Researchers at Black Hat found a weak spot in some WSUS configurations that could allow an attacker to compromise any server or desktop in an enterprise.
Tag Archives: SSL
New Study: 10 Out of 10 Smartwatches Vulnerable
A new study on the Internet of Things with focus on smartwatches released by HP revealed that of 10 smartwatches that were tested, all contain significant vulnerabilities and are a “risk that goes beyond the device”.
So what exactly are we talking about? According to the study (PDF) “the results of the research were disappointing, but not surprising.” There are deficiencies when it comes to authentication and authorization, privacy concerns, and problems with the implementation of SSL/TSL.
Their key takeaways are as following:
- “Data collected initially on the watch and passed through to an application is often sent to multiple backend destinations (often including third parties)
- Watches that include cloud interfaces often employed weak password schemes, making them more susceptible to attack
- Watch communications are trivially intercepted in 90% of cases
- Seventy percent of watch firmware was transmitted without encryption
- Fifty percent of tested devices offered the ability to implement a screen lock (PIN or Pattern), which could hinder access if lost or stolen
- Smartwatches that included a mobile application with authentication allowed unrestricted account enumeration
- The combination of account enumeration, weak passwords, and lack of account lockout means 30% of watches and their applications were vulnerable to Account Harvesting, allowing attackers to guess login credentials and gain access to user account”
So yes, it’s basically the same cycle as with most of the ‘newer’ tech gadgets. They get released, there is a big hype, but security becomes only important after lots and lots of reports on hacks, vulnerabilities, and the inevitable bad press. Think nothing of it guys, everything is just the way it always was …
The post New Study: 10 Out of 10 Smartwatches Vulnerable appeared first on Avira Blog.
Spoofed URLs: Homograph Attacks Revisited
How homograph attacks can present a spoofed, malicious link, and a case where a secure connection doesn’t guarantee a safe site.
The post Spoofed URLs: Homograph Attacks Revisited appeared first on We Live Security.
![]()
OpenSSL Patches Critical Certificate Validation Vulnerability
A high-severity bug in OpenSSL was disclosed today, and it affects only organizations that installed an update released in June, and allows anyone with an untrusted TLS certificate to become a CA.
Researcher Says LG App Update Mechanism Doesn’t Verify SSL Cert
Many smartphones manufactured by LG contain a vulnerability that can allow an attacker to replace an APK file with a malicious file of his choice. The problem is the result of several conditions on LG phones. Like other manufacturers, LG includes custom apps on its handsets, which are not available through the normal Google Play […]
IETF Officially Deprecates SSLv3
The IETF, in RFC7568, declared SSLv3 “not sufficiently secure” and prohibited its use. SSLv3 fallbacks were to blame for the POODLE and BEAST attacks.
Explaining Avast’s HTTPS scanning feature

Avast Web Shield scans HTTPS sites for malware and threats.
Internet users with basic security knowledge are aware that they should look for the padlock icon in the address bar or the HTTPS in a web address to indicate that a website is secure. We have gotten used to seeing it on bank sites or shopping carts where we input our credit card information. More and more, regular websites are making the switch from unencrypted HTTP to encrypted HTTPS. Last year, search giant Google sweetened the pot by adding HTTPS to their ranking algorithm. That action encouraged webmasters everywhere to make the switch to HTTPS.
But is HTTPS really more secure than HTTP?
The simple answer is not always. As more and more online services are moving to HTTPS, attacks are increasing. An encrypted connection ensures that the connection cannot be modified by anyone else, but it does not guarantee that the actual content being downloaded is safe. Just as with plain HTTP, if a legitimate website is hacked, malware scripts and binaries can be placed into the HTTPS page that appears to be safe.
That’s why it is imperative for security software to check this attack vector. To address this, Avast’s trusted Web Shield technology scans HTTPS sites for malware and threats.
How Avast’s HTTPS scanning feature works (the short version)
Avast is able to detect and decrypt TLS/SSL protected traffic in our Web-content filtering component. To detect malware and threats on HTTPS sites, Avast must remove the SSL certificate and add its self-generated certificate. Our certificates are digitally signed by Avast’s trusted root authority and added into the root certificate store in Windows and in major browsers to protect against threats coming over HTTPS; traffic that otherwise could not be detected.
Avast whitelists websites if we learn that they don’t accept our certificate. Users can also whitelist sites manually, so that the HTTPS scanning does not slow access to the site.
This video gives you an overview, but if any of this didn‘t make much sense to you, read below for a more detailed explanation. You can also explore the FAQ about HTTPS scanning in Web Shield.
What is HTTP and why is it being changed?
HyperText Transfer Protocol or HTTP is the network protocol used to deliver virtually all files and other data on the World Wide Web. When you visit a website you may see the HTTP:// prefix in the address. This means your browser is now connected to the server using HTTP. The problem with HTTP is that it is not a secure way to establish a connection, opening a door to cybercrooks who want to eavesdrop on your activities.
Hackers can eavesdrop via an HTTP address because when you connect to a website with HTTP, your browser assumes it is connected to the correct web server. The problem with this is that there is no way to authenticate that you are actually connected to the correct website. This is a big problem if you think you are connecting to your bank’s website, but you are really on a compromised network and have been redirected to a fake website. This is when the hacker can eavesdrop and see any passwords, credit cards, or other data.
HTTPS is meant to solve this problem
HTTPS, which literally stands for HTTP Secure, is the safe encrypted counterpart to HTTP. When you connect with HTTPS , it provides identity verification and security, so you get the benefit of encryption that prevents others from eavesdropping on your communications and ensures you that you are connected to the intended server.
What is a website security certificate?
HTTPS encryption and authentication are provided by security protocols known as TLS and SSL. The SSL protocol verifies that you are connected to the intended server with a “handshake” which proves the identity of the server to the client. This is achieved using SSL security certificates, which contain various pieces of information like the name of the holder, the domain, validity date, the certificate’s public key, and the digital signature.
Usually the certificate is digitally signed by a trusted certificate authority (CA) that it already knows. For the connection to succeed, the server, and in some cases the client, must provide a certificate that allows the computer to determine if the connection should be trusted or not. If the private key to the certificate is leaked, anyone can mimic the server’s identity.
Why does Avast create a ‘certificate authority’ and how is it created?
When the browser is about to make a connection to a HTTPS server, Avast Web Shield takes over the handshake and connects itself to the server. When the server sends its certificates, Web Shield verifies them against the Windows System Certificate Store – the same list of trusted certificates that Internet Explorer, Chrome, Opera, and other programs use. Web Shield scans the flow of the data connection, and after verifying that the communication is secure, hands over the connection to the browser.
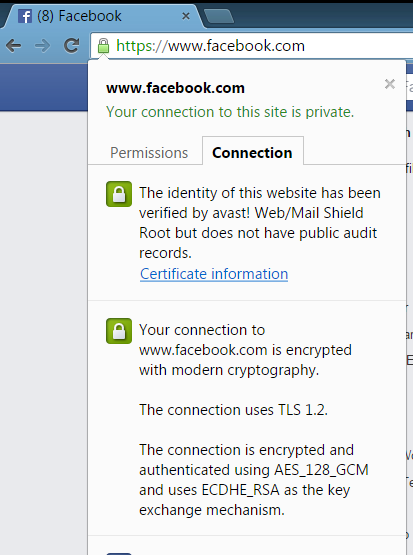 What is a MITM attack and how does it differ from what Avast is doing?
What is a MITM attack and how does it differ from what Avast is doing?
The SSL protocol is imperfect, so hackers can take advantage of it. A man-in-the-middle (MITM) attack takes place when a hacker intercepts the communication between two systems by impersonating the two parties. This clever ruse makes them think that they are talking to each other when they are both actually talking to the attacker. The attacker can read, insert, or modify the data in the intercepted communication and no one ever knows.
The Avast WebShield must use a MITM approach in order to scan secure traffic, but the important difference is that the “middle man” we use is located in the same computer as the browser and uses the same connection. Since Avast is running with Administrator rights and elevated trust on the computer, it can create and store certificates that the browser correctly accepts and trusts for this, and only this, machine. For every original certificate, Avast makes a copy and signs it with Avast’s root certificate, located in the Windows Certificate store. This special certificate is called “Avast Web/Mail certificate root” to clearly distinguish who created it and for what purpose.
We want to emphasize that no one else has the same unique key that you have from the installation generated certificate. This certificate never leaves the computer and is never transmitted over the internet. The Windows System Certificate Store is the only place where your computer’s certificate is stored and accessed.
How do I maintain my privacy when Avast is scanning my banking connections?
Our customers’ privacy was our first concern when planning the implementation of HTTPS scanning. That’s why we created a way for whitelisting, or ignoring, the connection when Avast users access banking sites. Our current list has over 600 banks from all over the world and we are constantly adding new, verified banking sites. You can, and should, verify the bank’s security certificate when using online banking sites. Once verified, you can submit the banking or other web site to our whitelist by sending us an email: banks‑[email protected].
How to disable the HTTPS scanning feature
If you do not want Avast to scan HTTPS traffic, you have the option of disabling the feature in the Avast settings:
1. Open the Avast user interface → select Settings.
2. Select Active protection → click Customize next to Web Shield.
3. Select Main settings → check/uncheck Enable HTTPS scanning to turn this feature on/off.
Second Crypto Bug in Networking Library Could Affect 25,000 Apps
A few weeks after the developers of the AFNetworking library that’s popular among iOS and OS X app developers patched a serious bug in the library that enabled man-in-the-middle attacks, another, similar flaw has surfaced. The new vulnerability is related to how the AFNetworking library handles domain name validation for certificates. As it turns out, the library […]
BlackBerry Warns Many Products Vulnerable to FREAK Attack
BlackBerry is warning customers that a large portion of the company’s product portfolio is vulnerable to the FREAK SSL attack. Many versions of the BlackBerry OS and BlackBerry Enterprise Server are vulnerable to FREAK, as are a number of versions of BlackBerry Messenger. The advisory from BlackBerry says that there are no workarounds for the […]
New FREAK Attack Threatens Many SSL Clients
For the nth time in the last couple of years, security experts are warning about a new Internet-scale vulnerability, this time in some popular SSL clients. The flaw allows an attacker to force clients to downgrade to weakened ciphers and break their supposedly encrypted communications through a man-in-the-middle attack. Researchers recently discovered that some SSL […]
