Ten years ago we started celebrating World Information Society Day on May 17th. On this day, we honor the Information Society and the importance of telecommunications by raising awareness about the Internet and its possibilities, as well as other information and communication technologies (ICT). Luis Corrons, technical director of PandaLabs, pointed out some of the Internet’s capabilities for society and business, and gave us some information on how we can reduce digital divide.
Ten years ago we started celebrating World Information Society Day on May 17th. On this day, we honor the Information Society and the importance of telecommunications by raising awareness about the Internet and its possibilities, as well as other information and communication technologies (ICT). Luis Corrons, technical director of PandaLabs, pointed out some of the Internet’s capabilities for society and business, and gave us some information on how we can reduce digital divide.
Panda Security– The majority of traditional media outlets are already on the Internet, what advice do you have for them regarding computer security?
Luis Corrons– Internet is a communication tool. Online media sites do not differ much from the rest of other websites, so really, the security measures are similar to those of any website belonging to a company in another sector. What they need are reliable systems that provide availability and are fast, but also take safety measures to protect them against possible server attacks. Also, businesses must be extra careful with personal information belonging to their users and/or subscribers.
PS– Social Networks are the main catalyst for change when it comes to the way we communicate, also affecting the personal world of an individual. Are privacy and cyber-security connected?
LC– No, privacy and cyber-security go hand in hand. Social networks and privacy are connected, because they encourage that we abandon our privacy by asking us to share personal information that would have never been public prior to their existence.
There are always those who violate the law by taking advantage of the Internet’s benefits.
PS– Internet Day celebrates everyone’s digital freedom: we can decide what to do in a digital environment, how to do it, and to whom. Is this a way for cyber-criminals to intervene?
LC– This is similar to the freedom we have walking through the streets of a city. But we are not going to prohibit walking down the street, or allocate pedestrian licenses, or make people check in on every corner so that the authorities know where they are at all times. It is clear that in a free environment there are always those who violate the law by taking advantage of the benefits, like those on the Internet, but we cannot let that be an excuse.
PS– The use of the Internet is increasingly widespread. One of the best examples is the number of mobile phones in our country. Do you think we should remind users that their security is in constant danger when browsing the Internet, or do you think that many times it is an exaggeration?
LC– Complete security does not exist in any part of life and definitely does not exist on the Internet. But we must not be paranoid. Just as we know that when driving a vehicle the probability of an accident is lower if we follow the rules, we can be reasonably safe if we have taken appropriate measures prior to surfing the web: have software updated and use a dependable security solution for all devices like computers, tablets and Smartphones.
PS– Internet is linked to technology. It is connected to TVs, online videos, the Internet of Things… do we communicate better or worse thanks to these technological developments?
LC– We communicate easier. Never in the history of mankind have we enjoyed so many options like the ones at our disposal today. With those options we can communicate better or worse… it is debatable. It can be said that there are people who are very faithful to the online world, and are much more isolated from the real world than they would be without the Internet. Do we communicate worse or better? It depends on each person.
If security is not present during a company’s digital transformation, it can ruin them.
PS– Digital transformation is a mandatory process for companies. What guidelines must be followed to complete this process safely?
LC– For those companies who have not already adopted digital transformation, it is probably too late. In any case it is essential that we take into account a company’s security when undertaking a digital project. We can have the best idea in the world, run the project perfectly, and make it a great success, but if security is not present our businesses will sink. Let us remember the damage that was suffered by companies for these type of attacks. Last year, the website Ashley Madison and the Italian company Hacking Team are clear examples of the damage these cyber-attacks can have.
PS– “Cloud” services group customer information into a network of specific servers. Do you need extra security to protect them?
LC– The fact is, for both the user and for the business, using cloud services actually decreases the work we have to do to protect the information. As much as a company wants to protect their users’ information, who is going to be able to devote more resources to do so than companies like Google or Microsoft? From this point of view it is clear that the information is more secure in the Cloud. However, there are other risks that we cannot forget: if someone were to steal one’s identity they would have access to those services that can be accessed remotely.
Remembering to update, protect and distrust are key for navigating the web safely.
PS– What minimum precautions should a user take for a safe experience?
LC– There are some guidelines that apply to all devices (computers, tablets, Smartphones)
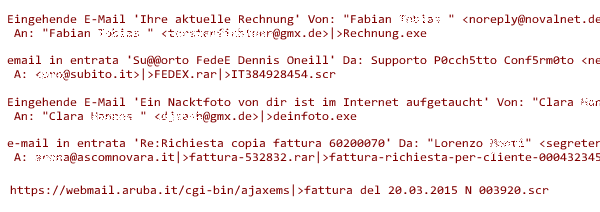
- Update: always have applications and the operating system updated, in order to patch any known security holes.
- Protect: Use a security solution to protect us from the millions of attacks that occur on a daily basis.
- Distrust: Many times, the users themselves cause security problems. We are very confident when we are on the Internet, and cyber-criminals take advantage of this by using the so-called “social engineering techniques”, where they trick us and infect our companies.
PS– Technology and cyber-security: what do we see for them in the future?
LC– A lot. The Internet of Things are going to fundamentally change the world of cyber-security, with more devices that need protecting every day, from domestic appliances to vehicles, all of them are connected to the Internet. The greatest risk is that many of these newly connected devices were designed without taking into account that they would be connected to the Internet one day. Their manufacturers do not make security a priority. Just imagine that someone “kidnapped” your house using ransomware and does not allow you to leave or enter the house until the ransom is paid. Although this seems like science fiction, we must be well prepared for what lies ahead.
The post “Complete security does not exist in any part of life and definitely does not exist on the Internet” appeared first on Panda Security Mediacenter.







 Panda Security
Panda Security