
Skype worms are not exactly new anymore (unfortunately).
Scenario is simply: someone on your friends list got infected and is now sending you a link to a ‘funny image’ or pictures of you. In this case, you are being baited by a video of you. Let’s just hope it’s nothing embarrassing ![]()
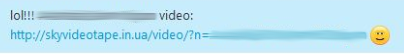
Lol! Seems like there’s a cool new video of you going around.
When visiting the (totally not malicious looking) link, you get a video, but apparently you need to download a plugin first:
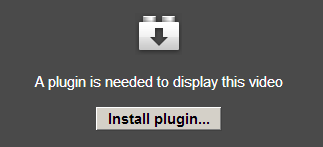
When you click on Install plugin… a new file called ‘setup.exe’ gets downloaded. It’s actually simply a self-extracting archive which contains a file named: ‘setup_BorderlineRunner_142342569355180.exe’
When running the setup.exe file:
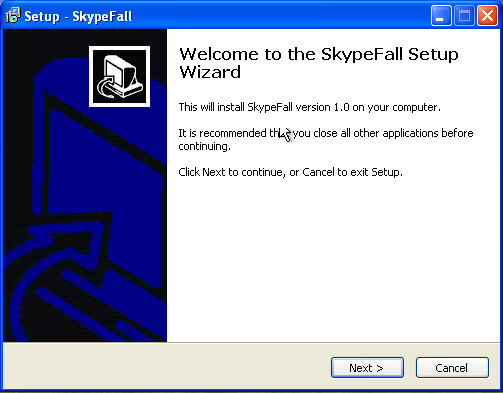
It almost seems like we’re installing legitimate software, SkypeFall version 1.0. Almost.
Clicking Next, Next, Next in the setup wizard, nothing much seems to be happening, but in the background there’s quite a lot going on:
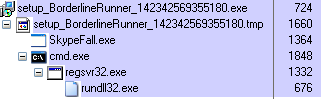
A new file called ‘SkypeFall’ is dropped and a new DLL is being registered. Afterwards, two new processes are now active in memory: SkypeFall.exe and rundll32.exe, in which the latter is actually running the DLL BorderlineRunner.dll.
Files are being created in both respectively %programfiles%BorderlineRunner and %appdata%SkypeFall. A new service is also registered:
HKLMSystemCurrentControlSetServices6b57ae94
Afterwards you’ll spam all your friends with the same message as well, following the pattern:![]()
We detect this malware as:
W32/Skyper.A.worm
IOCs
Domains:
hxxp://24onlineskyvideo.info
hxxp://24videotur.in.ua
hxxp://deepskype.net
hxxp://factorygood.net
hxxp://ironskype.net
hxxp://letitskype.info
hxxp://letskype.net
hxxp://popskypevideo.net
hxxp://popvideoskype.com
hxxp://popvideoskype.info
hxxp://popvideoskype.net
hxxp://skypepopvideo.net
hxxp://skypepopvideo.net
hxxp://skyvideo24.in.ua
hxxp://skyvideo24online.in.ua
hxxp://skyvideo24online.ru
hxxp://skyvideotape.in.ua
hxxp://skyvideotape.ru
hxxp://someskype.com
hxxp://someskype.net
hxxp://techine.info
hxxp://techine.net
hxxp://videosk.in.ua
hxxp://videosk.info
hxxp://videoskype.ru
hxxp://videoskype24.ru
hxxp://videoss.in.ua
Hashes (SHA1):
b6f690849e9ed71b3f956078934da5ed88887aa3
42c685ac60555beaacd5e07d5234a6600845e208
dfb9bfb274e9df857bb0fae02ba711e62a2a9eb6
726db7f1c956db8c5e94d21558cbbe650b949b7e
How to avoid the malware W32/Skyper.A.worm
- Never click on unknown links, especially when a friend sends you a generic text saying there are pictures or videos of you going around. If you’re really curious, ask them first what’s it about. Better be safe than sorry.
- Don’t be fooled by known icons or “legit” file descriptions, this can easily be altered.
- Even if you clicked the link and you’re not suspicious, you should be when a file is downloaded and no pictures are shown, but just an EXE file.
The post Skype worm reloaded appeared first on MediaCenter Panda Security.

