Microsoft’s switch to rollup patching for Windows 7/8.1 will have an impact on security, one expert says.
Tag Archives: Malware
Malvertising campaign intent on soiling Avira’s white vest

Have you already heard about the term “Malvertising” in the mobile world?
The post Malvertising campaign intent on soiling Avira’s white vest appeared first on Avira Blog.
Know the tricks of the new Locky

In this new Tales from Ransomwhere we discovered the tricks of one of the most infamous families in the landscape of the ransomware: Locky .
Recently (our colleagues from Avira reported it in July) they added a new feature, it includes an offline mode so it is able to encrypt files when the connection to the server is not available. The weak point is that this key is the same for every computer which files are encrypted, that’s why this is just something that is performed when for some reason the C&C server is unavailable.
On top of this now they have changed the way they infect computers. Usually these attacks rely on a small downloader Trojan who downloads and executes the ransomware. For example, when the attack comes from a javascript file, this usually downloads a small executable which only function is to get the ransomware and execute it. As I have explained in previous articles, cybercriminals are all the time making small changes trying to avoid detection from security solutions.
Distribution of new attack
In this case the attack is being distributed through email, we have seen a number of them with a zip file that has a javascript file inside named “utility_bills_copies <random characters>.js”. However there are different versions using different subjects and file types, for example this one:
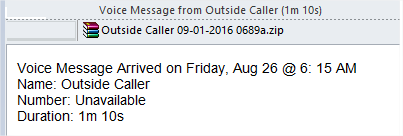
Which inside has the following file:
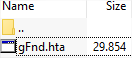
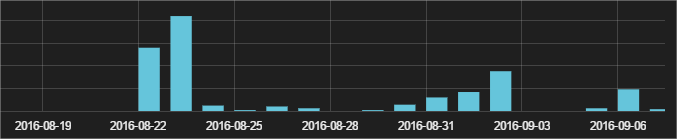
They have skipped the downloader Trojan part and the script gets the Locky variant in DLL format (with the downloader in most cases the downloaded file was an EXE), which is executed using Windows rundll32.exe. The first sighting of this was on August 22nd, and so far they keep using the same strategy. As you can see they are launching one wave per week:
The most severely affected territories
We have seen just a few hundred infection attempts mainly in North and South America and Europe, although there are some in Africa and Asia too. In case they get a good return of investment we’ll probably see an increase in the next weeks. Here you can find a few hashes of this Locky variant:
The post Know the tricks of the new Locky appeared first on Panda Security Mediacenter.
Google Shares Android Nougat, Safe Browsing Security Enhancements
Google stepped up efforts this week to bolster its security strategy with news from both its Android Security Team and its Safe Browsing Team.
Warning! This Cross-Platform Malware Can Hack Windows, Linux and OS X Computers
Unlike specially crafted malware specifically developed to take advantage of Windows operating system platform, cyber attackers have started creating cross-platform malware for wider exploitation.
Due to the rise in popularity of Mac OS X and other Windows desktop alternatives, hackers have begun designing cross-platform malware modularly for wide distribution.
Cross-platform malware is
![]()
Hacker Who Hacked Official Linux Kernel Website Arrested in Florida
Around five years after unknown hackers gained unauthorized access to multiple kernel.org servers used to maintain and distribute the Linux operating system kernel, police have arrested a South Florida computer programmer for carrying out the attack.
Donald Ryan Austin, a 27-year-old programmer from of El Portal, Florida, was charged Thursday with hacking servers belonging to the Linux Kernel
![]()
Threatpost News Wrap, September 2, 2016
Mike Mimoso, Tom Spring, and Chris Brook discuss the news of the week, including the MedSec/Muddy Waters story, how the Angler EK was traced back to the Lurk Gang, Fairware hitting Linux servers, and the Bashlite IoT malware.
Malvertising Campaign Pushing Neutrino Exploit Kit Shut Down
Researchers uncovered a global malvertising campaign exposing potentially millions of users to the risk of being hit with CrypMIC ransomware delivered via the Neutrino Exploit Kit.
Insecure Redis Instances at Core of Attacks Against Linux Servers
Attackers are targeting insecure Redis instances, exposed to the internet, to access Linux servers and delete web files and folders in exchange for ransom.
BASHLITE Family Of Malware Infects 1 Million IoT Devices
More than one million consumer web-connected video cameras and DVRs are compromised by bot herders who use the devices for DDoS attacks, researchers say.


