Camilo Gutierrez Amaya looks at five key aspects for aspects that companies should be taken into consideration when developing a virtualization project.
The post 5 key aspects for safe virtualization appeared first on We Live Security.
![]()
Camilo Gutierrez Amaya looks at five key aspects for aspects that companies should be taken into consideration when developing a virtualization project.
The post 5 key aspects for safe virtualization appeared first on We Live Security.
![]()
There’s a term in public health known as “herd immunity.” The idea is that when a critical number of people are immunized against a contagious disease, most members of that community become protected against the disease, whether or not they received an inoculation.
Breaking the chain of a disease’s transmission enables us to interrupt the ability of the pathogen to set in at a broader scale in our community. In this way, vaccinations protect people who have and haven’t been vaccinated.
The same principle applies to our digital lives which are just as connected, if not more connected, to digital threats and “pathogens” that steal our data and identities, disrupt our productivity, and mar our public profiles. We spend a great deal of time and energy investing in firewalls and the technical parts of our infrastructure to protect data and privacy, but what about our behavioral practices?
Do we take the time to inoculate ourselves against habits that could risk the digital wellbeing of our family and friends? Or do we, for example, still ask family members for Social Security numbers via email? Or send credit card information and/or passwords insecurely?
“The important principle here is that there are things I can do to help ensure a safer online world for you, and vice versa.”.
If, for example, you posted a compromising photo on social media, I can opt to not re-post it, protecting you from further harm. And if everyone who comes across the photo does the same, we’ve inoculated you from damage even though you had failed to protect yourself.
This is the mindset that we need to adopt in being good digital citizens and embodying the characteristics of a “smart user.” By doing so, we can create an entire network and community of safety and protection.
Most of us, especially the youth and others around the world who are coming online for the first time, are particularly vulnerable. We were all the same at some time. When I worked at Netscape, for example, and got my first email message from a friend “stranded in Thailand,” asking for money – I almost fell for it! On the exposure curve, I was just like a lot of new users today.
Let’s take a page from the herd immunity playbook and create a safer and more private digital world for all of the new users coming online, in addition to helping these users become more educated in smart online behaviors.
AVG has committed to a smart user digital citizenship initiative to build a better web. Please join us or see how you can support this initiative. Because after all, the more you do to help make the web a safer place, you do so not only for yourself but for the whole herd.
To learn more, please visit smartuser.com.
![]()
![]()

Don’t ignore Facebook alerts and take your time to improve your security
Facebook has become more concerned about its users’ security. The social giant understands that education is the key to providing users with a secure experience. We have already seen the Facebook “dinosaur” guiding us via privacy settings. Now Facebook pops out a short guide to improve the security of our profiles. We strongly recommend not to ignore it and take those steps to ensure that your profile is properly protected.

Don’t ignore Facebook alerts and take your time to improve your security
We check our Facebook profile on multiple devices: Our smartphones, tablets and via different apps (Facebook group, messenger, Facebook app). Sometimes we don’t even realize it! ‘Log Out of Unused Apps’ will show you all the apps that you use to log in, but haven’t used for a long period of time. From a security perspective that can create a vulnerable situation. If you don’t use the app, better log out!
We have also a solution for that. If you don’t want to be bother with constant login into your social account, we recommend Avast Passwords available for all your mobile devices for FREE. Check it out for Android and iOS. With one password you can safely log in into your all social apps, without remembering multiple passwords!
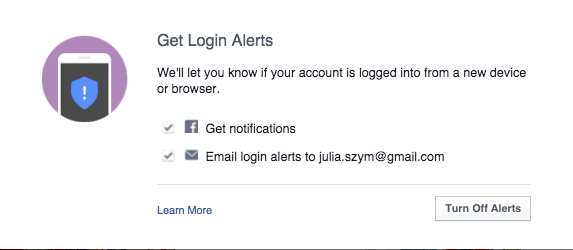
Login alerts will notify you about unauthorized login attempts into your account
Facebook will let you know when there is an attempt to log into your account via a new device or browser. You can set up both – Facebook notifications as well as email alerts. In this way you have better control over who, when, and where someone tries to login into your profile. You will receive a notification and if it is a hacking attempt, you can block it. We recommend to chose both options, in order to increase your chances to discover a hacker, before he cracks your account.
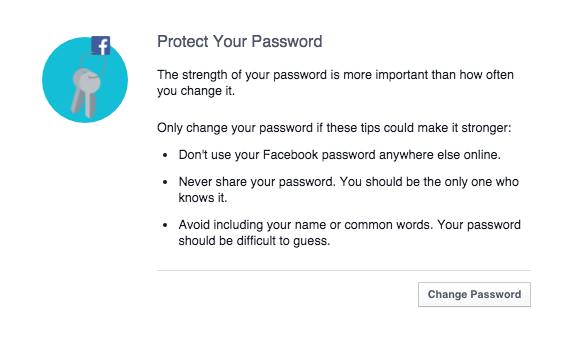
Follow Facebook rules to protect your password
Follow simple security rules:
Secure Facebooking!
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()

Don’t ignore Facebook alerts and take your time to improve your security
Facebook has become more concerned about its users’ security. The social giant understands that education is the key to providing users with a secure experience. We have already seen the Facebook “dinosaur” guiding us via privacy settings. Now Facebook pops out a short guide to improve the security of our profiles. We strongly recommend not to ignore it and take those steps to ensure that your profile is properly protected.

Don’t ignore Facebook alerts and take your time to improve your security
We check our Facebook profile on multiple devices: Our smartphones, tablets and via different apps (Facebook group, messenger, Facebook app). Sometimes we don’t even realize it! ‘Log Out of Unused Apps’ will show you all the apps that you use to log in, but haven’t used for a long period of time. From a security perspective that can create a vulnerable situation. If you don’t use the app, better log out!
We have also a solution for that. If you don’t want to be bother with constant login into your social account, we recommend Avast Passwords available for all your mobile devices for FREE. Check it out for Android and iOS. With one password you can safely log in into your all social apps, without remembering multiple passwords!
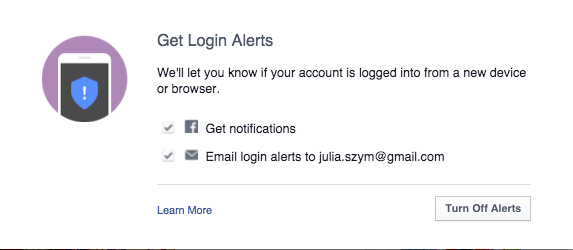
Login alerts will notify you about unauthorized login attempts into your account
Facebook will let you know when there is an attempt to log into your account via a new device or browser. You can set up both – Facebook notifications as well as email alerts. In this way you have better control over who, when, and where someone tries to login into your profile. You will receive a notification and if it is a hacking attempt, you can block it. We recommend to chose both options, in order to increase your chances to discover a hacker, before he cracks your account.

Follow Facebook rules to protect your password
Follow simple security rules:
Secure Facebooking!
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()

Don’t ignore Facebook alerts and take your time to improve your security
Facebook has become more concerned about its users’ security. The social giant understands that education is the key to providing users with a secure experience. We have already seen the Facebook “dinosaur” guiding us via privacy settings. Now Facebook pops out a short guide to improve the security of our profiles. We strongly recommend not to ignore it and take those steps to ensure that your profile is properly protected.

Don’t ignore Facebook alerts and take your time to improve your security
We check our Facebook profile on multiple devices: Our smartphones, tablets and via different apps (Facebook group, messenger, Facebook app). Sometimes we don’t even realize it! ‘Log Out of Unused Apps’ will show you all the apps that you use to log in, but haven’t used for a long period of time. From a security perspective that can create a vulnerable situation. If you don’t use the app, better log out!
We have also a solution for that. If you don’t want to be bother with constant login into your social account, we recommend Avast Passwords available for all your mobile devices for FREE. Check it out for Android and iOS. With one password you can safely log in into your all social apps, without remembering multiple passwords!

Login alerts will notify you about unauthorized login attempts into your account
Facebook will let you know when there is an attempt to log into your account via a new device or browser. You can set up both – Facebook notifications as well as email alerts. In this way you have better control over who, when, and where someone tries to login into your profile. You will receive a notification and if it is a hacking attempt, you can block it. We recommend to chose both options, in order to increase your chances to discover a hacker, before he cracks your account.

Follow Facebook rules to protect your password
Follow simple security rules:
Secure Facebooking!
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
200 startups gave their pitches at the Web Summit this year in Dublin. Over 2,100 startups participated, the vast majority of which had “poster board” displays and one or two eager founders giving their elevator pitch. That makes the Web Summit a welcome change to other conferences that typically rotate around industry giants.
Two messages seemed to pervade the conference this year: location and security. The “location” bit was the move of the Web Summit from Dublin to Lisbon next year. As you can imagine, this was a bit of a blow to the locals, and they could not stop talking about it. Hopefully Lisbon imports Guinness and Jameson so that a little bit of Dublin carries over.
“Security” discussions seemed more prevalent than ever before. The recent breaches at TalkTalk and Ashley Madison were discussed over and over again…and the recent UK decision to store web histories for everyone for a year was a hot topic, as was the Safe Harbor European Court of Justice ruling. But, more than that, the need for both security and privacy was raised in almost every context: from publishing your web app to talking to IoT devices. The phrase “the Internet of unpatchable crud” was being thrown around often. Interestingly, many of these conversations were underway before people learned that I was with AVG, and thus involved with security and privacy issues directly.
Further, a lot of the discussions focused around personal security, not just enterprise security. This is a change from a year ago, or even six months ago. This bodes well for AVG’s move into protecting people as well as devices and data.
AVG has been pushing something called “the law of least data” with IoT groups for a while now. The core idea is that data should be routed as directly as possible between entities. This augments the idea of “storing only required and essential data” that has been a mainstay of good data design for a long time. My canonical example is my thermostat talking to my furnace. While setting up the relationship between the two may require the cloud, the day to day control and feedback between the two should not have to leave my house (i.e., my local area network). Even if encrypted, an eavesdropper could probably tell when someone was at home based on the volume of traffic between the two. This is a simple idea, but an important one. When you extend that thinking to many connected devices, including those dealing with health and security, you can imagine the impacts of not respecting the “law of least data.” However, the business/capitalistic forces at work today mean that every vendor wants to backhaul all data to the cloud under the rubric of “data is the new currency.” This is a dangerous architecture and one that we should all be challenging.
Many people, when asked about their personal data leaking, have a fairly resigned attitude. They say, “it is not a big deal, and I get more personalized offers; I know the tradeoffs I am making.” I like to use a simple example to help people understand that seemingly innocuous data is still valuable and can be used in unexpected ways. If you are a serious cycler, you will probably sign up for a bike ride sharing application. It is fun; you can compete against others as motivation and track your personal progress online. However, thieves also sign up for these services. Using the simple logic that users who ride the most often and the farthest probably have the most expensive bikes, led the thieves to steal bicycles easily using the location tracking data in the services. Again, you can extend this idea to all types of data to understand that, by default, we should be keeping our data safe and secure.
So, it was refreshing to see these, and other, security topics being actively discussed at the Web Summit. It bodes well for our industry that this is now top of mind.
![]()
![]()
200 startups gave their pitches at the Web Summit this year in Dublin. Over 2,100 startups participated, the vast majority of which had “poster board” displays and one or two eager founders giving their elevator pitch. That makes the Web Summit a welcome change to other conferences that typically rotate around industry giants.
Two messages seemed to pervade the conference this year: location and security. The “location” bit was the move of the Web Summit from Dublin to Lisbon next year. As you can imagine, this was a bit of a blow to the locals, and they could not stop talking about it. Hopefully Lisbon imports Guinness and Jameson so that a little bit of Dublin carries over.
“Security” discussions seemed more prevalent than ever before. The recent breaches at TalkTalk and Ashley Madison were discussed over and over again…and the recent UK decision to store web histories for everyone for a year was a hot topic, as was the Safe Harbor European Court of Justice ruling. But, more than that, the need for both security and privacy was raised in almost every context: from publishing your web app to talking to IoT devices. The phrase “the Internet of unpatchable crud” was being thrown around often. Interestingly, many of these conversations were underway before people learned that I was with AVG, and thus involved with security and privacy issues directly.
Further, a lot of the discussions focused around personal security, not just enterprise security. This is a change from a year ago, or even six months ago. This bodes well for AVG’s move into protecting people as well as devices and data.
AVG has been pushing something called “the law of least data” with IoT groups for a while now. The core idea is that data should be routed as directly as possible between entities. This augments the idea of “storing only required and essential data” that has been a mainstay of good data design for a long time. My canonical example is my thermostat talking to my furnace. While setting up the relationship between the two may require the cloud, the day to day control and feedback between the two should not have to leave my house (i.e., my local area network). Even if encrypted, an eavesdropper could probably tell when someone was at home based on the volume of traffic between the two. This is a simple idea, but an important one. When you extend that thinking to many connected devices, including those dealing with health and security, you can imagine the impacts of not respecting the “law of least data.” However, the business/capitalistic forces at work today mean that every vendor wants to backhaul all data to the cloud under the rubric of “data is the new currency.” This is a dangerous architecture and one that we should all be challenging.
Many people, when asked about their personal data leaking, have a fairly resigned attitude. They say, “it is not a big deal, and I get more personalized offers; I know the tradeoffs I am making.” I like to use a simple example to help people understand that seemingly innocuous data is still valuable and can be used in unexpected ways. If you are a serious cycler, you will probably sign up for a bike ride sharing application. It is fun; you can compete against others as motivation and track your personal progress online. However, thieves also sign up for these services. Using the simple logic that users who ride the most often and the farthest probably have the most expensive bikes, led the thieves to steal bicycles easily using the location tracking data in the services. Again, you can extend this idea to all types of data to understand that, by default, we should be keeping our data safe and secure.
So, it was refreshing to see these, and other, security topics being actively discussed at the Web Summit. It bodes well for our industry that this is now top of mind.
![]()
![]()
200 startups gave their pitches at the Web Summit this year in Dublin. Over 2,100 startups participated, the vast majority of which had “poster board” displays and one or two eager founders giving their elevator pitch. That makes the Web Summit a welcome change to other conferences that typically rotate around industry giants.
Two messages seemed to pervade the conference this year: location and security. The “location” bit was the move of the Web Summit from Dublin to Lisbon next year. As you can imagine, this was a bit of a blow to the locals, and they could not stop talking about it. Hopefully Lisbon imports Guinness and Jameson so that a little bit of Dublin carries over.
“Security” discussions seemed more prevalent than ever before. The recent breaches at TalkTalk and Ashley Madison were discussed over and over again…and the recent UK decision to store web histories for everyone for a year was a hot topic, as was the Safe Harbor European Court of Justice ruling. But, more than that, the need for both security and privacy was raised in almost every context: from publishing your web app to talking to IoT devices. The phrase “the Internet of unpatchable crud” was being thrown around often. Interestingly, many of these conversations were underway before people learned that I was with AVG, and thus involved with security and privacy issues directly.
Further, a lot of the discussions focused around personal security, not just enterprise security. This is a change from a year ago, or even six months ago. This bodes well for AVG’s move into protecting people as well as devices and data.
AVG has been pushing something called “the law of least data” with IoT groups for a while now. The core idea is that data should be routed as directly as possible between entities. This augments the idea of “storing only required and essential data” that has been a mainstay of good data design for a long time. My canonical example is my thermostat talking to my furnace. While setting up the relationship between the two may require the cloud, the day to day control and feedback between the two should not have to leave my house (i.e., my local area network). Even if encrypted, an eavesdropper could probably tell when someone was at home based on the volume of traffic between the two. This is a simple idea, but an important one. When you extend that thinking to many connected devices, including those dealing with health and security, you can imagine the impacts of not respecting the “law of least data.” However, the business/capitalistic forces at work today mean that every vendor wants to backhaul all data to the cloud under the rubric of “data is the new currency.” This is a dangerous architecture and one that we should all be challenging.
Many people, when asked about their personal data leaking, have a fairly resigned attitude. They say, “it is not a big deal, and I get more personalized offers; I know the tradeoffs I am making.” I like to use a simple example to help people understand that seemingly innocuous data is still valuable and can be used in unexpected ways. If you are a serious cycler, you will probably sign up for a bike ride sharing application. It is fun; you can compete against others as motivation and track your personal progress online. However, thieves also sign up for these services. Using the simple logic that users who ride the most often and the farthest probably have the most expensive bikes, led the thieves to steal bicycles easily using the location tracking data in the services. Again, you can extend this idea to all types of data to understand that, by default, we should be keeping our data safe and secure.
So, it was refreshing to see these, and other, security topics being actively discussed at the Web Summit. It bodes well for our industry that this is now top of mind.
![]()
![]()
Futurecom is Brazil’s major conference and exhibition for the mobile industry to come together and look at the specific requirements that this unique country and culture need.
I was fortunate enough to be asked to be on a panel of industry experts, which included companies such as Tefonica, TIM, Telebras, Deloitte IBM, KPMG and of course AVG. The discussion was promised to be about cybersecurity with the following questions asked by the moderator through the 1.5 hours to get the discussion going.
Each participant gave a view point, and what interested me was how the entire conversation, regardless of the question, seemed to revolve around two topics: data breaches and consumer privacy. This dominated the answers, yet if the same questions had been asked 3 years ago this would have been about malware and protecting devices, but now the conversation is about us, the consumer.
Brazil has some unique challenges in this area as there is no legislation requiring companies to disclose any data breach, and therefore the consumer never knows if their data has been compromised. The consensus of the panel was that governments need to legislate. While I agree with the need for ‘some’ legislation there is also an opportunity for industry to self-regulate and show a responsible path. Self-regulation in any industry allows companies involved to find innovative ways to provide solutions and allows new business practices that may not have been permitted by the strictness of specific legislation.
The fact that data breaches and consumer privacy topped the agenda is not surprising. If we look at the trend of security stories in the US and Europe you’ll notice that the news coverage is all around these topics and the many data breaches that have taken place.
We, whether knowingly or not, disclose and share more information with companies than any generation has ever done before us: our preferences for food, where we shop, our location — the list of data is endless. It is only when this data falls into the wrong hands do we take time to think about the consequences of having shared it, and then maybe regretting it a little. As consumers we need greater choice and control on what is being collected about us and ultimately how it may be used.
It’s not surprising that in one of the world’s major populations, in which a large number of people moved straight to mobile skipping the PC generation, that mobile applications are used in slightly different ways to the rest of the world. I recommend watching to see how Brazil handles the challenges of data breaches and consumer privacy, whether legislated or self-regulated.
![]()
![]()
Mozilla has pushed a feature in Firefox live that allows Firefox web browsers to block certain page elements while browsing privately.