Wi-Fi Security is a feature that is available for Android users within the Avast Mobile Security app as well as within Avast SecureMe for iOS. The feature’s job is to scan Wi-Fi connections and notify you if it finds any security issues including routers with weak passwords, unsecured wireless networks, and routers with vulnerabilities that could be exploited by hackers.
While conducting user testing, we found that 22% of Avast Mobile Security users make use of the Wi-Fi Security feature, making it the 2nd most used feature within Avast Mobile Security.
“Avast SecureMe and Avast Mobile Security offer users a simple, one-touch solution to find and choose safe networks to protect themselves from the threat of stolen personal data,” said Jude McColgan.
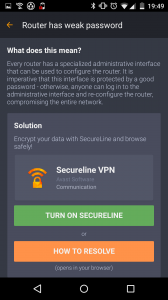
Wi-Fi Security scan notifies you of any issues that are detected
From all the users who tested the Wi-Fi Security feature, more than 10% of the scans performed returned some kind of problem, such as the use of non-encrypted passwords or a router that is susceptible to security threats. The Wi-Fi Security feature currently performs checks for the following four key elements:
- Non-encrypted, unsecured wireless networks
- Networks with weak encryption
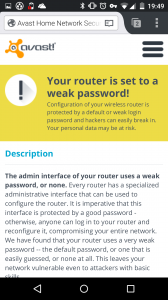
- Weak router passwords
- Routers with known security issues
What’s the risk that my personal data will be stolen?
If you use unsecured Wi-Fi when you log in to a banking site, for example, thieves can capture your log in credentials which can lead to identify theft. On unprotected Wi-Fi networks, thieves can also easily see emails, browsing history, and personal data if you do not use a secure or encrypted connection like a virtual private network (VPN). See our global Wi-Fi hacking experiment to see how widespread the threat really is.
Wi-Fi Security offers two solutions to defend against malware threats
After the Wi-Fi Security feature has scanned your device, you’re presented with two options:
1) Launch Avast SecureLine VPN
2) Click the ‘How to resolve’ button
The first of the two options is meant to be used when you’re connecting to public networks – it’s ideal for cafes, airports, or hotels. On the contrary, users should opt to resolve detected threats if they’re browsing at home using their own devices. When taking this route, you’re redirected to the Avast website in order to set up your router in accordance with our guidelines.

How do I get the Wi-Fi Security feature onto my device?
Avast SecureMe will soon be available in the iTunes Store. Before its widespread release, we will be conducting an invitation-only public beta test. Please sign up here, and the SecureMe team will contact you. If you have already downloaded Avast Mobile Security for Android then you’re all set to start using the Wi-Fi Security feature (you’ll find the “Wi-Fi Security” button on the app’s dashboard). For those yet to download Avast Mobile Security, it is available now from the Play Store.







 Speaking of Wi-Fi – Just like in real estate, one of the most important things for your router is location, location, location.
Speaking of Wi-Fi – Just like in real estate, one of the most important things for your router is location, location, location.  I run because I really REALLY like Beer!
I run because I really REALLY like Beer! World Backup Day
World Backup Day The family IT expert knows how frustrating it can be to help someone solve a computer problem over the phone. Avast makes it easier with our Remote Assistance service. Now you can
The family IT expert knows how frustrating it can be to help someone solve a computer problem over the phone. Avast makes it easier with our Remote Assistance service. Now you can  With all the security improvements in browsers and operating systems, some people have questioned whether they still need antivirus protection. The business of malware has changed, but it can still be devastating if you are targeted. COO ONdrek Vlcek explains why Avast is
With all the security improvements in browsers and operating systems, some people have questioned whether they still need antivirus protection. The business of malware has changed, but it can still be devastating if you are targeted. COO ONdrek Vlcek explains why Avast is