In the quest for social validation people are playing with the truth and whitewashing their lives.
Category Archives: Antivirus Vendors
Antivirus Vendors
Brand-new AVG PC TuneUp speeds up, cleans up and now updates critical software
Users have been asking for it for ages and now it’s here. With our new 2017 release of the AVG PC TuneUp ,we’re pleased to introduce Automatic Software Updater!
A product which keeps users’ PCs up to date with their critical software for improved experience and protection from vulnerabilities.
AVG PC TuneUp cleans, speeds up, and improves battery life of all Windows®-based PCs and laptops and it’s based on 20 years of solid engineering and experience of getting the best out of PCs. If you are a fan, we’ll show you what’s new for 2017 and give newcomers a rundown of what makes AVG PC TuneUp an essential part of everyone’s PC.
The Big One For 2017: Automatic Software Updater
For this release, we moved beyond speeding and cleaning and looked at some of the core reasons for bugs, crashes and security issues – UPDATES! Since keeping up with updates for all your programs is tedious, it’s no wonder that our research across 116 million users found that 52% of programs are out-of-date on people’s PCs.
That’s why we created our all new Automatic Software Updater, which checks and updates the most popular applications people run on PCs to fix vulnerabilities, solve problems and even add new features to programs like Skype, Chrome or Java.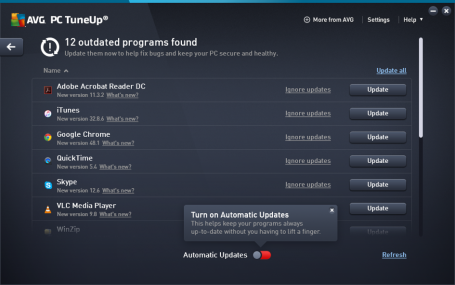
Here’s what you get with our new Automatic Software Updater
- Peace of mind: no more dealing with constantly checking for updates manually or annoying update nags
- Support for the most used applications: including Skype, Adobe Reader, Flash or Chrome
- Works fully automatically: no need to bother with painful installers, ad-ware or reboots
- Informs you about what’s new in your favorite programs
- Manage Software Updates: go the hands-on way if you choose and manually check, download, update and manage all your software updates, all on one screen
- Notifications: for critical software updates
And we’re adding more programs over time, all the time
Which programs do we support?
We’ve made sure that we support the most popular and critical applications, such as:
- Browsers: Mozilla Firefox, Opera, Safari, Google Chrome and Internet Explorer
- Tools and Programs: 7-Zip Filemanager, WinRAR Archiver, WinZip 9
- Frameworks and technologies: Flash Player Plug In, Adobe AIR, Adobe Shockwave, Java Runtime Environment 6, 7 & 8, VLC Media Player, GOM Media Player, iTunes, Nero MediaHome, DivX, Adobe Reader, FoxIt Reader
and more!
Where can I find Automatic Software Updater in TuneUp?
If a program is out of date you’ll find it under the Fix Problems category or you will get a notification on your desktop. Once clicked, you’ll see an entry for a list of outdated programs that you can update manually – or flip a switch and have it be done fully automatically.
IMPROVED: Sleep Mode Tackles Slow PCs
Is your PC sluggish? Tired of battling it to get things done? The new release of AVG PC TuneUp puts speed, battery and network draining programs to sleep to give you that extra performance boost.
The new version of AVG TuneUp comes with a significantly improved Sleep Mode, previously known as Program Deactivator, which stops inactive programs from draining your PC, giving you back that fresh out-of-the-box performance.
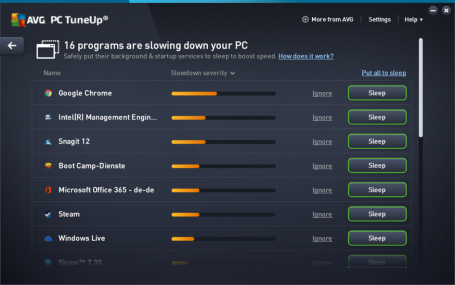
Sleep Mode speeds up your PC by stopping programs that you rarely use from quietly draining processor power, such as instant messaging tools, screen capture utilities or driver control panels. And you don’t need to worry about losing access to the programs you love as the Automatic Start-Stop Mode allows any programs that you have deactivated to be reactivated in a single click. When you have finished using them, they are automatically deactivated again.
In this new version for 2017, we have also combined our Startup Manager feature – which detects items that automatically run when you turn your computer on – with Sleep Mode. Sleep Mode now shows a single list of all the applications that are draining your PC’s performance, giving you smarter detection across even more programs.
IMPROVED: Deeper Than Ever Cleaning
Our new Disk Cleaner include significant new and improved cleaning definitions to help remove the wasteful files of 40 additional programs.
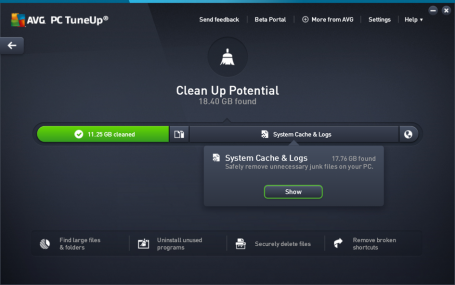
We’re also removing 60 types of browser traces from the latest releases of Chrome, Firefox, IE and now Microsoft Edge.
The Top 10 Features & Benefits from PC TuneUp
In a nutshell, AVG PC TuneUp keeps your computer running at peak performance. Get more speed, less crashing, longer battery life and more disk space, whether you choose automatic maintenance or want to take a more hands on approach.
Live Optimization helps keep your PC at top speed. Live Optimization works silently in the background, constantly prioritizing all the applications that are running to increase loading speed and computer performance. For those who want that extra bit of power, Turbo Mode turns off over 70 processes with just one click. In addition to the existing Economy Mode, there’s Flight Mode: both features significantly prolong battery life, which is invaluable when you’re on the go.
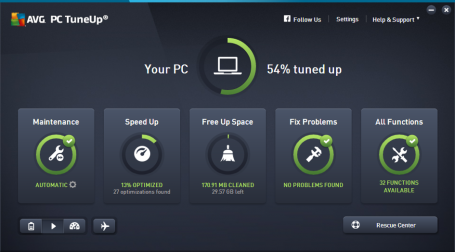
And you can easily free up more disk space, thanks to New Disk, Duplicate, and Browser Cleaners. Out of 40 features, these are our top favorite:
- ENHANCED! Program Deactivator: puts resource-draining programs and startup items to sleep and makes your PC feel like new again
- Live Optimization: constantly prioritizes all programs to deliver optimum performance
- NEW! Automatic Software Updater: regularly checks & updates dozens of the most important applications
- Registry Cleaner: cleans up your registry and helps you solve problems
- Duplicate Finder: the new automatic selection helps you get rid of duplicate even faster than before
- ENHANCED! Disk Cleaner: now wipes junk to free up disk space from 220+ applications, such as the gaming platforms Steam® and popular programs like VMware
- Flight Mode: one click turns off Wi-Fi® and Bluetooth® for even longer battery life
- Automatic Maintenance: cleans up and fixes your PC every few days, completely silently in the background
- Defrag: over the years your hard disk may have become cluttered, slowing down read & write access. With AVG Disk Defrag you’ll bring order into chaos and speed up your disk
- Uninstall Manager: helps you identify and get rid of long-forgotten programs that you installed over the years
AVG PC TuneUp is available standalone or as part of our AVG TuneUp – Unlimited package for $49,49/year, which can be activated on an unlimited amount of devices. It also includes AVG Cleaner for Android PRO and AVG Cleaner for Mac. You can download the 30 day trial here.
![]()
![]()
Beware new WhatsApp scam offering “free internet without Wi-Fiâ€
The number of scams spreading through the messaging app WhatsApp keeps on increasing, reports Lucas Paus. And there’s already a new one in 2017.
The post Beware new WhatsApp scam offering “free internet without Wi-Fi” appeared first on WeLiveSecurity
![]()
“Eye Pyramidâ€, the Cyber-Espionage Malware that has Italy Reeling
This Tuesday, the Italian state police dismantled a cyber-espionage ring spearheaded by a brother and sister that sought to exert control over public institutions and administrations, professional studios, employers, and politicians. The network was able to access confidential information by installing a virus on victims’ computers, stealing information sensitive to financial institutions and state security.
Among those affected are former Prime Ministers Matteo Renzi and Mario Monti, as well as the president of the Central European Bank, Mario Draghi, as well as other individuals in possession of confidential information. Mayors, cardinals, regional presidents, economists, employers, and law enforcement officials are also on the list.
How Eye Pyramid Works
The investigation has been dubbed “Eye Pyramid”, after the particularly invasive malware that the suspects used to infiltrate the systems of the people they spied on.
These intrusions appear to have first surfaced in 2012, reaching 18,327 users with the theft of 1,793 passwords using a keylogger. This comes out to be around 87GB data. The method of infiltration was simple given the serious nature of the attack: the cybercriminal sent an email, the recipient opened it, and upon opening the email a software was installed on the device, giving access to its secret files.
Older versions of the malware with unknown origins (although possibly linked to Sauron) were probably used in 2008, 2010, 2011, and 2014 in various spear phishing campaigns.
In a hyperconnected world, with mounting tension between cybersecurity and cyber-espionage — we’ve recently seen a crossfire of accusations exchanged between major powers like the US, China, and Russia — these attacks appear to have special relevance to state security and the dangers it faces in the cyber world.
Advanced Persistent Threat, or How to Avoid a Cybernetic Nightmare
This attack, unprecedented in Italy, will continue to be under investigation and, according to authorities, may end up revealing connections to other cyberattacks carried out in other countries.
Protecting your confidential and sensitive data from cybercriminal networks and attacks such as ATPs is crucial in combatting the growing professionalization of cybercrime.
Advanced threats are no longer an issue when you’ve got an advanced cybersecurity solution like Adaptive Defense 360, the platform that connects contextual intelligence with defense operations to stay ahead of malicious behaviors and data theft. Protection systems are triggered and jump into action before the malware even has a chance to run.
Thwarting potential threats before they become a real problem is the only way to rest easy knowing that your information has not ended up falling into the wrong hands.
The post “Eye Pyramid”, the Cyber-Espionage Malware that has Italy Reeling appeared first on Panda Security Mediacenter.
How to share your internet mobile connection safely
Are you aware of the dangers of sharing your internet mobile connection?
Most smartphones have a built-in function that allows you to share the mobile internet connection with other people nearby. Acting very much like a traditional WiFi hotspot, mobile internet connection sharing turns your phone into a hub – authorised devices can then connect to your phone and share the data connection.
This “mobile hotspot” feature is particularly useful when your friends cannot get a reliable connection to their mobile network. Or when you need to get online with your laptop really quickly while “out and about”.
But just as you (should) secure your home network to prevent abuse and deter hackers, you need to take a few extra steps to keep yourself safe. If someone does manage to hack your mobile hotspot they may be able to steal the data stored on your phone – or run up a large phone bill simply by using up your data allowance.
Here are our top tips for boosting your security.
1. Use a ‘secure’ passphrase
When someone tries to connect to your mobile hotspot, they will be prompted to enter a password – which is exactly the same procedure as connecting to any other secure WiFi network. This password needs to be “complex” to prevent hackers from guessing it.
Android and iOS both generate long, complicated passwords by default, but it is worth checking your own settings to confirm. You must resist the urge to replace the password with something simple though – if you make it too easy for your friends to get connected, you also make it easier for hackers to jump online.
The Apple iPhone mobile hotspot requires a password at least eight characters long, but you should consider choosing something even longer that uses a combination of upper and lower case letters, mixed with numbers and punctuation marks (like ! Or ?) to deter dictionary attacks from “guessing” the password. The same password tip applies to smartphones running Android.
2. Disable by default
You can toggle the mobile hotspot function on and off – so it’s only available when you actually need it. You should always ensure the hotspot is toggled off when not in use to reduce the risk of unauthorised connections.
A few extra taps on the screen to enable the hotspot may be annoying – but nowhere near as frustrating as an unexpectedly high phone bill run up by people abusing your mobile data connection.
3. Keep an eye on your screen
Both Android and iOS provide helpful on-screen indicators to show when your mobile hotspot is switched on, and how many devices are currently connected. You should keep an eye on that indicator – it will help you spot when someone is connecting without your permission.
If you do detect an unauthorised connection, turn the hotspot off, and change the password immediately. This will help to prevent your connection being hijacked again.
Using these three tips, you can greatly reduce the risk of becoming another mobile fraud victim. For more help securing your mobile device, download a free trial of Panda Mobile Security.
The post How to share your internet mobile connection safely appeared first on Panda Security Mediacenter.
Your free wifi map for airports

At local airports there might be local WiFi available. But is it free? And what’s the password?
The post Your free wifi map for airports appeared first on Avira Blog.
CES: IoT security comes of age
For years, IoT security seemed like solving a problem that didn’t exist. Not anymore says ESET’s Cameron Camp, who was at this year’s CES.
The post CES: IoT security comes of age appeared first on WeLiveSecurity
![]()
Amazon Echo and the Alexa dollhouses: Security tips and takeaways
Tips on securing the Alexa service on Amazon Echo devices, notably voice purchasing, a topic brought into focus by the recent “San Diego dollhouse TV story”.
The post Amazon Echo and the Alexa dollhouses: Security tips and takeaways appeared first on WeLiveSecurity
![]()
Cybercriminals ‘should be punished with Wi-Fi jammers’
A senior UK police officer has suggested that offenders of cybercrime should be penalized by being made to wear Wi-Fi jammers rather than being sent to prison.
The post Cybercriminals ‘should be punished with Wi-Fi jammers’ appeared first on WeLiveSecurity
![]()
Security scare over hackable heart implants
A US government probe into claims that certain heart implants are vulnerable to hacking attacks, has resulted in emergency security patches being issued for devices that cardiac patients have in their homes.
The post Security scare over hackable heart implants appeared first on WeLiveSecurity
![]()