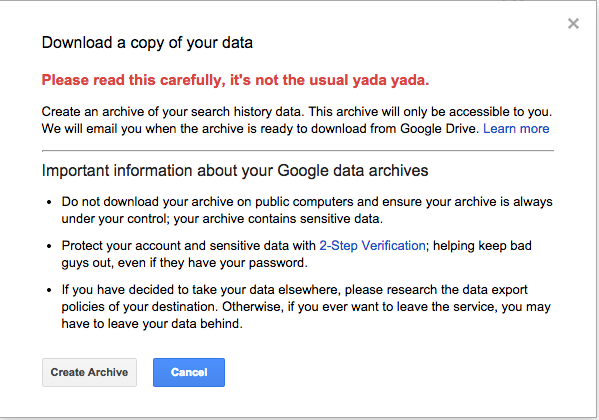
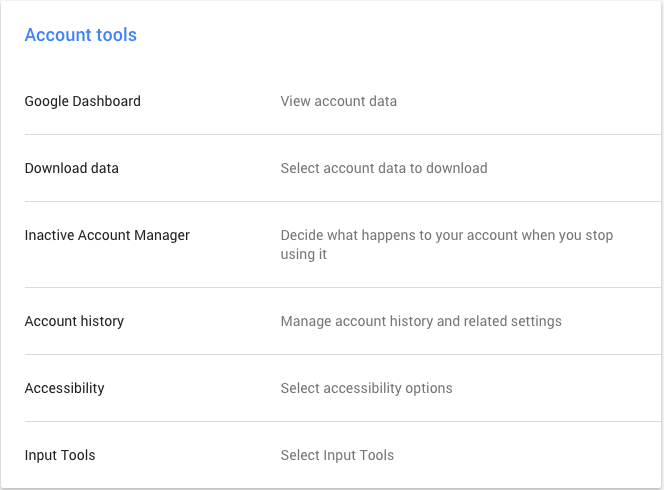
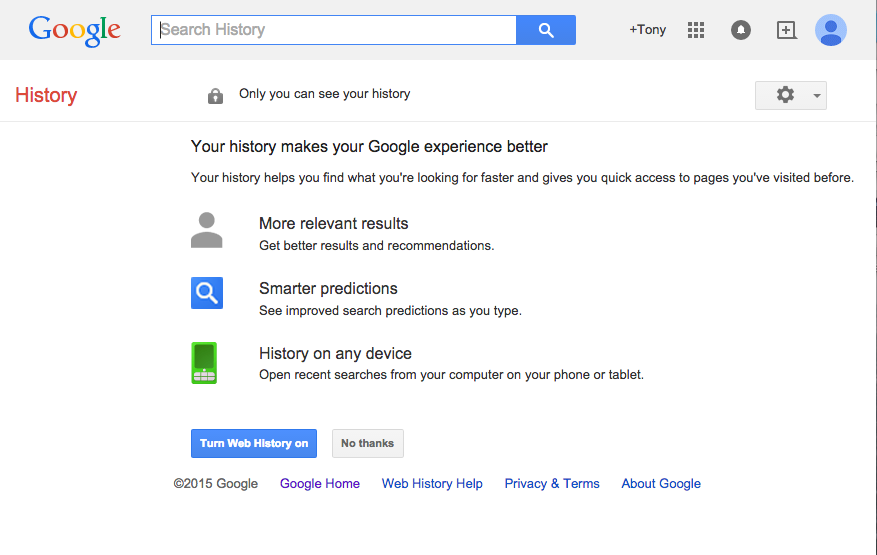
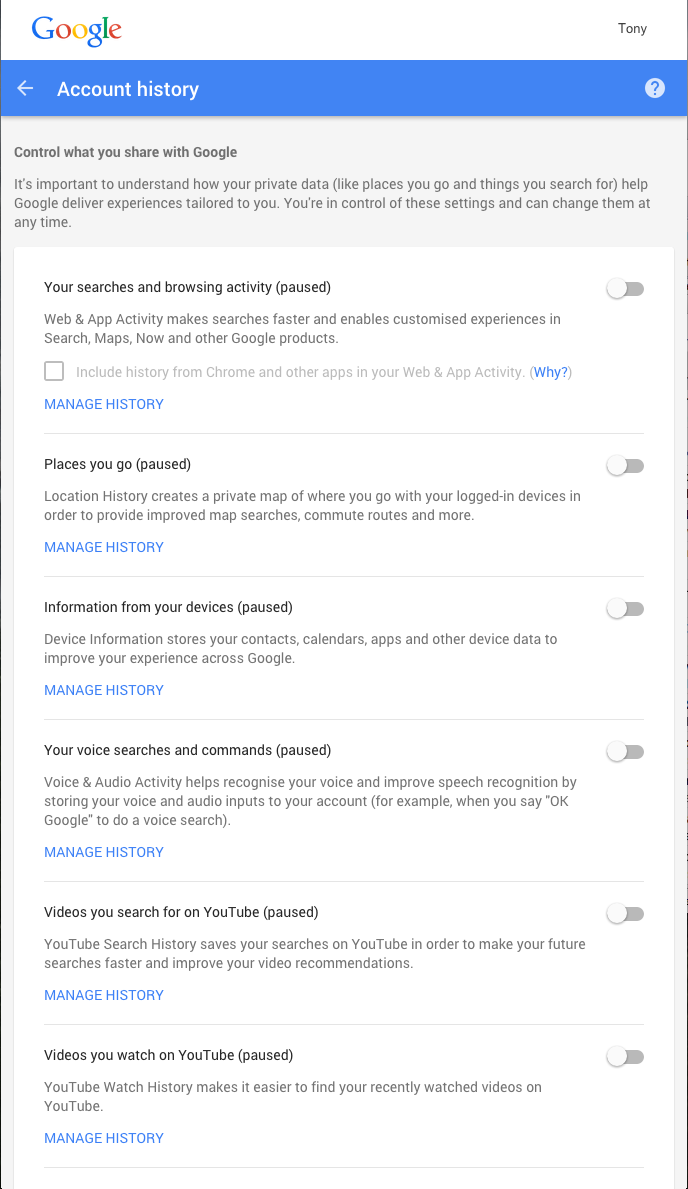
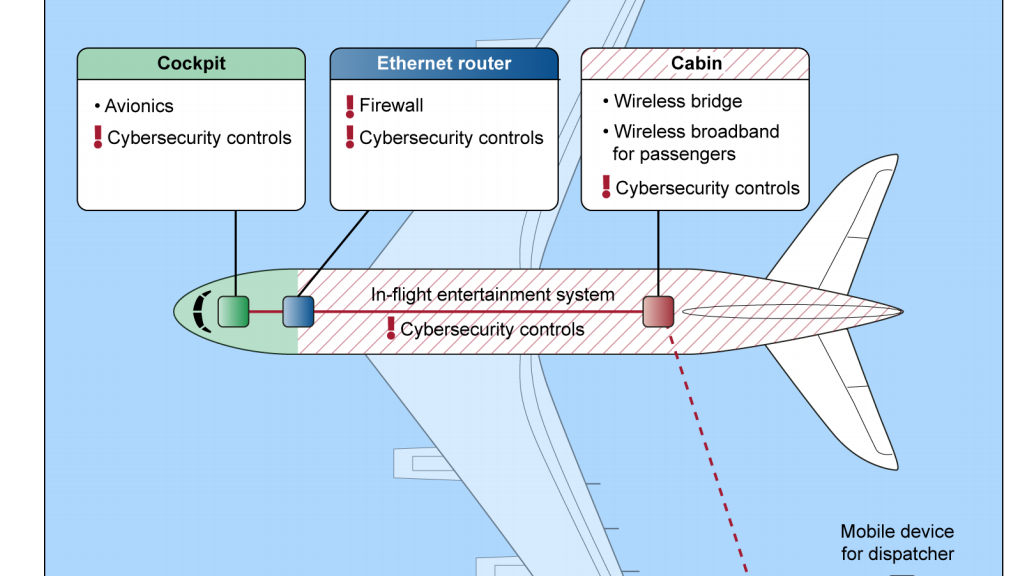
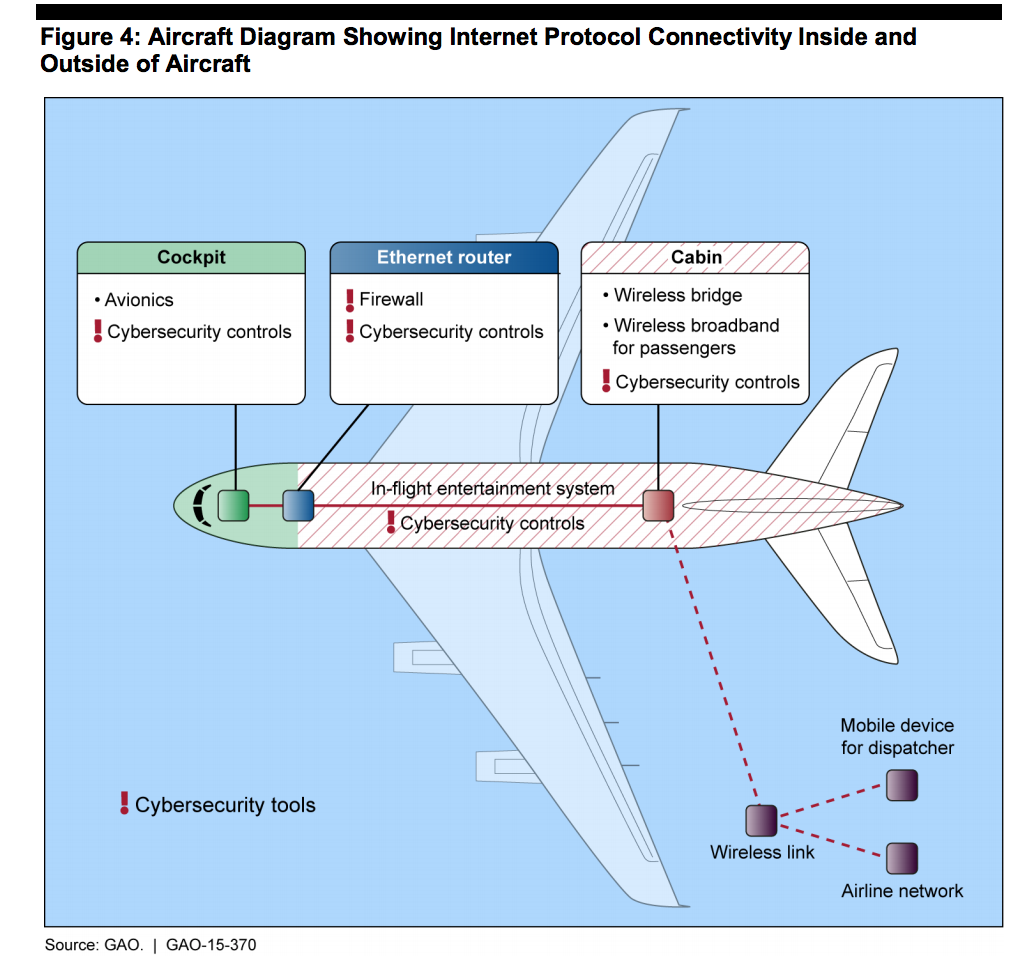
Over the past 18 months we have witnessed monumental data breaches affecting tens of millions of users. As consumers though, do we worry about what happens to our leaked data? Are attackers aggregating it with other sources, are they applying for credit in my name or even using medical services?
We should be concerned and the latest disclosure from the I.R.S. demonstrates what can be done when attackers gain access to our valuable personal information. Using Social Security numbers, dates of birth, home addresses and other personal information, cyber criminals have accessed over 100,000 past tax returns.
Once they have the past return, they can file a new return with new data including the refund destination account. As a result, the IRS issued $50 million in refunds before detecting the intrusion method.
Fraudulent tax claims are nothing new to the I.R.S. In 2013 the agency paid out a massive $5.8 billion in falsely claimed refunds. IRS spokesperson, John Koskinen, said “These are extremely sophisticated criminals with access to a tremendous amount of data.”
Cyber criminals have amassed a huge amount of data through the many data breaches but also through our own propensity to share our data without due consideration. The IRS has successfully put a stop to this particular form of attack, but with so much data available, it’s only a matter of time before the bad guys work out another way to make fraudulent use of it.
What can you do to protect against identity theft?
Avoid Cold Calls: If you don’t know the person calling then do not hand over payment or personal details. If in doubt, hang up and call the organization directly to establish you are talking to legitimate operators.
Set privacy Settings: Lock down access to your personal data on social media sites, these are commonly used by cybercriminals to socially engineer passwords. Try AVG PrivacyFix, it’s a great tool that will assist you with this.
Destroy documents: Make sure you shred documents before disposing of them as they can contain a lot of personal information.
Check statements and correspondence: Receipts for transactions that you don’t recognize could show up in your mail.
Use strong passwords and two factor authentication: See my previous blog post on this, complex passwords can be remembered simply!
Check that sites are secure: When you are sending personal data online, check that the site is secure – there should be a padlock in the address or status bar or the address should have a ‘https’ at the start. The ‘s’ stands for secure.
Updated security software: Always have updated antivirus software as it will block access to many phishing sites that will ask you for your personal data.
If you believe that you have been affected by a data breach, be sure to take out any identity protection service offered to you as compensation. These services scour the Internet looking for your data being misused or sold.
You can follow me on twitter @tonyatavg
Title image courtesy of dineshdsouza
![]()
![]()