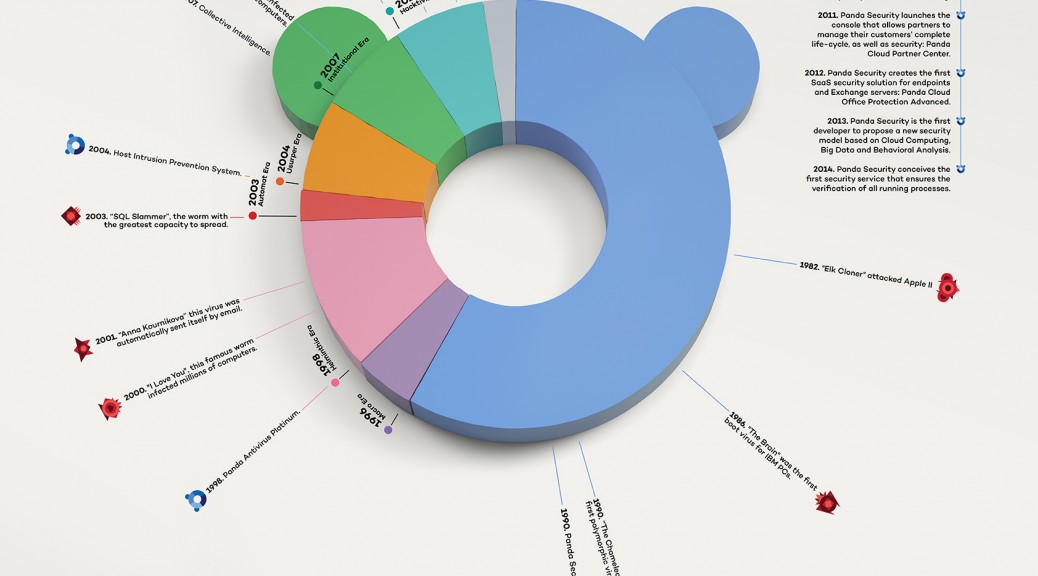
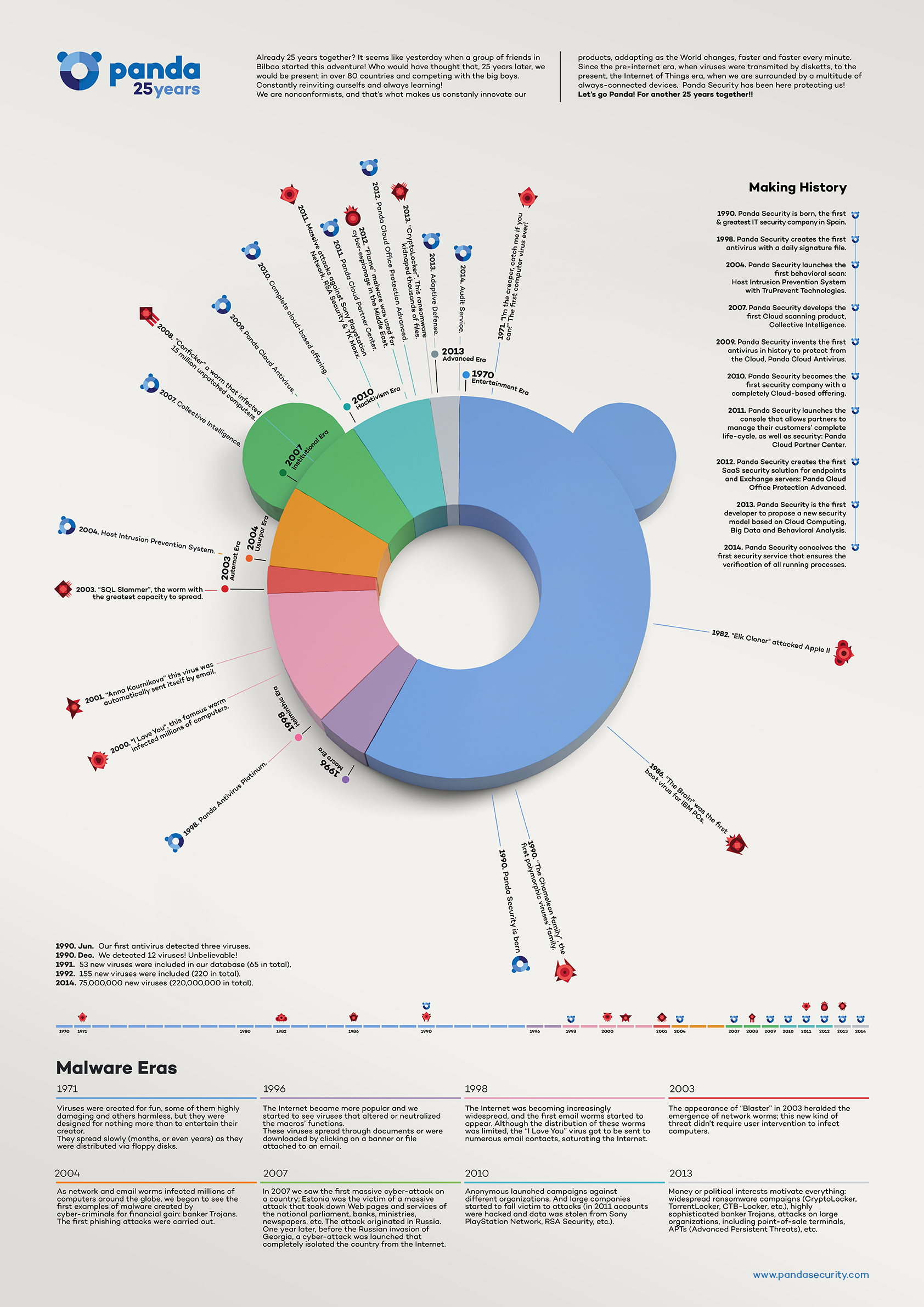
Already 25 years together? It seems like yesterday when a group of friends in Bilbao started this adventure! Who would have thought that, 25 years later, we would be present in over 80 countries and competing with the big boys. Constantly reinviting ourselfs and always learning! We are nonconformists, and that’s what makes us constanly innovate our products, addapting as the World changes, faster and faster every minute. Since the pre-internet era, when viruses were transmited by disketts, to the present, the Internet of Things era, when we are surrounded by a multitude of always-connected devices. Panda Security has been here protecting us!
Let’s go Panda! For another 25 years together!
Our technology
- 1998. We lunch the 1st antivirus with a daily signature file.
- 2004. We launch the 1st behavioral scan.
- 2007. We develop the 1st Cloud scanning product.
- 2009. We launch the 1st antivirus in history to protect from the Cloud.
- 2010. We become the 1stsecurity company with a completely Cloud-based offering.
- 2011. We launch a console for partners to manage their customers’ complete life-cycle & security.
- 2012. We launch the 1st SaaS security solution for endpoints & Exchange servers.
- 2013. We are the 1st developer to propose a disruptive security model based on Cloud Computing, Big Data and Behavioral Analysis.
- 2014. We launch the 1st security service that ensures all running processes.
Malware Eras
- Entertainment Era: From 1971
Viruses were created for fun, some of them highly damaging and others harmless, but they were designed for nothing more than to entertain their creator. They spread slowly (months, or even years) as they were distributed via floppy disks.
- Macro Era: From 1996
The Internet became more popular and we started to see viruses that altered or neutralized the macros’ functions. These viruses spread through documents or were downloaded by clicking on a banner or file attached to an email.
- Helminthic Era: From the end of 1998
The Internet was becoming increasingly widespread, and the first email worms started to appear. Although the distribution of these worms was limited, the “I Love You” virus got to be sent to numerous email contacts, saturating the Internet.
- Automat Era: From 2003
The appearance of “Blaster” in 2003 heralded the emergence of network worms; this new kind of threat didn’t require user intervention to infect computers.
- Usurper Era: From 2004
As network and email worms infected millions of computers around the globe, we began to see the first examples of malware created by cyber-criminals for financial gain: banker Trojans. The first phishing attacks were carried out.
- Institutional Era: From 2007
In 2007 we saw the first massive cyber-attack on a country; Estonia was the victim of a massive attack that took down Web pages and services of the national parliament, banks, ministries, newspapers, etc. The attack originated in Russia.
One year later, before the Russian invasion of Georgia, a cyber-attack was launched that completely isolated the country from the Internet.
- Hacktivism Era: From 2010
Anonymous launched campaigns against different organizations. And large companies started to fall victim to attacks (in 2011 accounts were hacked and data was stolen from Sony PlayStation Network, RSA Security, etc.).
- Advanced Era: From 2013
Money or political interests motivate everything: widespread ransomware campaigns (CryptoLocker, TorrentLocker, CTB-Locker, etc.), highly sophisticated banker Trojans, attacks on large organizations, including point-of-sale terminals, APTs (Advanced Persistent Threats), etc.
Want to share this infographic? Here is the code!
The post Panda Security: 25 years fighting against malware – Infographic appeared first on MediaCenter Panda Security.

 Prepare yourself before disaster strikes
Prepare yourself before disaster strikes

 What can I do to protect my small business?
What can I do to protect my small business?