Some webpages are giving away free codes for Playstation Network and Steam but, are they reliable?
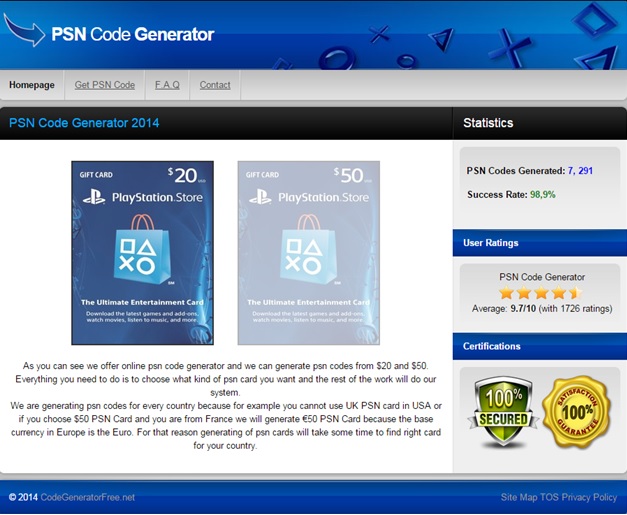
At Avast we discovered a lot of webpages offering free codes, with a value from $20 to $50, for Playstation Network and Steam, two of the most important internet-based digital distribution platforms. Those webpages look very suspicious so we decided to analyze them.
We chose one of those webpages and followed all the steps required in order to get our “free code” for Playstation Network or Steam.
After a first look at the main page, we found some suspicious items. To prove how trustworthy the transaction is, the webpage placed two security “certifications” in a visible location, but as we discovered, no security companies are associated with those certifications. They are completely fake!
Also, there’s a label with user ratings (4 ½ stars!), but we cannot rate the webpage; it’s just an image. Both fake images make the users think that they are in a safe and reliable website.
What happens when we click on a gift card? Are we going to receive the code?
The answer is no.
Let’s see what’s next:
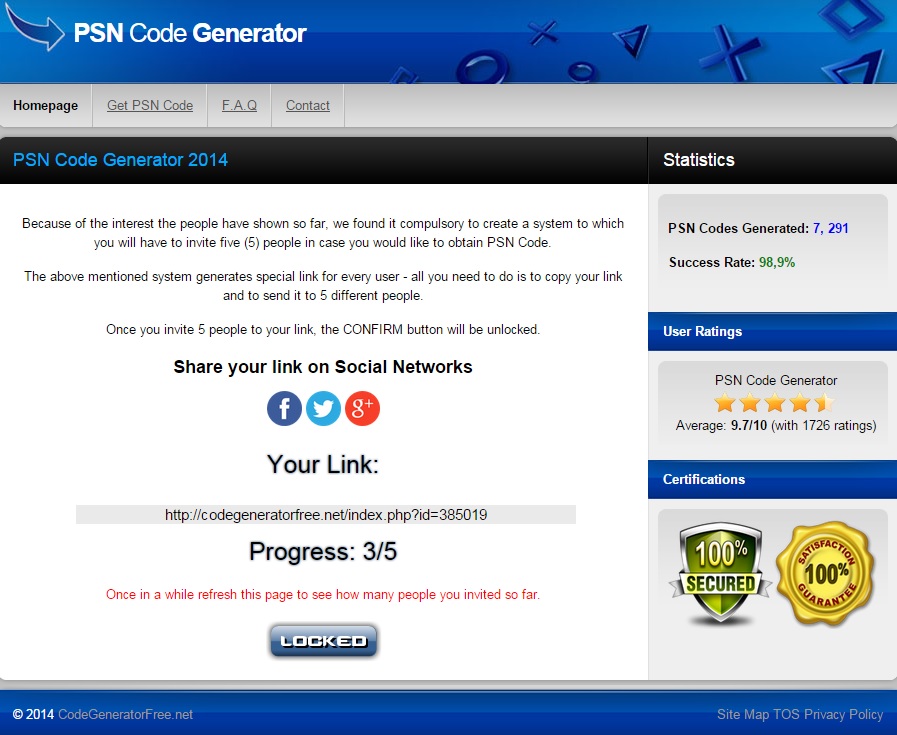
When we click on a gift card¸ instead of receiving the promised free code, we are asked to share a link with our friends in order to unlock the code.
Why do they do that?
When we share the link we are contributing to an increase in the number of visitors and, of course, the number of people that will try to redeem the “free code.” Keep this in mind, it will be important at the end of this post.
Ok, we already invited 5 of our friends and, in theory, we unlocked the code. Is this the last step? Are we going to receive the code now?
Again, the answer is no.
Looks like they don’t want to give us the code. Suspicious, right? So, what do they want now?
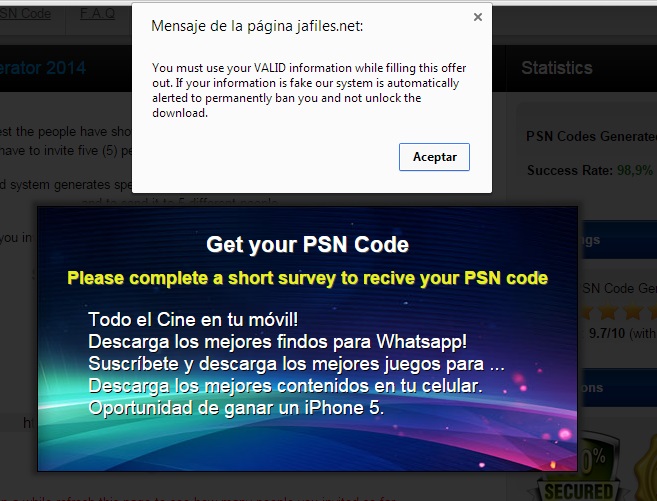
As we can see in the image, in order to receive our PSN code, we need to complete a short survey (like inviting 5 friends wasn’t already enough?!).
When we click on one of the surveys, a little pop-up with a message appears on the top of the screen. The message says: “You must use your VALID information while filling this offer out”.
Why do they need our VALID information?
Here’s the reason:
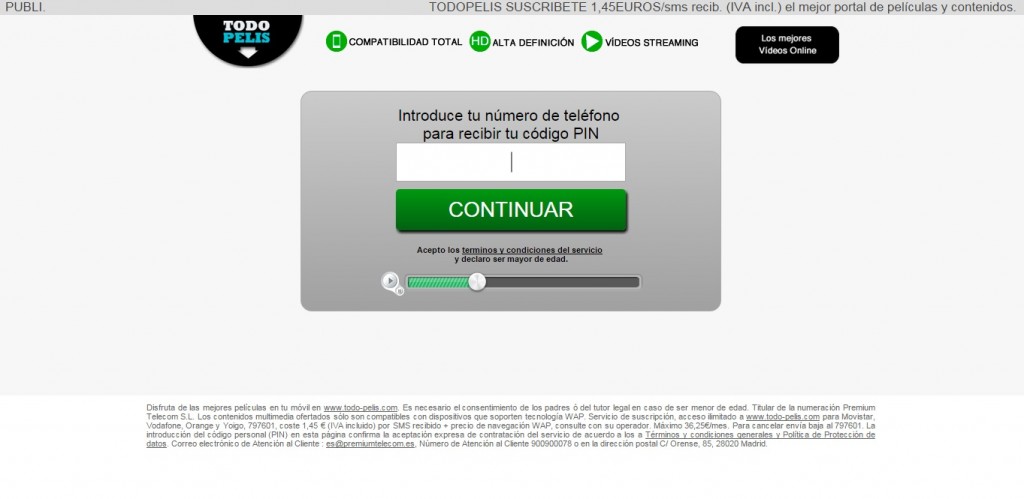
In order to receive the code, we need to introduce our phone number – our VALID phone number. But wait, before doing that, let’s read the text at the bottom of the page.
Surprise! It’s a premium SMS service with a total amount of 36,25€/month (>$40/month)! If we enter our phone number, we will be automatically subscribed to this premium service.
Remember the 5 friends you sent the link to? Well, now imagine how many people can fall into this scam just by sharing a link to 5 friends: 5+(5*5)+(5*5*5)+… creepy, right?
And of course, there’s no free code for your PSN or Steam accounts.
Unfortunately, there’s a lot of webpages using the same method to get user’s money. Also, there are other webpages offering software to generate codes. Cybercrooks create those
fake apps and get money from “download servers” because they bring
them users.
Tonda Hýža, from the AVAST Virus Lab, described those webpages as Adware due to the big amount of lies, advertisements and weird privacy policies.
Make sure you share this alert with your gamer friends J
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.