In this week’s Tales From Ransomware, we take a look at a ransomware that isn’t really ransomware. Nor even malware. But it can hijack your server anyway.
A few days ago we saw a typical Remote Desktop Protocol (RDP) attack, which lead us to believe that it was a similar attack to the one we told you about a few months ago which cybercriminals are using to infect devices with ransomware. But we were very wrong.
First of all because instead of encrypting data, it locks the desktop with a password that the victim doesn’t know. Secondly, it does not demand a ransom (!) in exchange for the credential, but rather seeks to keep the device locked for as long as possible so that it can be used for bitcoin mining for as long as possible. And thirdly, it doesn’t use malware as such.
Once they’ve gained access to your machine by brute force (this particular server was fielding 900 attempts daily) the attacker copies a file called BySH01.zip. This in turn contains:
- BySH01.exe (executable through AutoIt)
- 7za.exe (goodware, the well-known free tool 7zip)
- tcping.exe (goodware, a tool for performing TCP pings)
- MW_C.7z (a compressed password-protected file), which contains:
- An application –goodware for bitcoin mining
- An application –goodware for blocking the Windows desktop
The attacker runs the BySH01.exe file, and the following interface appears:
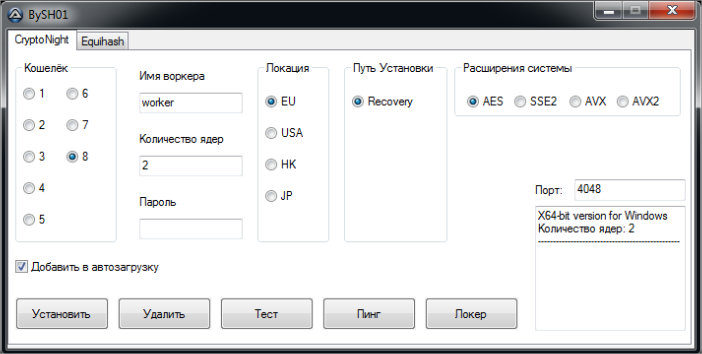
With the help of our colleagues at Panda Russia, those of us who don’t know Russian can get an approximate idea of what its telling us with the above word list.
Basically, the bitcoin mining application uses this interface to configure how many cores to use, what extension of processor instructions to use, what “wallet” to send the bitcoins to, etc. Once the desired configuration is selected, the attacker clicks on Установить to install and run the bitcoins mining application. The application is called CryptoNight, which was designed for mining bitcoins using CPUs.
Then they click on Локер, which installs and runs the desktop lock application. It is the commercial application Desktop Lock Express 2, modified only so that the information shown in the properties of the file are the same as those of the system file svchost.exe. Finally it clears all the files used in the attack except CryptoNight and Desktop Lock Express 2.
We detected and blocked several attacks in different countries. Examples such as this one show how, once again, cybercriminals take advantage of weak passwords that can be guessed using the brute force method over a given period of time. Malware is no longer necessary to gain access to the system, so it’s up to you to use a robust password that will keep out unwanted visitors.
Tips for the System Admin
In addition to using a solution like Adaptive Defense, which detects and prevents this kind of attack, a couple of tidbits of advice for all administrators who have to have an open RDP:
- Configure it to use a non-standard port. What 99.99% of cybercriminals do is track all Internet on TCP and UDP ports 3389. They might bother to track others, but they do not have to, since most do not change these ports. Those who do change ports do so because they are careful about security, which probably means that their credentials are already complex enough to not be gotten by brute force within any reasonable amount of time.
- Monitor failed RDP connection attempts. Brute force attacks can easily be identified in this way, since they use automated systems and can be seen making a new attempt every few seconds.
The post It Isn’t Ransomware, But It Will Take Over Your Server Anyway appeared first on Panda Security Mediacenter.