a malware executable being downloaded from the Internet is a nightmare for them.
At the end of the day ransomware is a hell of a business for cybercriminals, and as such they invest a lot of resources into finding new ways to stay undetected by all kind of security solutions, being this Powerware just one example. The general behavior doesn’t change, but there are always subtle changes at least every week. These changes can apply to the ransomware itself (how it performs its actions) or the delivery (using new exploits, changing known exploits, changing the payload of the exploits, etc.)
A good example of new delivery methods is one we have seen recently: after exploiting Internet Explorer, it is executed CMD using the “echo” feature to create a script. Then a number of Windows files are executed in order to perform all actions to avoid detection of suspicious behavior by security solutions. The script is run by wscript, and it downloads a dll, then it uses CMD to run regsvr32, that will execute the dll (using rundll32). In most cases that DLL is a ransomware, so far we have blocked +500 infection attempts using this new trick.
so far we have blocked +500 infection attempts using this new trick
We haven’t looked at the exploit used (we really don’t care a lot as long as we are blocking it) but given the timeframe where this infection attempts have shown up (first on June 27th) it happened when AnglerEK had already disappeared, so probably attackers are using either Neutrino or Magnitude.
Every time we see something new like this, someone ends up publishing information about it a month later, so I am afraid we may have screwed up someone’s research, or at least it won’t look that new. To make up for it I have listed all the MD5s of the DLLs we have captured in the wild in those +500 infection attempts:
00d3a3cb7d003af0f52931f192998508
09fc4f2a6c05b3ab376fb310687099ce
1c0157ee4b861fc5887066dfc73fc3d7
1cda5e5de6518f68bf98dfcca04d1349
1db843ac14739bc2a3c91f652299538c
2c5550778d44df9a888382f32c519fe9
2dcb1a7b095124fa73a1a4bb9c2d5cb6
2f2ca33e04b5ac622a223d63a97192d2
38fb46845c2c135e2ccb41a199adbc2a
3ac5e4ca28f8a29c3d3234a034478766
4cb6c65f56eb4f6ddaebb4efc17a2227
562bf2f632f2662d144aad4dafc8e316
63dafdf41b6ff02267b62678829a44bb
67661eb72256b8f36deac4d9c0937f81
6dbc10dfa1ce3fb2ba8815a6a2fa0688
70e3abaf6175c470b384e7fd66f4ce39
783997157aee40be5674486a90ce09f2
7981aab439e80b89a461d6bf67582401
821b409d6b6838d0e78158b1e57f8e8c
96371a3f192729fd099ff9ba61950d4b
9d3bf048edacf14548a9b899812a2e41
a04081186912355b61f79a35a8f14356
a1aa1180390c98ba8dd72fa87ba43fd4
a68723bcb192e96db984b7c9eba9e2c1
abb71d93b8e0ff93e3d14a1a7b90cfbf
b1ac0c1064d9ca0881fd82f8e50bd3cb
b34f75716613b5c498b818db4881360e
b6e3feed51b61d147b8679bbd19038f4
bbf33b3074c1f3cf43a24d053e071bc5
cba169ffd1b92331cf5b8592c8ebcd6a
d4fee4a9d046e13d15a7fc00eea78222
d634ca7c73614d17d8a56e484a09e3b5
de15828ccbb7d3c81b3d768db2dec419
df92499518c0594a0f59b07fc4da697e
dfd9ea98fb0e998ad5eb72a1a0fd2442
e5c5c1a0077a66315c3a6be79299d835
The post Tales from Ransomwhere appeared first on Panda Security Mediacenter.
Locky goes offline (by design)
New Locky variant can encrypt files without directions from the ransomware’s CnC. That makes it tougher to block. But, this new variant may have the weakness that once someone has paid the ransom for their private key ID – it should be possible to reuse the same key for other victims with the same public key.
The post Locky goes offline (by design) appeared first on Avira Blog.
AVG offers free ransomware decryptor tools for businesses
AVG just released six new ransomware decryption tools for our channel partners and their clients. The free tools decrypt the recent ransomware strains Apocalypse, BadBlock, Crypt888, Legion, SZFlocker and TeslaCrypt.
While our AVG Business products help detect and block against all known ransomware strains – including this recent six – our AVG partners now have helpful tools if a new client, or even a prospect, has a situation where files are already infected by ransomware.
With our new decryption tools, you should be able to recover your clients’ files and data without paying the ransom.
Using the AVG ransomware decryption tools
To use our AVG decryptor tools for the six recent ransomware strains, follow our simple five step process to unlock the encrypted files:
- Run a full system scan on the infected PC and quarantine all the infected files.
- Identify which infection strain encrypted the files. See the descriptions of each strain below. If the ransomware infection matches the strain details, download the appropriate tool and launch it.
- The tool opens a wizard, which breaks the decryption process into several easy steps.
- Follow the steps and you should again be able to reclaim your files in most cases.
- After decryption, be sure to properly back up restored files.
The six ransomware strains and AVG decryptor tools include:
- Apocalypse
- Description: The Apocalypse ransomware appends “.encrypted,” “.locked,” or “.SecureCrypted” to names of encrypted files (e.g. example.docx.encrypted, docx.locked, example.docx.SecureCrypted). It also creates ransom messages in files with extensions “.How_To_Decrypt.txt”, “.README.Txt,” or “.Contact_Here_To_Recover_Your_Files.txt” (e.g. example.docx.How_To_Decrypt.txt, example.docx.README.Txt)
- In those messages, you can find contact addresses such as [email protected], [email protected], [email protected], or [email protected].
- For example:
- Download the AVG decryptor tool: AVG offers one decryptor tool for the early versions of Apocalypse and one for the current version:
- http://files-download.avg.com/util/avgrem/avg_decryptor_Apocalypse.exe
- http://files-download.avg.com/util/avgrem/avg_decryptor_ApocalypseVM.exe
- BadBlock
- Description: BadBlock does not rename encrypted files. You can identify BadBlock by the ransom message named “Help Decrypt.html” and by a red window with ransom messages that begin with “This machine was infected with ransomware BadBlock . . .”
- Download the AVG decryptor tool (for 32-bit and 64-bit systems):
- http://files-download.avg.com/util/avgrem/avg_decryptor_BadBlock32.exe
- http://files-download.avg.com/util/avgrem/avg_decryptor_BadBlock64.exe
- Crypt888
- Description: Crypt888 (aka Mircop) creates encrypted files with the prepended name “Lock.” It also changes your desktop’s wallpaper to a message on a black background that begins with, “You’ve stolen 48.48BTC from the wrong people, please be so kind to return them and we will return your files.”
- Unfortunately, Crypt888 is a badly written piece of code, which means some of the encrypted files or folders will stay that way, even if you pay the fine, as the cybercriminals’ “official decryptor” may not work.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_Crypt888.exe
- Legion
- Description: Legion encrypts and renames files with names like “example.docx[email protected]$.legion.” It also changes the desktop wallpaper and displays a “Your data is encrypted!!” warning.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_Legion.exe
- SZFLocker
- Description: The name of the SZFlocker ransomware originates from a string that is appended to the names of encrypted files (e.g. example.docx.szf). The original files are rewritten with a Polish message.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_SzfLocker.exe
- TeslaCrypt
- Description: This tool supports decryption of files encrypted by TeslaCrypt v3 and v4. The encrypted files come with different extensions, such as .vvv, .micro, .mp3, or with the original name only.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_TeslaCrypt3.exe
At AVG, we take ransomware threats very seriously. We encourage our partners to continue being proactive by using multilayered protection, such as AVG Business solutions, which detect and block ransomware. You can find additional examples of the six ransomware strains and detailed descriptions here.
![]()
![]()
Ransomware: First files … now complete devices
Over the past year, cases of ransomware have gained prominence in the field of computer security due to a notable growth in the number of victims. This is, in turn, due to the significant profits that cybercriminals can obtain from this type of malicious campaign.
The post Ransomware: First files … now complete devices appeared first on We Live Security.
![]()
Locky is back with a twist of COM
Locky is continuing to evolve after its return to the marketplace last week. The new June 28 variant uses Windows COM objects to erase old copies, resulting in more difficult behavior-based detection by security programs.
The post Locky is back with a twist of COM appeared first on Avira Blog.
Zero-Day Warning! Ransomware targets Microsoft Office 365 Users
If just relying on the security tools of Microsoft Office 365 can protect you from cyber attacks, you are wrong.
Variants of Cerber Ransomware are now targeting MS Office 365 email users with a massive zero-day attack that has the ability to bypass Office 365’s built-in security tools.
According to a report published by cloud security provider Avanan, the massive zero-day Cerber ransomware
![]()
Don’t pay the Ransom! AVG releases six free decryption tools to retrieve your files
Ransomware has proven very lucrative for criminals. Many have extended their “business” models by adding ransomware to their malicious catalog. To help prevent personal data and files being held hostage by cybercriminals, we have previously, advised on how to avoid ransomware infections, and what to do if your files have already been held to ransom. In that article, we stated that:
“Many ransomware families contain weaknesses in their encryption algorithm, which may lead to decrypting your files even without paying the ransom! It may take some time to spot and exploit such weaknesses, but in the meantime don’t delete your encrypted files; there may still be hope.”
And now there is hope. With our new tools, you should be able to recover your files without paying the ransom.
Using the Ransomware Decryption Tools
Our new free tools are for the decryption of six current ransomware strains: Apocalypse, BadBlock, Crypt888, Legion, SZFLocker, and TeslaCrypt.
To use, follow our simple four step process to unlock your files:
- Run a full system scan on the infected PC.
- (Optional) Back-up the encrypted files on their own flash drive, so they can then be transferred to another PC for decryption.
- Identify which infection strain encrypted your files. See the descriptions of each strain below. If your ransomware infection matches the strain details, download the appropriate tool and launch it.
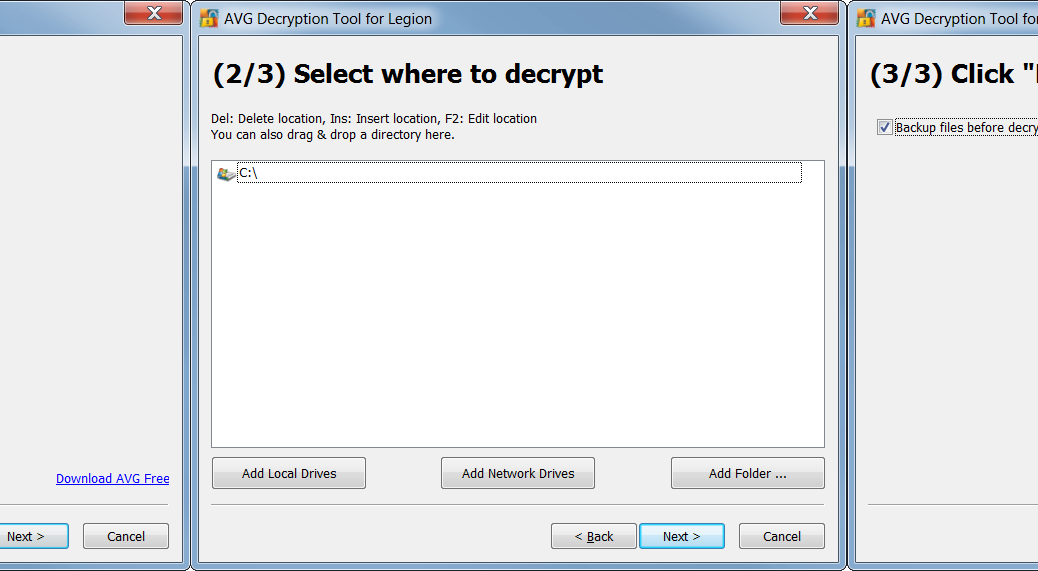
- The tool opens a wizard, which breaks the decryption process into several easy steps:
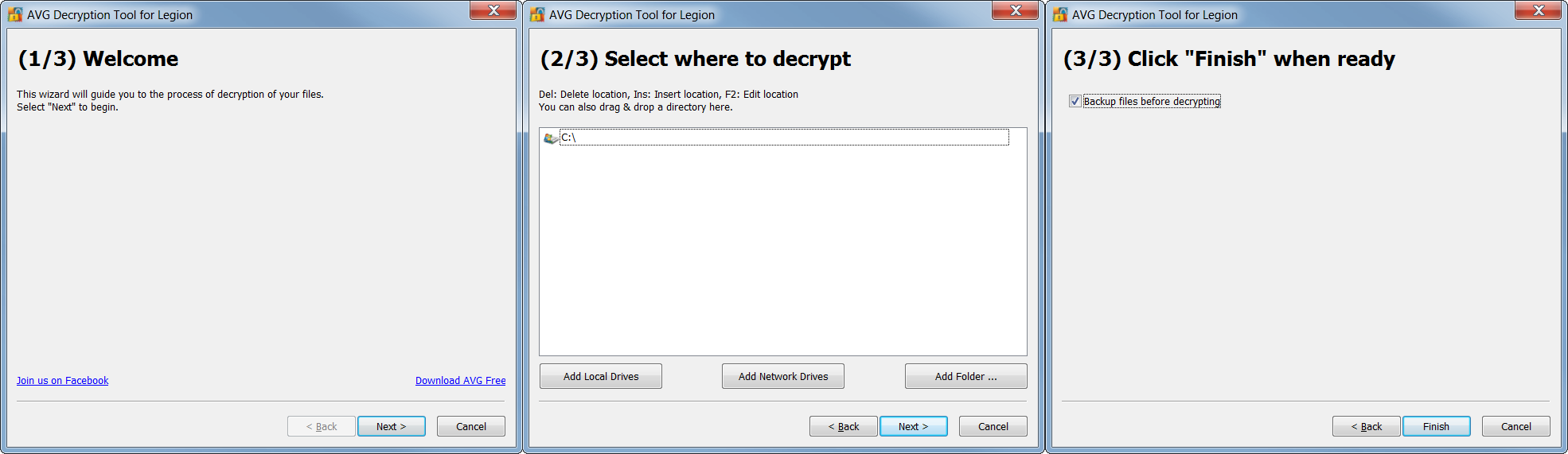
Follow the steps, and you should again be able to reclaim your files in most cases. After decryption, be sure to securely back up restored files on a flash drive or in the cloud.
Apocalypse
The Apocalypse ransomware appends “.encrypted”, “.locked”, or “.SecureCrypted” to names of encrypted files (e.g. example.docx.encrypted, example.docx.locked, example.docx.SecureCrypted). It also creates ransom messages in files with extensions “.How_To_Decrypt.txt”, “.README.Txt”, or “.Contact_Here_To_Recover_Your_Files.txt” (e.g. example.docx.How_To_Decrypt.txt, example.docx.README.Txt, or example.docx.Contact_Here_To_Recover_Your_Files.txt).
In those messages, you can find contact addresses such as [email protected], [email protected], [email protected], or [email protected]. For example:
We prepared two separate decryption tools for this strain: one for the early versions of Apocalypse and the other one for the current version:
http://files-download.avg.com/util/avgrem/avg_decryptor_Apocalypse.exe
http://files-download.avg.com/util/avgrem/avg_decryptor_ApocalypseVM.exe
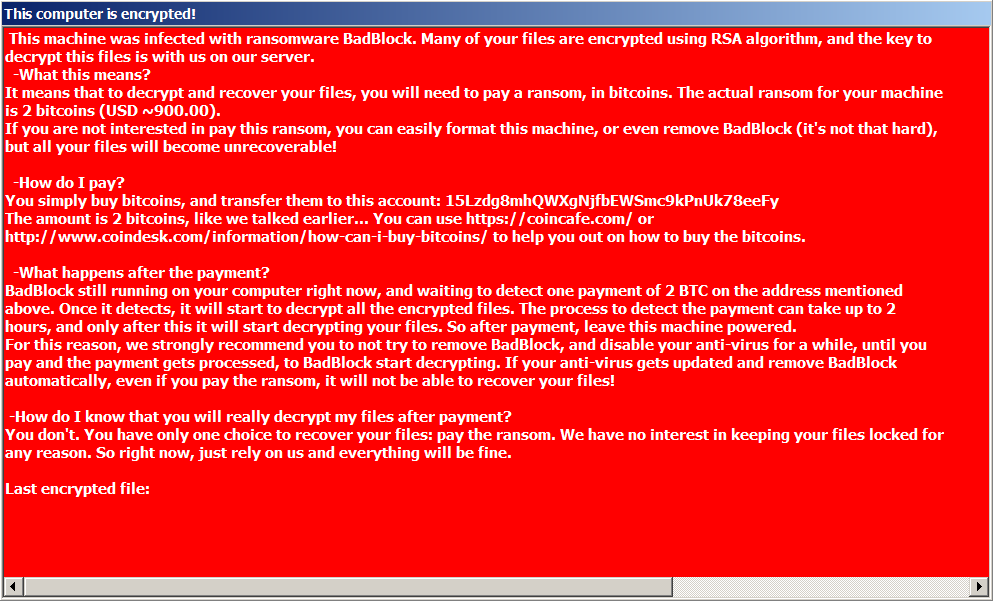
BadBlock
BadBlock does not rename encrypted files. You can identify BadBlock by the ransom message named “Help Decrypt.html” and by the red windows with ransom messages, like the following ones:
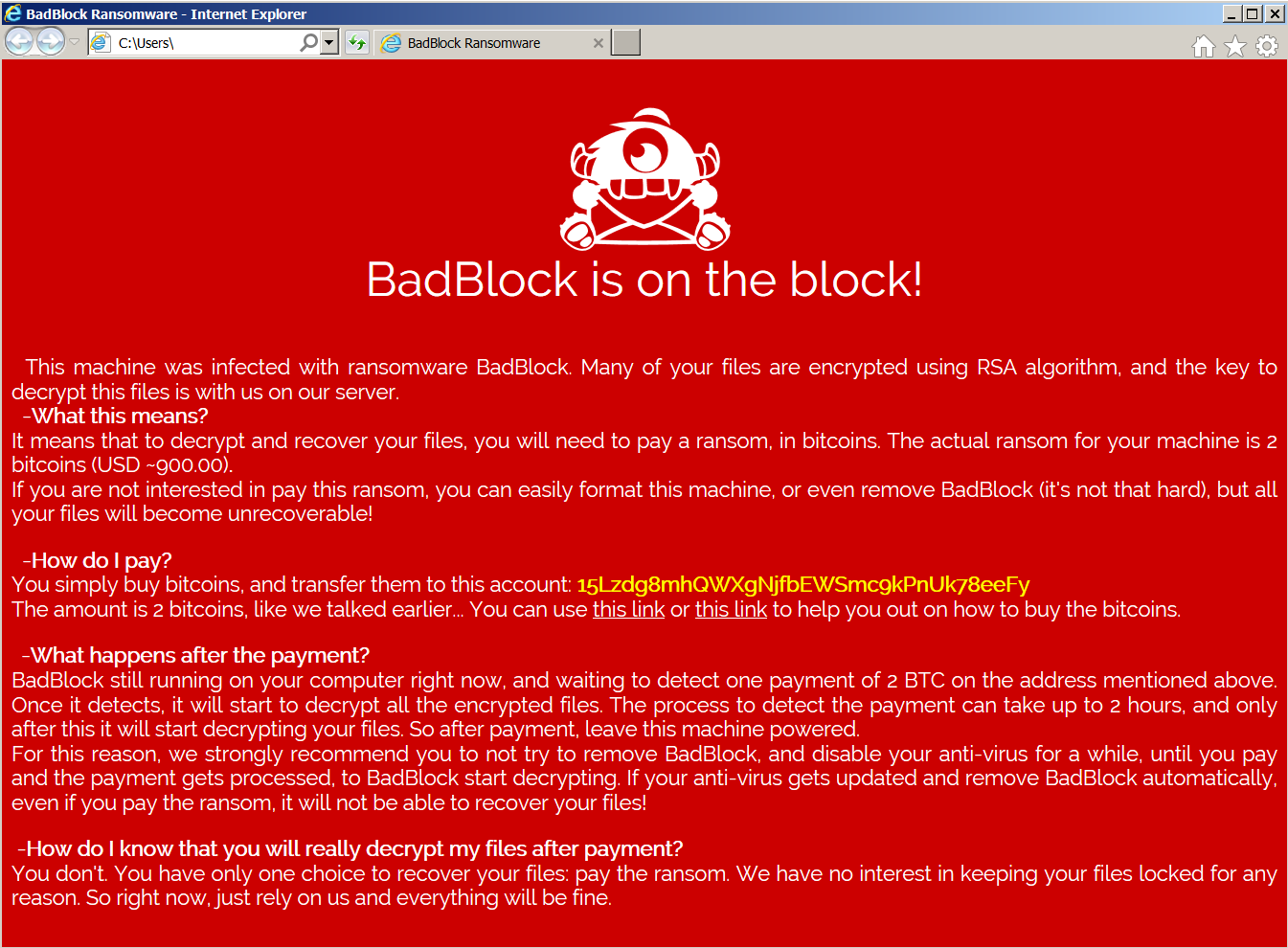
The BadBlock decryption tool can be found here:
http://files-download.avg.com/util/avgrem/avg_decryptor_BadBlock32.exe
http://files-download.avg.com/util/avgrem/avg_decryptor_BadBlock64.exe
Crypt888
Crypt888 (aka Mircop) creates encrypted files with the prepended name “Lock.” (e.g. Lock.example.docx). It also changes your desktop’s wallpaper to the following image:
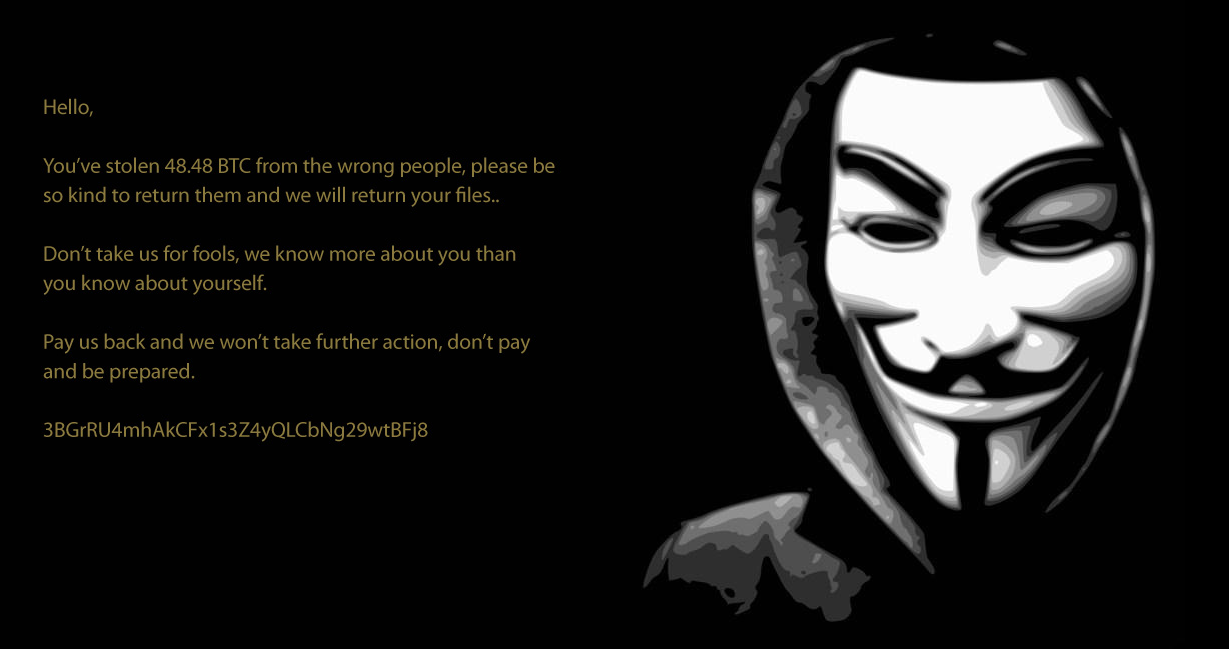
Unfortunately, Crypt888 is a badly written piece of code, which means some of the encrypted files or folders will stay that way, even if you pay the fine, as their “official decryptor” may not work. The AVG decryptor can be found here:
http://files-download.avg.com/util/avgrem/avg_decryptor_Crypt888.exe
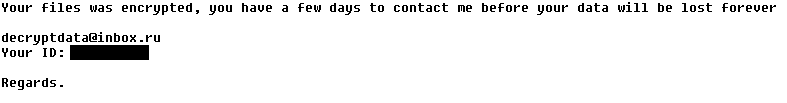
Legion
Legion encrypts and renames your files with names like “example.docx[email protected]$.legion”. It also changes the desktop wallpaper and displays a warning about your encrypted files:
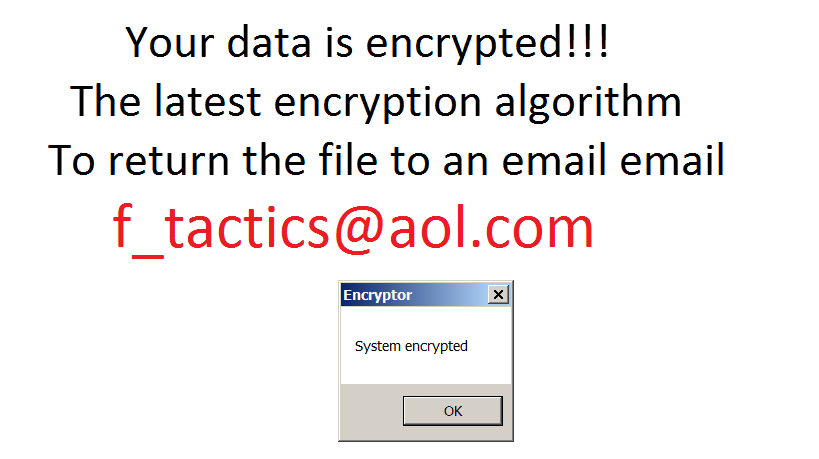
Note: Don’t be confused by another ransomware strain that renames files to a similar name – “[email protected]”. It is NOT the same strain and it cannot be decrypted by this tool.
The decryptor is available here:
http://files-download.avg.com/util/avgrem/avg_decryptor_Legion.exe
SZFLocker
The name of this ransomware originates from a string that is appended to the names of encrypted files (e.g. example.docx.szf). The original files are rewritten with the following Polish message:
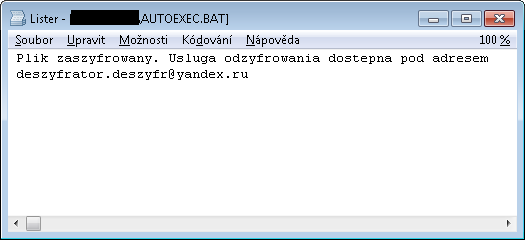
The decryptor for SZFLocker is available here:
http://files-download.avg.com/util/avgrem/avg_decryptor_SzfLocker.exe
TeslaCrypt
Last but not least, we prepared a decryptor for the infamous TeslaCrypt. This tool supports decryption of files encrypted by TeslaCrypt v3 and v4. The encrypted files come with different extensions, such as .vvv, .micro, .mp3, or with the original name only. It also displays a message like the following:
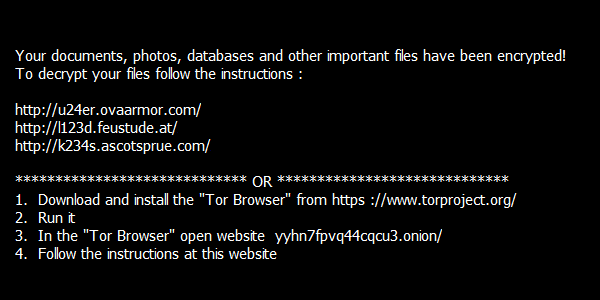
The decryptor can be found here:
http://files-download.avg.com/util/avgrem/avg_decryptor_TeslaCrypt3.exe
Conclusion
At AVG, we take ransomware threats very seriously. Be proactive by using multilayered protection, such as AVG Antivirus Pro, which detects and removes ransomware. Adding decryption tools is a last resort for when your files are already encrypted by ransomware and you need to get your valuable data back.
![]()
![]()