Posted by Daniel Busch on Dec 03
Monthly Archives: December 2014
Re: [The ManageOwnage Series, part IX]: 0-day arbitrary file download in NetFlow Analyzer and IT360
Posted by Pedro Ribeiro on Dec 03
A small correction: the NetFlow vulnerable versions are actually v8.6 to
v10.2 (which is the latest release). I’ve updated the advisory in the repo.
Regards
Pedro
Elipse SCADA Patches Denial-of-Service Vulnerability
Elipse, a Brazilian SCADA software developer, patched a serious denial-of-service vulnerability in the DNP Master Driver deployed in its SCADA web-based application.
Is backing up your data the same as exposing it? In this case – Yes!
Losing contacts from your mobile phone is highly inconvenient. There’s seems to be a solution – You can find them online! The catch? Your contacts are in a publicly accessible place.
Seriously.
If you care for your privacy you should always be suspicious about “Cloud Backup” solutions you find in the Google Play Store. The solution that is being analyzed here backs up your personal contacts online. In public.
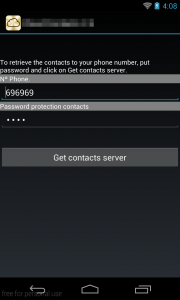
Upon starting the application, you will find a screen where you can put your mobile number and a password of your choice. Then you can upload your contacts in the cloud.
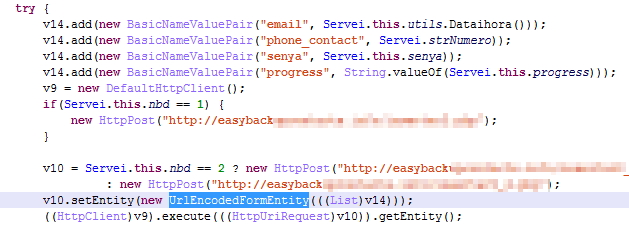
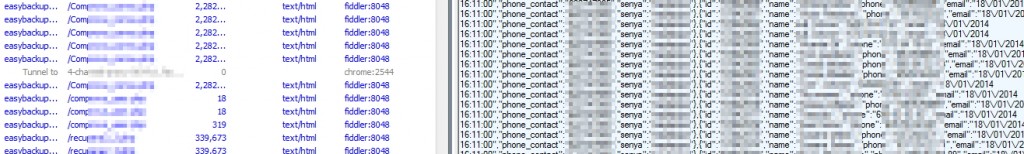
A brief analysis inside this application shows us how exactly it backs up your contacts in the cloud. The contacts are associated with the phone number that you have given in the previous step and they are sent through HTTP POST requests in a PHP page.
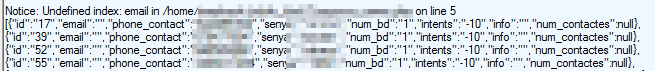
Further analysis through IP traffic capturing with Fiddler helped usdiscover the results in the pictures above; a page located online, for anyone to see, that contains thousands of un-encrypted entries of phone numbers and passwords. Using the info in the app you can retrieve personal private data (contacts) from another user.
We found log in data inside those entries from countries like Greece, Brazil, and others
The Play Store page says that this app has been installed 50.000-100.000 times. This is a big number of installations for an application that doesn’t deliver the basic secure Android coding practices. The developer must use technologies like HTTPS, SSL and encryption on the data that are transferred through the web and stored in the server. Nogotofail is a useful network security testing tool designed by Google to “to help developers and security researchers spot and fix weak TLS/SSL connections and sensitive cleartext traffic on devices and applications in a flexible, scalable, powerful way.“
 The application has been reported to Google without receiving any response.
The application has been reported to Google without receiving any response.
Avast detects it as Android:DataExposed-B [PUP].
Samples (SHA-256):
F51803FD98C727F93E502C13C9A5FD759031CD2A5B5EF8FE71211A0AE7DEC78C 199DD6F3B452247FBCC7B467CB88C6B0486194BD3BA01586355BC32EFFE37FAB
Disabling SSLv3 on the client and server
Recently, some Internet search engines announced that they would prefer websites secured with encryption over those that were not. Of course there are other reasons why securing your website with encryption is beneficial. Protecting authentication credentials, mitigating the use of cookies as a means of tracking and allowing access, providing privacy of your users, and authenticating your own server thus protecting the information you are trying to convey to your users. And while setting up and using encryption on a webserver can be trivial, doing it properly might take a few additional minutes.
Red Hat strives to ship sane defaults that allow both security and availability. Depending on your clients a more stringent or lax configuration may be desirable. Red Hat Support provides both written documentation as well as a friendly person that can help make sense of it all. Inevitably, it is the responsibility of the system owner to secure the systems they host.
Good cryptographic protocols
Protocols are the basis for all cryptography and provide the instructions for implementing ciphers and using certificates. In the asymmetric, or public key, encryption world the protocols are all based off of the Secure Sockets Layer, or SSL, protocol. SSL has come along way since its initial release in 1995. Development has moved relatively quickly and the latest version, Transport Layer Security version 1.2 (TLS 1.2), is now the standard that all new software should be supporting.
Unfortunately some of the software found on the Internet still supports or even requires older versions of the SSL protocol. These older protocols are showing their age and are starting to fail. The most recent example is the POODLE vulnerability which showed how weak SSL 3.0 really is.
In response to the weakened protocol Red Hat has provided advice to disable SSL 3.0 from its products, and help its customers implement the best available cryptography. This is seen in products from Apache httpd to Mozilla Firefox. Because SSL 3.0 is quickly approaching its twentieth birthday it’s probably best to move on to newer and better options.
Of course the protocol can’t fix everything if you’re using bad ciphers.
Good cryptographic ciphers
Cryptographic ciphers are just as important to protect your information. Weak ciphers, like RC4, are still used on the Internet today even though better and more efficient ciphers are available. Unfortunately the recommendations change frequently. What was suggested just a few months ago may no longer be good choices today. As more work goes into researching the available ciphers weaknesses are discovered.
Fortunately there are resources available to help you stay up to date. Mozilla provides recommended cipher choices that are updated regularly. Broken down into three categories, system owners can determine which configuration best meets their needs.
Of course the cipher can’t fix everything if your certificate are not secure.
Certificates
Certificates are what authenticate your server to your users. If an attacker can spoof your certificate they can intercept all traffic going between your server and users. It’s important to protect your keys and certificates once they have been generated. Using a hardware security module (HSM) to store your certificates is a great idea. Using a reputable certificate authority is equally important.
Clients
Most clients that support SSL/TLS encryption automatically try to negotiate the latest version. We found with the POODLE attack that http clients, such as Firefox, could be downgraded to a weak protocol like SSL 3.0. Because of this many server owners went ahead and disabled SSL 3.0 to prevent the downgrade attack from affecting their users. Mozilla has, with their latest version of Firefox, disabled SSL 3.0 by default (although it can be re-enabled for legacy support). Now users are protected even though server owners may be lax in their security (although they are still at the mercy of the server’s cipher and protocol choices).
Much of the work has already been done behind the scenes and in the development of the software that is used to serve up websites as well as consume the data that comes from these servers. The final step is for system owners to implement the technology that is available. While a healthy understanding of cryptography and public key infrastructure is good, it is not necessary to properly implement good cryptographic solutions. What is important is protecting your data and that of your users. Trust is built during every interaction and your website it usually a large part of that interaction.
Kaspersky Lab is Detecting 325,000 New Malicious Files Every Day
Sony hacking: were PlayStation servers used to spread stolen data?
Following the release of confidential documents and four unreleased films, as reported by We Live Security here, the bad news for Sony continued as it was reported that the company’s own PlayStation servers were used to distribute the stolen data, The Independent reports.
The post Sony hacking: were PlayStation servers used to spread stolen data? appeared first on We Live Security.
SA-CONTRIB-2014-116 -Webform Invitation – Cross Site Scripting
- Advisory ID: DRUPAL-SA-CONTRIB-2014-116
- Project: Webform Invitation (third-party module)
- Version: 7.x
- Date: 2014-December-03
- Security risk: 8/25 ( Less Critical) AC:Basic/A:User/CI:None/II:None/E:Theoretical/TD:All
- Vulnerability: Cross Site Scripting
Description
This module enables you to create custom invitation codes for Webforms.
The module failed to sanitize node titles.
This vulnerability is mitigated by the fact that an attacker must have a role with the permission “Webform: Create new content”, “Webform: Edit own content” and/or “Webform: Edit any content”.
CVE identifier(s) issued
- A CVE identifier will be requested, and added upon issuance, in accordance
with Drupal Security Team processes.
Versions affected
- Webform Invitation 7.x-1.x versions prior to 7.x-1.3.
- Webform Invitation 7.x-2.x versions prior to 7.x-2.4.
Drupal core is not affected. If you do not use the contributed Webform Invitation module,
there is nothing you need to do.
Solution
Install the latest version:
- If you use the Webform Invitation module for Drupal 7.x and Webform 7.x-3.x, upgrade to Webform Invitation 7.x-1.3
- If you use the Webform Invitation module for Drupal 7.x and Webform 7.x-4.x, upgrade to Webform Invitation 7.x-2.4
Also see the Webform Invitation project page.
Reported by
Fixed by
- Christian Paul Bruhn the module maintainer
- Pere Orga
Coordinated by
- Ben Dougherty provisional member of the Drupal Security Team
Contact and More Information
The Drupal security team can be reached at security at drupal.org or via the contact form at https://www.drupal.org/contact.
Learn more about the Drupal Security team and their policies, writing secure code for Drupal, and securing your site.
Follow the Drupal Security Team on Twitter at https://twitter.com/drupalsecurity
Avoiding Data Breaches with Context Aware Behavioral Analytics
Avivah Litan of Gartner explains how context aware behavioral analytics may have prevented recent retail breaches and the Snowden, NSA surveillance saga.
With NFC, even the most expensive smartphones are vulnerable

Nowadays we are defined by our phones. When you buy a smartphone, you automatically become a convert, defending the benefits of your particular brand over others. Some users become part of the Apple faithful, flocking to their exclusive stores to buy designer iPhones. Others are Google fanatics, with alerts set in their Nexus 5 to warn of the imminent arrival of Nexus 6. Compulsive Amazon shoppers click away on their Fire Phone cart, while traditionalists continue to trust in the numerous and much-lauded features of Samsung Galaxy.
Unless you are one of those who has joined the retro phone trend and have renounced WhatsApp forever, we are sorry to inform you that your smartphone -whatever the make- has a security flaw. Specifically, in the use of NFC (‘Near Field Communication’), a wireless communications system that lets you transfer data at high frequency over short distances, at a range of 10 centimeters. In fact, NFC is a subset of RFID (Radio-frequency identification) systems that have been used for years now to identify pets (microchips). So if dogs can be recognized through this system, why not phones?
In smartphones, NFC allows data to be exchanged between devices, although a more interesting use for this technology is that it allows our phones to be used as credit cards.

You can already use your NFC to pay for things thanks to Google and its PassWallet app. Apple, not wanting to be left behind, has introduced the Apple Pay system with iPhone 6. And now banks are getting on the mobile payment technology bandwagon. In the future, we will even be able to use phones as subway tickets or door keys. NFC offers the potential for all-in-one devices with myriad uses.
If you weren’t previously aware of this technology, then you must be marveling at the thought of not having to rummage around drawers looking for your wallet or keys. Well, it’s true, but don’t get too excited. Even though the system operates over very short distances, it still has security flaws. In the recent Pw20wn Mobile 2014 competition in Tokyo, where there was a reward of US$150,000 (€120,000) for the sharpest hackers on the planet, security flaws were detected in the NFC systems of many top-of-the-range phones.
Two separate groups of experts demonstrated during the competition different ways of compromising the NFC technology on Samsung Galaxy S5. These hackers are two-nil up on one of the most prestigious smartphones on the market.

Even the all-powerful Google has been unable to keep its precious Nexus 5 free from security problems. In the Pw20wn Mobile 2014 competition, a third NFC attack forced the pairing of devices thanks to a combination of two malicious programs.
And it’s not the first time that an NFC security hole has been uncovered in Google’s device. Charlie Miller, an ‘ethical hacker’, was able to communicate with a Nexus S through a chip placed near the device, as he demonstrated at Black Hat 2012 in Las Vegas. After this he forced the phone to enter a malicious website, from where he took complete control of the phone by exploiting the NFC vulnerability. The Nokia N9 was also subject to the same attack on this occasion.
Although there can be no doubt that the detection of these flaws improves the security of our smartphones, perhaps for the moment at least we all feel a little safer keeping our money and the keys to our houses in our pockets, handbags or under a pile of papers on our desks. Even the sharpest hacker would find it difficult to exploit a security hole there.
Nevertheless, your NFC could still be useful for many things. And no doubt it will gradually become more secure. For the moment, fans of Nexus 6 are looking forward to getting their hands on it, and plans are afoot to unlock the phone automatically with the help of an NFC ring on the user’s finger. Could the phone’s PIN also be hacked? Let’s see.
The post With NFC, even the most expensive smartphones are vulnerable appeared first on MediaCenter Panda Security.