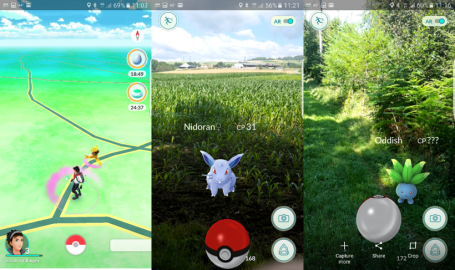
Pokémon GO is killing smartphones in less than 3 hours. Check out our in-depth app analysis of the phenomenon and 7 battery-boosting secrets to keep on hunting on the go.
Even compared to social or streaming apps like Facebook and Spotify, games are the real phone battery vampires (see our latest “AVG App Performance and Trends Report” for the top 10 ‘resource hogs’). And an augmented reality (AR) game like Pokémon Go makes even other game apps seem downright generous, as it constantly and simultaneously requires your phone to
- Share location via GPS
- Keep the screen fully lit
- Operate the camera
- Play sounds through the speakers, and
- Render 3D graphics.
Whew. The result? When I played Pokémon Go on my morning run, my battery went from 100% to 50% in less than 90 minutes.
“This has got to be the single most battery-hungry app I’ve ever used,” I thought. Being a data-driven guy, as well as a hardcore gamer (PC and console gaming more than mobile, though—more about that in a future post!), I immediately tested my theory and discovered that, if you’re nonstop seeking, catching, and levelling Pokémon, then your …
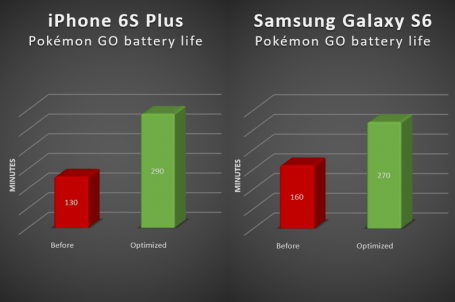
- iPhone 6S Plus battery will go from from 100% to 0% in 2 hours and 10 minutes.
- Samsung Galaxy S6 will survive Pokémon Go fever only an additional half-hour, lasting 2 hours and 40 Minutes before the screen goes dark.

Enough! I refused to let battery issues get in the way of my mastering the game (full disclosure, I’m so far only at level 15 with about 200 Pokémons collected, but I am full-on obsessed). I proceeded to systematically try every battery-saving technique I know (plus a battery-saving Android app), and turns out the effort was worth it.
AND THE RESULT? The following tweaks made my phone battery last more than 5 hours during gameplay. That’s a 123% increase. Which could mean … 123% more Pokémons.
(And so you know my outcomes weren’t a fluke, I repeated each test 3 times and averaged the results, for accurate data. I’m nothing if not thorough.)
1 – Use built-in Pokémon Go battery saver instead of reducing screen brightness (Android + iOS)
There’s no lack of quick online tips for boosting battery life when playing Pokémon Go, and most involve reducing screen brightness. Sure, it allows you to play longer, do you really think this is an enjoyable way to play?

Reducing brightness increases reflections, particularly in direct sunlight (and, um, a whole lot of the fun of Pokémon Go involves running around outside—notice they didn’t release the game in the middle of winter). Sure, this might be tolerable at night or indoors, but to really enjoy such a fun, colorful game, you’ll want to keep the brightness above 75%.
So instead of dimming, activate Pokémon Go’s built-in battery saver and keep the brightness near maximum. When you put your phone in your pocket or hold it upside down, the built-in battery saver will automatically make the screen go dark.
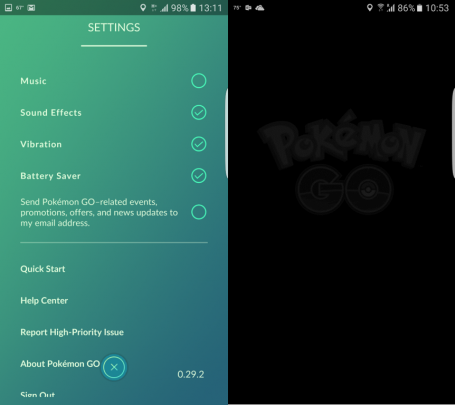
HOW TO DO IT
- Tap on the Pokéball icon
- Go to Settings
- Tap on Battery Saver
In battery saver mode, you remain logged in to the game and can hear sounds or feel vibration when Pokémons are nearby, without the massive power drain. While you’re at it, you can also turn off music or sound effects, which also has a slight effect on battery life. Just don’t turn off vibration, otherwise you won’t know when one of the pocket monsters is nearby, wanting to be caught!
2 – Turn off Bluetooth and WiFi (or 3G/4G)
The game requires a nonstop data connection and a GPS signal. So if you’re at home, don’t use your 4G/LTE connection, which is one of the heaviest resource drainers you’ve got.
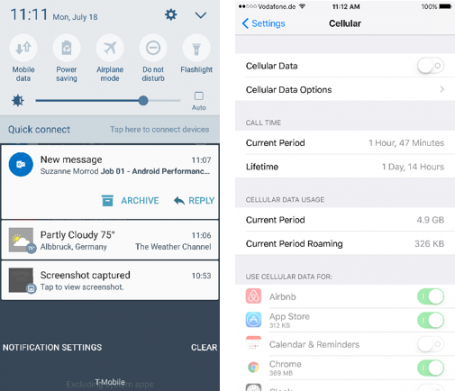
HOW TO DO IT
- iOS: Go to Settings, Cellular and switch off Cellular Data
- Android: Swipe down to bring up the quick actions and notifications center, turn off Mobile Data
If you absolutely need your mobile data connection (if you’re out and about), use a 3G connection, which often uses less battery than does 4G/LTE. The rule here is … there is no rule yet, you’ll need to test this a bit for yourself.
While 4G/LTE chips have become more efficient, in some rural areas with spotty connections you might end up draining the battery more quickly than when you’re using a solid 3G connection—or vice versa! Fortunately, Pokémon Go doesn’t drain a ton of data. During my 24 hours of nonstop testing, playing used only 4.2 MB on my iPhone and 5.9 MB on my Galaxy S6.
However, while this isn’t a lot of data, the game does transfer a lot of small data packets back and forth, preventing your 3G/4G/LTE chip from going to sleep, meaning it consumes more than it should. If you’re on the go, you should also make sure that WiFi and Bluetooth are turned off, to give a little more edge to your battery life.
3 – Use iOS and Android’s battery saver
Both iOS and Android offer built-in battery savers that, for example, throttle your phone’s performance a bit, use a more energy-efficient display color temperature, and reduce background app activities to a bare minimum.
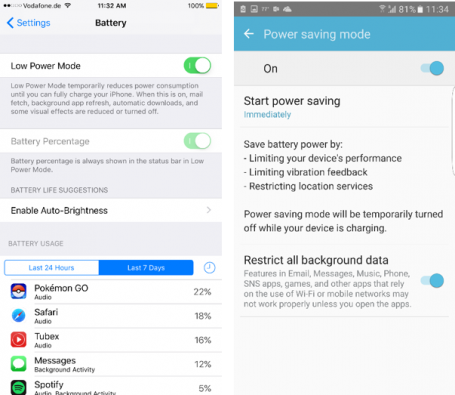
HOW TO DO IT
- iOS: Settings, Battery and Low Power Mode
- Android: Settings, Battery and Power saving mode (flip the switch)
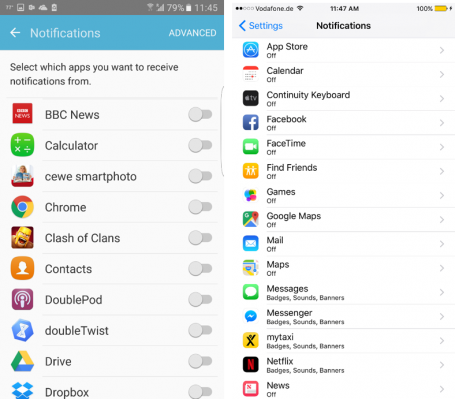
4 – Don’t use any unnecessary resource-eating apps
As our regular AVG App Performance and Trends report has shown, background apps can kill your smartphone’s battery even if you’re not using them actively.
To prevent that from raining on your Pokémon Go parade, turn off background activities and notifications for all apps you don’t need (in addition to the power savers, which limit most, but not all background activities). By doing so, your phone will spend less battery life checking for and displaying app notifications.
HOW TO DO IT
- On both Android and iOS, you’ll find the notification settings under Settings and Notifications
- Flip the switch for all apps whose alerts you can do without
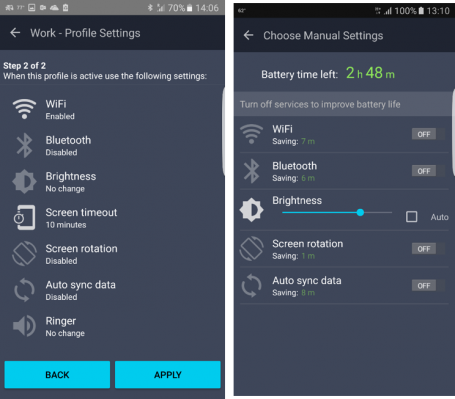
5 – Use a dedicated battery booster (Android only)
To save even more battery life for Pokémon Go, I’ve also used our own AVG Cleaner for Android 3.3, which comes with dedicated battery profiles and even more settings to save battery life when you really need it (for example, when you’re trying to level up Pidgeotto).
HOW TO DO IT
- Download the free app, open it and tap on Battery.
- Now you have multiple choices …
- Go to Choose Manual Settings and turn off battery-draining functionality like WiFi, Bluetooth, Brightness, Screen rotation and Auto sync data.
- Select Home profile when you’re playing at home and Car profile when you’re out and about. Quickly switching between them helps squeeze even more juice from your phone’s battery.
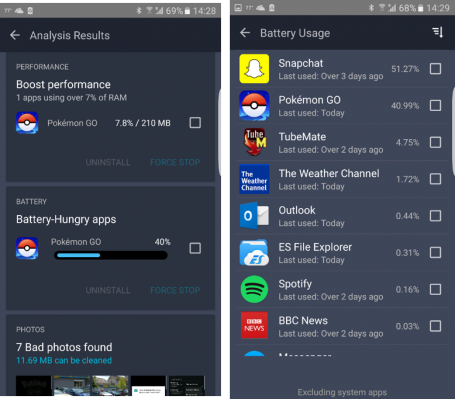
- Bonus tip: After you’ve used it for a day or two, AVG Cleaner for Android will automatically show you your phone’s top battery-drainers, so you know which apps to avoid, stop, or even uninstall when playing Pokémon Go.
- Open the app and tap on Analyze. Scroll down to the Battery-Hungry apps section and Force Stop or Uninstall what you don’t need. For a full list, go back to the main menu of AVG Cleaner and tap on Battery.
6 – Don’t zoom, don’t rotate, use less AR
One of the biggest drains on your phone’s battery is the GPU (Graphic Processing Unit), which is responsible for all the nifty 3D rendering in games, websites, videos and, well, everything you see on your display. Since 3D animations cost a lot of cycles, keep the rotation and zooming on the Pokémon Go map to an absolute minimum.
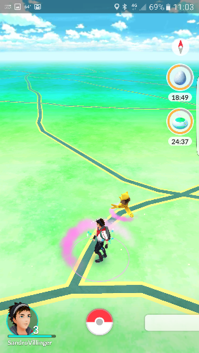
Also, when catching a Pokémon, turn off the AR (camera) feature if you’re running low on battery, by flipping the switch in the lower right corner. Instead of the camera picture (which drains more battery), you’ll see a static landscape that’s a bit more power-saving.

7 – Or … give up and get a battery pack!
For my longer trips overseas I usually bring an external battery to keep my phones and laptops charged (not all airlines have gotten the message that people might appreciate a power plug on every seat). And while you don’t necessarily need a brick like this …

… any battery pack that’ll charge up your phone at least twice should be good to satisfy your daily monster-catching needs.
Did it Work?
Let’s turn it over to you: Did our tips help you get through the day when playing Pokémon Go? Got more tips to share? Let us know in the comments!
![]()
![]()