In this blog, we’ll guide you through seven new and hidden things in the upcoming Windows 10 release so you’re fully prepared for what’s about to come to your PC.
The Windows 10 Anniversary Update comes out in July 2016. This is both good and bad news for you.
Let’s do the bad news first: On July 29th, Windows 10 will no longer be available as a free upgrade. You will only be able to purchase it as a standalone item (or via the purchase of a new PC or laptop). So if you haven’t got it already, you better act quick and make sure you’ve reserved your free upgrade for all your Windows 7 and 8.1 devices.
The good news: Windows 10 Anniversary Update is more than your traditional Service Pack. Its slightly updated look combines more performance tools, bug fixes, and features than any other update that has come before. Free of charge.
In this blog, we’ll guide you through seven new and hidden things in the upcoming Windows 10 release so you’re prepared for what’s coming to your PC. Note that most of this is already visible if you’re running Windows 10 Insider Build.
- Restarting The Start Button…again?
I can still hear the outcries when Microsoft introduced the Start screen in Windows 8, a full-screen cluster of tiles and that infamously removed the classic Start button and menu combination. Sure enough, they backpedaled with their “Big 10” last year and reintroduced the start menu, much to everyone’s satisfaction. But apparently Microsoft still isn’t quite happy with the Start menu, so they’ve been tweaking things.
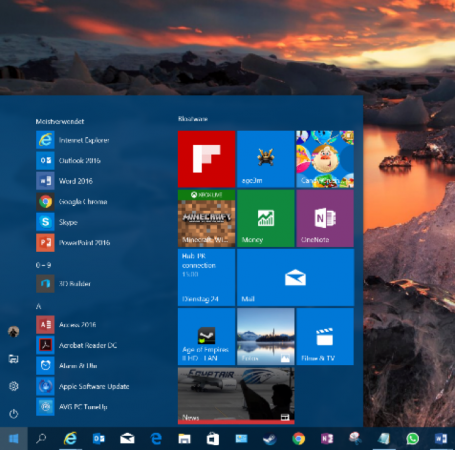
The three entries All Apps, Power, and Settings have now been reduced to icons – that will make it a bit tougher for beginners to find these. But it leaves more space for the list of apps and your tiles. Also new are interactive tiles. For example, the map tile will not just show you information but also let you interact with it. This is nothing revolutionary, but nice tweaks going forward.
- Information Overload: The New Notification Center
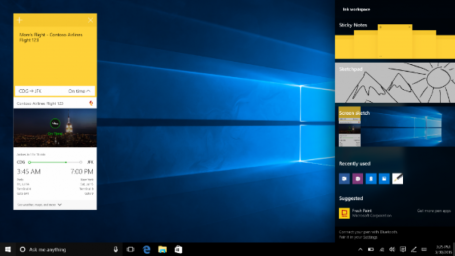
Clicking on the little speech bubble in the lower right corner will reveal a drastically updated notification center, which you can use to pin sticky notes, quickly sketch something, get access to apps you most recently used, and customize quick-action buttons, also in the lower right corner:
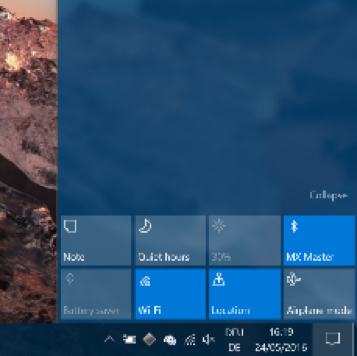
Going forward, this area will also link to your phone to display notifications such as incoming text messages that you can reply to from your PC. Microsoft’s new browser (“Edge”) will show notifications, so you can stay up-to-date on news from your favorite websites. Upcoming calendar appointments will also make an appearance to give you a quick-glance look at what’s happening.
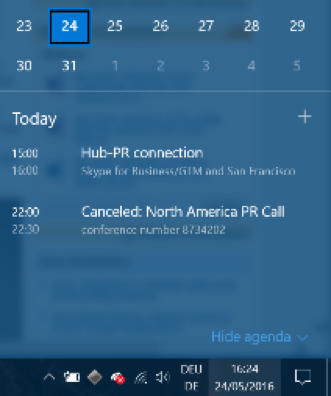
- Dark Mode
For those dark souls among us: Microsoft has gone “cool”, with a Windows 10 Dark Mode, which “paints” all third-party apps and certain parts of the Windows user interface black. This won’t just look a bit sleeker (to some), but it will also match the color schemes used by many applications (such as our own AVG products or Adobe’s Creative Suite) quite nicely. At the same time, it draws attention to the center of the screen and not Windows itself:
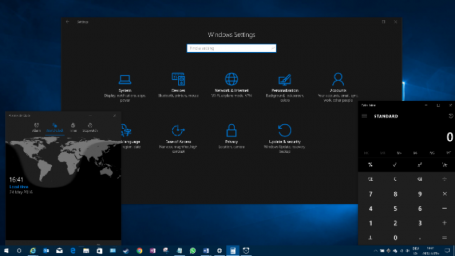
Once you have Windows 10 installed, simply head over to the Personalization category in your Windows Settings app and click on Dark!
- Linux + Windows = Bash!
For all those (super) tech geeks among you, the new Bash shell integrates a complete Linux command line into Windows. However, it’s not a full blown Linux virtual machine. Rather, it is simply a developer toolset that integrates some useful Linux commands and environments into Windows. All you coders out there using both Windows and Linux developing tools, head on over to Microsoft’s Scott Hanselmann for more information.
(Credit: Microsoft)
- On the bleeding Edge
Windows 10’s default browser, Edge, is also getting some welcome improvements that might just make me switch from Chrome or IE. First of all, Edge is being opened to long-awaited plug-ins (extensions), with some software makers getting an (invitation only) head start. Once the Windows 10 Anniversary Update rolls out, we will see what these add-ins are capable of. Many of you can’t live without plug-ins like LastPass in your browser – so it’ll be exciting to see if such plug-ins boost Edge adoption.
Plus, here’s another benefit close to my heart: Edge will pause Adobe Flash content that’s not critical to a website you’re looking at, putting a stop to nonsense advertising or animation that’s slows down your PC’s performance and shortens battery life.
Also new in Edge are Tab previews that give you a peek at websites loaded in the background without you having to look away from your current page.
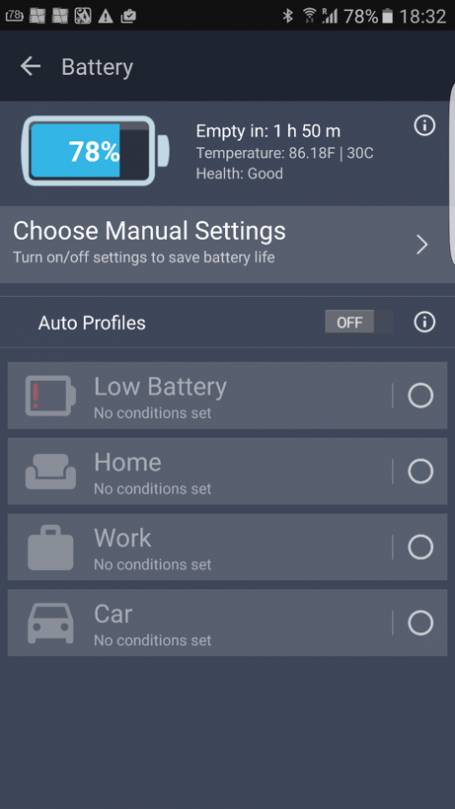
- Battery Saver 2.0
If you’re out and about, the new battery saver in Windows 10 will give you a sneak peek into which apps or traditional Windows programs are draining your battery.
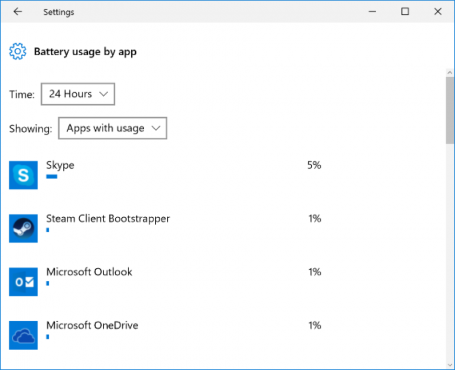
To help boost battery life, you can put Windows Apps to sleep using Windows’ own Battery Saver. You’ll find that in the new Windows Settings app under Devices and Battery. (To get even more life from your battery, we suggest using our own AVG Performance in Economy Mode.)
- Smarter Cortana
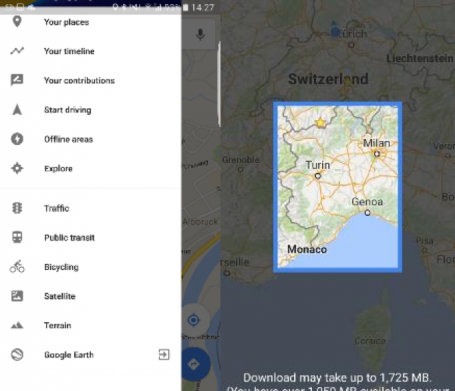
Voice assistant Cortana is getting a major overhaul in Windows 10 Anniversary Update. What was once very limited to local files and online (Bing) search results will now be tied deeply to your default Windows, email, calendar, and Office applications. This will give you more contextual voice commands, such as “Send Joe the Word file I worked on an hour ago”. It will also give software developers the ability to integrate Cortana into their own apps. That would, for example, give you the opportunity to order a pizza via a simple voice command on your PC. Neat. Even in the currently available Windows Insider preview, Cortana works quite well on the desktop. A simple voice command (“Give me directions to Monaco!”) showed me this:
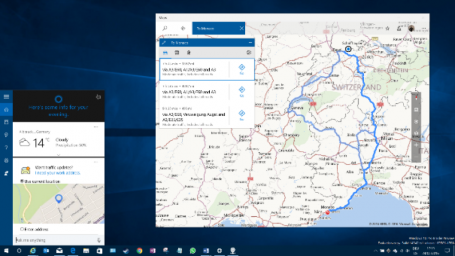
In less than a second.
These are my seven highlights for Windows 10. Again, make sure you’re making good use of the free Windows 10 upgrade offer while it’s still available, and have fun checking out the new stuff as it’s rolled out in July or August.


![]()
![]()