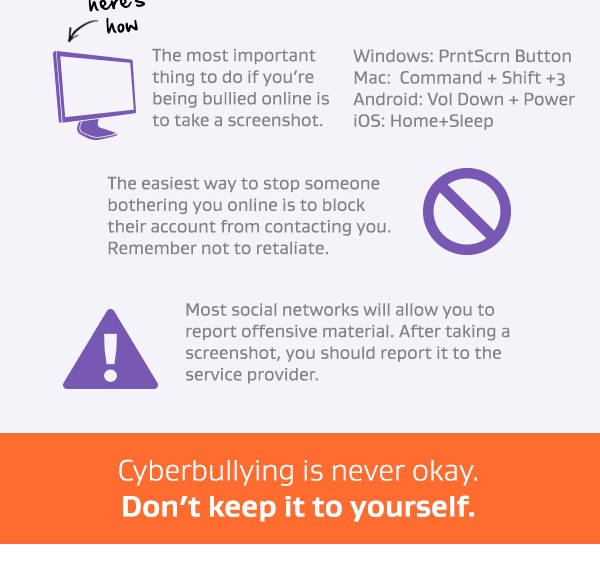
Each country has its own initiatives for protecting kids online. In the UK, for example, we have “Active Choice” which makes adult content opt-in rather than opt out. But I believe, that around the world, parents should be the first line of defense and guidance for our kids.
When we talk about children spending time online, it’s important to remember that our children do not have what we term ‘digital lives’. Technology is normal to them and part of growing up in today’s world.
I often hear parents raise concerns about how much time their children spend online and on devices. Generally I observe that they are equally guilty of this digital overindulgence. As ever, children mimic their parents’ behavior.
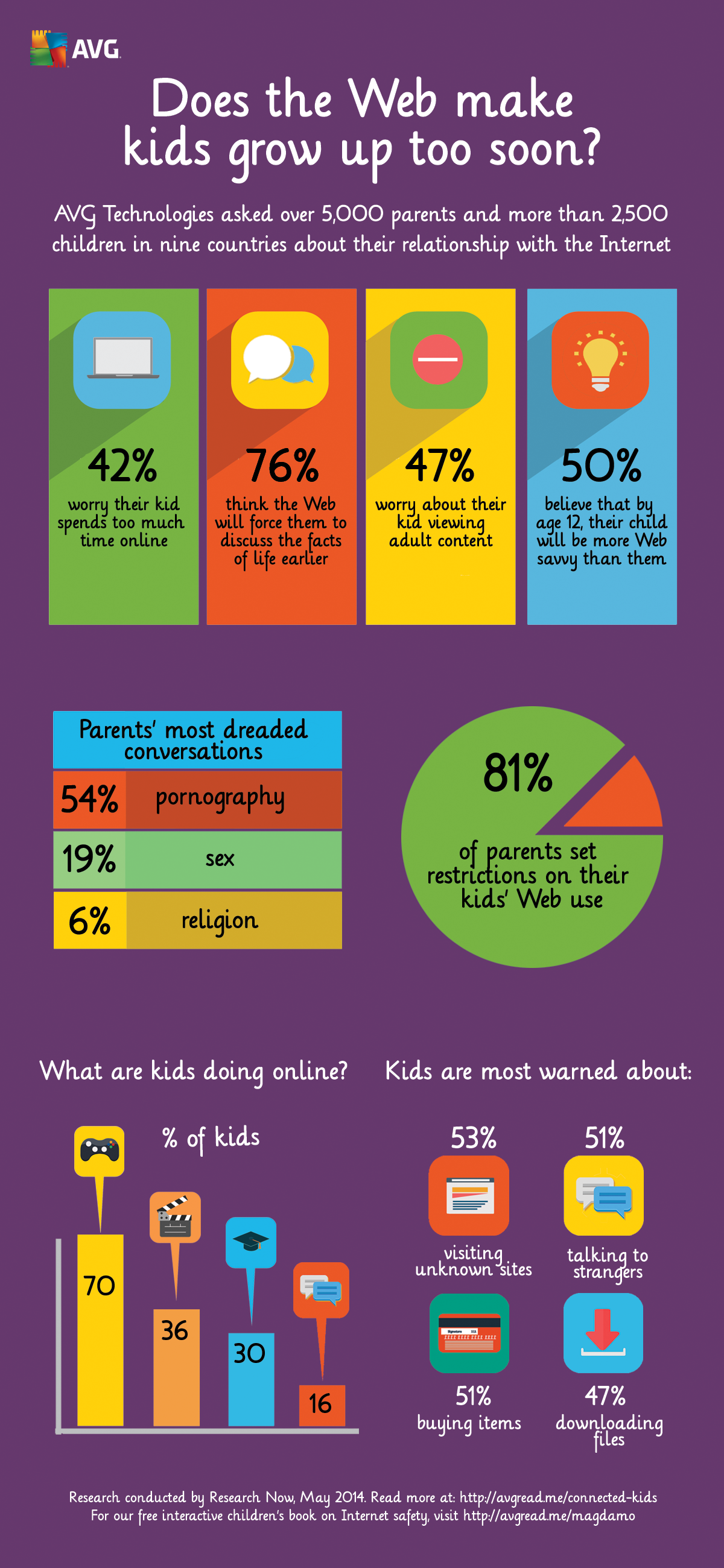
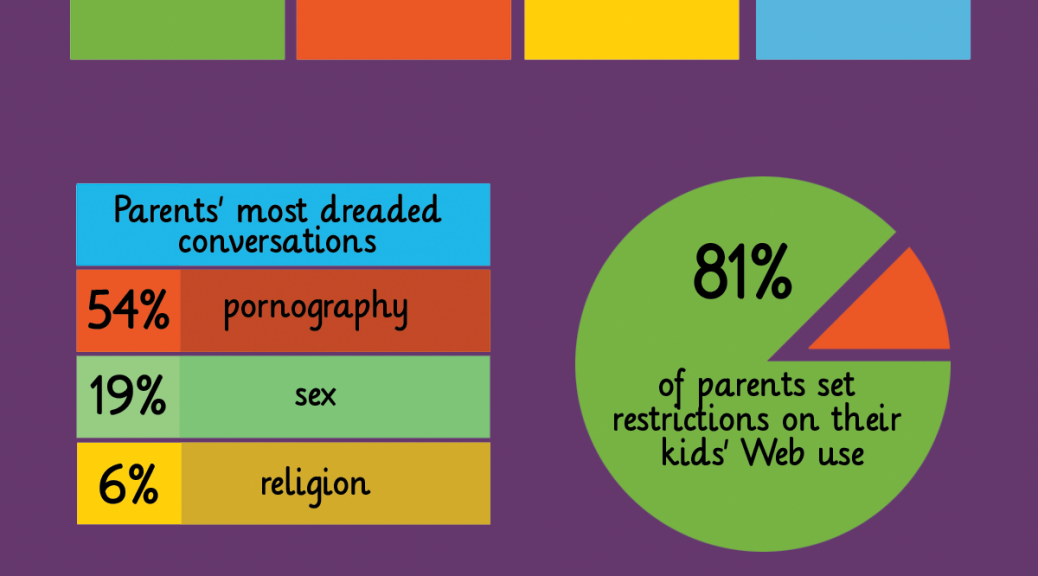
AVG Digital Diaries research last year examined how the Internet is having an impact on how quickly kids grow up. Our findings showed that children are increasingly interacting with digital devices,and 42% of the parents polled by AVG said that they are concerned that their child spends too much time on devices, and a similar number (43%) said they were worried their child didn’t spend enough time outside.
So who is responsible for the time our kids spend online? I believe that parents are, yet 42% of them say they are concerned about it.
As Safer Internet Day has just passed, I challenge the 42% in our survey last year to take charge of the technology in their homes and to correct the balance.
You might not be popular today but introducing other life skills is a good thing to do. Remember, technology is not a babysitter!
We’ve put together more statistics from the AVG Digital Diaries research in this infographic below.