Halloween is one of the most celebrated holidays, and cybercriminals always want to be part of it.
As we get closer to Halloween, hackers take advantage of the most popular Hollywood titles to launch so-called BlackHat SEO attacks, i.e. false Google and other search engine results with keywords related to popular topics of the time to trick users into clicking on their links.
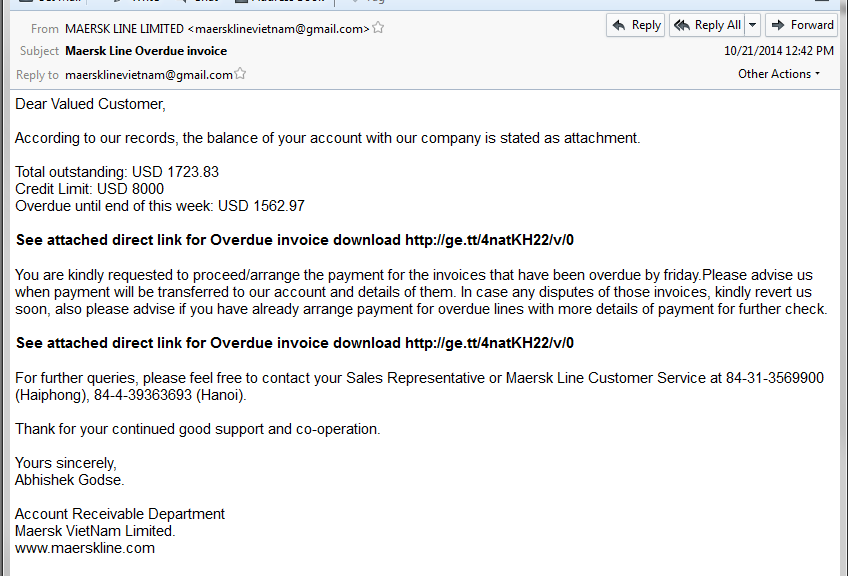
Another popular form for hackers that we see distributed during these days is spam. They use typical Halloween characters to trick users and bring them to where they want. This way, in addition to obtaining personal data and revenue through clicks achieved, they redirect the user to other websites selling fraudulent or prohibited products.
As always, education, common sense and being forewarned is our best advice. We must be aware that they will try to deceive us with practical jokes, introducing real malware to our equipment which will lead us to a lot of headaches.
10 Tips to Avoid Viruses on Halloween
- Do not open emails or messages received from social networks that can come from unknown sources
- Do not click a link you get by email, unless they’re from reliable sources. It is suggested to type the URL directly into the browser bar. This rule applies to messages received through any email client, such as those that come via Facebook , Twitter, other social networking, instant messaging programs, etc.
- If you click on one of these links, it is important to look at the landing page. If you don’t recognize it, close your browser
- Do not download attachments that come from unknown sources. During this time we must pay special attention to the files that come with issues or Halloween-related names
- If you do not see anything strange on the page, but it requests a download, be wary and do not accept.
- If, however, you begin to download and install any type of executable file and the PC starts to launch messages, there is probably a copy of malware
- Do not buy online from sites that do not have a solid reputation, and much less on pages where transactions are not made ​​securely. To verify that a page is secure, look for the security certificate that is represented by a small yellow lock at the bar of the browser or in the lower right corner
- Do not use shared computers to perform transactions that require you to enter passwords or personal data
- Make sure you have an installed and updated antivirus
- Keep up with all the security newsÂ
What about you? Have you ever been infect on Halloween?
The post 10 Tips to Avoid Viruses on Halloween appeared first on MediaCenter Panda Security.