Security-first, managed IT services portfolio from AVG Business by Avast provides security protection for KYOCERA Document Solutions Canada’s printer and multifunctional products customers.
MSPWorld, New Orleans, March 27, 2017 – Avast, the leader in digital security products for consumers and businesses, today announced a partnership with KYOCERA Document Solutions Canada, a top manufacturer of printers and multifunctional products (MFPs) in North America, to deliver customized endpoint security solutions and managed IT services to customers throughout Canada. The three-year deal, delivered through the AVG Business by Avast product portfolio, is designed as a proactive, immediate defense against cybercrime.
Through the KYOCERA Document Solutions Canada-Avast partnership, KYOCERA Document Solutions Canada customers also gain the security advantages of Avast’s cloud-based, machine learning threat detection network, among the largest and most advanced in the world that uses next generation technology to detect and block the latest cybersecurity attacks, including malware, phishing, ransomware, breaches in privacy, and more.
A certified Avast Elite Channel Partner, KYOCERA Document Solutions Canada can now customize AVG Business by Avast solutions to meet security needs across its key customer segments – education, government, healthcare and more. The solution set includes a full IT services portfolio with advanced endpoint security services and help desk and technical support. The company also gains access to specialized cloud and remote monitoring and management solutions to build, standardize and automate a managed security program for its extensive dealer network. Avast is providing technical training and support from its team of dedicated sales engineers, counsel and guidance on go-to-market strategy, and access to marketing resources.
Michel Naud, Director of Direct Operations for KYOCERA Document Solutions Canada, said “With the rapid growth of cyber threats such as ransomware, security has become a top priority for our customers. By partnering with Avast, not only can we provide immediate and effective security protection, we now have the technology, services and resources to build and scale the IT services side of our business. This is a clear market advantage for KYOCERA Document Solutions Canada.”
“We welcome KYOCERA Document Solutions Canada as a partner and look forward to helping them deliver tailored security and managed IT services for customers with any type of security need,” said Kevin Chapman, SVP and general manager of Avast’s SMB Business. “Our unique AVG Business by Avast solutions provide advanced security protection for end customers which simplify the delivery and automate the management of security services for our channel partners. Coupled with our comprehensive channel partner program, we’re ensuring our partners can go to market effectively and build a scalable program that fosters high recurring revenue and great margins.”
The AVG Business by Avast portfolio provides solutions to secure, simplify and optimize the IT experience for small and medium-sized businesses worldwide. AVG Business by Avast brings a 25 year-history in security and is the only remote monitoring and management solution provider with its own native security engine. This unique and strong combination of security and managed services experience provides end-customers and channel partners ‘trusted network’ security with solutions that extend across world-class endpoint protection to complete network management.
AVG Business by Avast is dedicated to the channel and has a comprehensive partner program in place to ensure partners can successfully position and sell the products, effectively secure SMBs, and enable profitable channel growth.
To learn more about AVG Business by Avast solutions, stop by Avast’s booth #33 at MSPWorld 2017 or attend the Monday speaking session on ‘Creating a Competitive MSP Pricing Model.’
About Avast
Avast (www.avast.com), the global leader in digital security products for businesses and consumers, protects over 400 million people online. Avast offers products under the Avast and AVG brands that protect people from threats on the internet and the evolving IoT threat landscape. The company’s threat detection network is among the most advanced in the world, using machine learning and artificial intelligence technologies to detect and stop threats in real time. Avast digital security products for Mobile, PC or Mac are top-ranked and certified by VB100, AV-Comparatives, AV-Test, OPSWAT, ICSA Labs, West Coast Labs and others. Avast is backed by leading global private equity firms CVC Capital Partners and Summit Partners.
About KYOCERA Document Solutions Canada, Ltd.
KYOCERA Document Solutions Canada, Ltd. (www.kyoceradocumentsolutions.ca), with headquarters in Mississauga, Ontario and regional offices / distribution networks across Canada, is a leading provider of computer-connectable document imaging and document management systems, including network-ready digital MFPs/printers, laser printers, colour MFPs/printers, laser facsimiles, and multifunctional and wide format imaging solutions. In North America, KYOCERA Document Solutions has earned numerous honours for its products’ high performance, reliability and cost efficiency. KYOCERA Document Solutions Canada, Ltd. is a subsidiary of KYOCERA Document Solutions Inc., a core company of KYOCERA Corporation, a world leading developer and manufacturer of advanced ceramics and associated products, including telecommunications equipment, semiconductor packages and electronic components. KYOCERA Corporation’s consolidated net revenues exceeded $US13.32 billion for the fiscal year ending on March 31, 2016.
Avast Media Contact:
Zoe Kine, Avast PR Director
E-mail: [email protected]
www.avast.com
KYOCERA Document Solutions Canada Media Contact:
Tony Swierkot
E-mail: [email protected]
http://www.kyoceradocumentsolutions.ca



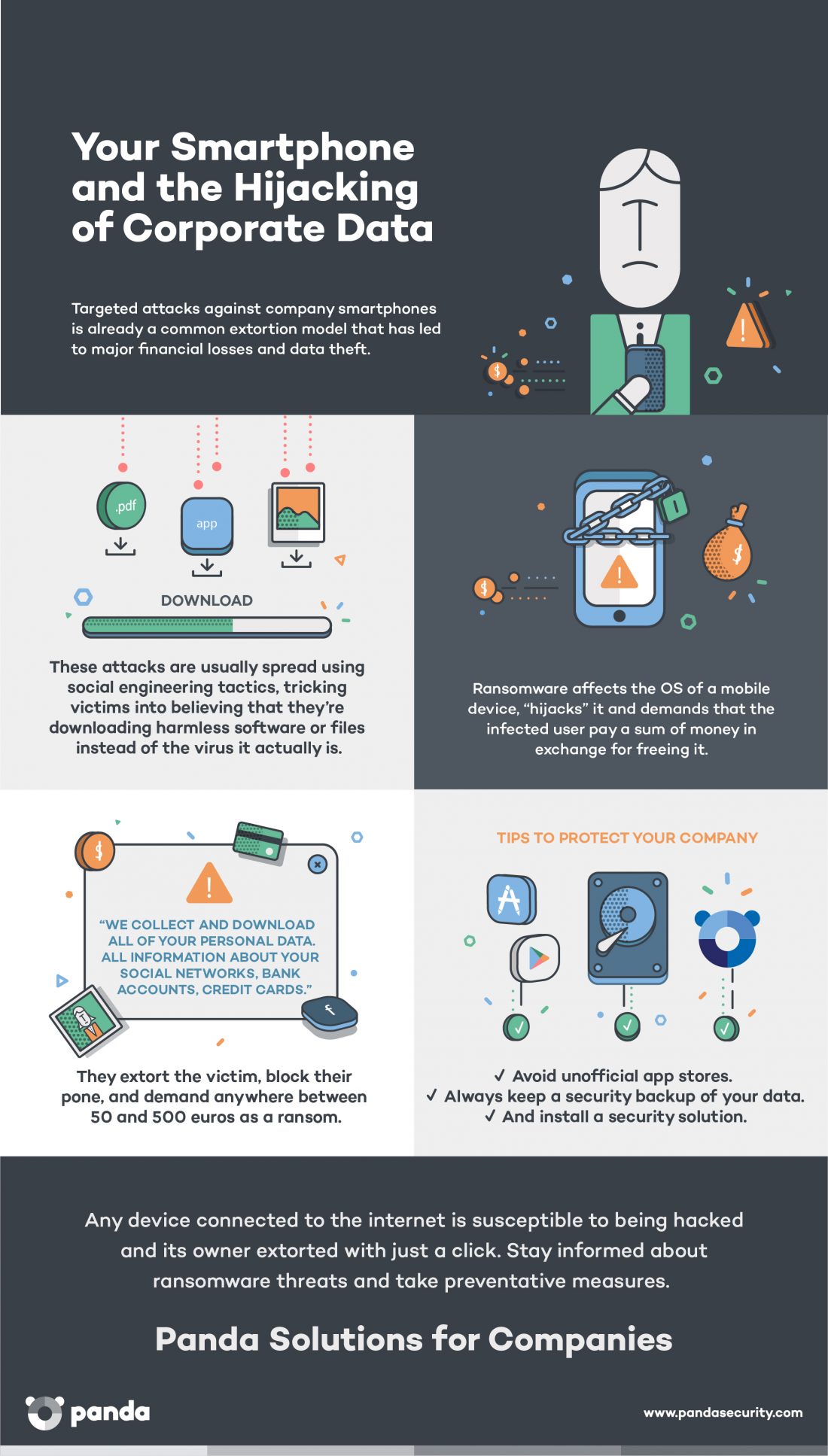 It is now the main threat to mobile devices, until now considered to be relatively virus-free compared with their PC counterparts. Recently, a new ransomware was discovered that goes by the name of Charger, which copies all the data from your agenda, text messages, etc., and seeks admin permissions from the devices owner. If the unwary user accepts the request, the malicious code begins its attack. A message warns the owner that their device has been blocked and their stolen personal data will be sold on the dark web unless they proceed to pay a ransom.
It is now the main threat to mobile devices, until now considered to be relatively virus-free compared with their PC counterparts. Recently, a new ransomware was discovered that goes by the name of Charger, which copies all the data from your agenda, text messages, etc., and seeks admin permissions from the devices owner. If the unwary user accepts the request, the malicious code begins its attack. A message warns the owner that their device has been blocked and their stolen personal data will be sold on the dark web unless they proceed to pay a ransom.


