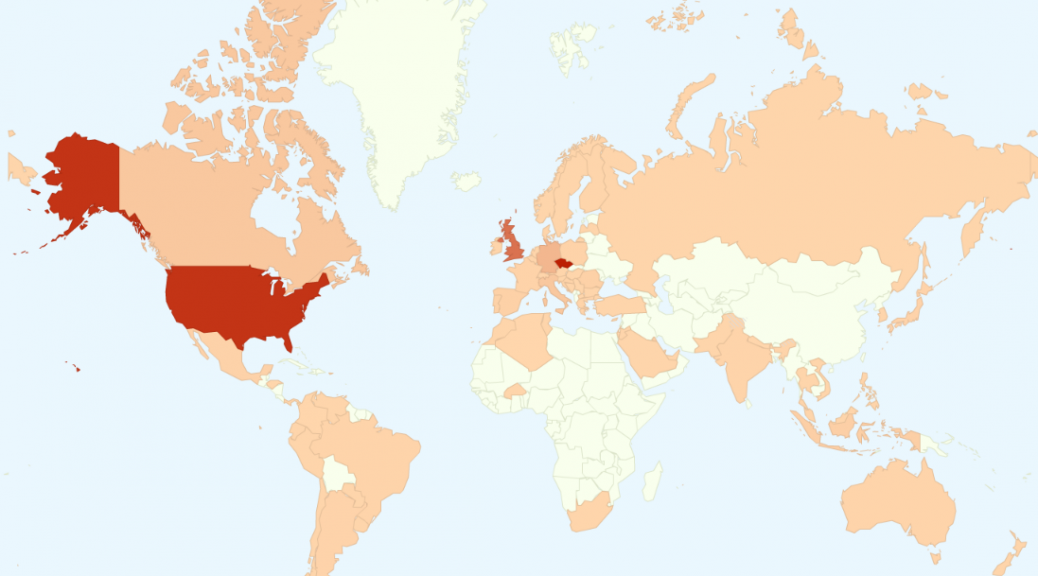
Over the last few months, AVG has tracked the rapid spread of a banking Trojan known as Vawtrak (aka Neverquest or Snifula).
Once it has infected a system, Vawtrak gains access to bank accounts visited by the victim. Furthermore, Vawtrak uses the infamous Pony module for stealing a wide range of login credentials.
While Vawtrak Trojans are not new, this particular sample is of great interest.
How and where is it spreading?
The Vawtrak Trojkan spreads in three main ways:
- Drive-by download – in the form of spam email attachments or links to compromised sites
- Malware downloader – such as Zemot or Chaintor
- Exploit kit – such as Angler
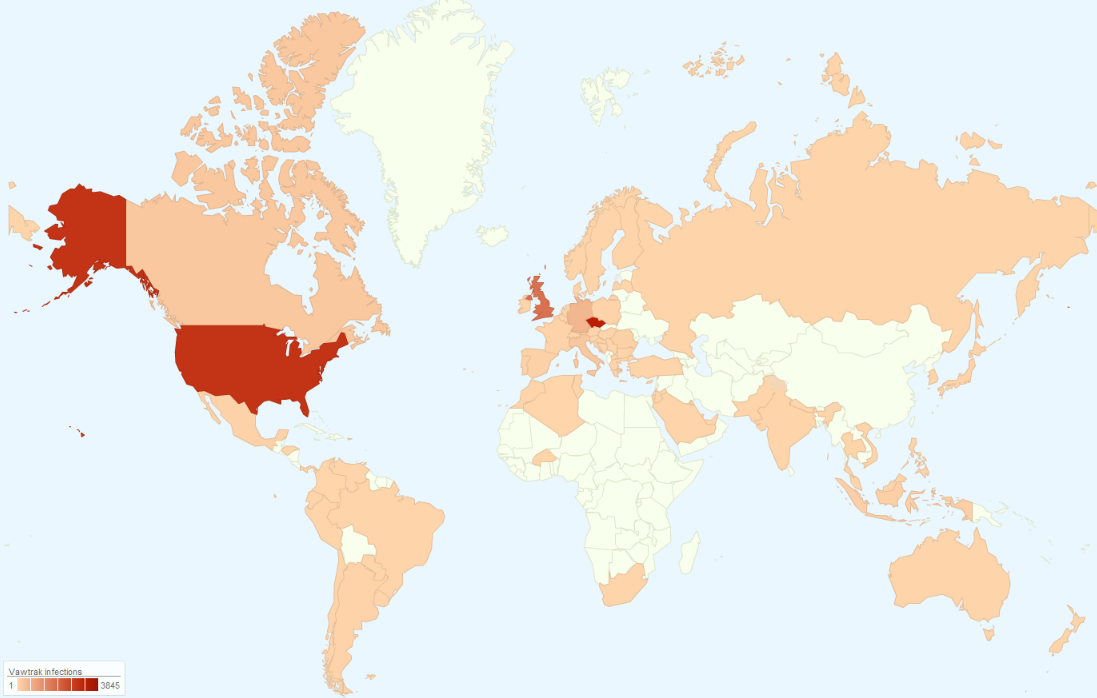
Based on our statistics, the Czech Republic, USA, UK, and Germany are the most affected countries by the Vawtrak campaigns this year.
What are the features of this Vawtrak?
This Vawtrak sample is remarkable for the high number of functions that it can execute on a victim’s machine. These include:
- Theft of multiple types of passwords used by user online or stored on a local machine;
- Injection of custom code in a user-displayed web pages (this is mostly related to online banking);
- Surveillance of the user (key logging, taking screenshots, capturing video);
- Creating a remote access to a user’s machine (VNC, SOCKS);
- Automatic updating.
Of particular interest from a security standpoint is that by using Tor2web proxy, it can access update servers that are hosted on the Tor hidden web services without installing specialist software such as Torbrowser.
Moreover, the communication with the remote server is done over SSL, which adds further encryption.
This Vawtrak sample also uses steganography to hide update files inside of favicons so that downloading them does not seem suspicious. Each favicon is only few kilobytes in size, but it is enough to carry a digitally signed update file hidden inside.
Detailed analysis
Our complete analysis of this malware is too long to publish in full on this blog so we have prepared a detailed white paper that describes this infection, its internals and functions in detail.
You can also download the report here
Stay Safe
While this Vawtrak Trojan is very flexible in functionality, it’s coding is mostly basic and can be defended against. At AVG, we protect our users from Vawtrak in several ways:
- AVG LinkScanner and Online Shield provide real-time scanning of clicked links and web pages containing malicious code.
- AVG Antivirus for generic detection of malicious files and regular scans.
- AVG Identity Protection, that uses a behavioral-based detection, will detect even the latest versions of such infections.
- AVG Firewall prevents any unsolicited network traffic, such as communication with a C&C server.