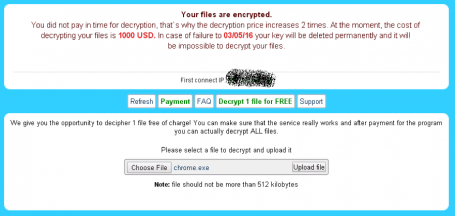
Alina Simone’s gripping 2015 account of her mother’s extortion ordeal was the first time many non-tech people had heard the term “Ransomware”. It presented a threat that felt intensely personal. It blocked access to data we use to define ourselves: family photos, letters to relatives, tax and financial records, and beloved music and movies.
Flash forward a year, and ransomware is all over the media. The reason for its rise is simple: money.
Before the emergence of ransomware, criminals mainly used (and still use) malware to take control of machines. Malicious code harvested user names, passwords, and credit card numbers. It might have also used infected PCs in a botnet for sending spam or launching attacks that shut down major websites, usually as a decoy while hackers broke in elsewhere.
For Criminals, Ransomware Is Lucrative
Ransomware cuts out the digital middlemen. Rather than collect credit card details that must then be sold on the dark web for a few cents to a few dollars, ransomware demands money directly from the victims. While the amount varies, it tends to be few hundred dollars for individuals.
Yet these small sums are taking a heavy toll. The exact number of ransomware attacks is hard to gauge, as many go unreported. But according to our data they are rising fast. While official complaints about ransomware (and ransoms paid) to the US Department of Justice amounted to only around $24 million in damages in 2015, other numbers are much higher. In April, CNBC estimated the cost of ransomware at around $200 million in the first three months of 2016 alone. Late last year, the Cyber Threat Alliance stated that a single piece of ransomware, CrytopWall v3, resulted in an estimated $325 million in damages worldwide over the course of its lifetime. And as far back as June 2014, the FBI issued a report saying CryptoLocker swindled more than $27 million from users over a two-month period.
Bigger Targets May Mean Bigger Paydays
These numbers speak to the audacity of ransomware purveyors. The long-tail effect of attacking individuals has proven so lucrative, it is unlikely to ever go away. But many organizations also hold sensitive customer data that needs to be protected both to ensure effective service and consumer privacy. That makes them particularly juicy targets to hackers.
Healthcare provides are a case in point. If they lose control of patient information, they may be unable to deliver treatment when needed. There are also strict legal requirements governing the protection of patient data. Both make them subject to lawsuits that could cost them far more than what they would have to pay in ransom. A hospital in Hollywood, California, paid $17,000 in bitcoin to hackers after being locked out of their data. Fortunately, so far, other reported attacks have fared less well. Healthcare providers in Kentucky and Ottawa refused to pay, as no patient data was compromised; and an attack in Germany was quickly contained by fast-acting IT staff.
Still, the hospitals have had to invest considerable time and resources into fighting the attacks. They will also need to launch multiple efforts internally and externally to restore patient trust.
And hospitals are not alone. A 2016 report by the Institute for Critical Infrastructure Technology, an industry think tank, declares 2016 the year of ransomware, suggesting few organizations are safe. For instance, systems at an Israeli electrical utility were infected by ransomware after a phishing attack. A utility in Michigan has been allegedly attacked. Multiple police stations have been hit and paid ransoms to regain access to their systems. Local governments are increasingly feeling the pressure, with attacks reported in places as diverse as Alto City, Texas, and Lincolnshire, UK. And criminals have subverted online adverts of venerable media organizations, such as the BBC and NYT, turning their websites into potential sources of drive-by ransomware.
The Right Protection Saves Money
This is why protection is essential, especially for individual users, most of whom lack the expertise and resources of even modest city councils and small hospitals. Over a three-month period earlier this year, a conservative estimate by AVG is that its antivirus prevented around $47 million in extortion demands through the interception of just three types of ransomware: Cryt0L0cker, CryptoWall, and TeslaCrypt. And that number says nothing of the mental and emotional costs that would have resulted from feeling violated or the costs of replacing machines, software, and media if a victim decided not to pay.
AVG does not recommend paying. There is no guarantee criminals will release the files. They may also leave a piece of malicious code behind that allows them to strike again. It is better to call tech support, salvage what you can, make frequent backups, and build a fortress around your PC – and thus prevent the writing of another news story like Alina Simone’s.


![]()
![]()