TalkTalk talks numbers – revealing that “only 4%” of its users were affected by the hacking attack on its systems.
The post Nearly 157,000 TalkTalk customers had their personal details hacked appeared first on We Live Security.
![]()
TalkTalk talks numbers – revealing that “only 4%” of its users were affected by the hacking attack on its systems.
The post Nearly 157,000 TalkTalk customers had their personal details hacked appeared first on We Live Security.
![]()
There’s more than one RAT
On Friday, I discovered OmniRat, a program similar to DroidJack. DroidJack is a program that facilitates remote spying and recently made news when European law enforcement agencies made arrests and raided the homes of suspects as part of an international malware investigation.
OmniRat and DroidJack are RATs (remote administration tools) that allow you to gain remote administrative control of any Android device. OmniRat can also give you remote control of any Windows, Linux or Mac device. Remote administrative control means that once the software is installed on the target device, you have full remote control of the device.
On their website, OmniRat lists all of the things you can do once you have control of an Android, which include: retrieving detailed information about services and processes running on the device, viewing and deleting browsing history, making calls or sending SMS to any number, recording audio, executing commands on the device and more.
Like DroidJack, OmniRat can be purchased online, but compared to DroidJack, it’s a bargain. Whereas DroidJack costs $210, OmniRat costs only $25 to $50 depending on which device you want to control.
You may be asking yourself, “Why is software like this being sold on the Internet?”. According to DroidJack’s creator, Sanjeevi, “Droidjack is a parental tool for Android remote administration,” but Europol has made it very clear that using software like DroidJack for malicious purposes can have major consequences. In an investigation supported by Europol and Eurojust, law enforcement agencies in Europe and the U.S. arrested users of DroidJack.
OmniRat variant in the wild
A custom version of OmniRat is currently being spread via social engineering. A user on a German tech forum, Techboard-online, describes how a RAT was spread to his Android device via SMS. After researching the incident, I have come to the conclusion that a variant of OmniRat is being used.
The author of the post received an SMS stating an MMS from someone was sent to him (in the example, a German phone number is listed and the SMS was written in German). The SMS goes on to say “This MMS cannot be directly sent to you, due to the Android vulnerability StageFright. Access the MMS within 3 days [Bitly link] with your telephone number and enter the PIN code [code]“. Once the link is opened, a site loads where you are asked to enter the code from the SMS along with your phone number.
Once you enter your number and code, an APK, mms-einst8923, is downloaded onto the Android device. The mms-einst8923.apk, once installed, loads a message onto the phone saying that the MMS settings have been successfully modified and loads an icon, labeled “MMS Retrieve” onto the phone.
Once the icon is opened by the victim, mms-einst8923.apk extracts OmniRat, which is encoded within the mms-einst8923.apk. In the example described on Techboard-online, a customized version of OmniRat is extracted.
The OmniRat APK requires users to accept and give OmniRat access many permissions, including edit text messages, read call logs and contacts, modify or delete the contents of the SD card. All of these permissions may seem evasive and you may be thinking, “Why would anyone give an app so much access?”, but many of the trusted and most downloaded apps on the Google Play Store request many of the same permissions. The key difference is the source of the apps. I always recommend that users read app permissions carefully. However, when an app you are downloading directly from the Google Play Store requests permissions, it is rather unlikely the app is malicious. I therefore advise you only download apps directly from the Google Play Store. If, like this in case, the app is downloaded from an untrusted source, users should be highly suspicious of the permissions being requested.
Once installed, OmniRat gives full remote administrative control of the device to the attacker. Even if the victim deletes the original “MMS Retrieve” icon installed with the mms-einst8923, OmniRat remains on the infected device. The victim then has no idea their device is being controlled by someone else and that every move they make on the device is being recorded and sent back to a foreign server.
Furthermore, once cybercriminals have control over a device’s contact list, they can easily spread the malware to more people. Inside this variant of OmniRat, there is a function to send multiple SMS messages. What makes this especially dangerous is that the SMS spread via OmniRat from the infected device will appear to be from a known and trusted contact of the recipients, making them more likely to follow the link and infect their own device.
We know that the data collected by the customized version of OmniRat targeting the German person from the Techboard-online forum post is being sent back to a Russian domain, based on the command and control (C&C) server address the data is being sent to.
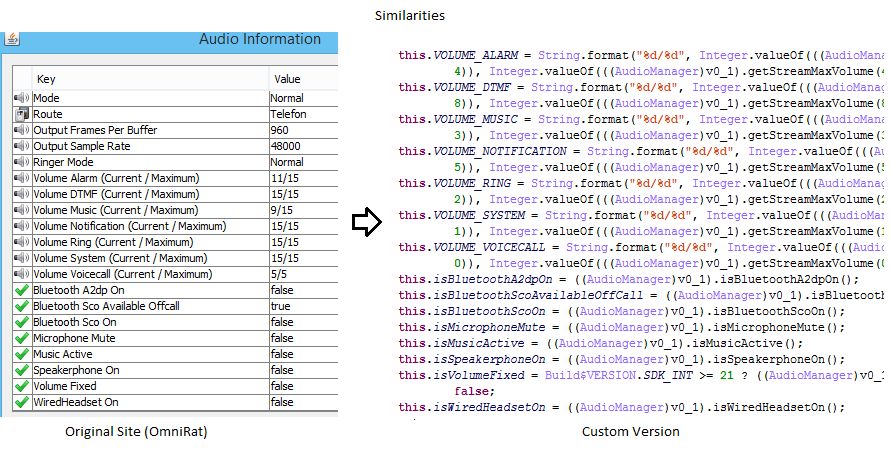
The left image above was taken from OmniRat’s Website and shows the audio data that is being extracted from the victim’s device. The right image is of the custom version of OmniRat and shows the similarity of the data (and the order) that it is being gathered in and sent back to a Russian domain.
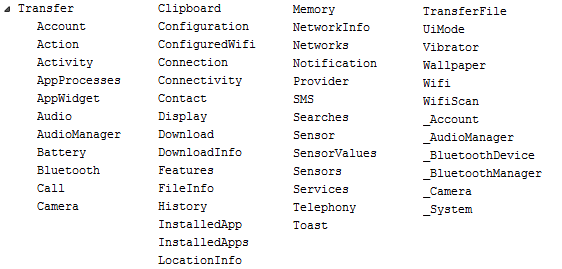
In the image above, we can see all the dex classes of the second APK file that gather various information about the device and sends it back to the server.
How to protect yourself
![]()

Avast 2016 introduces new products to protect your privacy
Count the number of devices you own. If you are like most modern digital-age people, you have a smartphone, half of you own a tablet, and most all of us have a desktop or laptop computer connected through a home router.
Now think about all the private information that you have on those devices. Bank account numbers, passwords, photos, messages and emails – all of them needing some form of protection to stay out of the wrong hands.
In a survey we did this year, 69% of you told us that your biggest fear is that the wrong person would see your personal information. In fact, Americans are so scared of having their financial information get into a bad guy’s possession, that 74% said they’d rather have nude photos of themselves leaked on the Internet! The problem is that most people are not doing anything to protect their privacy, for example, 40% of Americans don’t even lock their smartphones.
“While people are rightfully concerned about privacy, there is a disconnect between that concern and the steps they take to protect themselves,” said Vince Steckler, chief executive officer of Avast. “Users have a multitude of devices and passwords to keep track of, which can be overwhelming. When users feel overwhelmed, they tend to default to unsafe practices that put their privacy at risk.”
So time to face your fear and take steps to protect yourself. Here’s some tools that Avast is launching today to help you:
You probably use your Android mobile phone more than your laptop these days. Much of your life is on your mobile devices – banking information, private messages and photos. Protect all your data with the completely redesigned Avast Mobile Security – for free!
Here’s Avast Mobile Security features I want you to know about today:
Leading Mobile Malware Protection — Yes, malware is a threat but it works differently than classic PC viruses and Trojans. We’re on top of it, with the most advanced mobile malware protections available, now even faster with Avast’s cloud-scanning engine.
Privacy Advisor – Your apps, from mobile messengers to your bank, contain information that you want to protect. Privacy Advisor informs you about what data apps have access to and the ad networks that are included in the apps.
Wi-Fi Security – It’s not called mobile for nothing. You are out-and-about all the time, connecting to who-knows-what free Wi-Fi hotspot. We notify you when you connect to an unsecure router, so you can avoid bad guy’s eavesdropping and snooping on you.
Unlimited App Locking — Nosy kids, friends, and family members can be kept out of your business because we can password protect any apps on your device, providing another line of defense against prying eyes.
The designers and engineers of the world’s most trusted antivirus got together with the mission to make your life easier. Avast 2016 sports a new simplified user interface with fewer buttons. It’s compatible with Windows 10, and it notifies you of Windows updates so you can easily keep software up-to-date and patched.
But it’s these two new features that we’re most excited about today:
Avast Passwords (for PC, iOS, Android) automatically generates extremely strong passwords that you don’t have to struggle to remember! All you do is set and remember one master password to access all your passwords. One password to rule them all!
SafeZone Browser (available with all premium versions of Avast) keeps all your banking and payment sites isolated in a protected space called Pay Mode, and if you run into suspicious sites, an isolated, virtual environment called Safe Mode will automatically open, so you don’t risk the safety of your machine and data.
Wi-Fi Security – This is the same great feature that’s available in Avast Mobile Security. When you connect to an unsecure router you will be notified.
VPN – Avast SecureMe establishes a secure connection when you’re connected to open Wi-Fi.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()

We’re happy to announce that Avast Free Antivirus on Windows 10 64-bit has been certified by ICSA Labs! After being tested in the ICSA Labs Anti-Virus Certification Testing Laboratory, Avast Free Antivirus on Windows 10 64-bit has satisfied the requirements for the Desktop Server AV Detection module within the Anti-Virus Corporate Certification Testing Criteria.
The Desktop Server AV Detection is targeted at antivirus products designed to protect individual desktops, laptops, or servers of individuals and businesses from malicious code infection. In order to meet all the requirements within the Desktop Server AV Detection module, antivirus products must accomplish the following things:
• Detect malware on-demand
• Detect and prevent the replication of viruses on-access
• Report no false positives
• Log the results of attempted malware detections
• Perform necessary administrative functions
About ICSA Labs
ICSA Labs is the security industry’s principle antivirus product testing and certification facility. The company is a reliable source for finding which products are currently certified and also includes a collection of detailed lab reports of the tests that are conducted on the products.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
Can cars be hacked remotely or is the idea of remotely hackable cars still only a hypothetical threat? Evidence is presented to help answer this question.
The post The great car hacking debate appeared first on We Live Security.
![]()
Sounds like a risky thing to do, but in a recent experiment in four major U.S. cities, that’s exactly what happened when 200 unbranded USB devices were left in public places. One in five people let their curiosity get the best of them and plugged the flash drive into a device. These “Nosy Nellys” proceeded to open text files, click on unfamiliar web links, or send messages to a listed email address. All potentially risky behaviors!

You can scan your USB sticks with Avast
“These actions may seem innocuous, but each has the potential to open the door to the very real threat of becoming the victim of a hacker or a cybercriminal,” said Todd Thibodeaux, president and CEO of The Computing Technology Industry Association (CompTIA) the trade association that commissioned the experiment.
Every time you plug an unknown flash drive into your computer, you’re taking a risk because a USB drive can spread malware, as well as attract it. Here are some dramatic examples:
The infamous Stuxnet worm and Flame malware, alleged American-Israeli cyber weapons designed to attack and spy on Iran’s nuclear program, relied on USB sticks to disseminate attack code to Windows machines.
A tainted USB drive was responsible for attacks at two U.S. power generation facilities documented in late 2012. The U.S. Industrial Control Systems Cyber Emergency Response Team were called in to investigate and found that infections were spread by USB drives that were plugged into critical systems without back-ups.
Avast antivirus products come with a number of pre-defined scans including the ability to scan any removable storage device that is connected to your computer, like USB flash drives and external hard drives. It will scan the drive to detect potential “auto-run” programs that may try to launch when the device is connected.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
Hace unos días recibimos en Twitter un mensaje de Juan José, usuario de Avast en su teléfono móvil, en el que nos comentaba que, gracias a Avast Anti-Theft, pudo recuperar su teléfono perdido.

Juan José con su móvil recuperado gracias a Avast Anti-Theft
Mientras Juan José paseaba por Sevilla, se dio cuenta de que su teléfono móvil ya no estaba con él, lo había perdido. Su primera reacción fue llamar al número para ver si alguien lo había recogido y podía devolvérselo. El teléfono daba señal, pero nadie respondía.
Temiendo que quien había encontrado el teléfono no tenía intención de devolvérselo, Juan José dio unos pasos muy importantes en estos casos. Desactivó la tarjeta SIM y modificó la contraseña de su cuenta de Google.
Lo que no se esperaba es que, gracias a una acción que realizó anteriormente, iba a recuperar su teléfono.
Juan José fue previsor e instaló Avast Anti-Theft en su teléfono. Durante la instalación, introdujo un número de teléfono “amigo”, por lo que siempre que haya un cambio en la tarjeta SIM del dispositivo, el teléfono indicado recibirá un mensaje con todos los detalles de la nueva tarjeta.
Y eso es exactamente lo que sucedió. Al cabo de unos días, y sin tener esperanza en recuperar el teléfono perdido, Juan José recibió un mensaje de Avast informando sobre el cambio de tarjeta SIM en el dispositivo.
Gracias a los datos que el mensaje incorporaba, Juan José pudo contactar con el propietario de la tarjeta que, de buen grado, accedió a devolverle el teléfono.
Como ya explicamos anteriormente en el blog y tal y como hemos podido ver, hay que estar preparado por si alguna vez perdemos o nos roban nuestros teléfonos móviles. Instala gratuitamente Avast Anti-Theft en tu dispositivo Android.
¿Tienes alguna historia similar? Envíanos un mensaje en Facebook o Twitter.

¿Tienes alguna historia relacionada con nuestros productos? Envíanos un mensaje en nuestras redes sociales
![]()
Organisations of all sizes need to do more to protect their social media accounts from being hijacked.
The post Police force blames hacker after #CyberAware tweet sent out containing bogus security advice appeared first on We Live Security.
![]()
Forget about zombies, vampires, and ghosts. Americans don’t fear things that go bump-in-the-night as much as they do their own government. The annual Survey of Fear conducted by Chapman University asked Americans about their level of fear in 88 different topics ranging from crime, the government, disasters, personal anxieties, technology, and others. The majority of Americans said that they are “afraid” or “very afraid” of the corruption of government officials.

One of American’s greatest fears is government-sponsored spying
The misuse of technology, financial crime, and privacy-related issues took up half of the Top 10 fears of 2015. After two years of high-profile data breaches and the revelations of government spying from the Edward Snowden leaks, it’s not too surprising. Here’s the list:
From this survey, it’s apparent that Americans’ awareness and concern about guarding their personal privacy is growing. An interesting topic that was further down the list is “Technology I don’t understand,” feared by 19% of Americans surveyed. At least that is something that individuals can control – just watch some videos or read this blog and you will learn about technology and how you can minimize your risks of these other things happening to you. For example, here’s how to secure your Facebook login and protect your personal privacy and identity.
The fears of government spying don’t go unwarranted. Facebook has reason to believe that it’s an important issue “because these types of attacks tend to be more advanced and dangerous than others.” These are the words of Facebook’s Chief Security Officer, Alex Stamos, in a recent announcement telling if the social media network suspects that a user is being targeted by government-sponsored hackers, they will issue an alert advising them to “take the actions necessary to secure all of their online accounts” such as “rebuild or replace these systems [your computer or mobile device] if possible.”
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()

Is something not right with your browser, but you can’t quite figure out what?
Here’s another reason to slow down when installing software, especially free software. A new Potentially Unwanted Program (PUP) disguised as the Google Chrome browser is sneaking onto users computers bundled with legitimate software, hidden deep within the ‘Custom’ or ‘Advanced’ settings that most people skip over. Once installed, eFast, as it has been called, serves up ads and tracks your online activities and sells personally identifiable information to advertisers.
“Read the installer screens to make sure what they actually install,” warns Michal Salat, researcher in the Avast Virus Lab. ” The Next->Next->Next->Done approach is exactly why we deal with PUPs daily. If there isn’t an option not to install some additional software, terminate the installer immediately. Better safe then sorry.”
Researchers at Malwarebytes says that eFast actually installs a new browser rather than hijacking your existing one. If you already have Chrome installed, it will replace it making itself the default browser. The fake browser uses the same source code for the user interface as the real thing making it difficult to tell the difference. It is so tricky that it even replaces shortcuts on your desktop that look similar to Google Chrome.
In addition to all that, eFast hijacks some file associations, so that it can open as many times as possible therefore having the opportunity to show you more ads! If you open a file like JPEG, PDF, or PNG, it will be opened with eFast, resulting in pop-ups, more ads in your searches, and other adware. You can see the list of file associations on Malwarebytes security blog.
Open your browser and type in chrome://chrome. The authentic Chrome browser will take you to the ‘About’ section and check if your browser software is up-to-date. It looks like this.
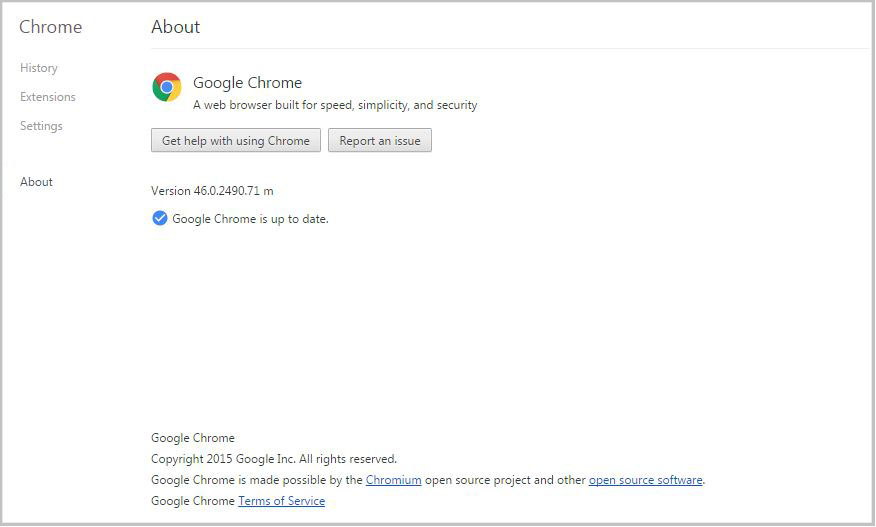
If you have a fake version of Chrome, then you will be taken to a fake About page, get an error, or the link won’t work. In that case, check out the removal instructions on PCrisk.
eFast is classified as a Potentially Unwanted Program, also known as a PUP. PUPs are annoyances like search bars, intrusive adware, etc. that Avast does not detect by default. However, the option can be enabled.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()