String of Fileless Malware Attacks Possibly Tied to Single Hacker Group – PCWorld
Category Archives: Antivirus Vendors
Antivirus Vendors
Panda Security Detects 100% of malware, According to AV- Comparatives

Panda Security has obtained a 100% detection rate on February’s Real-World Protection Test from the independent labs of AV- Comparatives. The Real-World Test is recognized in the industry for providing an accurate reflection of the protection offered by cybersecurity solutions readily available on the market
Panda Security obtained the highest possible score, topping the list of twenty other providers that also underwent testing.
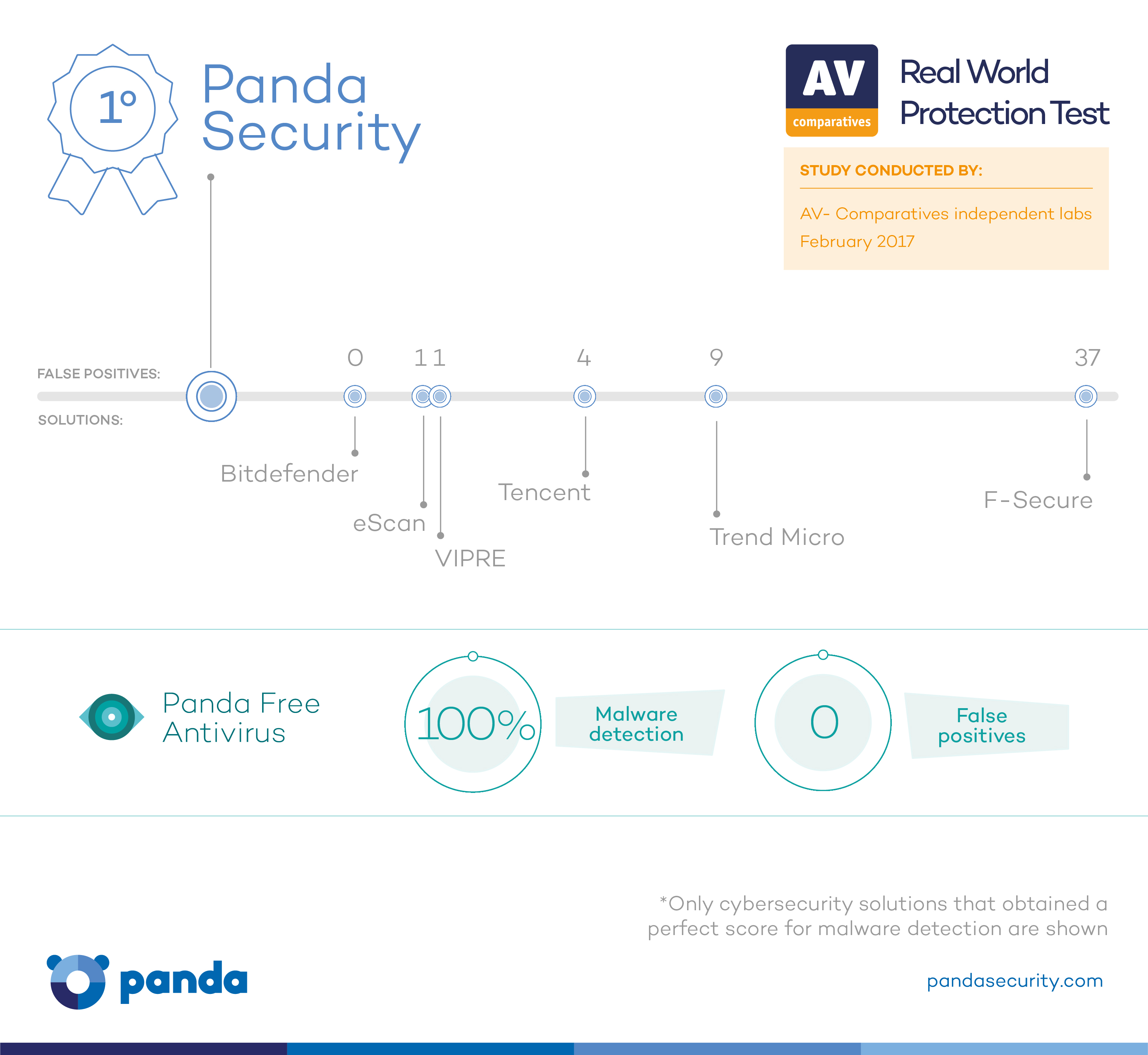
The analysis, which is available here, takes into account the same infection vectors that a user might experience on any normal day (browsing websites containing malicious content or exploits, running a virus received by email, etc.). In this case, Panda Free Antivirus was able to detect 100% of the malware to which it had been exposed. The fundamental objective of the Real-World Test is to determine if security solutions are able to protect the system as it is exposed to an array of malware samples.
Panda Security, 100% Detection and Zero False Positives in AV- Comparatives’ Most Rigorous Test
“We are especially pleased with the excellent results obtained in the AV-Comparatives Real-World Test because they validate our efforts to offer our users the best protection against all types of threats in real conditions. We are fully committed to the constant improvement of our solutions in order to provide maximum security levels with minimum performance impact, being more aggressive towards threats the bigger the risk of infection” said Alberto Añón, Consumer Product Manager in Panda Security
This result speaks to the success of the set of technologies present in the company’s cybersecurity solutions, ideal for all types of users, private or professional, and for everyone from freelancers to large corporations.
Panda Security has developed its products in response to the rapid evolution of malware in recent years. In this regard, it offers the most effective response to threats like ransomware and proves to be the best ally in the prevention, protection and response to the latest attacks.
Latest updates
The company recently launched their Panda Protection, the multi-device antivirus protection that adapts to the user’s needs through a monthly service subscription.
The post Panda Security Detects 100% of malware, According to AV- Comparatives appeared first on Panda Security Mediacenter.
Partner or perish: Why SMBs need MSPs
We were surprised by a recent research report that found enterprises are moving more quickly to managed security service providers (57 percent to provide 24×7 IT systems monitoring, 45 percent for threat detection and intelligence, and 41 percent for technology assessment and analysis). The results were surprising because SMBs are facing even more threats than enterprises, and they have less resources – tools, skills, and personnel.
![]()
In the Wake of the CIA WikiLeaks Case, Some Tips on Corporate Cybersecurity

Year Zero, the first delivery from WikiLeaks of the “biggest document leak” the Central Intelligence Agency has ever seen, is made up of over 8,000 files. The revelations they contain are causing quite a stir. If nothing else, they’ve shown that the CIA has at its disposal an enormous cyberespionage arsenal.
The documents detail how cyberweapons were prepared to make use of “zero day” attacks (which target vulnerabilities that haven’t been made public yet, and can therefore be easily exploited). These cyberweapons would be used to compromise the security of devices using iOS, Android, Windows, and macOS operating systems.
Something of considerable note from these leaks is that the CIA would not have to break the encryption protecting apps such as WhatsApp, Signal, or Telegram. By gaining access to the smartphone’s OS using malicious software, they are able to access all the information stored on it.
According to the documents, which have been deemed authentic by several security experts, the CIA even made use of security holes in other smart devices. The US agency worked with their British counterparts to develop a cyberespionage tool called Weeping Angel to use smart TVs as hidden microphones. So, how did the affected companies react? And what can the rest of us learn from this leak?
Google and Apple’s Reaction
Apple reacted to the leak with a lengthy statement, pointing out that the security holes that the CIA used had already been patched in the latest version of iOS. The company also ensured that is would continue working to resolve any vulnerability and encouraged users to download the latest version of its OS.
Google claimed that Android and Chrome’s updates had already solved the problems, while Microsoft and Samsung have said they are investigating the issue. Although WikiLeaks hasn’t released technical aspects of the malware in question, they have announced their intention to share them with manufacturers.
For their part, the CIA is keeping pretty quiet about the whole thing. They’ve limited themselves to a “no comment” about the leaked documents and have stated that the revelations put US citizens in danger. It’s the first major challenge for CIA director Mike Pompeo, recently appointed by President Trump.
Keeping in mind that US intelligence is able to detect vulnerabilities even in the tech giants themselves and even develop cyberweapons to take advantage of them, what can a company learn from these leaks?
One of the first lessons to learn is that the security on our devices leaves much to be desired. Another, to avoid exposing our companies to zero day attacks, a perimeter-based security solution isn’t going to cut it. The only way to combat zero-day attacks: update, update, update, and spring for an advanced cybersecurity solution.
Panda Security’s Adaptive Defense 360, to name but one example, is not too shabby when it comes to top of the line security. It allows continuous monitoring through surveillance and logs of all activity at every workstation and detects advanced threats in real time. It stops untrusted software the moment it attempts to run, responds in a matter of seconds, and recovers instantaneously. It’s nice to know that your as-yet-unknown security holes (and there is always one or two lurking beneath the radar, even at companies like Google and Apple) won’t be much use to potential intruders.
The post In the Wake of the CIA WikiLeaks Case, Some Tips on Corporate Cybersecurity appeared first on Panda Security Mediacenter.
Avast Software B.V. completes squeeze-out process of minority shareholders of AVG Technologies B.V.
Prague, Czech Republic / Amsterdam, The Netherlands, March 16, 2017 – Today, Avast Software B.V. (“Avast“) enforced the judgement of the Enterprise Chamber of the Court of Appeal of Amsterdam, the Netherlands (the “Enterprise Court“) of 14 February 2017.
As announced on February 15, 2017, The Enterprise Court ordered all minority shareholders of AVG Technologies B.V. (“AVG“) to transfer their shares to Avast in exchange for a payment of EUR 22.84 per share in cash, increased by statutory interest to be calculated over the period from October 31, 2016 until the date of transfer of the shares.
Up until March 15, 2017, shareholders of AVG could voluntarily adhere to the judgment of the Enterprise Court by transferring their shares in AVG to Avast. On March 16, 2017, Avast enforced the judgement of the Enterprise Court by transferring the aggregate squeeze-out price of the remaining outstanding shares in AVG to the Consignment Fund of the Ministry of Finance of the Netherlands (the “Consignment Fund“).
As a result of the consignment, all remaining outstanding shares of AVG that were not yet held by Avast were transferred to Avast by operation of law as per 16 March 2017. The former holders of these shares should reach out to the Consignment Fund for payment of the squeeze-out price, which amounts to EUR 23.01 per share in AVG including statutory interest as per 16 March 2017.
Requests for payment of the squeeze-out price and questions with regard to claiming the squeeze-out price should be directed to the Consignment Fund. The contact details of the Consignment Fund are included below.
Ministry of Finance
Attn. The Consignment Fund
PO Box 20201
2500 EE THE HAGUE
THE NETHERLANDS
E-mail: [email protected]
About Avast
Avast (www.avast.com), the global leader in digital security products for businesses and consumers, protects over 400 million people online. Avast offers products under the Avast and AVG brands that protect people from threats on the internet and the evolving IoT threat landscape. The company’s threat detection network is among the most advanced in the world, using machine learning and artificial intelligence technologies to detect and stop threats in real time. Avast digital security products for Mobile, PC or Mac are top-ranked and certified by VB100, AV-Comparatives, AV-Test, OPSWAT, ICSA Labs, West Coast Labs and others. Avast is backed by leading global private equity firms CVC Capital Partners and Summit Partners.
Media Contact:
Zoe Kine, Avast PR Director
E-mail: [email protected]
www.avast.com
![]()
![]()
Avast at Machine Learning Prague 2017
Machines can learn incredibly fast. Faster than us, actually. They are already changing our world, our business, and our life. Avast, as a part of the artificial intelligence revolution, is proud to be a gold partner of Machine Learning Prague 2017, held from April 21st to April 23rd in Prague, Czech Republic.
![]()
What is beta testing?

Installing a near final, potentially buggy and unstable application on a real system with the possibility to provide feedback to developers directly. That’s beta testing. Well, it isn’t as easy as it sounds but if you are trying to summarize beta testing in one sentence you might end up with something like that. So … what […]
The post What is beta testing? appeared first on Avira Blog.
The Dark Side of Shopping Apps

Are shopping apps safe?
As we shoppers get better at identifying scams, cybercriminals are having to create new ways to try and steal our money. Effective PC security tools like Panda Safe Web can identify and block fake websites before scammers have a chance to trick us.
But increasingly we are shopping from our smartphones and tablets instead of desktop PCs. Realising this, cybercriminals have begun to develop a range of mobile-focused attacks designed to steal personal data and money.
So when you do fire up a shopping app on your mobile phone, how do you know it can be trusted?
Here are some tips.
1. Only download apps from official sources
Both the Apple App Store and Google Play Store use a very strict approval process to protect their customers. Whenever an app is submitted to one of these official stores, it is checked to ensure that it is not infected with malware, and doesn’t take personal data without your permission.
For iPhone users this is great news – every app they can download has been checked to ensure it is safe. Especially as Apple devices cannot install apps from anywhere else but the App Store.
Android users on the other hand are not limited to the Google Play store – they can download and install apps from virtually anywhere. Although this is much more flexible, not all app stores or websites apply the same security checks. Cybercriminals exploit this weakness by tricking Android users into downloading infected apps from email attachments or fake app stores. Once installed, this malware allows scammers to steal credit card details, or to encrypt your files so you cannot access them without paying a ransom.
When it comes to downloading shopping apps you must ensure they come from the official app store – otherwise you could be inviting cybercriminals onto your phone.
2. Install a mobile Security tool
You wouldn’t dream of leaving your PC unprotected against malware – so why ignore your mobile phone? Just this week mobile hacking hit the headlines again as government officials tried to highlight the risks.
It is absolutely essential that Android owners install a mobile security tool to protect themselves against fake shopping apps. Panda Mobile Security scans installed apps to detect malware and alert you to potential problems before your data can be stolen.
Using Panda Mobile Security you can also control what each app does, preventing them from accessing your data, or from triggering your camera or microphone. You can also prevent apps – good or bad – from uploading your information to the cloud, adding an additional layer of protection.
Stay alert
As well as installing security software on your mobile phone, you need to treat apps, web downloads and email attachments with caution. In the same way that you don’t open attachments from people you don’t know on your PC, you shouldn’t download unknown apps from untrusted websites.
As our phones become an important part of our shopping habits, criminals will devote more of their time and effort to attacking them. So it pays to protect yourself now before they attack you.
The post The Dark Side of Shopping Apps appeared first on Panda Security Mediacenter.
US charges Russian FSB officials in connection with massive Yahoo security breach
The United States has charged four men, including two officials of Russia’s FSB intelligence agency, in connection with a hacking attack against Yahoo that saw the details of 500 million users stolen and the use of forged cookies to break into accounts.
The post US charges Russian FSB officials in connection with massive Yahoo security breach appeared first on WeLiveSecurity
![]()
New Kaspersky Security for Virtualization Agentless Reinforces Security Capabilities of VMware NSX – VMBlog
New Kaspersky Security for Virtualization Agentless Reinforces Security Capabilities of VMware NSX – VMBlog